2023-11-8 05:21:28 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
MITRE ATT&CK is invaluable for SOC teams in understanding adversary behaviors and actions across a range of networks. This robust framework offers granular insight into various attack tactics, techniques, procedures, and threat groups, thereby enabling cybersecurity teams to bolster their defense mechanisms effectively.
Mature SOC teams depend on incident response automation tools to drastically cut down the time from threat detection to response. Utilizing D3 Security’s Smart SOAR (Security Orchestration Automation and Response) platform, enterprises can automate specific responses to various cyber threats mapped to their MITRE ATT&CK techniques. Let’s explore five examples of how Smart SOAR enables an automated response, specific to these ATT&CK techniques.
New To MITRE ATT&CK & D3FEND? Start here
MITRE ATT&CK (Adversarial Tactics, Techniques, & Common Knowledge) is a framework developed by the MITRE Corporation, encapsulating common behaviors exhibited by cyber adversaries in real-world incidents. Conversely, MITRE D3FEND focuses on defensive strategies. While ATT&CK illuminates adversary tactics, D3FEND provides a complementary perspective by spotlighting defense, thus offering a well-rounded approach to understanding and fortifying against cyber threats. For a deep dive, read our comprehensive explainer on MITRE ATT&CK and D3FEND.
Automating Incident Response to MITRE ATT&CK Techniques: 5 Examples
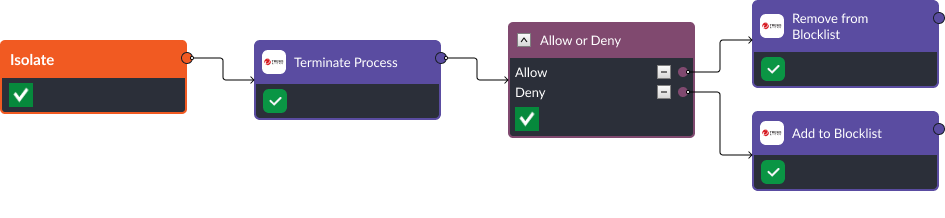
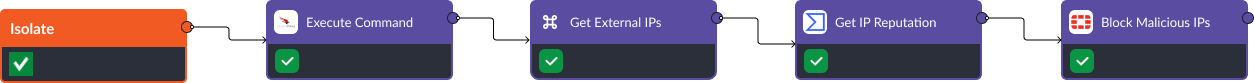
1. Brute Force Attack – T1110
Mitigating brute force attacks, where attackers attempt to gain access through relentless login attempts, demands a structured response. This blog shows you how to operationalize MITRE D3FEND’s recommendations via Smart SOAR and automate response actions during the isolate, deceive, and evict stages of a brute force attack. This includes leveraging tools like CrowdStrike for network traffic filtering, and employing Active Directory commands to create decoy credentials, invalidate authentication caches and reset passwords, ensuring a swift and robust response to such threats.
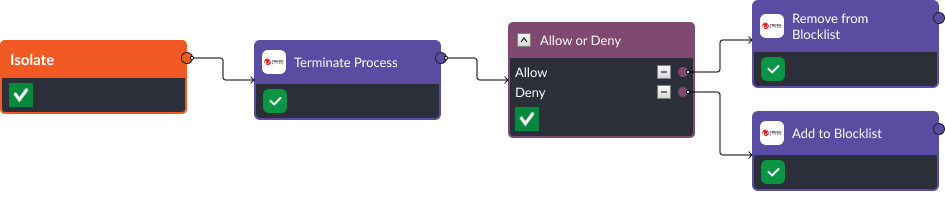
2. Command and Scripting Interpreter – T1059
Smart SOAR can be utilized to automate responses to Command and Scripting Interpreter attacks through the six stages of the MITRE D3FEND Matrix: model, harden, detect, isolate, deceive, and evict. Each stage comprises specific tasks automated by Smart SOAR, such as conducting vulnerability scans, managing file permissions, analyzing files, and handling malicious executables.
3. Scheduled Task/Job Threats – T1053
Scheduled Task/Job threats, encapsulated by MITRE ATT&CK Technique T1053, are potent attack vectors that could lead to unauthorized access, data breaches, and disruptions in critical processes. Automation, enabled by Smart SOAR, is pivotal in addressing these threats. See how we implement MITRE D3FEND recommendations across stages like Model, Harden, and Detect. For instance, in the Detect stage, Smart SOAR utilizes commands from Trellix, Okta, and Zscaler to perform comprehensive analysis like Process Spawn, Scheduled Job, and File Analysis, aiding in the thorough examination and swift response to potential threats.

4. OS Credential Dumping – T1003
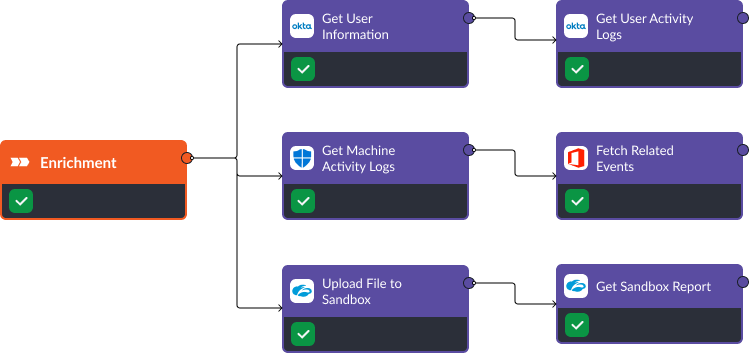
According to Elastic’s 2022 Global Threat Report, the most common method used by threat actors involves OS Credential Dumping. Mitigating OS Credential Dumping (T1003), where the attackers collect user authentication data from the operating system, necessitates a vigilant and automated approach. Utilizing Smart SOAR playbooks, triage is managed by an event playbook to ascertain the severity of alerts. In the next phase, Enrichment, the playbook gathers crucial data regarding the implicated user and device, aiding quick decision-making. In the Containment phase, steps to deactivate the malicious user and halt nefarious processes are automated, with additional measures like IP blocking. In the recovery phase, actions such as password resetting and reactivating user accounts can be orchestrated, thus restoring normalcy swiftly.
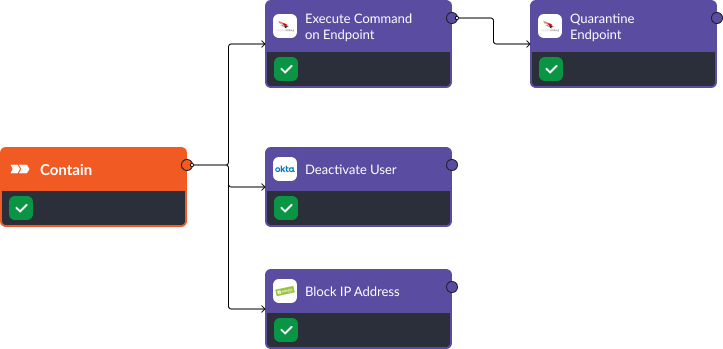
5. Phishing Attacks – T1566
Phishing attacks continue to pose a significant risk to enterprises, a situation made worse by the rise of advanced AI-driven social engineering tactics. Utilizing Smart SOAR, security teams can orchestrate and automate responses to phishing threats aligned with the MITRE ATT&CK Technique T1566. Our platform integrates effortlessly with your existing endpoint security, Identity and Access Management, and Network Security solutions. This enables automated workflows that handle everything from threat enrichment and containment to remediation and recovery. Powered by vendor-neutral playbooks, Smart SOAR ensures swift threat detection and decisive action, providing a comprehensive and proactive defense against evolving phishing strategies.
Automate MITRE ATT&CK With Smart SOAR
Leveraging Smart SOAR empowers organizations to automate incident responses to various techniques enumerated in the MITRE ATT&CK framework. Smart SOAR not only significantly condenses the timeframe from threat detection to remediation but also augments the overall defensive posture by operationalizing frameworks like MITRE D3FEND. Sign up for a demo to learn how we can help you get started with your MITRE ATT&CK automation strategy.
The post MITRE ATT&CK Technique-Driven Automation with Smart SOAR appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Shriram Sharma. Read the original post at: https://d3security.com/blog/mitre-attack-automation-with-smart-soar-examples/
如有侵权请联系:admin#unsafe.sh
