The Genesis of Apigee API Security Guidelines
In today's digital epoch, APIs (Application Programming Interfaces) have ascended to be the fundamental infrastructure underpinning software development - furnishing the medium for diverse software systems to interact and exchange data. Yet, with this escalating dependency on APIs, putting them under a robust security cover has emerged as a quandary of paramount significance. It's at this juncture where Apigee, an integral segment of Google Cloud, offers its API Security Guidelines.
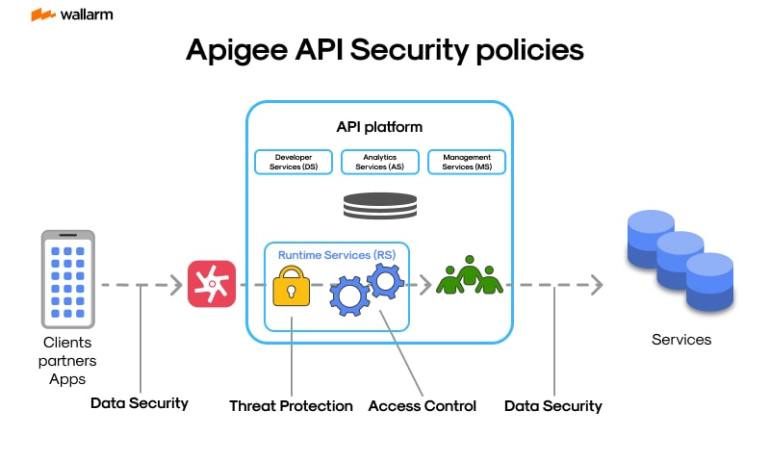
Apigee leads the vanguard in delivering a comprehensive API management solution that enables businesses to strategize, fortify, launch, observe, and augment APIs. The API Security Guidelines from Apigee come as a comprehensive safety protocol that helps shield APIs from potential threats and breaches, thereby sustaining data privacy and integrity.
Decoding the Apigee API Security Guidelines
Intentionally architected to bolster API security at all levels, Apigee API Security Guidelines come with a multitude of safety specifications:
- Traffic Regulation Guidelines: These act as the gatekeepers of API traffic, avert overload scenarios and promote seamless functioning. Fellows of this group comprise of Spike Arrest, Concurrent Rate Limit, and Quota Guidelines.
<code class="language-xml"><SpikeArrest>
<Rate>100pm</Rate>
</SpikeArrest></code>
In the above instance, the Spike Arrest guideline limits the API calls to a maximum count of 100 per minute.
- API Safety Guidelines: These buffer APIs against prevalent web assaults. Representatives cover JSON Threat Protection, XML Threat Protection, and Regular Expression Protection guidelines.
<code class="language-xml"><JSONThreatProtection name="JSON-Threat
-Protection-1">
<ArrayElementCount>100</ArrayElementCount>
<ObjectEntryCount>100</ObjectEntryCount>
<StringLength>100</StringLength>
</JSONThreatProtection></code>
The depicted JSON Threat Protection measure restricts the array elements tally, object entries, and string length to a maximum of 100.
- Arbitration Guidelines: These enable the transformation of request and response payloads. Included are JSON to XML, XML to JSON, and XSL Transformation guidelines.
<code class="language-xml"><XMLToJSON async="false"
continueOnError="false" enabled="true"
name="XML-To-JSON">
<DisplayName>XML To JSON</DisplayName>
</XMLToJSON></code>
The XML to JSON guideline shown here translates XML payloads to JSON.
- Addon Guidelines: These facilitate the integration of bespoke scripts for additional functionalities. They cover JavaScript, Python, and Java Callout guidelines.
<code class="language-javascript"><Javascript async="false"
continueOnError="false" enabled="true"
timeLimit="200" name="JavaScript-1">
<DisplayName>JavaScript 1</DisplayName>
<ResourceURL>jsc://sample.js</ResourceURL>
</Javascript></code>
In the display above, the JavaScript guideline allows the execution of a custom script derived from the given resource URL.
The Marvel of Apigee API Security Guidelines:
Comprehensive and adaptable, the Apigee API Security Guidelines extend an impressive scheme for API security shielding. They afford businesses to customize security protocols to cater to their unique requirements, thereby giving superior authority over API accessibility and use.
Moreover, implementing and managing Apigee's guidelines is straightforward with their XML-styled configuration and user-friendly interface. Coupled with seamless integration capabilities with Apigee's other services including analytics and developer portal, they make an ideal end-to-end API management solution.
As we continue to expand on our understanding in the subsequent chapters, we will delve into the essentials of Apigee API Security Guidelines, elucidate their implementation process and share optimum practices for their configuration. Stay connected!
`
`
Breaking Down the Basics of Apigee's Measures for Guarding APIs
As the World Wide Web becomes increasingly interconnected, the safety of APIs takes center stage. In this situation, Apigee, a comprehensive API stewardship tool, offers robust defensive techniques that keep your APIs shielded from potential vulnerabilities. This section aims to dissect the fundamental layers of security offered by Apigee for APIs, in an easy to understand, and execute manner.
Grasping the Concept of API Security
Protecting APIs entails blocking illegitimate uses. This includes disallowing unauthorized access, ensuring data confidentiality, and maintaining data integrity. The security parameters set by Apigee for its APIs act as a panacea for these challenges.
Understanding Security Offerings for APIs by Apigee: A Quick Overview

Security elements offered by Apigee for APIs act as guidelines or instructions dictating the conduct of APIs within the system and with end-users. Apigee develops bespoke defensive measures aimed at shielding APIs against a variety of potential risks and weaknesses. You could categorize these elements into four fundamental parts:
-
Monitoring of API Traffic: These elements focus on managing the flux of API traffic, helping to prevent potential overload on backend services. They focus on techniques such as Spike Arrest, Quota, and Concurrent Rate Limit.
-
Safety Oriented Elements: These elements strengthen the API's resilience against security-related threats. They apply methods like OAuth, API Key Validation, and JSON Threat Protection.
-
Elements Related to Extension: These elements amplify the abilities of APIs using Python Script, Java Callout, and Service Callout.
-
Elements Related to Mediation: These elements tune API feedback mechanisms and responses through techniques like JSON to XML, XML to JSON, and Assign Message.
Method to Implement Security Measures for APIs by Apigee
Executing Apigee's security measures for APIs involves integrating these elements into the API proxies, as shown below using a Spike Arrest element:
<code class="language-xml"><PreFlow name="PreFlow">
<Request>
<Step>
<Name>SpikeArrest</Name>
</Step>
</Request>
<Response/>
</PreFlow></code>
Here, the Spike Arrest element is inserted into the request process of the API proxy, 'SpikeArrest' signifies the element name in the 'Name' area.
Highlighting the Efficiency of Apigee's Measures for API Security
The secret behind Apigee's exemplary success in API security lies in its versatile and comprehensive security elements. These are adaptable to meet specific security specifications. For example, the Spike Arrest measure can be adjusted to limit the API traffic to a certain number of requests per minute:
<code class="language-xml"><SpikeArrest name="SpikeArrest">
<Rate>100pm</Rate>
</SpikeArrest></code>
Here, the Spike Arrest measure is tailored to cap API traffic at 100 requests per minute.
Proven Strategies for Implementing Security Measures for APIs by Apigee
To successfully integrate Apigee's security measures for APIs, you first need to identify your security needs and then choose the appropriate measures. Here's some advice:
-
Deploy Traffic Monitoring measures to manage API traffic and prevent possible system overloads.
-
Use Safety-Oriented measures to bolster your APIs against common security flaws.
-
Leverage Extension-Related measures to boost your APIs capabilities.
-
Utilize Mediation-Related measures to fine-tune API feedback mechanisms and responses.
-
Tailor measures to cater to specific security requirements.
Surveying Common Obstacles in Implementing Apigee's Security Measures for APIs
Common roadblocks in incorporating Apigee's security measures for APIs include incorrectly configured measures and execution errors. Examining measure configurations and monitoring their functionality can help overcome these issues.
Advancing API Defense Systems with Apigee's Security Measures
Apigee's security measures serve as the foundation for a trustworthy API defense system. By mastering the basic facets of these elements, you can build a formidable API network and set up a safe and foolproof API structure.
A Guided Tour towards Implementing Apigee API Defensive Mechanisms

This part of the instructional manual takes you on a guided journey of implementing Apigee API defensive mechanisms. Let's traverse this comprehensive walkthrough that imparts a profound understanding of fostering and overseeing your API defensive mechanisms via Apigee.
Initial Step: Unraveling Your API Defence Needs
Prior to veering towards the application of any defensive measures, the pivotal element lies in comprehending the mandatory defence strategies of your API. At the core of this understanding is recognizing the types of information your API will handle, gauging potential security risks and pinpointing the required level of defense.
Next Stage: Developing Your Apigee Platform
Having fully fathomed your API defense needs, the following step constitutes the development of your Apigee framework. This involves creating an Apigee account, organizing your foundation, and initializing an API proxy.
<code class="language-bash"># Create an Apigee account
curl -X POST https://login.apigee.com/accounts -d '{"email":
"your-email","password":"your-password"}'
# Organize your foundation
curl -X POST https://api.enterprise.apigee.com/v1/organizations -d '{"name":
"your-organization"}'
# Initialize an API proxy
curl -X POST https://api.enterprise.apigee.com/v1/organizations/your-organization/apis
-d '{"name":"your-api"}'</code>
Stage 3: Launching Security Policies
Apigee provides a substantial assortment of defensive measures that you can employ to fortify your APIs, such as:
- Spike Arrest: This measure contributes to protecting your API from traffic spikes and DoS attacks.
- OAuth: This measure empowers you to employ OAuth 2.0 validation and eligibility for your APIs.
- XML Threat Protection: This measure contributes to securing your API from XML-based risks.
- JSON Threat Protection: This measure contributes to shielding your API from JSON-based risks.
To launch a defensive measure, you need to add the specified measure to your API proxy.
<code class="language-xml"><!-- Add a Spike Arrest measure -->
<Policy>
<SpikeArrest>
<Rate>100pm</Rate>
</SpikeArrest>
</Policy>
<!-- Add an OAuth measure -->
<Policy>
<OAuthV2>
<AccessToken>your-access-token</AccessToken>
</OAuthV2>
</Policy>
<!-- Add an XML Threat Protection measure -->
<Policy>
<XMLThreatProtection>
<ElementDepth>100</ElementDepth>
</XMLThreatProtection>
</Policy>
<!-- Add a JSON Threat Protection measure -->
<Policy>
<JSONThreatProtection>
<ArrayElementCount>100</ArrayElementCount>
</JSONThreatProtection>
</Policy></code>
Stage 4: Verifying Your Security Policies
Once the defensive measures are launched, it is crucial to confirm their proper operation. This can be achieved by directing queries towards your API and analyzing the feedback.
<code class="language-bash"># Direct a query towards your API
curl -X GET https://your-api-url
# Analyze the feedback
{
"message": "Your query was successfully processed."
}</code>
Final Step: Overseeing and Fine-Tuning Your Security Policies
Upon successful deployment and operation of your defensive mechanisms, it is crucial to consistently monitor them and adjust as necessary. Apigee provides a comprehensive control suite aiding you in overseeing your API usage, witnessing stats, and fine-tuning your defensive measures.
In a nutshell, the successful application of Apigee API Defensive Mechanisms calls for a deep understanding of your API's defense requirements, building an Apigee structure, employing necessary security procedures, their validation and unrelenting monitoring and tweaking. By following these guidelines, you can assure that your APIs are shielded from any potential threats.
Revealing The Secrets of Efficiency in Apigee's API Security
Originating from the family tree of Google Cloud, Apigee offers comprehensive management across the entire API lifecycle. It equips organizations with the necessary tools to craft, safeguard, implement, oversee, and augment their APIs. The distinguishing feature of Apigee over its competitors is its impregnable security measures. They're crafted to guard APIs against potential hazards, fortify data confidentiality and uphold the integrity of the data transfer process. Curious about the secrets behind the efficiency of Apigee's API security? Let's uncover them.
- Securing through Policies
Principally, the resourcefulness of Apigee's security lies within the application of policy-based mechanisms. Flexibly reusable, policies form fragments of code that an API proxy flow incorporates to reinforce security, supervise traffic, and modify data. Below is an insulated sample of how policies might be devised in the XML format:
<code class="language-xml"><OAuthV2 async="false" continueOnError="false" enabled="true" name="OAuth-v20-1"> <DisplayName>OAuth v2.0 1</DisplayName> <ExternalAuthorization>false</ExternalAuthorization> <Operation>VerifyAccessToken</Operation> <SupportedGrantTypes/> <GenerateResponse enabled="true"/> </OAuthV2></code>
This particular policy inspects the authenticity of an access token in every OAuth 2.0 request. If the token is authenticated, the API call continues; otherwise, it discontinues.
- Array of Security Measures
Apigee supplies a multitude of security measures spanning across diversified elements of API security. These comprise:
-
Regulating Traffic policies: These guidelines oversee the API traffic, avert abuse of API, and assure service availability. They involve the Spike Arrest, Quota, and Concurrent Rate Limit policies.
-
Defensive policies: These policies shield the API from potential threats and invasions. They encompass OAuth, API Key Validation, JSON Threat Protection, and XML Threat Protection policies.
-
Mediation policies: These govern transformations in the API request and response data, including JSON to XML, XML to JSON, and XSL Transform policies.
- Adaptable Policy Integration
Apigee proposes policy integration at varying points within the API proxy flow, offering increased agility in the application of security. You can integrate a policy at the ProxyEndpoint to implement it on incoming requests or at the TargetEndpoint to apply it to outgoing requests, or anywhere in between to apply it at a distinct measure in the flow.
- Policy Linking
Apigee supports policy linking, an approach where one policy's output is repurposed as another's input. This empowers you to formulate intricate security application scenarios. Illustratively, a Quota policy can follow an OAuth policy to apply quota on authenticated OAuth requests.
- Policy Administration and Configuration
Apigee offers an intuitive interface to facilitate the configuration and management of policies. It allows you to seamlessly add, eliminate, or modify policies without meddling with the API code. This simplifies the challenges of managing API security and boosts operational efficacy.
- Policy Efficacy
The plethora of policies that Apigee provides is engineered for maximum output. They operate efficiently, ensuring a marginal effect on the API response duration. This proves essential in maintaining a reliable and prompt API service.
To wrap up, Apigee's API security efficiency primarily derives from its policy-based tactics, extensive security measures, adaptable policy integration, policy linking, straightforward policy administration, and productive execution of policies. Availing these features enables you to construct a solid and efficient security strategy for your API with Apigee.
Mastering the Configuration of Your Apigee API Protection Measures
Implementing appropriate protective procedures for your Apigee API is critical in preserving the confidentiality and accuracy of your data. However, the importance lies not only in establishing these safeguards but doing so effectively. In this chapter, let's explore the most effective strategies for configuring your Apigee API protection parameters.
- Pinpoint Your Defense Requirements
Before initiating any protective protocol, it's vital to pinpoint your defense requirements. Recognize the nature of your data, its sensitivity, and prospective hazards. This comprehension will guide you in selecting suitable protection protocols.
- Adopt OAuth 2.0 for User Verification
OAuth 2.0 is a convention that permits applications to authorize restricted access to user profiles on an HTTP service. Its popularity stems from its sturdy structure and adaptability. Apigee supports OAuth 2.0, and it's advisable to adopt it for user verification.
<code class="language-xml"><OAuthV2 async="false" continueOnError="false"
enabled="true" name="OAuthV2-1">
<DisplayName>OAuth v2.0</DisplayName>
<Operation>GenerateAccessToken</Operation>
<SupportedGrantTypes>
<GrantType>client_credentials</GrantType>
</SupportedGrantTypes>
<GenerateResponse enabled="true"/>
</OAuthV2></code>
- Engage Traffic Controlling
Traffic controlling is a method for capping network traffic. It puts a cap on the number of requests a client can pose to the API within a particular timeframe. This procedure can avert misuse and maintain your API's stability.
<code class="language-xml"><SpikeArrest async="false"
continueOnError="false" enabled="true"
name="SpikeArrest-1">
<DisplayName>Spike Arrest</DisplayName>
<Properties/>
<Identifier ref="request.header.some-header-name"/>
<MessageWeight ref="request.header.some-other-header-name"/>
<Rate>30pm</Rate>
</SpikeArrest></code>
- Apply Quota Directive
The Quota directive empowers you to cap the number of requests an app developer can pose to an API within a period. Establishing a quota directive is a smart measure to curb the over-utilization of your API.
<code class="language-xml"><Quota async="false"
continueOnError="false" enabled="true"
name="Quota-1">
<DisplayName>Quota</DisplayName>
<Properties/>
<Allow count="100" countRef="verifyapikey.Verify-API-Key.
apiproduct.developer.quota.limit" continueOnError="false"/>
<Interval ref="verifyapikey.Verify-API-Key.apiproduct.developer.
quota.interval">1</Interval>
<TimeUnit ref="verifyapikey.Verify-API-Key.apiproduct.developer.
quota.timeunit">hour</TimeUnit>
</Quota></code>
- Cipher Delicate Data
Should your API handle delicate data, it's a wise approach to cipher this information. Apigee offers the EncryptVariable directive for this objective.
<code class="language-xml"><EncryptVariable async="false"
continueOnError="false"
enabled="true" name="Encrypt-Variable-1">
<DisplayName>Encrypt Variable</DisplayName>
<Source>request.header.sensitive-data</Source>
<Target>request.header.encrypted-data</Target>
<Key>encryption-key</Key>
<Algorithm>AES</Algorithm>
</EncryptVariable></code>
- Consistently Revise and Refresh Your Protocols
Protection isn't a one-off effort; it's a sustained endeavor. Consistently revise and refresh your protection protocols to ensure how they align with the modern defense standards and risk factors.
- Keep a Close Eye on Your API
Observing your API can aid in spotting any irregular operations or possible defense risks. Apigee provides various surveillance tools for usage.
By adhering to these first-rate strategies, you can guarantee that your Apigee API protection measures are robust and effective. The objective isn't simply to create defensive measures, but to establish them proficiently.
Addressing Frequent Concerns in the Administration of Apigee API Security Protocols
Within the realm of API safety, Apigee claims a hefty reputation for being a staunch and dependable source. However, similar to other technological systems, it's not impervious to elements that might lead to complications. The intent of this chapter is to provide a comprehensive guidance to navigate routine complications that could arise while managing Apigee API security protocols and efficient strategems to rectify them.
Errors in Policy Setup
Mistakes in policy configuration are quite familiar and can originate from multitudinous reasons like incorrect XML formulation, invalid rules for policy or the absence of mandatory components.
For efficient rectification, review your policy setup to spot any syntactical mistakes. Apigee Edge includes a user-friendly XML editor that acts as a catalyst in pinpointing and rectifying these inadequacies. Additionally, verify that all essential components are incorporated and appropriately implemented.
<code class="language-xml"><OAuthV2 async="false" continueOnError="false"
enabled="true" name="OAuth-v20-1">
<DisplayName>OAuth v2.0 1</DisplayName>
<Properties/>
<Attributes/>
<ExternalAuthorization>false</ExternalAuthorization>
<Operation>GenerateAccessToken</Operation>
</OAuthV2></code>
In the demonstrated example, all essential components are incorporated and appropriately implemented.
Unsuccessful Authentication
Failure in authentication may occur if the client software fails to validate its identity to the Apigee API system. This can result from wrong client identification, expired passkeys, or client software unregistered with Apigee.
As a corrective measure, affirm the client identification details, ensuring their correctness. Keep a tab on the passkey expiry window and rejuvenate the passkey if required. If the client software is unregistered with Apigee, register it and give it another go.
Authorization Denials
Authorization denial can happen when the client software lacks permission to fetch the sought-after resource. This might be due to the software lacking access rights or the specific resource being guarded by an API security protocol.
For rectification, inspect the rights of the client software and affirm its access to the requested resources. If the resource is guarded by a safety protocol, verify that the protocol is appropriately configured and the client software holds the rights to access the resource.
Quota Breach Errors
Errors due to overflowing the quota emerge when the client software surpasses the assigned number of API requests within a specified timeframe. This is controlled by the Quota protocol in Apigee.
For addressing this, examine the Quota protocol setup and ensure it's rightly configured. If the client software is exceeding the quota, ponder on augmenting the quota or incorporating a throttling mechanism.
<code class="language-xml"><Quota name="Quota">
<Interval>1</Interval>
<TimeUnit>minute</TimeUnit>
<Allow count="100"/>
<Distributed>true</Distributed>
<Synchronous>true</Synchronous>
</Quota></code>
In the sample demonstrated above, the Quota protocol permits 100 API requests every minute.
`
`
API Performance Discrepancies
Degradation in API performance may occur due to multiple causes like network delays, server congestion, or deficient API layout.
For rectification, utililze Apigee's in-house analytics toolset to spot performance issues and bottlenecks. Monitor server congestion and network delays, and fine-tune them as required. If the API layout is found lacking, think about revamping the API for augmented performance.
To summarize, an efficient rectification of issues in Apigee API security protocol administration requires an in-depth knowledge of the system and the protocols themselves. By recognizing the frequent problems and effective strategies to address them, you can guarantee your APIs stay secure and continue delivering optimal performance.
Amplifying API Guard: Accelerating Apigee Defense Solutions
Unblemished API architecture necessitates top-notch security shields. Apigee, a complete blueprint for maneuvering through the API lifecycle, is equipped with a multitude of robust, alert safeguards constructed to reinforce your APIs against prospective dangers and emerging security violations. In this chapter, we dive into the process of boosting your API protection administration by effectively capitalizing on these security resources.
- Unraveling Apigee's Defensive Measures
Intelligently crafted to empower your APIs, Apigee's extensive defensive measures deter harmful security threats, including SQL attacks, cross-site forgery (XSS), and relentless Denial of Service (DoS) threats. These protective tactics are crucial in maintaining data confidentiality and aiding conformity with pivotal legal ordinances like GDPR and HIPAA.
- Augmenting Apigee's Security Measures
For productive deployment of Apigee's security measures, it's critical to understand their capabilities and masterful employment. To accomplish that, examine these strategies:
-
Forge a Mixed Security Approach: Apply varied protective measures to build a multilayered defense system. OAuth can verify identities, the Spike Arrest can deflect DoS intrusions, and the JSON Threat Protection can aid in deflecting dangerous JSON payloads.
-
Adopt Measure Sequencing: Apigee provides the capability to blend multiple measures at once, elevating your overall shield. Combining the XML Threat Protection measure with the Regular Expression Protection measure offers a comprehensive defense against both XML and regex hazards.
-
Tailor Measures to Suit Your Needs: Apigee's adjustable security measures are fully customizable to align with your individual protection necessities and threat scenarios.
- Utilizing Apigee's Security Measures
Employ this methodical procedure to institute Apigee's security measures:
-
Step 1: Enter your Apigee dashboard and navigate to the API Proxy Editor.
-
Step 2: Proceed to the 'Policies' section and select the option 'Add Policy'.
-
Step 3: Pick the security measure you wish to engage from the assortment of options.
-
Step 4: Modify the measure properties according to your circumstances and click 'Save'.
The OAuth tool can be initiated this way:
<code class="language-xml"><OAuthV2 async="false" continueOnError="false"
enabled="true" name="OAuth-v20-1">
<DisplayName>OAuth v2.0 1</DisplayName>
<ExternalAuthorization>false</ExternalAuthorization>
<Operation>VerifyAccessToken</Operation>
<SupportedGrantTypes/>
<GenerateResponse enabled="true"/>
</OAuthV2></code>
- Evaluating and Adjusting Apigee's Security Measures
Apigee introduces comprehensive audit and modification tools to assist you in supervising your defensive measures. The Apigee Edge platform can be harnessed to monitor tool functions, detect irregularities, and remedy any disparities.
- Recommended Practices for Apigee's Security Measures
Adhere to these guidelines to optimize the functionality of Apigee's security measures:
-
Keep Abreast with Measure Enhancements: Apigee ceaselessly ameliorates its security resources to neutralize emerging menaces and security gaps. Confirm that your measures are always updated to ensure optimal defense.
-
Perform Rigorous Tests: Prior to embedding any protection measures, execute thorough assessments to ascertain they function without hindering your API's operations.
-
Track Measure Functionality: Regularly oversee the functionality of your defensive measures to diagnose any probable complications or threats.
Adept and proficient implementation of Apigee's defensive measures can considerably elevate your API's security levels. Keep in mind, security isn't a once-off task but a continuous obligation. Stay sharp, maintain currency of your tools, and persistently evaluate their functionality to ensure the integrity of your APIs.
如有侵权请联系:admin#unsafe.sh