2023-11-6 21:31:30 Author: www.threatfabric.com(查看原文) 阅读量:21 收藏
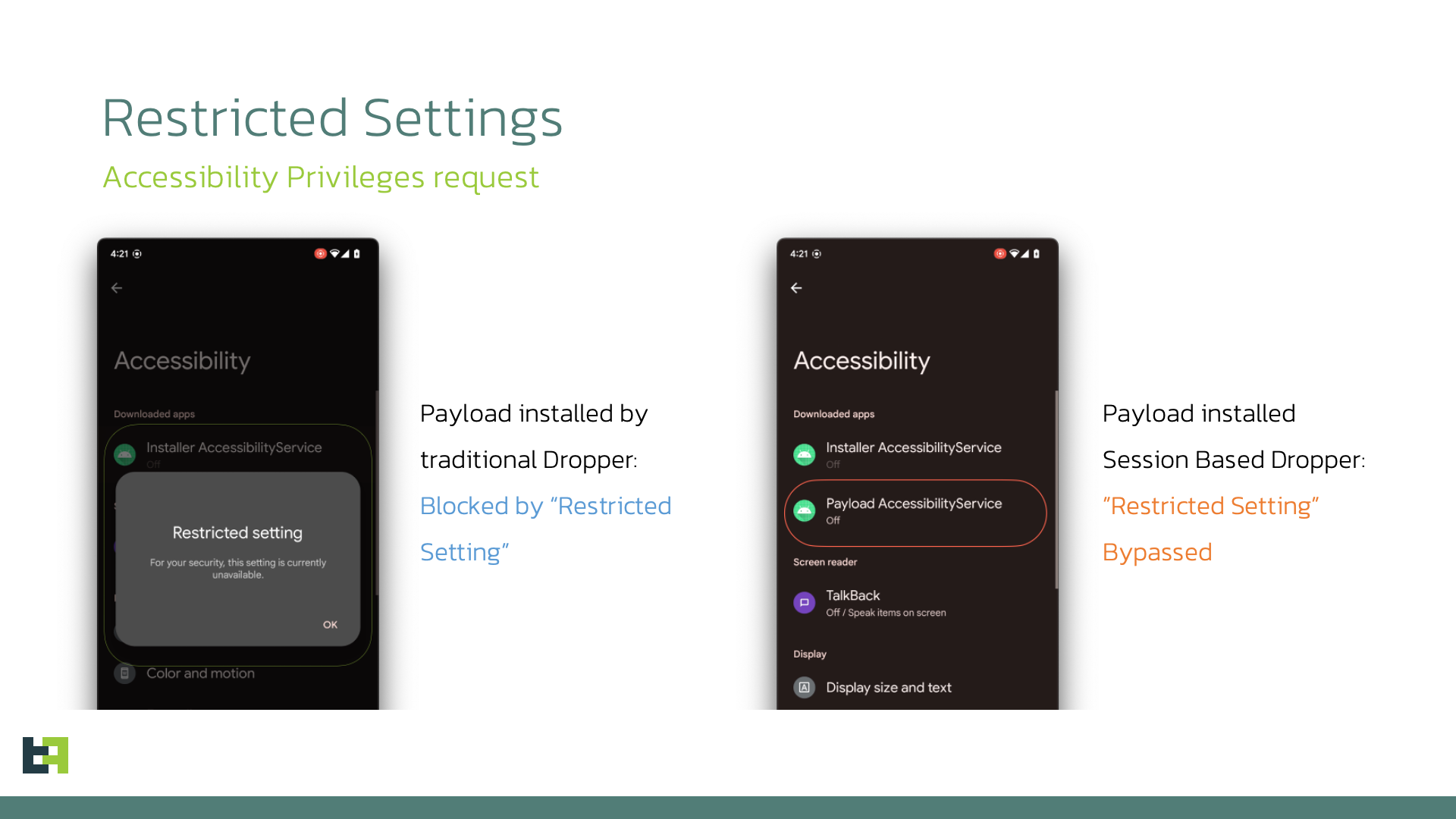
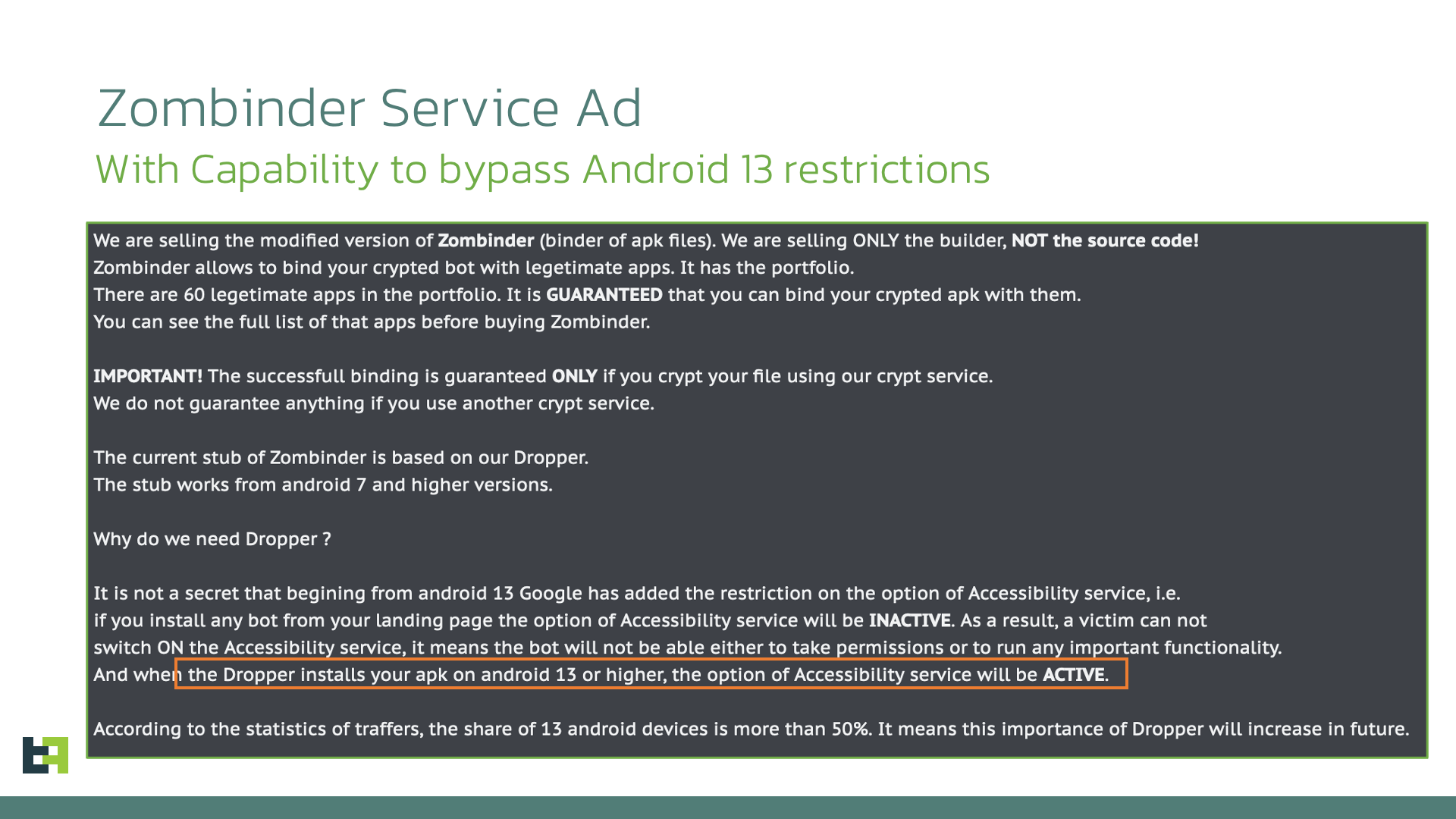
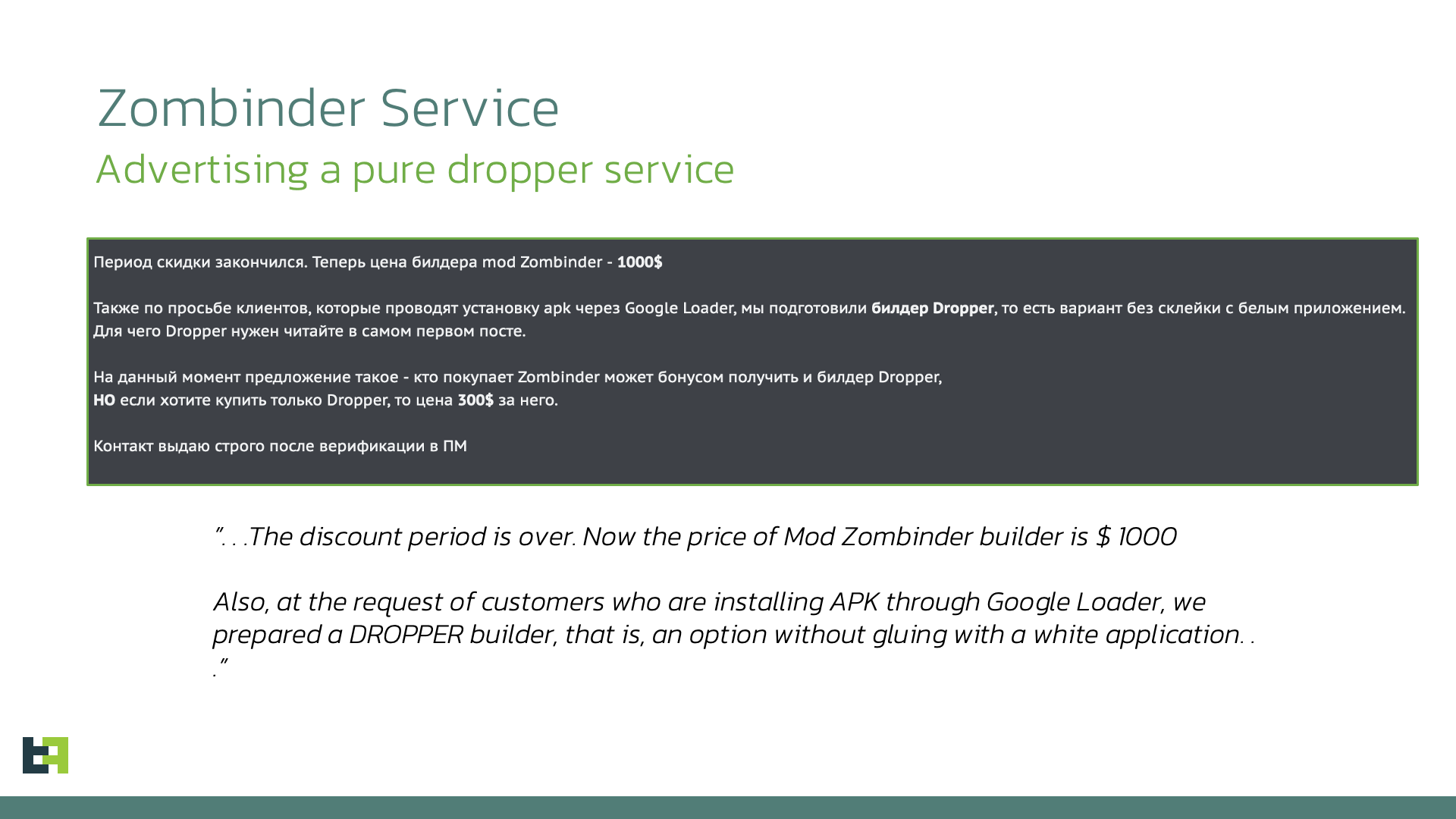
In this blog we will look at how threat actors are bypassing the "Restricted Settings" security measure introduced by Google in Android 13 to help protect against malware by taking a closer look at SecuriDropper, the first example of a widely distributed dropper bypassing this security measure. Droppers are a specific category of malware whose main purpose is to install a payload on an infected device. The use of droppers allows actors to separate the development and execution of an attack from the installation of the malware. This can also be a businness endeavour in itself, as many actors choose to focus on developing droppers that can be sold to other criminals as part of what is commonly defined as MaaS (Malware-as-a-Service). No wonder then that Android Droppers have emerged as the preferred method for deploying malware onto unsuspecting users' devices. Malware actors are focusing more and more energy and effort on this aspect of their distribution strategies to increase their reach as much as possible. Droppers and the actors behind them are in a constant state of evolution as they strive to outwit evolving security measures. In Android 13, Google responded with their latest salvo in this ongoing battle by introducing restrictions on the privileges granted to sideloaded applications, a change we discussed in our 2022 mobile threat landscape update. Google calls this feature "Restricted Settings". Sideloaded applications are applications which are loaded onto the device from sources other than official app stores (such as the Google Play Store). Because sideloaded apps are not subject to the same checks as apps submitted for publication in official app stores, this method of loading apps onto devices is seen as attractive to malware developers. Restricted Settings acts as a gatekeeper, prohibiting sideloaded applications from directly requesting Accessibility settings and Notification Listener access, two features often abused by malware. For sideloaded apps, the entry in the Accessibility menu corresponding to the app will be greyed out and not directly accessible, while the user will receive a Restricted Setting alert. Restricted Settings only affects sideloaded applications, while apps downloaded from app stores are not affected. So how does the Android Operating System tell sideloaded apps apart from official apps? Applications downloaded from official stores employ a specific installation method, namely using a "session-based" package installer, while sideloaded apps do not normally use this method. When we initially analysed the new Restricted Setting feature, we theorised that if a sideloaded app was able to use a "session-based" installer, it would bypass the restrictions. Consequently, this solution, while a significant step, does not prevent cybercriminals from acquiring the necessary privileges and permissions for their malicious intentions. Up to this point, we did not see underground actors adopt this approach at scale. It remained the domain of theories and proof of concepts. Recently, this has changed. We have observed a new Dropper-as-a-Service (DaaS) offering that bypasses Restricted Settings using the method we identified back in 2022. We've named this dropper family SecuriDropper. Roughly at the same time, our researchers also noticed a new advertisement in cybercrime forums for the Zombinder service, which also claims to bypass Restricted Settings. In the next part of this article, we will examine SecuriDropper, including its observed payloads. Next, we will take a closer look at the Zombinder service. Dropper-as-a-Service (DaaS) is a kind of service that is gaining quite a lot of momentum in the cyber underground. DaaS offers a two-staged infection process, which in the case of SecuriDropper allows cybercriminals to bypass any security solutions including Android 13's Restricted Settings without being detected. The first stage involves the distribution of a seemingly harmless application, often disguised as a legitimate app, which serves as the dropper. The dropper is responsible for installing a secondary payload, typically malware (spyware or banking Trojans), onto the victim's device. This separation of tasks adds an extra layer of complexity to the attack, making it harder for security measures to detect and prevent malicious activity. What makes SecuriDropper stand out is the technical implementation of its installation procedure. Unlike its predecessors, this family uses a different Android API to install the new payload, mimicking the process used by marketplaces to install new applications. In this way, the Operating System cannot differentiate between an application installed by a dropper and a marketplace and allows the payload to bypass the "Restricted Settings" feature in Android 13. We will not discuss the exact details of how to implement a session-based installation in this article, as we do not want to provide easy access to this information to underground actors. However, we will discuss the main points that distinguish SecuriDropper from other dropper families. In delving into the inner workings of this discovered dropper's operation, we found that it primarily relies on two key permissions: "Read & Write External Storage" and "Install & Delete Packages" permissions, which it solicits from users during installation. Once these permissions are granted, the dropper springs into action. It first checks if the payload's package is preinstalled on the device. If it detects the payload, it directly launches the application. This launch request may also include the crucial enabling of AccessibilityService, to enable its malicious functionalities. The following code snippet showcases the process of launching the payload app, whether it's preinstalled or necessitates installation. In instances where the payload is absent on the device, the dropper's strategy shifts. It manages user interfaces and buttons, presenting messages tailored to the device's language and location. The following code snippet details the default language used for text display, prompting users to install the payload by clicking the "Reinstall" button. Once initiated, users are guided through the process of enabling the necessary permissions for payload installation. After the session-based installation, the malicious application operates according to its intended purpose, successfully requesting the essential permissions while prompting users to enable AccessibilityService, which is possible due to the circumvention of Android 13's "Restricted Setting" feature. ThreatFabric researchers continuously track the activity of SecuriDropper. The dropper has been observed camouflaging itself as a legitimate application spanning various categories, from social apps to productivity tools. In our investigation into the payloads deployed through SecuriDropper we uncovered malware families belonging to two different malware categories: Spyware and Banking Trojans. Recently, a significant surge in the activity of SpyNote, a renowned spyware family with potent Remote Access Trojan (RAT) capabilities, has caught our attention. Notably, a substantial number of SpyNote samples have surfaced on cybercrime forums, where actors are not only selling the samples but also discussing strategies for widespread distribution that remain undetected. ThreatFabric unveiled a campaign of SpyNote samples distributed through phishing websites, deployed by SecuriDropper. SpyNote needs AccessibilityService permissions to function (a defining feature within SpyNote among spyware families): it uses it to capture sensitive information, including text messages, call logs, and even screen recordings. Given this requirement, it is no surprise that a SpyNote campaign would use SecuriDropper as its dropper: without it it would not be able to obtain the required permissions as Restricted Settings is intended to prevent sideloaded apps from obtaining this often abused permission. Our investigation on SecuriDropper also unveiled the use of this dropper family to distribute Banking Trojans through deceptive websites and third-party platforms. These Banking Trojans are explicitly engineered to steal financial information, being capable of intercepting login credentials and tampering with transactions, thereby putting victims at risk of substantial financial losses. An intriguing aspect of our findings centres around the Ermac malware family, a notable player within the realm of Banking Trojans. What sets this discovery apart is the deployment of Ermac samples via the Discord platform, a widely known and legitimate communication channel, primarily used by gamers and diverse online communities. Discord, much like GitHub repositories, has often been repurposed from its intended use by threat actors within the Android ecosystem as a distribution channel for their malicious exploits, highlighting the adaptability of these cybercriminals. This campaign initiates its first stage of distribution via the Discord platform, where users unwittingly download SecuriDropper. Upon installation, a prompt urges users to "Reinstall" an application. Should users comply and click the button, the dropper promptly deploys the payload. Upon launching the payload, a request surfaces, this time seeking user consent to enable AccessibilityService – the frequently exploited permission Restricted Settings was intended to deny to these apps. Recently, an event that piqued our curiosity was the re-surfacing of Zombinder, advertised and sold in the shadows of hacking forums. Zombinder boldly advertises its capabilities, not just as a service but also as a provider of app builders adept at circumventing Android 13's restrictions. Zombinder got its name due to its peculiarity of "gluing" together a legitimate application with code responsible for installing a payload on an infected device. In effect, Zombiner piggybacks a dropper on the back of a legitimate app. These Zombinder builders are available at a price point of $1000. What is interesting about recent advertisements, is that purchasers of the Zombinder service also gain access to a dropper builder, which consists only of the dropper capability (without the "gluing" feature). Interestingly, this description fits quite well with the features of SecuriDropper. However, at the time of writing this blog, we do not possess definitive information to establish a direct connection between SecuriDropper and the advertised Zombinder service. ThreatFabric researchers will continue to closely monitoring both the SecuriDropper and Zombinder services. In our exploration of droppers bypassing Android 13 restrictions, we have witnessed the evolution of the mobile security landscape. As Android continues to raise the bar with each iteration, cybercriminals, too, adapt and innovate. Dropper-as-a-Service (DaaS) platforms have emerged as potent tools, allowing malicious actors to infiltrate devices to distribute spyware and banking Trojans. These malicious payloads, once unleashed, can compromise users' privacy and financial security. Securidropper is evidence that underground actors have independently discovered a method of bypassing Android 13's Restricted Settings feature first identified in May of this year by ThreatFabric researchers. Moreover, the emergence of services like Zombinder are indications of a booming market in cybercrime, offering builders and tools for evading Android 13's defenses. It is a testament to the resourcefulness of those seeking to exploit security vulnerabilities for their gain. SecuriDropper and Zombinder are reminders for organisations that rely on or conduct business through mobile channels that it is critically important to stay abreast of developments. ThreatFabric’s Fraud Risk Suite enables safe & frictionless online customer journeys by integrating industry-leading mobile threat intel, behavioral analytics, advanced device fingerprinting, and over 10,000 adaptive fraud indicators. This will give you and your customers peace of mind in an age of ever-changing fraud.Introduction
Restricted Setting
SecuriDropper
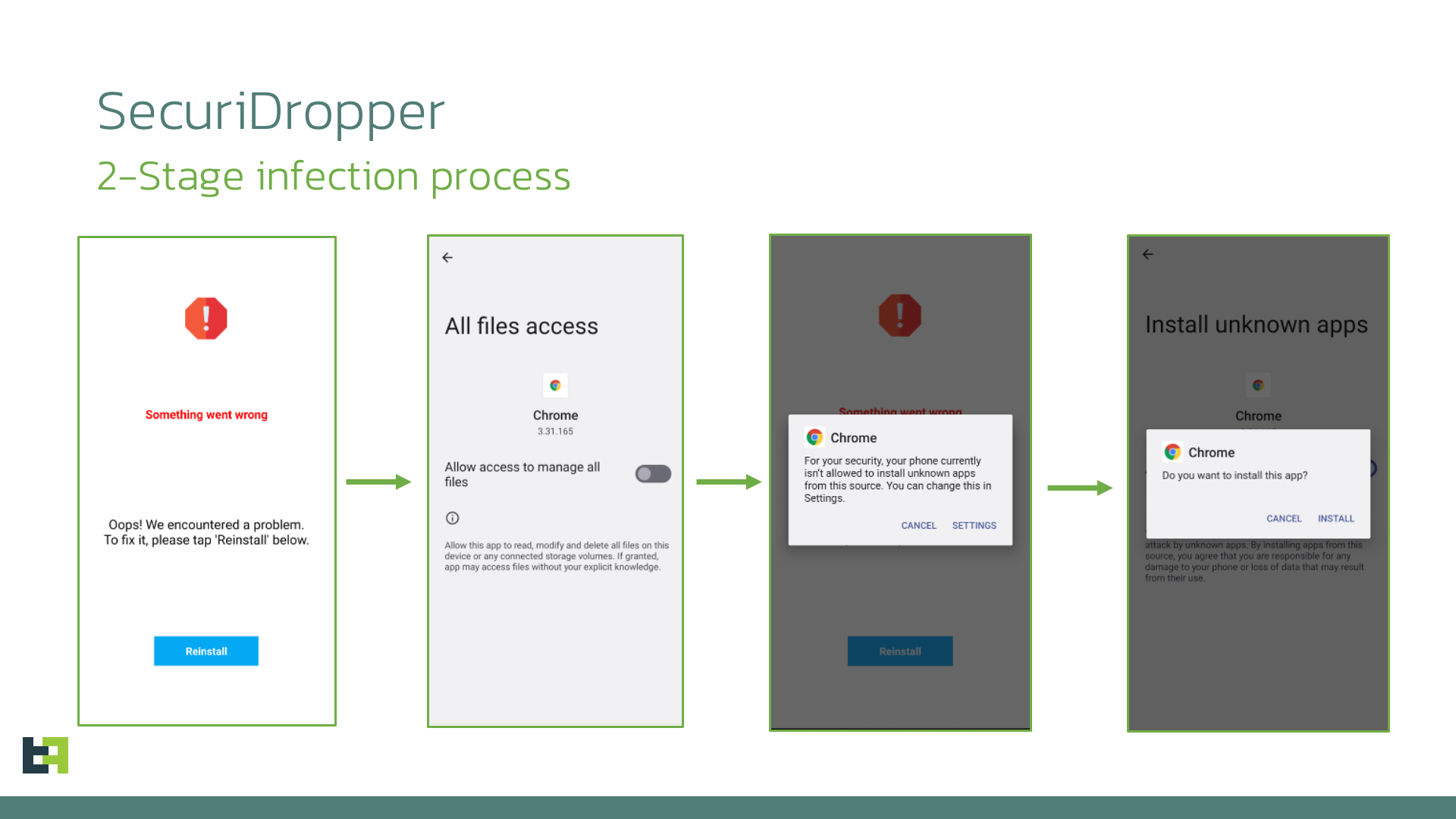
How does it work?
private void requestPermissions() {ActivityCompat.requestPermissions(this, new String[]{"android.permission.WRITE_EXTERNAL_STORAGE", "android.permission.READ_EXTERNAL_STORAGE"}, 1);}public static String TargetBaseid = <app_package_name>;
protected void onCreate(Bundle bundle0) { super.onCreate(bundle0); Context context0 = this.getApplicationContext(); this.mContext = context0; if (InstallActivity.isAppAvailable(context0, InstallActivity.TargetBaseid)) { Intent intent0 = this.getPackageManager().getLaunchIntentForPackage(InstallActivity.TargetBaseid); intent0.addFlags(0x10000000); intent0.addFlags(0x20000000); this.startActivity(intent0); this.finish(); return; }
...
}this.upbtn = (Button)this.findViewById(0x7F05000F);default: { this.titleview.setText("Something went wrong."); this.decripview.setText("We encountered a problem. To fix it, please tap \'Reinstall\' below."); this.upbtn.setText("Reinstall"); this.upbtn.setOnClickListener(new View.OnClickListener() { ... public void onClick(View view0) { if(!InstallActivity.this.checkPermissions()) { InstallActivity.this.requestPermissions(); return; } worker.install(InstallActivity.this.getApplicationContext()); }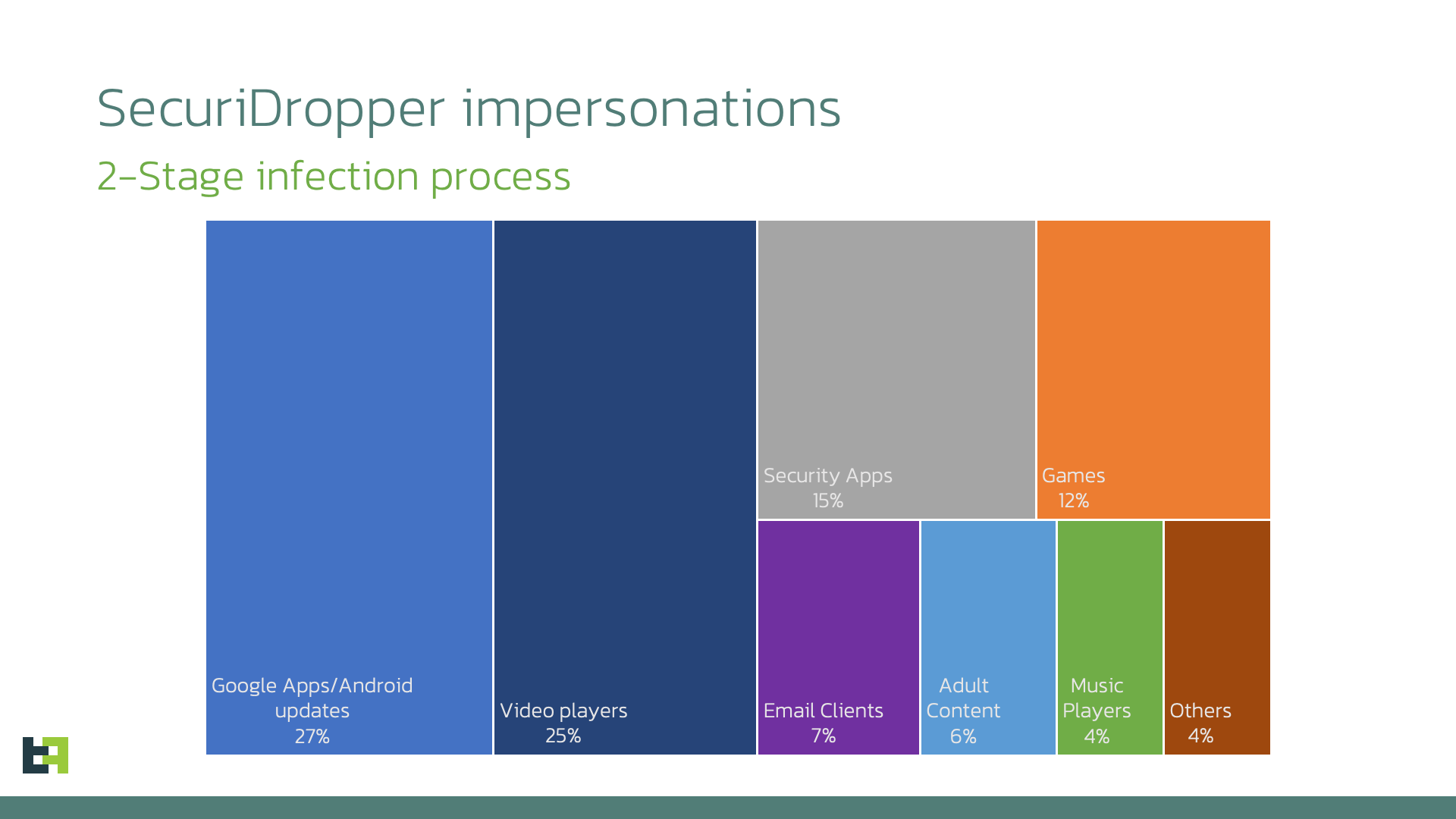
Spyware and Banking Trojans: The Perils of DaaS
Spyware Families
Banking Trojans
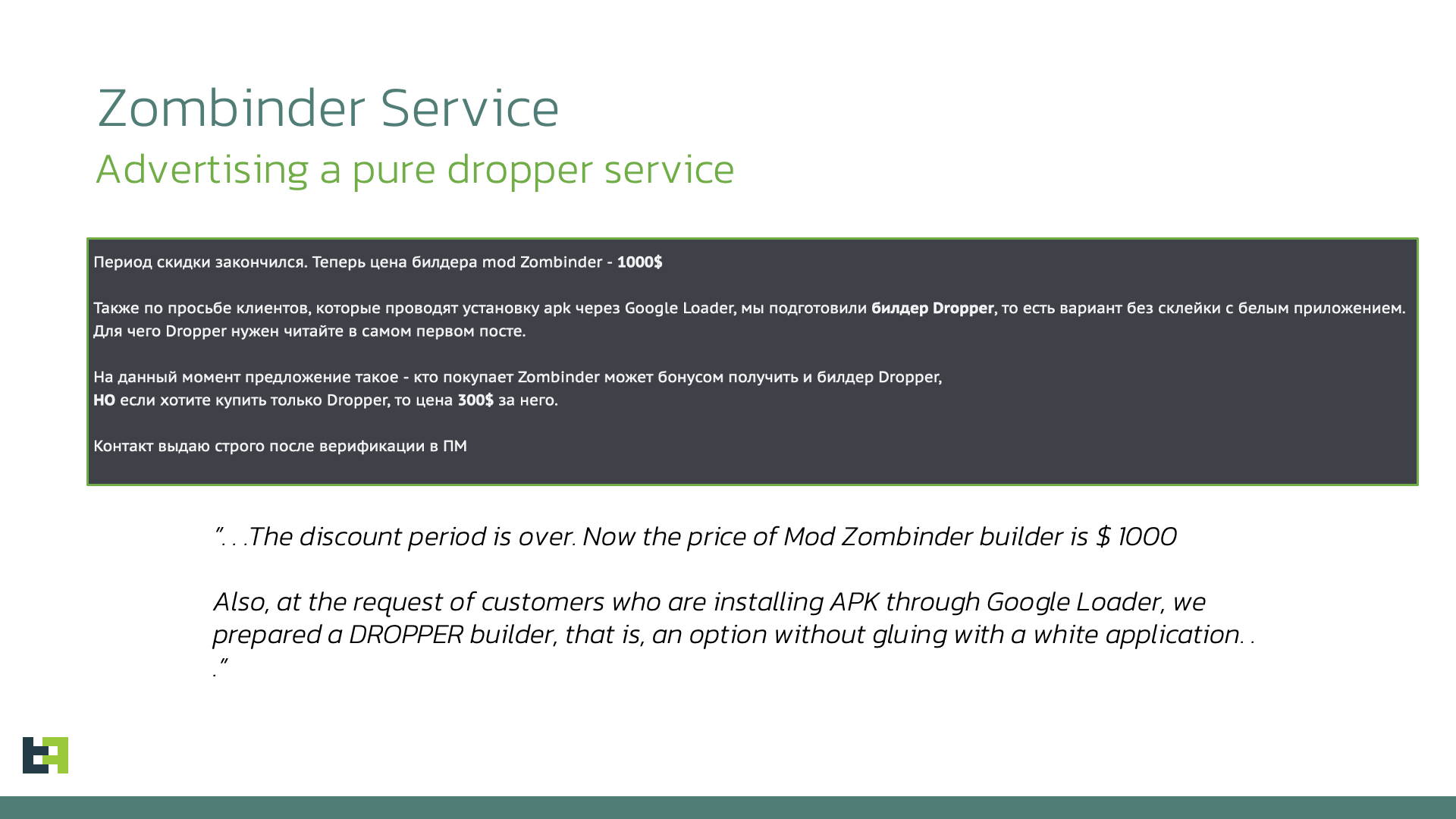
Zombinder also bypasses Restricted Settings
Conclusion
Fraud Risk Suite
Appendix
Indicators of compromise
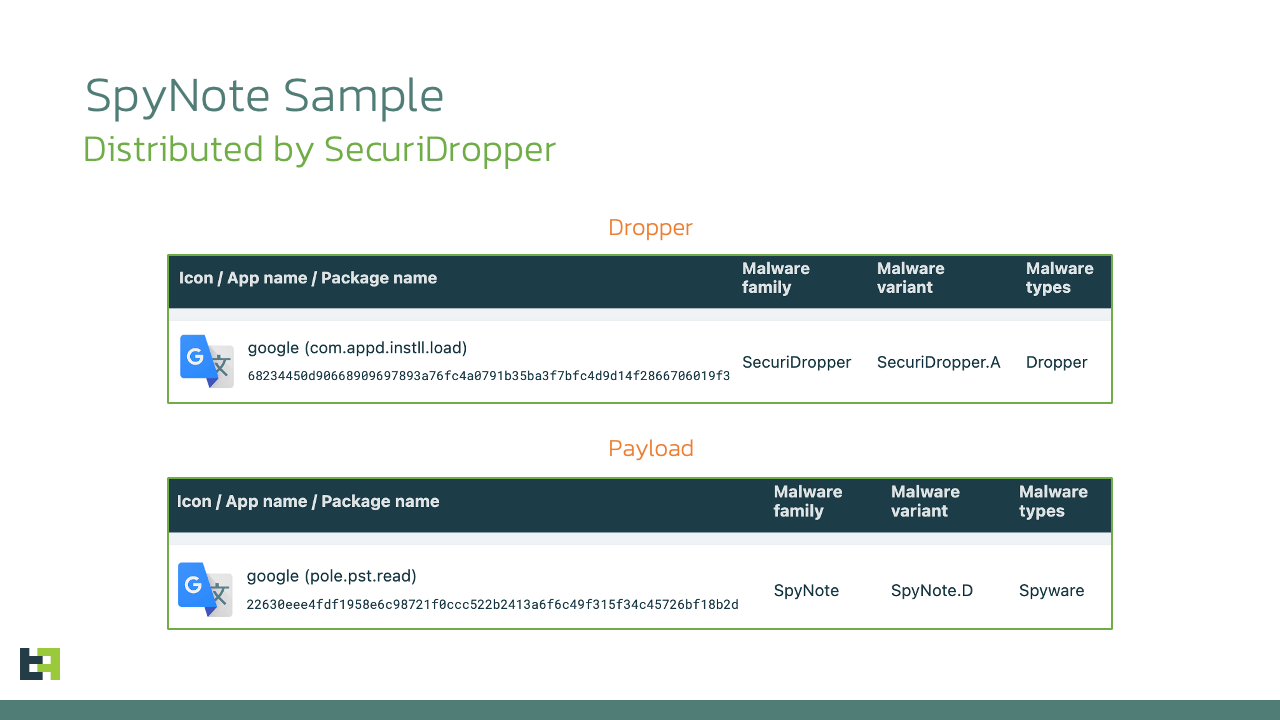
SecuriDropper Samples
HASH (SHA256)
APP NAME
PACKAGE NAME
68234450d90668909697893a76fc4a0791b35ba3f7bfc4d9d14f2866706019f3
Google
com.appd.instll.load
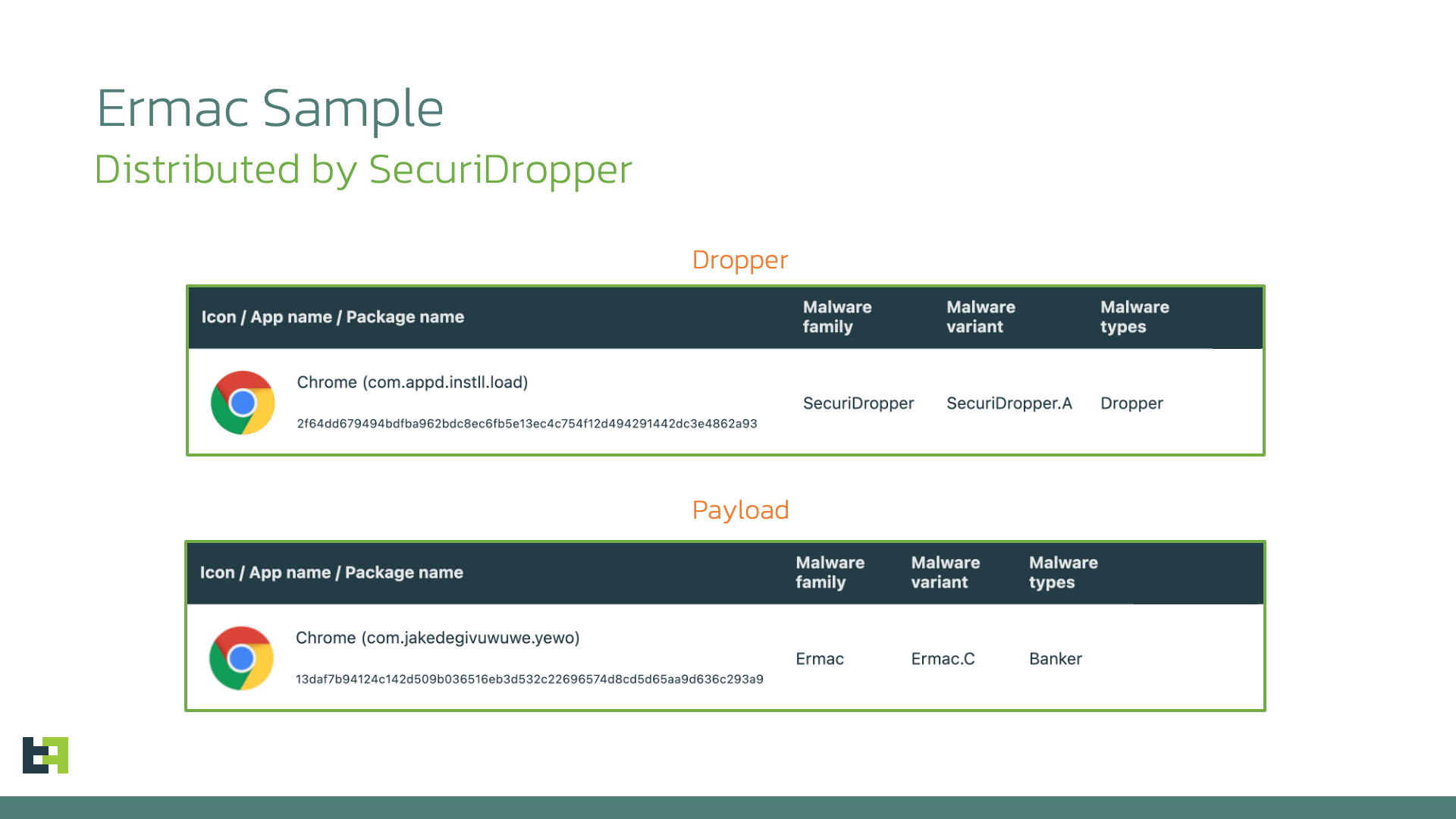
2f64dd679494bdfba962bdc8ec6fb5e13ec4c754f12d494291442dc3e4862a93
Chrome
com.appd.instll.load
Dropped Payload Samples
SpyNote.D
HASH (SHA256)
APP NAME
PACKAGE NAME
22630eee4fdf1958e6c98721f0ccc522b2413a6f6c49f315f34c45726bf18b2d
Google
pole.pst.read
Ermac.C
HASH (SHA256)
APP NAME
PACKAGE NAME
13daf7b94124c142d509b036516eb3d532c22696574d8cd5d65aa9d636c293a9
Chrome
com.jakedegivuwuwe.yewo
如有侵权请联系:admin#unsafe.sh