2023-11-6 19:43:9 Author: lab.wallarm.com(查看原文) 阅读量:6 收藏
Gaining Insight: The Imperative for an Electronic Threat Handling Framework
As we traverse further into the digital era, the threat of cyber encroachments elevates consistently. This looming risk is a reality for all, from emergent startups to well-established corporations, placing operations in jeopardy and potentially causing unrepairable damage. Here is where an Electronic Threat Handling Framework (ETHF) becomes critical. In the occurrence of a cyber break-in or a security breach, together known as an 'event', the ETHF delivers a detailed mitigation plan. ETHF empowers businesses to tackle the crises effectively, decrease the aftermath, expedite recovery, and reduce costs, thereby, aiding in the protection of the brand's image.
The imperative for an Electronic Threat Handling Framework is beyond argument. A report by the Ponemon Institute revealed that the average global cost of a data violation in 2020 reached a shocking $3.86 million. This alarming figure underscores the financial hazards of operating without an ETHF. Simultaneously, the identical report unveils that enterprises utilizing both, an ETHF alongside a proficient threat management crew, faced $1.23 million less in typical data violation expenses contrasted to those deprived of these provisions.
<code class="language-python"># Sample cost calculation
expenses_without_ETHF = 3.86 # in millions
expenses_with_ETHF = 3.86 - 1.23 # in millions
potential_economies = expenses_without_ETHF - expenses_with_ETHF
print(f"Potential economies with an ETHF: ${potential_economies}
million")</code>
This simplistic Python script exemplifies the financial gains an organization could accomplish by adopting an ETHF.
| Financial Aftermath | Without ETHF (in million $) | With ETHF (in million $) | Prospective Economies (in million $) |
|---|---|---|---|
| Data Violation | 3.86 | 2.63 | 1.23 |
Additionally, an ETHF is paramount in bolstering consumer confidence. Following a data violation, customers expect a solid resolution strategy from the company to rectify and prevent similar future dilemmas. A thoughtfully designed ETHF can deliver this comfort, hence defending the company's reputation even amid tough times.
In short, an Electronic Threat Handling Framework should be a pivotal component of any corporation's cyber defense strategy. It provides invaluable direction during cyber disasters, assists in minimizing financial toll, and aids in maintaining customer trust. In subsequent segments, we'll explore the specificities of what constitutes a 'cybersecurity event,' fathom why an ETHF is crucial, and suggest guidelines for implementing a solid ETHF. We'll also discuss the significance of threat awareness in event handling and use a case scenario to elucidate the nuances of managing events in real-world settings. Lastly, we will discuss how to keep your ETHF flexible to adapt to emerging cyber threats.
Unveiling the Concept of a 'Digital Security Occurrence'
Venturing into the realm of digital protection, the term 'occurrence' embodies a unique connotation. It signifies any event that could potentially risk the integrity of an institution's virtual assets or proprietary intel. This scope ranges from minor disruptions such as an unexpected service interruption to major infringements involving exposure of confidential client data. Grasping the idea of a digital security occurrence is foundational for curating an effective response strategy for managing these situations.
Digital security occurrences can be loosely categorized into two primary classifications, primarily, safeguarding occurrences and confidentiality occurrences.
Safeguarding occurrences represent instances that compromise the protective barriers and preventive measures instituted by a company. This includes varied events such as unauthorized infiltration into a network, an intrusive malware assault, or an overwhelming traffic attack disrupting service availability.
On the other hand, a confidentiality occurrence is typified by illicit acquisition, alteration, exposure, or eradication of confidential data. Scenarios that can spawn such occurrences include data breaches, baiting attacks, or threats stemming from inside the company.
The accompanying graphic provides a more detailed dissection of the differences between safeguarding and confidentiality occurrences:
| Facet of Occurrence | Safeguarding Occurrence | Confidentiality Occurrence |
|---|---|---|
| Explanation | Violation of security procedures | Illegal activities focused on personal data |
| Illustrations | Illegitimate network access, malware swoop, service disruption | Data infringement, baiting scheme, internal risk |
Let's explore the usual sorts of occurrences prevalent in the sphere of digital protection:
-
Illegitimate Network Penetration: This scenario transpires when an unauthorized user manipulates a loophole in the network or uses pilfered credentials to infiltrate a network or system.
-
Perilous Code Assault: This relates to the software designed to disrupt the operation of a network or system. Examples encompass viruses, worms, trojans, ransomware, and spyware.
-
Service Ambush: In this situation, a perpetrator overwhelms a network or system with exorbitant incoming traffic, rendering it unusable for users.
-
Data Infringement: This occurrence pertains to unsolicited access and disclosure of integral and sensitive data such as credit card information, identity numbers, or health-related intel.
-
Baiting Scheme: This type of attack involves the perpetrator tricking the target into disclosing sensitive data like usernames or card details under the pretence of being a reliable party.
-
Internal Risk: This type of digital occurrence happens when an individual with system access misuses their privilege to inflict damage either intentionally or inadvertently.
Consider the following basic Python script to comprehend how an occurrence might be logged within a security system:
<code class="language-python">class Occurrence:
def __init__(self, kind, summary, impact):
self.kind = kind
self.summary = summary
self.impact = impact
occurrence1 = Occurrence("Illegitimate Network Penetration", "An
unrecognized IP address was discovered penetrating the system", "High")</code>
In this instance, an illegitimate network penetration occurrence is documented, 'High' impact signifies the gravity of the situation and a brief summary provides more insight into the situation.
In concluding, understanding the constituents of a digital security occurrence is essential for identifying potential hazards that an organization might encounter. Furthermore, it lays the groundwork for formulating a poignant occurrence response plan. A lucid understanding of the different occurrence types and their potential impacts equips companies to more accurately anticipate, prepare, and respond to these threats.
Innovating a Harmonized Course for Cybersecurity Tactics

Formulating a robust cybersecurity initiative is a pivotal stride in shielding a company's digital wealth. This initiative illuminates the strategies to deploy when facing a cyber vulnerability, facilitating swift and potent solutions. Crafting such a cybersecurity initiative requires an exhaustive understanding of numerous key architectural models. This section delves into these vital elements required to shape such a scheme.
Deconstructing the NIST SP 800-61 Directives
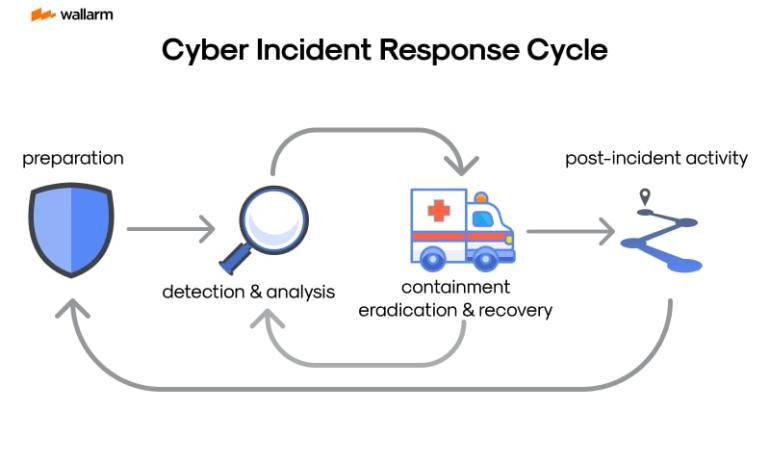
The NIST SP 800-61, sanctioned by the National Institute of Standards and Technology, offers a requisite blueprint for a methodical response to digital discrepancies, from their identification to post-anomaly processes.
This blueprint condenses this process into:
-
Readiness Step: This includes establishing a sturdy mechanism to respond to cyber abnormalities, bringing together experts to manage incidents, setting up a protected communication grid, and initiating comprehensive training modules.
-
Recognition and Estimation Phase: This step involves identifying cyber infringements, verifying them via in-depth scrutiny, and evaluating them based on their danger magnitude.
-
Correction, Eradication, and Reconstruction Stage: This entails confronting the discrepancy through segmentation to mitigate impact, investigating the origin for its elimination, and reinstating the standard functioning of the affected systems.
-
Exploration Phase: The concluding step involves an intricate review of the aftermath of the discrepancy, applying the insights obtained and instigating modifications to stave off similar future instances.
`
`
Navigating through the ISO/IEC 27035's Prescribed Directives
The ISO/IEC 27035 norms, collectively framed by the International Organization for Standardization and the International Electrotechnical Commission, present another significant structure for deploying an insightful and systematic response for incident management. This encompasses detecting, documenting, assessing, controlling, and drawing lessons from these deviations.
This structure divides into five key stages:
-
Tactical Planning and Resource Mobilization: This involves drawing up an incident response blueprint and a detailed agenda, appointing roles, and obtaining necessary apparatus for incident handling.
-
Discovery and Archiving: This includes tracking and documenting all security discrepancies and potential susceptibilities.
-
Evaluation and Countermeasures Drafting: This includes determining if an occurrence is labelled an incident according to the directives and, if so, ranking them and devising a counterplan.
-
Revitalizing Measures: This executes strategies to diminish, annihilate, and recover from the incident.
-
Post-Mission Review: The concluding stage includes an in-depth reevaluation of the incident-handling framework, refining it based on the assimilated insights.
Decoding SANS Institute's Detailed Manual for Incident Handling

The SANS Institute offers a utilitarian manual providing a phase by phase method in addressing cyber risks, initiating from readiness to post-incident examination. This manual splits into six portions:
-
Anticipation Stage: This includes readying the organization to efficiently tackle potential digital anomalies.
-
Identification Phase: Comprises pinpointing and cataloging looming threats.
-
Segregation Stage: Concentrates on physically or digitally distancing the anomaly to impede further damages.
-
Elimination Phase: Refers to the complete obliteration of the incident's source.
-
Restoration Stage: Considers managing the return to normal operations.
-
Examination Phase: The final phase involves reflective evaluation of the incident and the remediation tactics used, followed by implementing necessary enhancements.
Significantly, these structured methods are suggestions and not universal fixes. Every company's strategy to safeguard its cyber resources should be specifically tweaked to resonate with its unique necessities.
In subsequent sections, we will delve more into devising a practical digital security plan by using these frameworks as a foundational structure.
Detailed Guidelines for Crafting Your Security Incident Tactic Plan
Formulating a well-devised scheme for handling security breaches is crucial in protecting your company's digital assets. This chapter will guide you in tailoring an effective blueprint to address security incidents and significantly decrease the consequences of a potential information leak by following a sequence of meticulously chosen steps.
Action Step 1: Lay the Groundwork
The first phase in developing a security breach management plan is preparation. It entails an in-depth understanding of your company's technological environment, pinpointing possible security threats, and assigning tasks and responsibilities within the team tasked for handling incidents.
<code class="language-python"># An example of how to delegate tasks and responsibilities
class BreachResponseGroup:
def __init__(self, post, duty):
self.post = post
self.duty = duty
group_member = BreachResponseGroup('Cybersecurity Analyst', 'Scrutinize and
decipher security alerts')
print(group_member.post)
print(group_member.duty)</code>
Action Step 2: Pinpoint the Incident
Navigating towards the detection of the occurrence is vital. This step entails closely watching and analyzing security warnings to identify any out-of-the-ordinary activities.
<code class="language-python"># An example of how to spot incidents
class RecognizedIncident:
def __init__(self, alert, reaction):
self.alert = alert
self.reaction = reaction
recognized_incident = RecognizedIncident('Erratic server load',
'Anomalous network traffic')
print(recognized_incicent.alert)
print(recognized_incident.reaction)</code>
Action Step 3: Curb the Damage
Upon recognizing the occurrence, the following step is to isolate it. This phase is about restricting the breached system to prevent the incident from causing further damage.
<code class="language-python"># An example of how to isolate incidents
class DamageLimitation:
def __init__(self, unit, procedure):
self.unit = unit
self.procedure = procedure
limit_damage = DamageLimitation('Server X', 'Sever network connection')
print(limit_damage.unit)
print(limit_damage.procedure)</code>
Action Step 4: Eliminate the Danger
After restraining the event, the next procedure is complete removal. The assigned team should purge the danger from the system and revert it to the pre-incident condition.
<code class="language-python"># An example of how to neutralize danger
class DangerNeutralization:
def __init__(self, unit, procedure):
self.unit = unit
self.procedure = procedure
neutralize_danger = DangerNeutralization('Server X',
'Delete detected malware')
print(neutralize_danger.unit)
print(neutralize_danger.procedure)</code>
Action Step 5: Reinstate the System
The last stage in the security breach management scheme is recovering operations. This phase deals with resuming the system to its usual state and being on constant alert for signs of a recurring incident.
<code class="language-python"># An example of systemic recovery
class SystemRecuperation:
def __init__(self, unit, procedure):
self.unit = unit
self.procedure = procedure
recover_system = SystemRecuperation('Server X',
'Resume routine operations')
print(recover_system.unit)
print(recover_system.procedure)</code>
In conclusion, constructing a strategy for dealing with security incidents requires thoughtful synthesis of steps to effectively control and limit the negative aftermath of an information leak. Commitment to these action stages strengthens your company's resilience against unforeseen cybersecurity threats.
Unscrambling the Significance of Hazard Cognition in Handling Security Incidents
The importance of hazard cognition in effectively handling security incidents is extremely crucial. This essential information serves as a guidebook for establishments to discover, examine, and systematically structure system vulnerabilities. The interweaving of hazard awareness into your incident administration strategy furnishes your enterprise with an advantage in addressing digital misdemeanors proactively.
Understanding Hazard Cognition
The core of conscious hazard decision-making involves gathering and evaluating data about likely or current digital threats and unacceptable web behavior. By minutely examining their plans, maneuvers, and operations, it becomes manageable to reveal the roots of prospective digital incursions and suppress them successfully.
Multiple avenues contribute toward a comprehensive understanding of hazard cognition. These encompass Open-source Intelligence (OSINT), sector-specific hazard alerts, alike industry data, and intelligence willingly shared within businesses or cyber defense communities.
Understanding the Influence of Hazard Cognition in Incident Management
- Hazard Identification and Arrangement: Hazard cognition supports in discovering likely dangers, classifying them based on their effect and possibility of happening. This enables organisations to focus their resources on managing the most severe hazards.
<code class="language-python"># Sample code to organize hazards based on potential
disruption and odds of occurrence
hazards = [{'name': 'Hazard X', 'effect':
'High', 'odds': 'High'},
{'name': 'Hazard Y', 'effect':
'Medium', 'odds': 'Low'},
{'name': 'Hazard Z', 'effect':
'Low', 'odds': 'High'}]
# Organize the hazards based on potential disruption and odds
arranged_hazards = sorted(hazards, key=lambda x: (x['effect'],
x['odds']), reverse=True)
print(arranged_hazards)</code>
-
Analysis of Incidents: Hazard cognition endows comprehensive understanding of the procedures, tactics, and stratagems of possible dangers, steering incident specialists in understanding the complexities and potential outcomes of cyber infiltrations.
-
Development of Incident Strategy: With an extensive understanding of the hazard landscape, businesses can devise functional planning to administer incidents. This strategy involves detecting necessary resources, technologies, and procedures to mitigate the risk.
-
Post-Incident Review and Learning from Experience: Following a security compromise, hazard cognition supports in gaining from organizational mishaps and identifying solutions to avoid similar errors in the future. It also presents insights into developing hazard trends and evolving adversary tactics.
Incorporating Hazard Cognition into Incident Management
To seamlessly weave hazard cognition into your incident administration strategy, follow these steps:
-
Defining Relevant Hazard Cognition Sources: Pinpoint the best relevant sources of conscious hazard decision-making inherent to your company. This could include alike industry data, hazard alerts, OSINT, or intelligence circulated within fellow businesses.
-
Building a Hazard Cognition Team: Delegate a dedicated group for aggregating, scrutinizing, and disseminating hazard cognition data. This team should operate concurrently with the incident management team.
-
Infusing Hazard Awareness into Incident Management Procedures: Braid hazard understanding into all facets of the incident administration process, starting from identification to inspection, response, and post-incident analysis.
-
Consistent Review and Assessment of Hazard Cognition: Given the dynamic nature of web threats, frequent revision and evaluation of your hazard cognition are essential for its effectiveness and precision.
In conclusion, hazard cognition serves as a leading tool in incident management, equipping businesses with the insight necessary to proficiently identify, evaluate, and counter attacks. By amalgamating hazard cognition with your incident administration strategy, you can boost your company's robustness against digital infringements.
Case Analysis: Nuances of a Security Reaction in Motion
In this section, we'll explore an actual instance to shed light on the intricacies of a security response in motion. We'll study the notorious "XYZ Corporation" data compromise as our case analysis. This incident demonstrates how the absence of a comprehensive security reaction strategy can trigger disastrous outcomes.
The XYZ Corporation, a prominent banking entity, fell prey to a complex cyber-assault causing the pilferage of confidential customer information. The violation was only discovered several months post the initial breach, underlining the necessity of prompt discovery and action.
Primary Discovery:
The intrusion was initially spotted when an outside cybersecurity company noticed irregular operations emanating from XYZ Corporation's system. The company flagged this to the Corporation, which then launched a company-wide scrutiny.
<code class="language-python"># Primary discovery code sample
def spot_violation(network_communication):
for communication in network_communication:
if 'irregular' in communication:
return True
return False</code>
Prevalence Evaluation:
XYZ's cybersecurity unit dissected the violation and found that the culprits had gained entry via a fraudulent electronic mail. This message deceived an employee who revealed their access credentials, which the culprits subsequently utilized to infiltrate the network.
<code class="language-python"># Prevalence evaluation code sample
def evaluate_violation(violation_origin):
if 'fraudulent_email' in violation_origin:
return 'Employee Access Breach'
return 'Source Undetermined'</code>
Restriction and Neutralization:
The team next moved to restrict the violation and neutralize the hazard. Affected systems were quarantined, all user access keys were changed, and the destructive software was eliminated from their network.
<code class="language-python"># Restriction and neutralization code sample
def restrict_violation(attacked_systems):
for system in attacked_systems:
system.quarantine()
return 'Violation Restricted'
def eliminate_hazard(network):
network.expel_malware()
return 'Hazard Neutralized'</code>
Restoration:
The restoration procedure involved reviving the attacked systems and confirming their security. The corporation also had to inform the impacted customers and propose credit tracking services.
<code class="language-python"># Restoration code sample
def revive_systems(attacked_systems):
for system in attacked_systems:
system.revive()
return 'Systems Revived'</code>
Post-Assault Procedures:
Following the ordeal, the corporation undertook a deep assessment of their cybersecurity mandates and set in place a holistic security response strategy to avert such occurrences in the future.
<code class="language-python"># Post-assault procedures code sample
def scrutinize_mandates(mandates):
for mandate in mandates:
mandate.scrutinize()
return 'Mandates Scrutinized'
def execute_strategy(strategy):
strategy.perform()
return 'Strategy Executed'</code>
This case analysis underscores the urgency for a prepared security response strategy. XYZ Corporation's delayed discovery and action led to substantial financial and image harm. A solid security response plan could have alleviated these impacts.
In the forthcoming chapter, we will outline how to defend your security reaction stratagem against future uncertainties, making sure it stands strong in the face of developing cyber threats.
Trailblazing Defensive Innovations for Crisis Control: Vital Enhancements and Progressions
As we delve progressively deeper into the realm of digital technology, the threats in cyberspace grow correspondingly, with their intricacies increasing in step with developments. The continuous metamorphosis in the digital domain highlights the necessity for businesses to bolster their crisis control strategy, ensuring it remains relevant against myriad technological advancements and dynamically mutating cyber security challenges.
`
`
-
Continual Upgrades in Abilities and Learning
Being at the leading edge of defensive innovations requires continual upskilling and learning. The realm of cyber defense is continually shifting with new vulnerabilities and threats cropping up every day. It is imperative that the crisis control team stays current with advancements and techniques in cyber defense.
<code class="language-python"># Illustration of a continual upgrade plan class ContinualUpgrades: def __init__(self, team): self.team = team def improve_abilities(self, current_advancements): for participant in self.team: participant.improve_abilities(current_advancements)</code>The code snippet above illustrates a simple continual upgrade plan where members enhance their abilities based on the current advancements.
-
Regular Audit and Review Regimen
Regular audits and scrutiny of the crisis control strategy play a pivotal role in trailblazing defensive developments. The process includes simulated exercises or practice runs to measure the efficacy of the implemented strategy and highlight areas of potential improvement.
Review Method Overview Discussion-based Exercise An interactive session where team members navigate through a hypothetical challenge to gauge the strategy's effectiveness. Full-scale Rehearsal A live, scenario-dependent run that evaluates the strategy under realistic conditions. -
Adoption of Cutting-edge Technologies
The integration of trailblazing technologies like artificial intelligence (AI) and machine learning (ML) can significantly augment crisis control strategies. These advancements offer automation in threat recognition and response, reducing the time required to navigate a crisis.
<code class="language-python"># Illustration of an AI-based threat recognition system class RiskDetectionSystem: def __init__(self, ML_framework): self.ML_framework = ML_framework def determine_risk(self, data_stream): return self.ML_framework.analyse(data_stream)</code>The code snippet signifies an AI-based threat recognition system that utilizes a training module to identify risks based on analysed data traffic.
-
Alignment with Other Defense Mechanisms
Trailblazing defensive innovations within a crisis control plan calls for harmonization with other defense strategies in the organization. This harmonization leads to a more robust stance on cyber defense, strengthening the entire protective landscape within the organization.
- Defensive Barrier
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Data and Event Management System (DEMS)
-
Staying Abreast of Legislative Requirements
Legislative stipulations in cybersecurity are continuously changing. It's crucially important to stay informed about these alterations, and adjust the crisis control strategy accordingly to avoid potential legal or regulatory dilemmas.
In essence, trailblazing defensive innovations in a crisis control plan is a constant endeavor requiring regular improvement and adaptations. By staying ahead through constant upskilling, routine audits, adopting state-of-the-art technologies, aligning with other defense mechanisms, and staying current with legislative requirements, organizations can ensure their crisis control plan remains robust and vigilant even as cyber threats continue to evolve.
如有侵权请联系:admin#unsafe.sh