
2023-11-9 06:47:40 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
Learn the signs of an APT Attack
In today’s digital landscape, the threat of cyberattacks looms larger than ever. But not all cyber threats are created equal. Advanced Persistent Threats (APTs) are a unique breed of cyberattacks that are stealthy, sophisticated, and potentially devastating. Recognizing the signs of an APT attack is not just important—it’s imperative. In this guide, we’ll uncover the signs of an Advanced Persistent Threat Attack that you simply can’t afford to ignore.
This post outlines the severity of Advanced Persistent Threats (APTs), sophisticated cyberattacks that target networks stealthily over long periods.
It details APT characteristics, stages of attack, and emphasizes the importance of recognizing early signs, such as unusual network activity and suspicious user behavior.
Real-world APT incidents, including the Sony Pictures and Operation Aurora attacks, are cited to illustrate their potential damage.
The article advises on preventative measures like software updates, employee training, and technical defenses like firewalls and antivirus software.
Speed in identifying and responding to APTs is highlighted as critical to minimizing their impact.

The Rising Threat Landscape: Why APTs are Different
In an era where cyber threats are not just frequent but increasingly sophisticated, understanding the nuances is crucial. While ransomware and phishing attacks make headlines, Advanced Persistent Threats (APTs) lurk in the shadows, often going unnoticed until it’s too late.
So, what sets APTs apart? Unlike other cyber threats that aim for quick gains, APTs are long-term, highly strategic attacks. They’re orchestrated by skilled adversaries, often backed by substantial resources, be it criminal organizations or nation-states. Their goal isn’t just immediate financial gain but often involves data exfiltration, espionage, or even sabotage.
Moreover, APTs are incredibly stealthy. They can infiltrate a network and remain undetected for months, or even years, continuously evolving to bypass security measures. This makes them particularly dangerous for small businesses that may not have the resources for advanced cybersecurity measures.
In summary, while all cyber threats pose risks, APTs are in a league of their own. Their long-term nature, high-level backing, and stealthy tactics make them a unique and formidable threat that requires specialized attention and action.
The Rising Threat Landscape: Why APTs are Different
In an era where cyber threats are not just frequent but increasingly sophisticated, understanding the nuances is crucial. While ransomware and phishing attacks make headlines, Advanced Persistent Threats (APTs) lurk in the shadows, often going unnoticed until it’s too late.
So, what sets APTs apart? Unlike other cyber threats that aim for quick gains, APTs are long-term, highly strategic attacks. They’re orchestrated by skilled adversaries, often backed by substantial resources, be it criminal organizations or nation-states. Their goal isn’t just immediate financial gain but often involves data exfiltration, espionage, or even sabotage.
Moreover, APTs are incredibly stealthy. They can infiltrate a network and remain undetected for months, or even years, continuously evolving to bypass security measures. This makes them particularly dangerous for small businesses that may not have the resources for advanced cybersecurity measures.
In summary, while all cyber threats pose risks, APTs are in a league of their own. Their long-term nature, high-level backing, and stealthy tactics make them a unique and formidable threat that requires specialized attention and action.
What Exactly is an Advanced Persistent Threat?
An Advanced Persistent Threat (APT) is a prolonged, targeted cyberattack where an intruder gains unauthorized access to a network and remains undetected for an extended period. Unlike other cyber threats that are often opportunistic, APTs are highly coordinated and specifically target organizations for strategic objectives, such as data theft, espionage, or sabotage.
Unique Characteristics of APTs
- Prolonged Duration: APTs can last for months or even years, allowing attackers to dig deep into the network.
- Highly Targeted: These attacks are usually aimed at organizations or entities with high-value information.
- Resource-Backed: Often supported by well-funded organizations or nation-states.
- Stealthy Tactics: APTs use advanced techniques to remain undetected, often leveraging zero-day vulnerabilities.
- Multi-Stage Attacks: APTs don’t happen in one go; they’re a series of coordinated attacks.
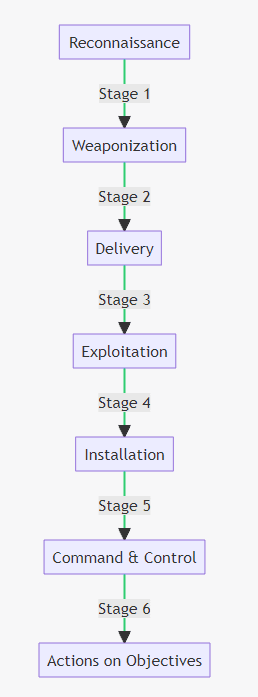
The Cyber Kill Chain
To understand the lifecycle of an APT, it’s useful to refer to the Cyber Kill Chain model, illustrated in the flowchart below. This model breaks down the stages of a cyberattack into seven steps: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command & Control, and Actions on Objectives. Each stage represents a critical point where the attack can be detected or stopped, offering multiple opportunities for defense.
By understanding what an APT is, its unique characteristics, and the stages it goes through as per the Cyber Kill Chain, you’re better equipped to identify and defend against these insidious threats.
Signs of an Advanced Persistent Threat Attack
Recognizing the signs of an Advanced Persistent Threat (APT) attack is crucial for timely intervention. Unlike other cyber threats that make their presence known almost immediately, APTs are masters of disguise. Here are key indicators that suggest you might be under an APT attack:
Unusual Network Activities
Keep an eye out for abnormal patterns in network traffic. This could include unusual data transfers, especially to foreign IP addresses, or an increase in encrypted traffic that doesn’t align with typical business operations.
Suspicious User Behavior
Watch for accounts that are accessing files or running commands they typically wouldn’t. Multiple failed login attempts or the sudden escalation of user privileges can also be red flags.
Data Anomalies
Unexplained modifications or deletions of data, especially in large volumes, can be a sign. Also, look for unauthorized data exports or unusual times of activity.
Unusual Server Communications
Check for servers communicating with external IPs in a pattern that doesn’t align with normal behavior, especially if the communication is encrypted.
Indicators of Compromise (IoCs)
These are technical artifacts or traces that point to an intrusion. Examples include unfamiliar files or scripts stored on a system, or unexpected packets captured during network traffic analysis.
By staying vigilant and monitoring for these signs, you can catch an APT attack in its tracks, potentially saving your organization from significant harm.
Real-world Examples of APT Attacks
Understanding the theoretical aspects of APTs is crucial, but real-world examples can drive the point home. Here are two notable instances where APTs wreaked havoc:
1. Sony Pictures Entertainment (2014)
In 2014, Sony Pictures fell victim to an APT attack, allegedly orchestrated by North Korea. The attack led to the leak of unreleased films, confidential emails, and sensitive employee data. The motive was to prevent the release of a film that portrayed North Korea’s leader in a negative light. The resulting impact was financial losses estimated at $15 million in the initial months.
2. Operation Aurora (2010)
Google and several other companies were targeted in an APT attack originating from China. The aim was to gain access to intellectual property and sensitive data. The resulting impact was the theft of source code. User accounts were also compromised. There was also a significant hit to the companies’ reputations.
These examples underscore the severe impact APTs can have, not just in terms of financial loss but also reputational damage and potential geopolitical consequences.
How APTs Penetrate Your Defenses
Understanding how APTs breach security measures is crucial for fortification. The ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) model by MITRE serves as a comprehensive guide to the tactics and techniques employed by APTs. Here’s how these threats commonly infiltrate:
Phishing Emails
A prevalent tactic documented in the ATT&CK model, phishing emails often contain malicious attachments or links that install malware when opened.
Zero-Day Vulnerabilities
The ATT&CK model highlights the use of zero-day vulnerabilities—unknown security flaws exploited by APTs to gain unauthorized access.
Social Engineering
Also covered in the ATT&CK framework, social engineering involves attackers posing as trusted individuals to trick employees into revealing sensitive information.
Insider Threats
The threat can sometimes come from within, a tactic that the ATT&CK model also acknowledges. Disgruntled or malicious employees can facilitate APT attacks.
Supply Chain Attacks
Infiltration through third-party vendors or software updates is another tactic documented in the ATT&CK model, compromising the entire network.
By integrating insights from the ATT&CK model, you can better understand the multifaceted tactics used by APTs, equipping you to defend your organization more effectively.
Steps to Prevent an APT Attack
There are steps one can take to prevent an APT attack. Let’s delve into each step in detail to fortify your defenses:
Regularly Update Software
Outdated software is a goldmine for attackers. Ensure all systems and applications are updated to the latest versions to patch any vulnerabilities.
Employee Training
Knowledge is power. Equip your staff with the skills to recognize phishing emails and other potential threats through regular training sessions.
Multi-Factor Authentication (MFA)
An extra layer of security can go a long way. Implement MFA to safeguard against unauthorized access.
Network Segmentation
Divide and conquer. By segmenting your network, you can contain a potential breach and prevent it from spreading.
Firewalls and Intrusion Detection Systems
Your first line of defense. Employ advanced firewalls and IDS to scrutinize incoming and outgoing network traffic.
Regular Audits
What gets measured gets managed. Conduct frequent security audits to identify vulnerabilities and take corrective action.
Data Encryption
A lock for your data. Encrypt sensitive information to protect it from unauthorized access, both in transit and at rest.
Endpoint Security
Your endpoints are entry points. Keep antivirus and anti-malware software updated on all devices connected to your network.
Access Control
Less is more. Limit user access to only the data and systems necessary for their roles to minimize risk.
Incident Response Plan
Be prepared. Have a well-documented and rehearsed incident response plan to act swiftly in case of a breach.
Monitor for Indicators of Compromise (IoCs)
Stay vigilant. Continuously monitor your network for signs that could indicate a security breach.
Consult ATT&CK Model
Knowledge is your weapon. The ATT&CK model provides invaluable insights into the tactics and techniques used by APTs. Make it a habit to consult it regularly.
By following these steps, outlined in our infographic, you’re well on your way to building a robust defense against APT attacks.

Preventing an Advanced Persistent Threat Attack
While the checklist provides a solid foundation, preventing an APT attack requires a more nuanced approach. Here’s how to go beyond the basics:
Strategic Planning
Develop a long-term cybersecurity strategy that aligns with your business objectives. This should include regular risk assessments and updates based on evolving threat landscapes.
Threat Intelligence
Invest in threat intelligence services to stay ahead of emerging threats. This proactive approach can help you adapt your defenses in real-time.
Behavioral Analytics
Utilize behavioral analytics tools to monitor for abnormal user activities, which could be indicative of an APT.
Data Loss Prevention (DLP)
Implement DLP solutions to monitor and control data transfers, ensuring sensitive information remains secure.
Red and Blue Team Exercises
Conduct simulated attack and defense exercises to identify weaknesses and improve incident response times.
Vendor Risk Management
Evaluate the security measures of third-party vendors. A weak link in your supply chain can expose your entire network.
Cyber Insurance
Consider investing in cyber insurance as a safety net for potential financial losses due to an APT attack.
Security Culture
Foster a culture of security within the organization. When every employee takes cybersecurity seriously, your defenses become more robust.
By adopting these advanced measures, you can build a more resilient defense against APT attacks, going beyond the essential steps outlined in the checklist.
Employee Education: The First Line of Defense Against APTs
Employees often serve as the first line of defense in cybersecurity. Their actions can either prevent an APT attack or inadvertently facilitate one. Here’s why educating your staff is paramount:
Human Error is a Weak Link
Even the best security systems can be compromised by simple human errors, such as clicking on a phishing link.
Awareness Reduces Risk
Educated employees are less likely to fall for social engineering tactics, reducing the risk of an insider-facilitated attack.
Quick Identification
Trained staff can quickly identify signs of an APT attack, enabling faster response times and minimizing damage.
Compliance and Regulations
Employee education is often a requirement for compliance with various data protection and cybersecurity regulations.
Empowerment
Knowledgeable employees feel empowered to take action, fostering a culture of collective responsibility for cybersecurity.
In summary, an educated workforce is a critical asset in your arsenal against Advanced Persistent Threats.
Implementing Security Measures: Your Technical Arsenal Against APTs
Technical safeguards are crucial in building a multi-layered defense strategy against APTs. Here’s a rundown of essential security measures:
Firewalls
A robust firewall acts as a barrier between your network and potential threats, filtering out unauthorized access and malicious traffic.
Antivirus Software
Antivirus software scans and removes malware, including those that could be part of an APT attack, from your system.
Intrusion Detection Systems (IDS)
IDS monitors network traffic for suspicious activities, providing an additional layer of security by alerting you to potential breaches.
Virtual Private Networks (VPNs)
VPNs encrypt internet traffic, making it more difficult for attackers to intercept sensitive data.
Data Loss Prevention (DLP) Tools
DLP solutions monitor and control data transfers, adding an extra layer of security to sensitive information.
Endpoint Protection Platforms
These solutions (EPP) provide comprehensive security for all network endpoints, from desktops to mobile devices, covering various attack vectors.
Security Information and Event Management (SIEM)
SIEM solutions aggregate and analyze activity from various resources, providing real-time analysis of security alerts.
By implementing these security measures, you’re not just ticking boxes; you’re building a fortress capable of withstanding APT attacks.
The Importance of Speed in Cybersecurity
In the realm of cybersecurity, time is of the essence. The longer an APT remains undetected, the more damage it can inflict. Here’s why speed is non-negotiable:
Early Detection Equals Less Damage
The sooner you detect an APT, the less time it has to move laterally across your network, minimizing potential damage.
Financial Implications
Every minute an APT goes undetected can cost your organization significantly, from data theft to reputational damage.
Regulatory Consequences
Quick action is often mandated by data protection laws. Failure to act swiftly can result in hefty fines and legal repercussions.
Containment and Eradication
Rapid detection enables quicker containment of the threat, preventing it from spreading to other parts of the network.
Competitive Advantage
In a market where trust is paramount, being known for robust and speedy cybersecurity can set you apart from competitors.
Understanding the critical role of speed in cybersecurity can be the difference between a manageable incident and a full-blown catastrophe.
Final Thoughts: Recognizing the Indicators of APT Attacks
In a cybersecurity landscape rife with threats, Advanced Persistent Threats (APTs) stand out for their complexity and potential for severe damage. Recognizing the signs of an APT attack—be it unusual network activities, suspicious user behavior, or data anomalies—is crucial for timely intervention.
The ATT&CK model serves as a comprehensive guide for understanding the tactics and techniques employed by APTs, emphasizing the importance of speed in detection and response. Early detection not only minimizes damage but also has financial and regulatory implications.
In summary, vigilance and quick action are your best defenses against the insidious and highly damaging nature of APTs.
The post Know the Five Signs of an Advanced Persistent Threat Attack appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/signs-of-an-advanced-persistent-threat-attack/?utm_source=rss&utm_medium=rss&utm_campaign=signs-of-an-advanced-persistent-threat-attack
如有侵权请联系:admin#unsafe.sh
