测试一下GitHub公开的Windows系统提权漏洞,github连接
https://github.com/apt69/COMahawk/该漏洞利用项目使用了二个CVE编号,我们使用SHC-Update漏洞数据订阅分析工具提取CVE-2019-1405和CVE-2019-1322漏洞公开信息。
CVE-2019-1405漏洞时间梳理漏洞创建时间:2019-01-01 0:00:00漏洞披露时间:2019-11-12 19:15:00漏洞修改时间:2023-10-06 17:13:27
CVE-2019-1322漏洞时间梳理漏洞创建时间:2019-01-01 0:00:00漏洞披露时间:2019-10-10 14:15:00漏洞修改时间:2023-10-06 16:21:03
漏洞简要分析第一个漏洞CVE-2019-1405是COM服务中的一个逻辑错误,可让本地普通用户以LOCAL SERVICE身份执行任意命令。第二个漏洞CVE-2019-1322是一个简单的服务配置错误,可让本地SERVICE组中的任何用户重新配置以SYSTEM权限运行的服务(此漏洞也被其他研究人员发现)。当以上两个漏洞结合在一起时,就允许本地普通用户以SYSTEM权限执行任意命令。可以发现漏洞创建时间都是在一起的。
CVE-2019-1405影响版本["Windows 7 for 32-bit Systems Service Pack 1","Windows 7 for x64-based Systems Service Pack 1","Windows 8.1 for 32-bit systems","Windows 8.1 for x64-based systems","Windows RT 8.1","Windows 10 for 32-bit Systems","Windows 10 for x64-based Systems","Windows 10 Version 1607 for 32-bit Systems","Windows 10 Version 1607 for x64-based Systems","Windows 10 Version 1709 for 32-bit Systems","Windows 10 Version 1709 for x64-based Systems","Windows 10 Version 1803 for 32-bit Systems","Windows 10 Version 1803 for x64-based Systems","Windows 10 Version 1803 for ARM64-based Systems","Windows 10 Version 1809 for 32-bit Systems","Windows 10 Version 1809 for x64-based Systems","Windows 10 Version 1809 for ARM64-based Systems","Windows 10 Version 1709 for ARM64-based Systems","Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Core installation)","Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1","Windows Server 2008 R2 for x64-based Systems Service Pack 1","Windows Server 2008 for 32-bit Systems Service Pack 2 (Core installation)","Windows Server 2012","Windows Server 2012 (Core installation)","Windows Server 2012 R2","Windows Server 2012 R2 (Core installation)","Windows Server 2016","Windows Server 2016 (Core installation)","Windows Server version 1803 (Core Installation)","Windows Server 2019","Windows Server 2019 (Core installation)","Windows Server 2008 for Itanium-Based Systems Service Pack 2","Windows Server 2008 for 32-bit Systems Service Pack 2","Windows Server 2008 for x64-based Systems Service Pack 2","Windows Server 2008 for x64-based Systems Service Pack 2 (Core installation)","Windows 10 Version 1903 for 32-bit Systems ","Windows 10 Version 1903 for x64-based Systems ","Windows 10 Version 1903 for ARM64-based Systems ","Windows Server, version 1903 (Server Core installation) "]CVE-2019-1322影响版本["Windows 10 Version 1803 for 32-bit Systems","Windows 10 Version 1803 for x64-based Systems","Windows 10 Version 1803 for ARM64-based Systems","Windows 10 Version 1809 for 32-bit Systems","Windows 10 Version 1809 for x64-based Systems","Windows 10 Version 1809 for ARM64-based Systems","Windows Server version 1803 (Core Installation)","Windows Server 2019","Windows Server 2019 (Core installation)","Windows 10 Version 1903 for 32-bit Systems ","Windows 10 Version 1903 for x64-based Systems ","Windows 10 Version 1903 for ARM64-based Systems ","Windows Server, version 1903 (Server Core installation) "]
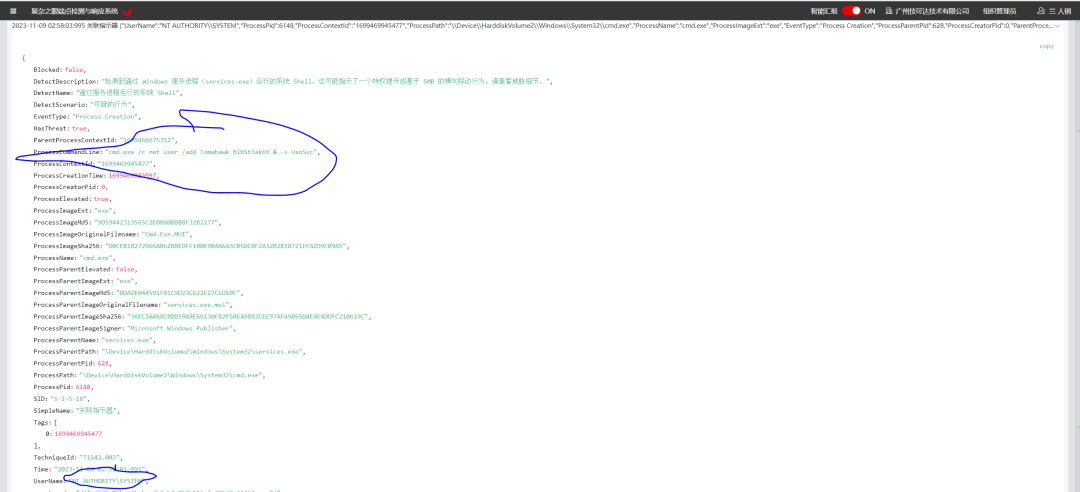
测试目标只要符合这上面的二个CVE编号影响版本条件,就可以利用成功,安装部署好复杂之眼EDR,测试的是Windows10版本1903符合利用条件,漏洞利用成功低权限用户成功添加Tomahawk账号,RibSt3ak69密码。
通过复杂之眼EDR查看触发告警,下方是CVE-2019-1405和CVE-2019-1322漏洞利用活动细节,可以看到持久化的告警添加账号。
COMahawk64.exe是CVE-2019-1405和CVE-2019-1322漏洞利用程序,可以看到执行时间和执行次数。可以看到使用事件猎手根据时间线去排查寻找该漏洞利用IOA攻击指标。
这是搭建的模拟环境真实业务生产环境,复杂之眼开启主动防御可以拦截CVE-2019-1405和CVE-2019-1322利用活动。
文章来源: http://mp.weixin.qq.com/s?__biz=MzU3NDY1NTYyOQ==&mid=2247485780&idx=1&sn=4e518ee8d47415ec8ad35b6d40d62884&chksm=fd2e54b6ca59dda051cfde1dea33d084028f9fc1b1f2be5ae7a2ab7e57ce2e05c2152b2eed93&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh