We have released the PCAP Format package for all licenses of Cerbero Suite.
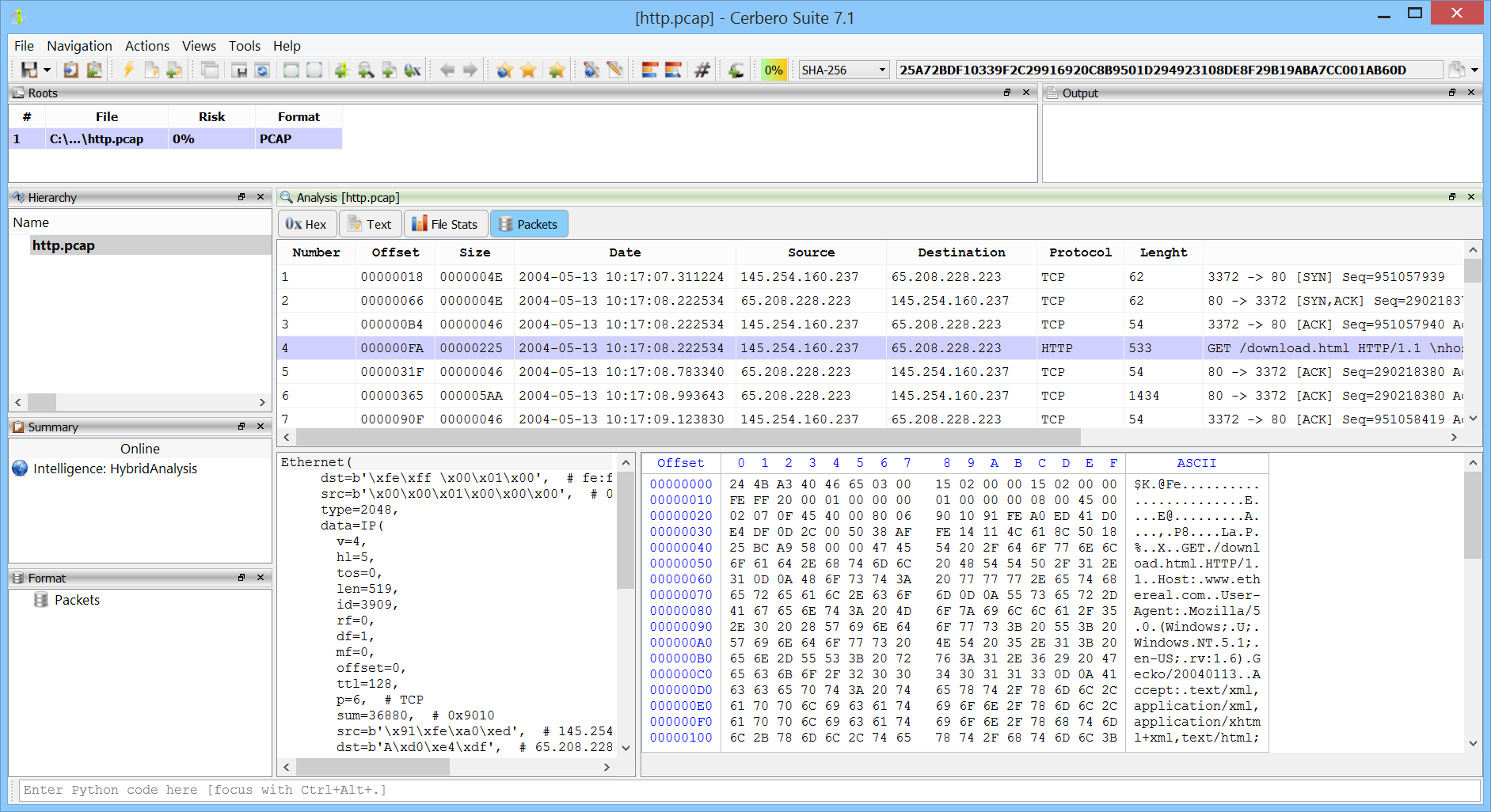
The PCAP format is the main capture file format used in TcpDump/WinDump, snort, and many other networking tools and is fully supported by Wireshark/TShark. Our support does not aim to compete against a specialized tool like WireShark, but it gives the capability to inspect PCAP files without leaving the Cerbero Suite interface. This is especially useful when analyzing malware reports.
For example, the HybridAnalys Intelligence package allows to download sandbox artifacts by clicking on the ‘Job ID’ in the report.
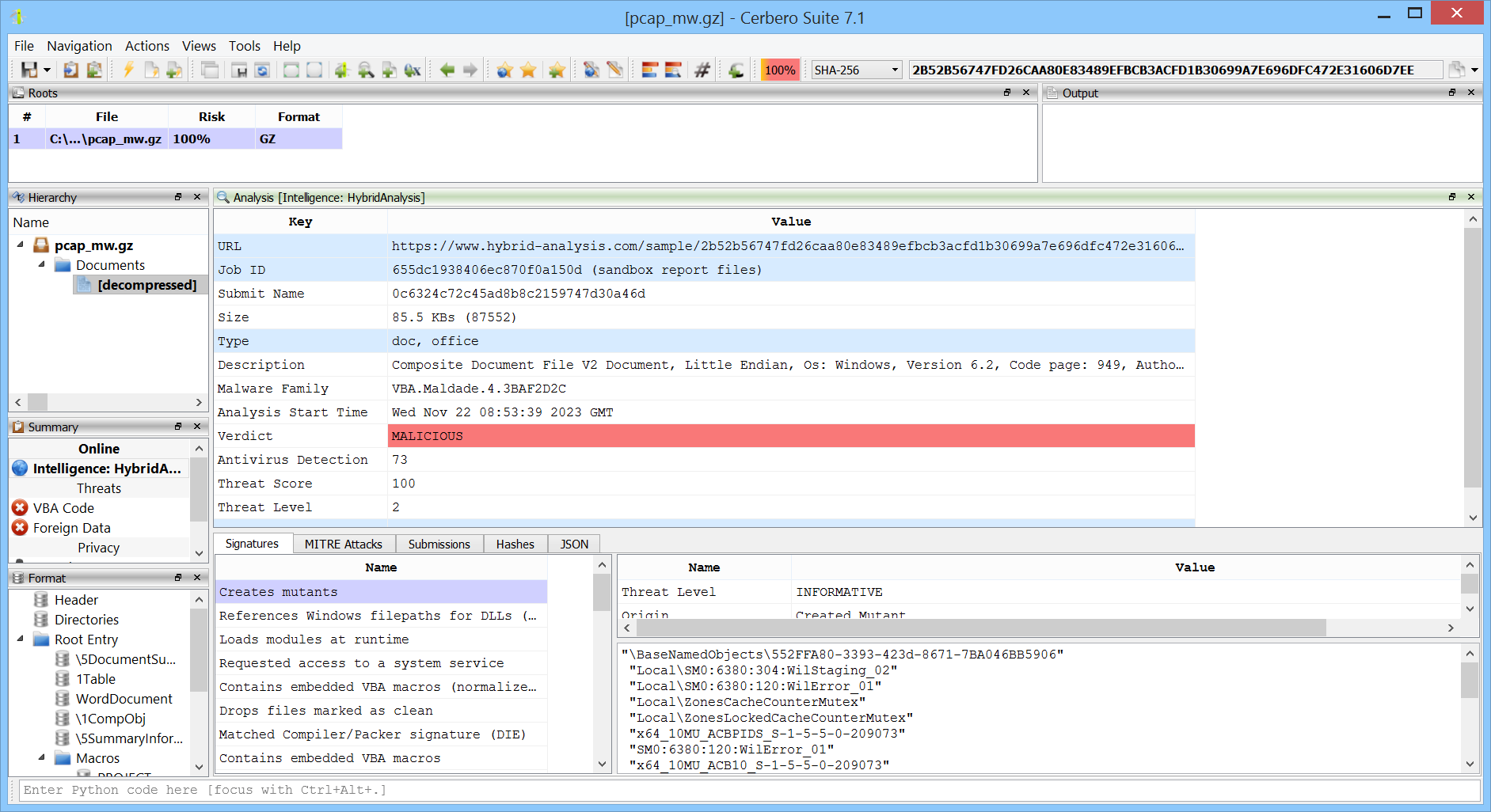
By selecting ‘PCap’, the associated PCAP data is automatically downloaded and added to the project as a child object.
It is now possible to directly inspect the generated traffic without leaving Cerbero Suite.
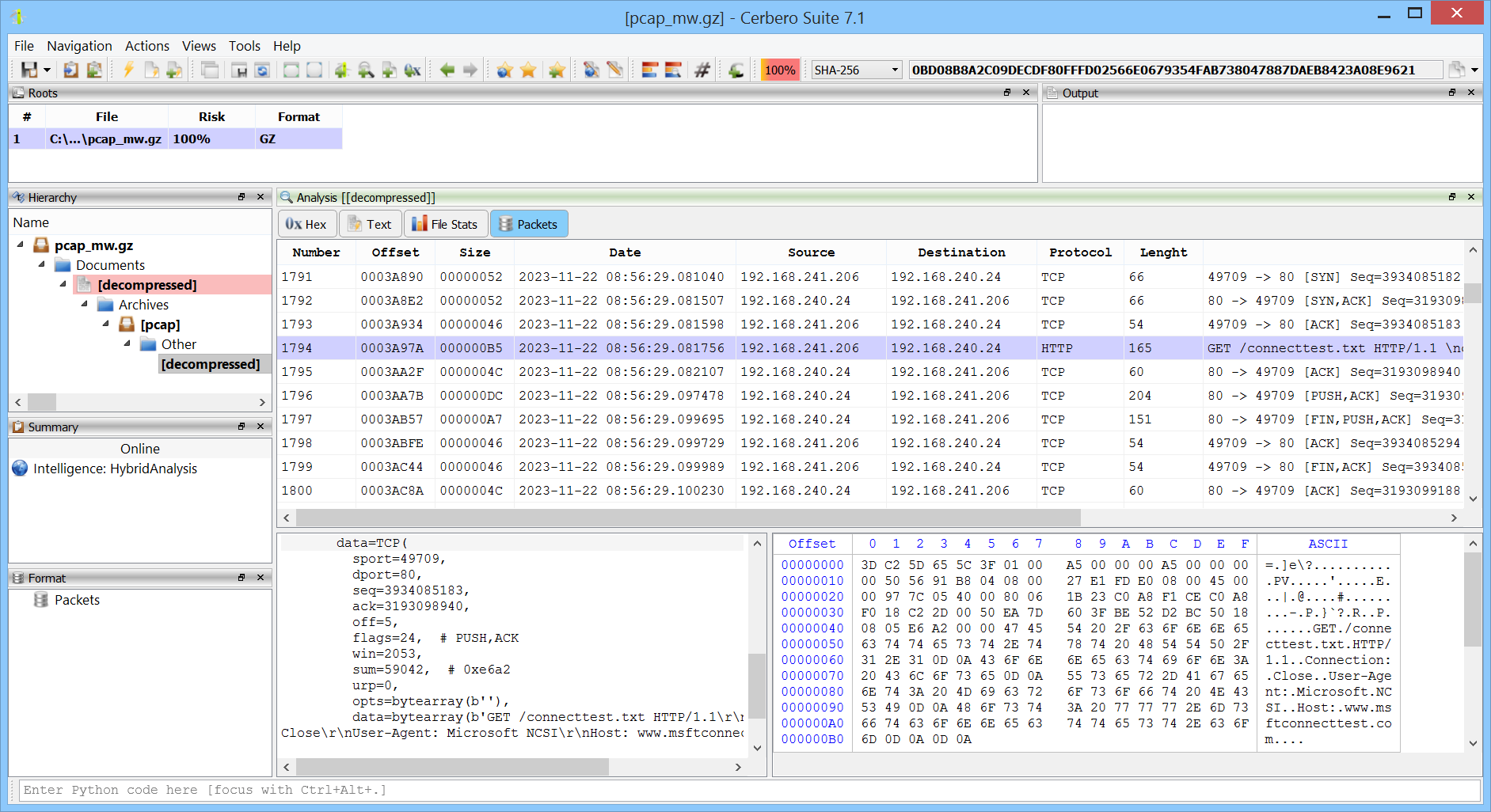
The package is also exposed to the SDK:
from Pro.Core import *
from Pkg.PCAP import *
def parsePCAP(fname):
c = createContainerFromFile(fname)
if c.isNull():
return
obj = PCAPObject()
if not obj.Load(c) or not obj.Parse():
return
for packet in obj.IteratePackets():
out = NTTextBuffer()
packet.Dump(out)
print(out.buffer)