
2023-11-8 16:0:0 Author: blog.nviso.eu(查看原文) 阅读量:22 收藏
Introduction
In today’s digital environment, we encounter a mix of evolving cyber systems and the complexities they introduce. One notable influence in this space is artificial intelligence (AI), alongside associated technologies such as machine learning, which offer promising avenues for reshaping cyber strategies.
Traditionally, cybersecurity has operated with definitive parameters, set boundaries, and post-event counteractions. Yet, given the growth in digital data and the evolving nature of threats, there’s a clear shift towards strategies that are not only responsive but also proactive. AI and machine learning serve this purpose, providing defenses that are not only immediate but also predictive.
It’s important to clarify that the discussion isn’t solely about AI as a standalone term. Within this broader term are technologies like machine learning, neural networks, and deep learning, each having its significance in cybersecurity. However, given the extensive scope, our focus will be on select areas, shedding light on how these technologies function and their practical implications in cybersecurity.
The goal here is to explore the roles of AI and machine learning without presenting them as the singular answer but rather to understand their potential and limitations within cybersecurity.
For this purpose, a well-known cybersecurity framework proposed by NIST was used to understand the solution categories needed to protect, detect, react and defend against cyberattacks
R. Kaur et al., Information Fusion 97 (2023) 101804

The subsequent section provides a graphical representation that outlines specific areas in which AI and machine learning are applied in cybersecurity. These areas span from ‘Automated Security Control Validation’ to ‘Decision Support for Risk Planning’, showcasing the various types of technology that can be categorized under each domain. This visualization serves as a reference to understand the scope and classification of technologies discussed in the article.
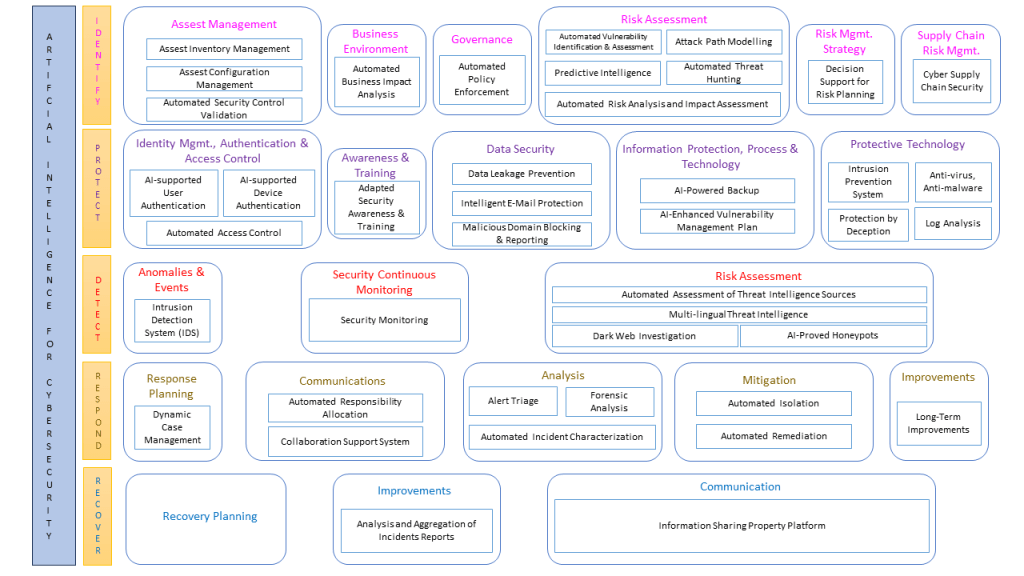
Ramanpreet Kaur, Dušan Gabrijelčič, Tomaž Klobučar,
Artificial intelligence for cybersecurity: Literature review and future research directions, Information Fusion, Volume 97, 2023
https://doi.org/10.1016/j.inffus.2023.101804.

Ramanpreet Kaur, Dušan Gabrijelčič, Tomaž Klobučar,
Artificial intelligence for cybersecurity: Literature review and future research directions, Information Fusion, Volume 97, 2023
https://doi.org/10.1016/j.inffus.2023.101804.

Ramanpreet Kaur, Dušan Gabrijelčič, Tomaž Klobučar,
Artificial intelligence for cybersecurity: Literature review and future research directions, Information Fusion, Volume 97, 2023
https://doi.org/10.1016/j.inffus.2023.101804.
In the domain of cybersecurity, while much attention has been given to Protection and Detection, there are other areas that demand attention and hold significant promise (in our case that would be Identify, Respond, Recover), especially with the advent of AI technologies. Many of these areas have been sidelined in popular discussions but are now emerging as pivotal components in the evolving cybersecurity landscape. Among these areas, we have identified several noteworthy topics:
- Automated Security Control Validation: This refers to the automated processes used to confirm that security measures are operating correctly within a given system.
- Automated Risk Analysis and Impact Assessment: A process that uses automation to evaluate potential threats and the possible consequences they could have on an organization.
- Decision Support for Risk Planning: Using technology to aid decision-makers in strategizing and planning for potential risks.
- Automated Responsibility Allocation: A method that uses automation to assign roles and responsibilities within a system, ensuring that tasks are designated to the right entity or personnel.
- Information Sharing Property Platform: A platform designed to facilitate the sharing of information across different entities in a secure manner.
The foundation of this stems from the previously cited publication, a meta study
resulted in 2395 studies, of which 236 were identified as primary. This article classifies the identified AI use cases based on a NIST cybersecurity framework using a thematic analysis approach.
https://doi.org/10.1016/j.inffus.2023.101804.
Why these topics?
In the current digital environment, businesses are required to anticipate and mitigate threats and vulnerabilities. The cyber landscape is continually changing. What was once considered secure can now be a weak point, underscoring the relevance of tools like Automated Security Control Validation and Risk Analysis. These tools enable companies to promptly detect and rectify vulnerabilities, staying abreast of the sophisticated techniques used by adversaries.
Business continuity is also crucial. Unresolved security issues can disrupt operations, affecting revenue and brand perception. Decision Support for Risk Planning offers a systematic approach for risk assessment and management, ensuring smooth operations amidst emerging threats.
Regulatory compliance adds another layer of complexity in many industries. Meeting these regulations often means implementing stringent security protocols. With updated practices such as automated responsibility allocation, companies can ensure adherence to legal requirements, minimizing legal repercussions.
As organizations grow, managing security across expansive infrastructures manually becomes complex. Automated solutions offer scalability in security, allowing businesses to expand without a corresponding rise in resources.
Information today represents a strategic asset. Platforms like an Information Sharing Property Platform could be essential, promoting a collective approach to cybersecurity, letting businesses share insights and strengthen overall security.
Building trust with customers, partners, and stakeholders is fundamental. Ensuring data security and safe interactions enhances this trust, providing a competitive advantage.
To sum up, in today’s digital world, for businesses to succeed, it’s imperative to embrace and stay updated with advanced security practices.
Evaluation of the studies under consideration
Below, we will examine each domain in detail, aiming to identify the pros and cons of employing AI and machine learning techniques, as derived from our analysis of the meta-study within the cybersecurity context.
Automated Security Control Validation
| Advantages | Disadvantages |
|---|---|
| Automated checks can be performed much faster than manual validations. | Might occasionally flag legitimate configurations as violations. |
| Perform checks uniformly without human error. | Might not always adapt swiftly to rapidly evolving threat landscapes or new security protocols. |
| Handle large infrastructures without additional resources. | Over-dependence on AI might lead to negligence in manual checks. |
| Real-time validation, ensuring immediate detection of security misconfigurations. | May not capture subtle nuances or instinctual insights that experienced human professionals might recognize in complex security scenarios. |
Automated Risk Analysis and Impact Assessment
| Advantages | Disadvantages |
|---|---|
| Process vast amounts of data rapidly, providing insights quicker. | Effective AI integration requires understanding and tuning of the models. |
| Predict potential future threats based on patterns. | Excessive trust in AI’s recommendations might overshadow human judgment. |
| Algorithms can correlate data from various sources for a more comprehensive risk profile. | Effectiveness is dependent on the quality of the data fed to it. |
Decision Support for Risk Planning
| Advantages | Disadvantages |
|---|---|
| Simulation of various risk scenarios, aiding in decision-making. | If historical data has biases, AI recommendations might inherit them. |
| Provide real-time updates based on changing data. | It might be challenging to effectively implement AI in decision-making processes. |
Automated Responsibility Allocation
| Advantages | Disadvantages |
|---|---|
| Immediate allocation of responsibilities during incidents. | AI might not understand the nuances of every situation. |
| Reduce decision-making time during crises. | Requires continuous updates to responsibility matrices and rules. |
| Decisions are based on data, not emotions or internal politics. | Sole reliance on AI might lead to issues if the system fails during a critical incident. |
Information Sharing Property Platform
| Advantages | Disadvantages |
|---|---|
| Shift through vast amounts of shared information to find relevant insights. | AI processing shared information might raise privacy issues. |
| Spot emerging threats or vulnerabilities from shared data. | Might misinterpret or take out of context certain shared information. |
| Generate summaries or insights from the shared information. | If not properly secured, AI systems could be a target for malicious actors trying to manipulate shared data. |
When examining the pros and cons presented, are there recurring themes that allow us to draw overarching conclusions? INDEED, there are!
We can identify four distinct categories:
- Speed and Data
- Understanding and Decision Making
- Adaptability and Complexity
- Security and Information
But what does each category signify, and how do they influence the broader scope of AI and machine learning in cybersecurity?
Conclusion
In the context of AI and machine learning within cybersecurity, several themes are evident:
Regarding Speed and Data, AI facilitates rapid and uniform data processing. However, it’s important to note that the quality of outcomes is contingent on the integrity of the data input, and there exists a risk of over-reliance on this speed.
In the area of Understanding and Decision Making, AI offers expansive views, promoting more objective decision-making processes. Yet, AI systems might not always replicate the nuanced understanding characteristic of human cognition.
Within Adaptability and Complexity, AI’s strength lies in its scalability and its ability to model diverse scenarios. Nevertheless, these systems can face challenges adapting to rapid technological changes, and their deployment can be intricate.
For Security and Information, AI’s capability for real-time monitoring allows for immediate threat detection. However, the speed of processing might increase the probability of misinterpretations, potentially introducing security vulnerabilities.
In addition to these themes, the Human Factor remains pivotal. AI systems, despite their sophistication, cannot replace human judgment, especially in ambiguous situations that require intuitive reasoning. The human element brings a unique combination of experience, intuition, and ethical consideration, aspects that AI currently cannot replicate fully. Hence, while automating processes can enhance efficiency, the human oversight ensures that decisions align with organizational values and the broader context. Balancing the capabilities of AI with human expertise optimizes the cybersecurity framework, ensuring robustness and adaptability.
Overall, while AI and machine learning bring substantial advantages to cybersecurity, it’s crucial to consider their inherent limitations and dependencies.

Maurice Striek
Maurice Striek is a Consultant in the Cyber Security & Architecture Team (CSA) at NVISO. His expertise lies in risk analysis based on IT-Grundschutz and ISO 27001/2 standards, as well as data analysis and data management.
如有侵权请联系:admin#unsafe.sh