2023-11-9 16:10:52 Author: isc.sans.edu(查看原文) 阅读量:11 收藏
Code injection techniques (T1055 from MITRE[1]) is a common technique these days. It’s a nice way for an attacker to hide malicious code into a legit process. A deviation of this technique is called “Process Hollowing”[2] where code of the legit suspended process is wiped and replaced by malicious code. Code injection is performed by calling Microsoft API calls like: VirtualAllocEx(), NtUnmapViewOfSecrio(), WriteProcessMemory(), ... (they are many others available)
When I’m teaching FOR610[3], many students are wondering why such API calls are provided by Microsoft to perform so dangerous actions. Indeed, there is no “hacking magic”. Microsoft supports them. for them, it’s difficult to "see" how such program behaves.
I spotted an interesting sample that perform this technique and I was able to collect “visible” information. The malware was delivered through a phishing email with a ZIP archive. The executable is called “deposit q.exe” (SHA256:e3471a6c13327493f5d5990cce84c095e66d83a4554e01f3eb891c15750acf60[4]). The malware downloads a payload from OneDrive:
hxxps://zevjwg[.]bn[.]files[.]1drv[.]com/y4mkABT3gyR6meHkPFqKxwXcR2Dalfzc8vcJYkh2YdRSprR5BjFVj_TAYpkjpyVIUgGHpc0hmklk0uIpA41vBgPlJBZKyIOI_mZlDj5KCikTCfH9FUIzcf4Ff31dCFnHU6X9oKVeA2FYnq0_vQqOqDp8NiEOASqrG1MQuNT214kS7dkwRo_h8gzuhBnzRvXgvYr
It drops multiple files to implement persistence:
- C:\Users\\Public\Libraries\Mxgaoauk.url
- C:\Users\\Public\Libraries\Mxgaoauk.PIF
- C:\Program Files (x86)\Rs8jlix\nxvxu6jfj49.exe
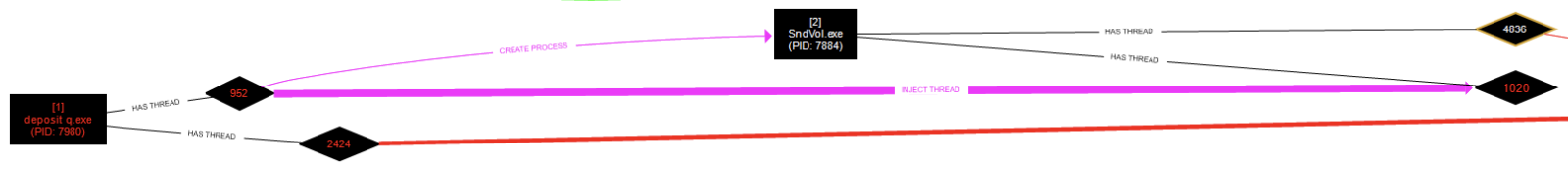
The malware creates a SndVol.exe process (the official Microsoft tool to manage audio volume on the system). Then it injects a thread into SndVol.exe as soon on the following picture (generated with ProcDOT):
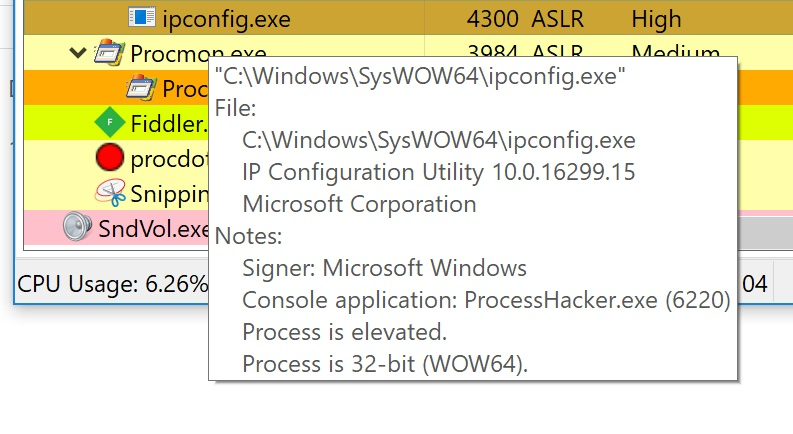
In the same sandbox, I found later the following process (ipconfig.exe), which also looks legit but it performs malicious activity:
The ipconfig.exe process is trying to contact C2 servers.
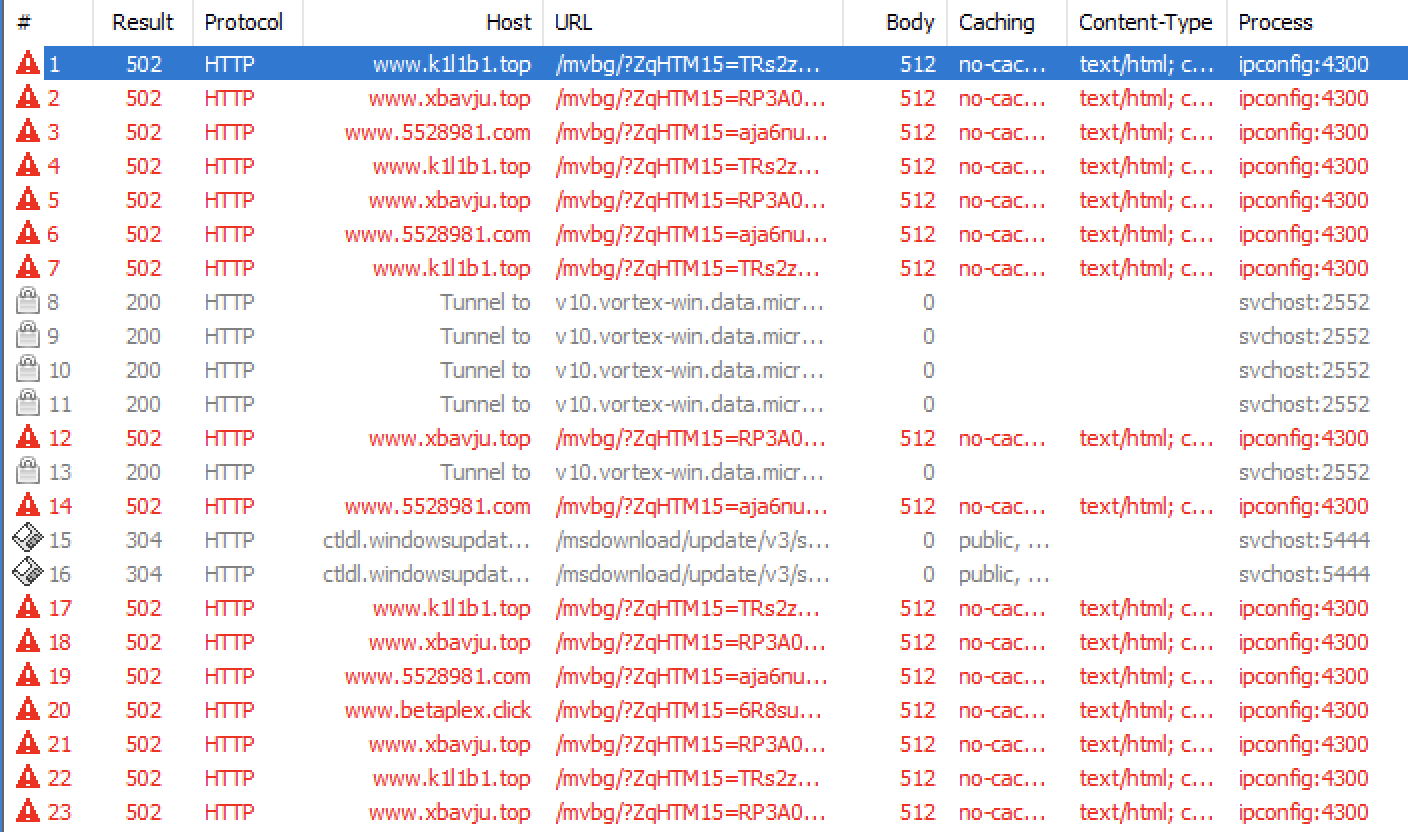
I identified the following hostnames:
- www[.]5528981[.]com
- www[.]betaplex[.]click
- www[.]grupolubriso[.]live
- www[.]k1l1b1[.]top
- www[.]xbavju[.]top
Note that injection in another (or the local) procress, can be performed from any programming languages, also scripts! I found plenty of techniques in PowerShell, Python, VBS, ...
[1] https://attack.mitre.org/techniques/T1055/
[2] https://attack.mitre.org/techniques/T1055/012/
[3] https://for610.com
[4] https://www.virustotal.com/gui/file/e3471a6c13327493f5d5990cce84c095e66d83a4554e01f3eb891c15750acf60
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
如有侵权请联系:admin#unsafe.sh