In cloud computing, especially within AWS, managing security risks is essential due to the vast array of services and configurations. Uptycs Risk Prioritization provides a practical solution for this. It helps prioritize risks across all AWS services, a vital step for any AWS ecosystem, from EC2 workloads to broader account management. This tool is designed to ensure that security alerts are not just acknowledged but are also ranked and addressed in an order that reflects their importance and urgency. Uptycs Risk Prioritization changes the game in threat management by introducing a smarter way to handle security risks within AWS. By assessing and prioritizing risks based on their severity and impact, this tool enables security teams to focus on the most pressing issues first. It goes beyond the typical one-size-fits-all alert system, offering a nuanced approach that considers the unique aspects of each threat. This means teams can efficiently allocate their resources and attention where it's needed most, ensuring that critical vulnerabilities and threats are not lost in the noise of less significant alerts. Integrating Uptycs Risk Prioritization into threat management transforms how security teams handle risks within AWS. This tool assesses and ranks threats based on severity and impact, allowing for focused attention on critical issues. It moves beyond traditional alert systems by offering a nuanced approach tailored to the specifics of each threat. This prioritization is especially crucial in environments overwhelmed with alerts, where distinguishing between critical and minor issues can be challenging. Uptycs tackles this by analyzing risks through three key dimensions: Workload Context, Cloud Context, and Business Context, providing a comprehensive understanding that drives efficient and effective threat management. To truly understand the impact of Uptycs Risk Prioritization, we will explore its application in a real-world scenario. In the following sections, we'll illustrate how it contributes to a more strategic and focused approach to threat prioritization within AWS environments: Workload context This dimension focuses on the specific environment in which workloads operate, delving deep into the detailed aspects of workload operation and security posture. Uptycs offers customers the ability to deploy the Uptycs Sensor or utilize agentless scanning. In the example below, we've identified six critical vulnerabilities with known exploits. This situation represents a high-risk scenario often targeted by attackers using readily available tools. It's not just a theoretical risk; it's a real and imminent threat. These vulnerabilities act as open doors for attackers, making the system an attractive target. From here, you can view all six vulnerabilities along with a description of each. Additionally, you have the ability to take further actions, such as creating a Jira ticket or adding an exception: Beyond this specific instance, similar risks could encompass host compliance breaches, operational anomalies, and more. While these may not be visible in this particular screenshot, they are crucial aspects of Workload Context in Uptycs' analysis when utilizing the Uptycs Sensor. This dimension examines configurations, network exposure, identity permissions, and anomalies, providing insight into the security landscape of the cloud. For example, we can observe that the security group is open to the internet, making the EC2 instance susceptible to confirmed attack paths. Additionally, we notice that the role attached to the EC2 instance has overly permissive permissions. Below, we can examine the identified overly permissive role to visualize its blast radius, i.e., what resources it can access: While this example spotlights port exposure, other scenarios may have issues such as GuardDuty findings of high severity, publicly accessible snapshots, unencrypted S3 buckets, disabled RDS instance audit and error logs, and more. These examples illustrate how Uptycs identifies and flags potential cloud-based risks. This dimension integrates technical insights with business imperatives, taking into account tags, operational environments, and team alignments to align risk focus with business priorities. Below, we've identified an overly permissive role that has access to an S3 bucket designated as a Critical Resource. A critical resource refers to any asset within an organization that, due to its significance, demands heightened security measures and attention to safeguard against potential threats or breaches. If we scroll down to the Risk Graph, we can visualize the S3 bucket marked as a critical resource, distinguished with a purple star: From there, you can select the critical resource bucket and identify the actions the overly permissive role can take on the bucket: Figure 8 - Critical resource displaying actions allowed by the role Furthermore, you can take several additional actions from the critical resource bucket or utilize the 'Ask Graph' feature by selecting a plain English question to learn more about the resource's configuration: In addition to this specific example, businesses must consider factors such as resource ownership and compliance regimes. Uptycs assists in identifying and categorizing these risks, even if they may not be directly visible in this particular screenshot. Uptycs uses contextual data to dynamically assess risks based on their likelihood and severity. High-risk scenarios, such as a vulnerable system with access to sensitive data, are prioritized, guiding security teams to address the most critical threats first. Likelihood assessment: Severity evaluation: Managing security risks in AWS environments can be quite a task with the volume of security alerts that teams face. This can lead to key issues being missed and inefficient responses. A major part of the challenge is the lack of context and structured methods to evaluate risks. Key takeaways: Your next move: Master cloud security by integrating Uptycs Risk Prioritization into your AWS strategy. Prioritize alerts intelligently, safeguard your cloud infrastructure, and stay ahead of evolving threats. Your organization's security is paramount—take action today. Mastering Cloud Security #1: Understanding Attack Paths and Risk How Uptycs Risk Prioritization transforms threat management
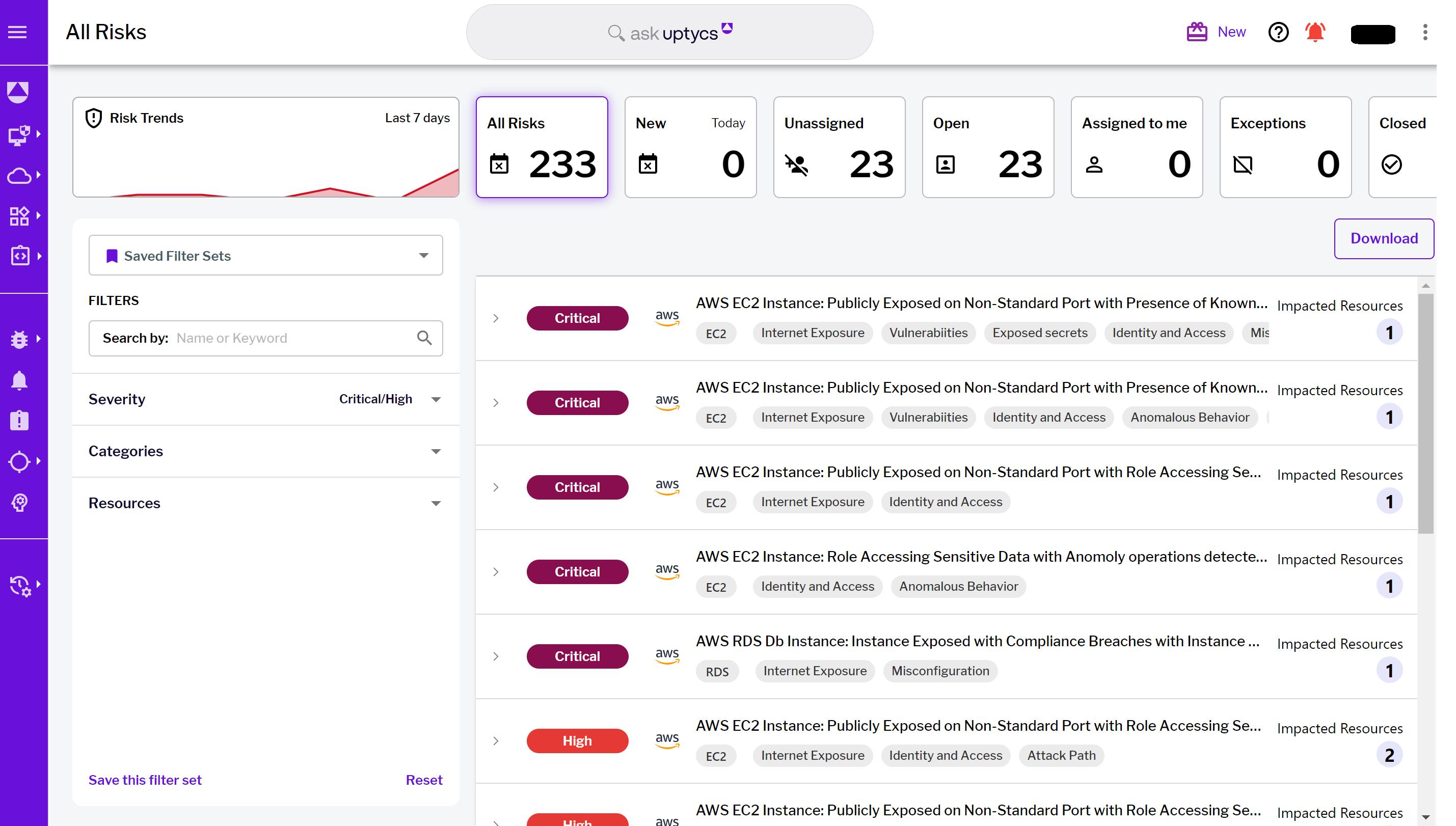 Figure 1 - Uptycs Risk Prioritization landing page
Figure 1 - Uptycs Risk Prioritization landing page
Cloud context
Business context
Dynamic risk assessmentWorkload context
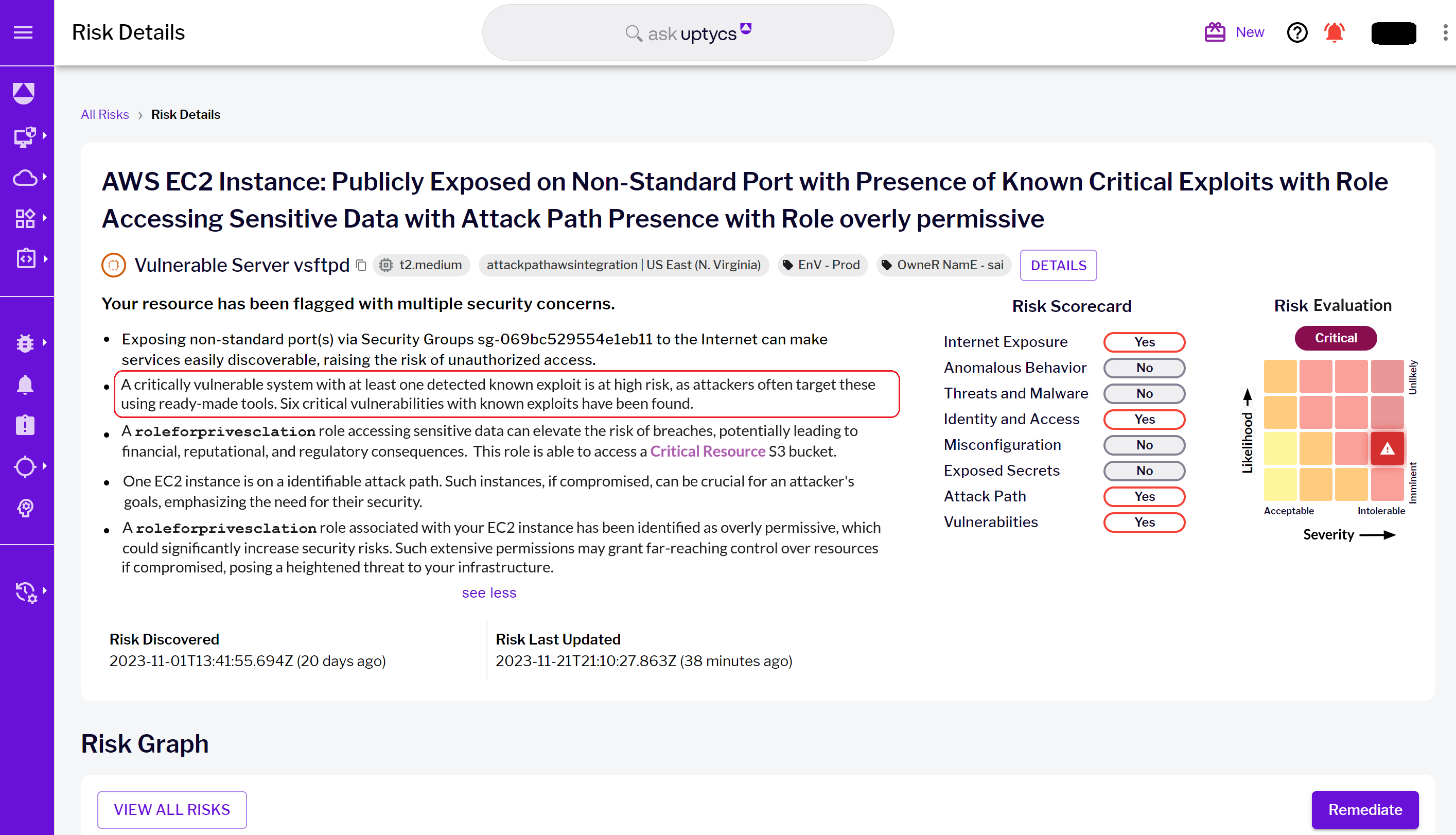 Figure 2 - Risk details landing page and highlighted workload context risks
Figure 2 - Risk details landing page and highlighted workload context risks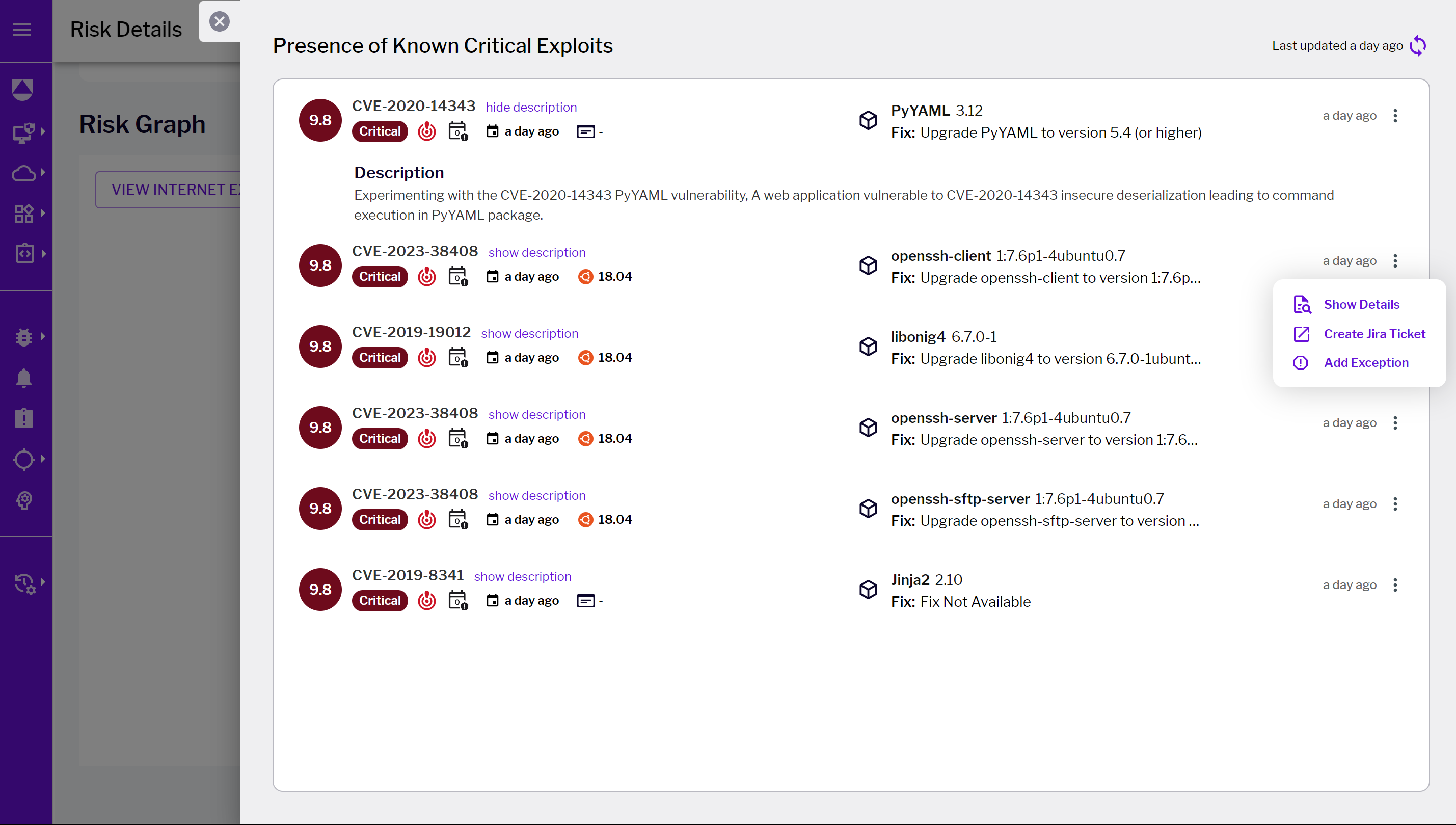 Figure 3 - Critical exploits details page
Figure 3 - Critical exploits details pageCloud context
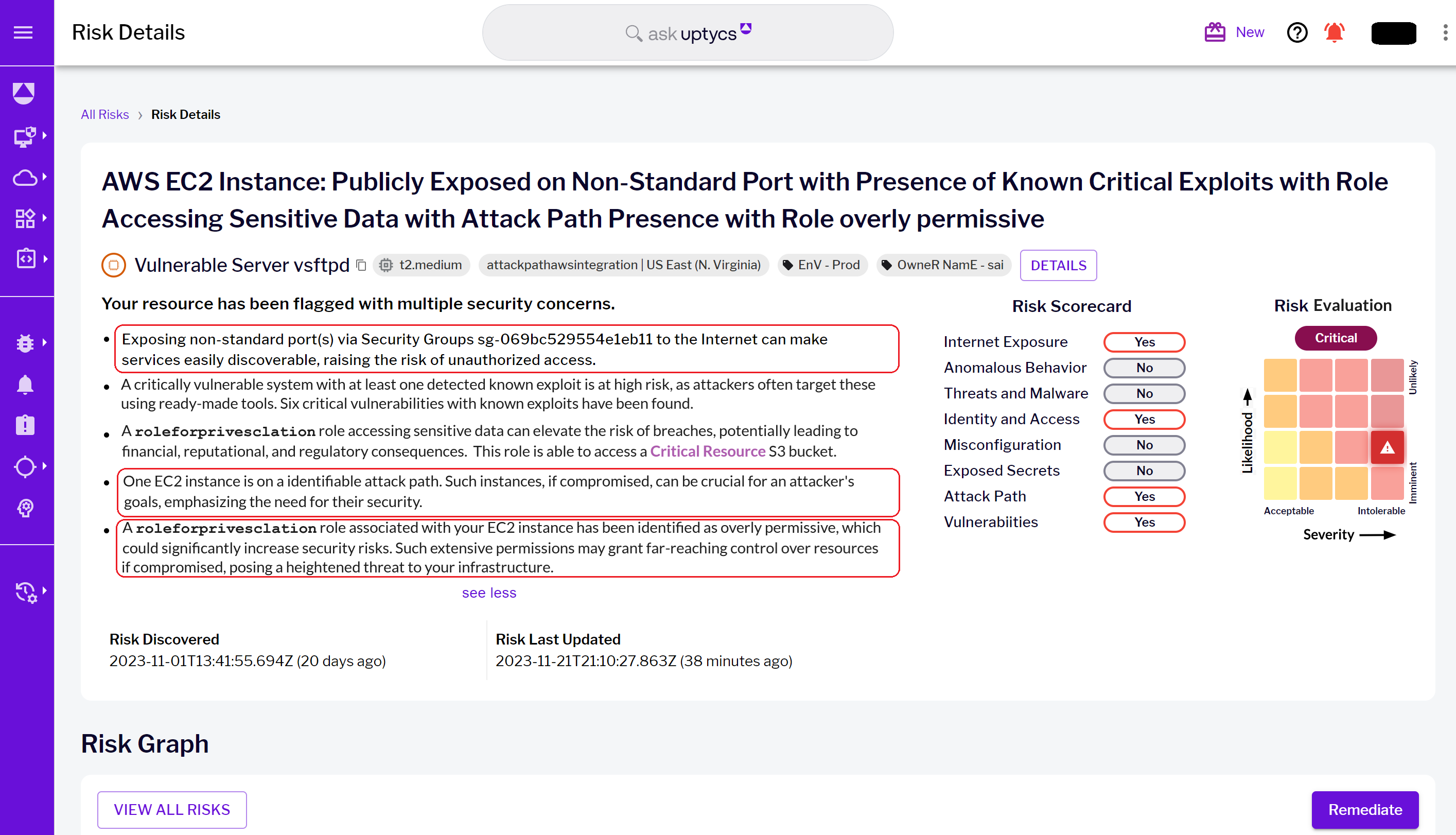 Figure 4 - Risk details landing page with highlighted cloud context risks
Figure 4 - Risk details landing page with highlighted cloud context risks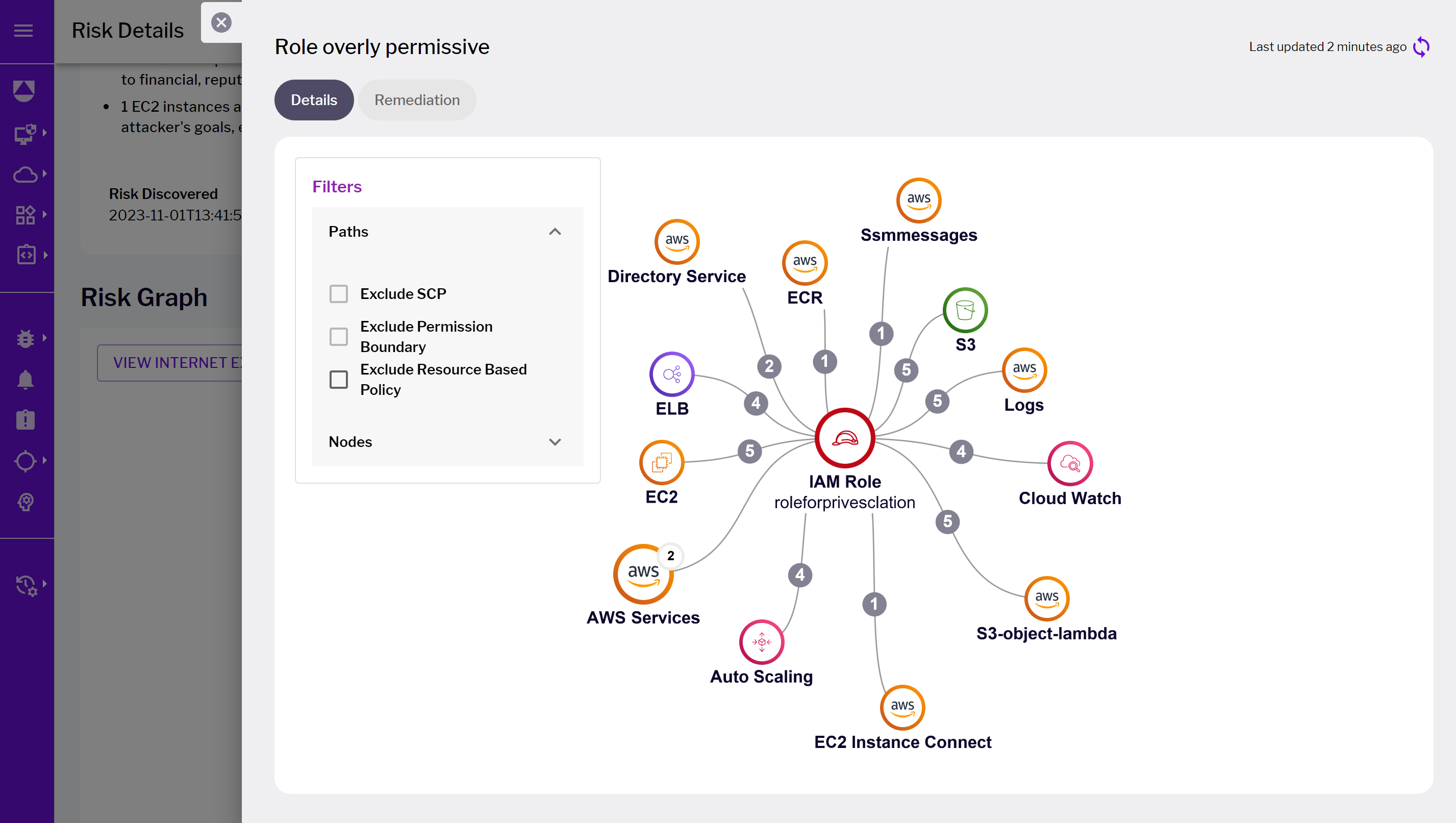 Figure 5 - Overly permissive role details page
Figure 5 - Overly permissive role details pageBusiness context
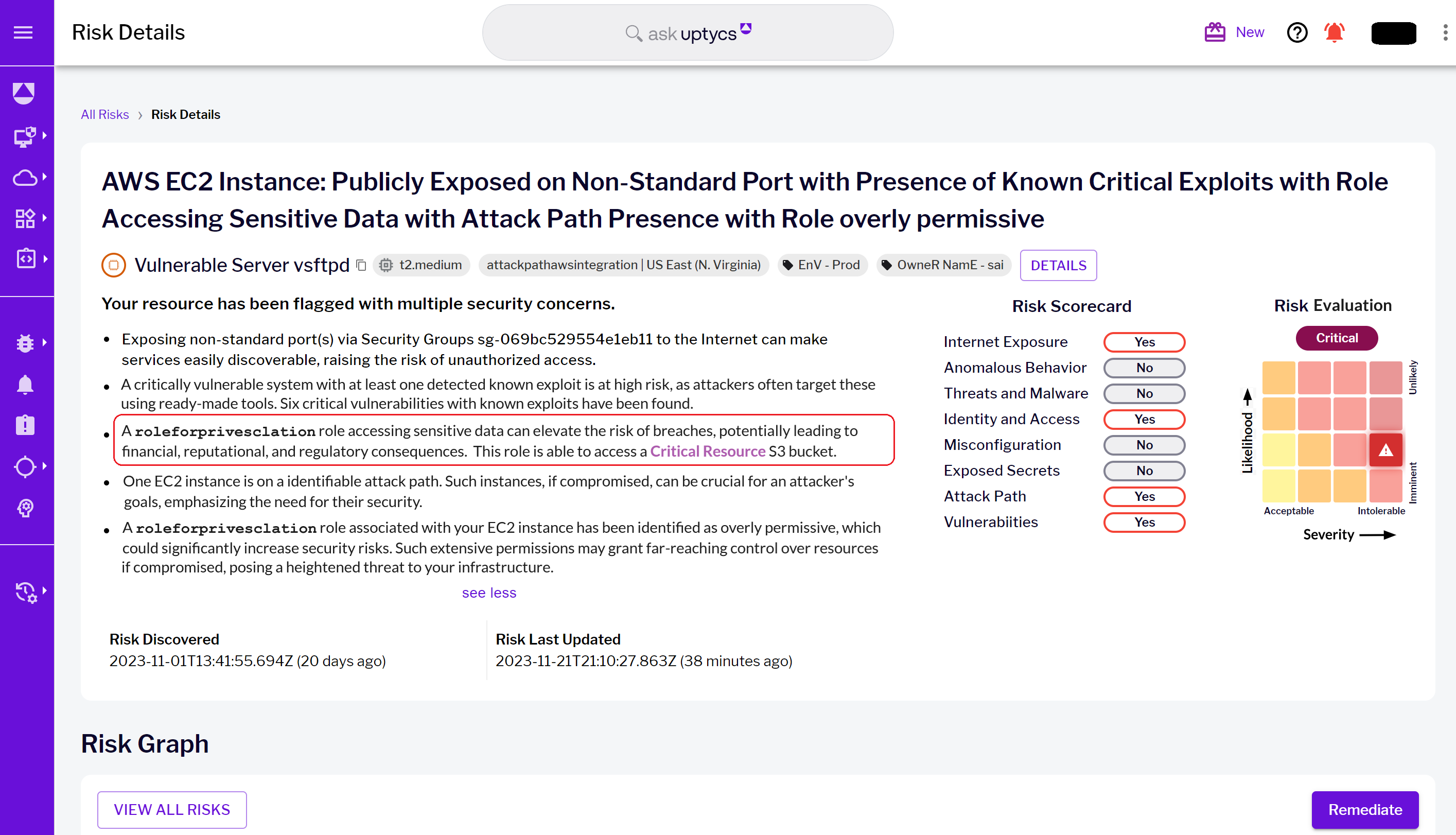 Figure 6 - Risk details landing page with highlighted business context risk & critical resource
Figure 6 - Risk details landing page with highlighted business context risk & critical resource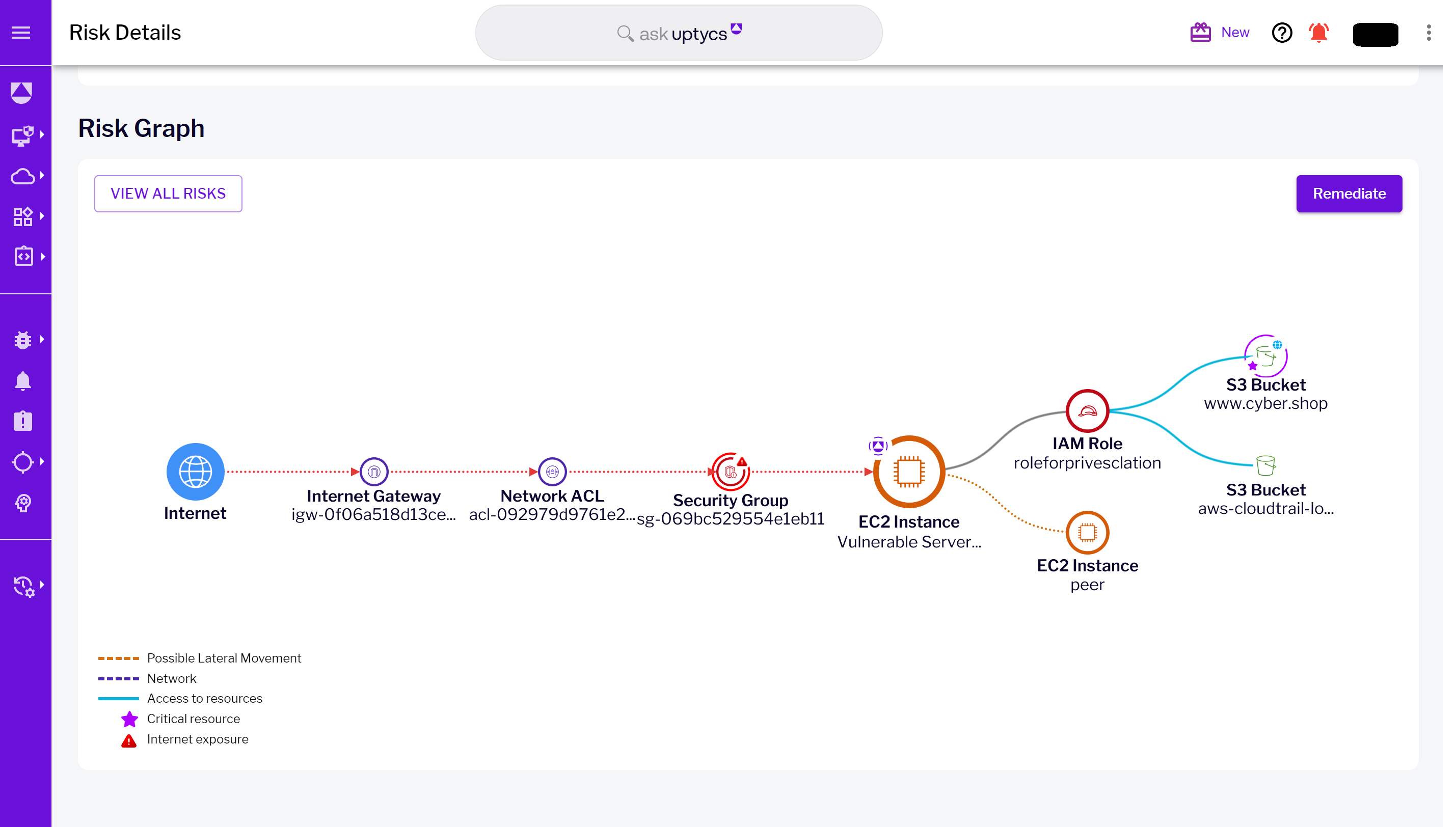 Figure 7 - Risk Graph landing page visualizing the critical resource S3 bucket
Figure 7 - Risk Graph landing page visualizing the critical resource S3 bucket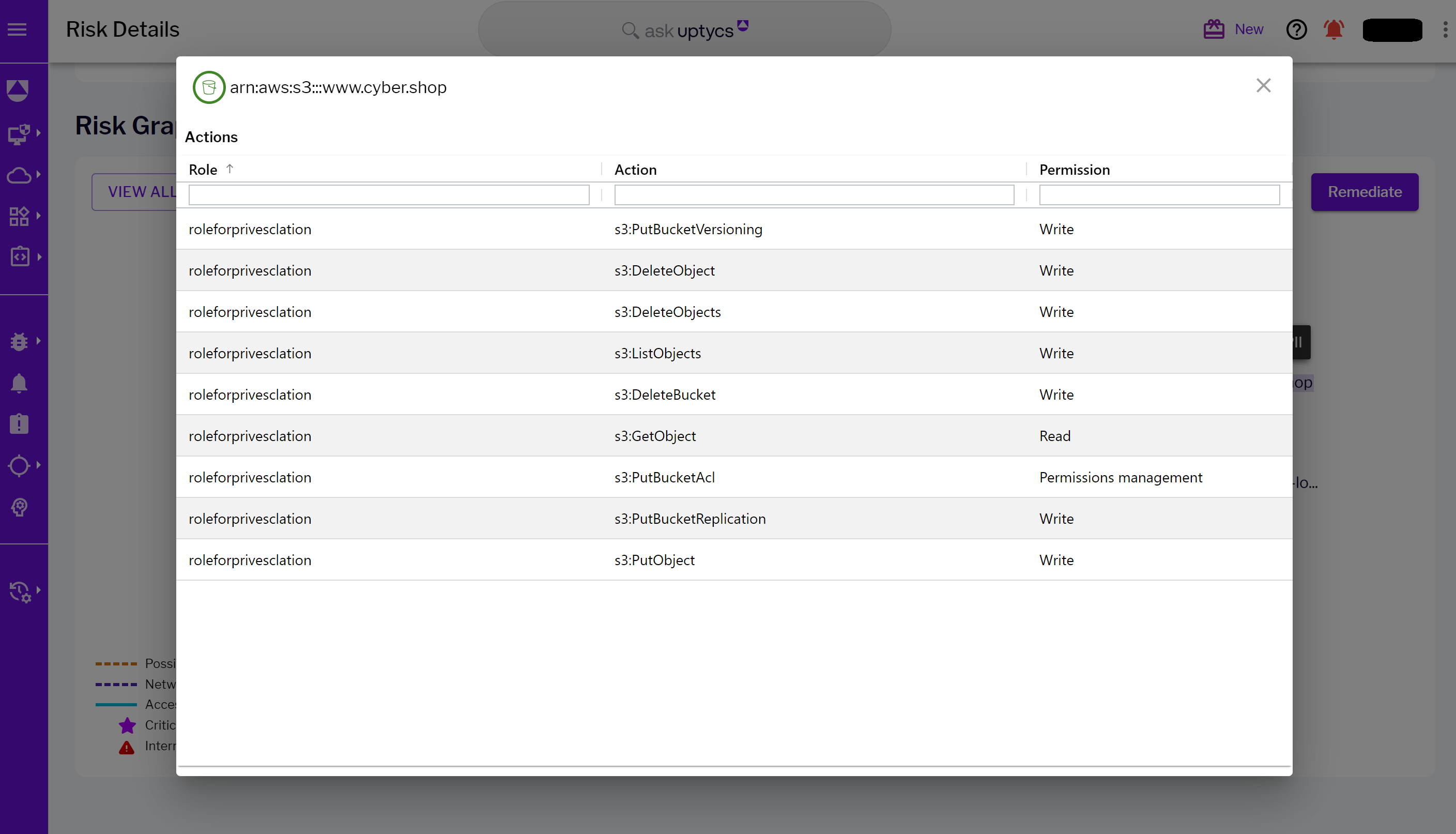
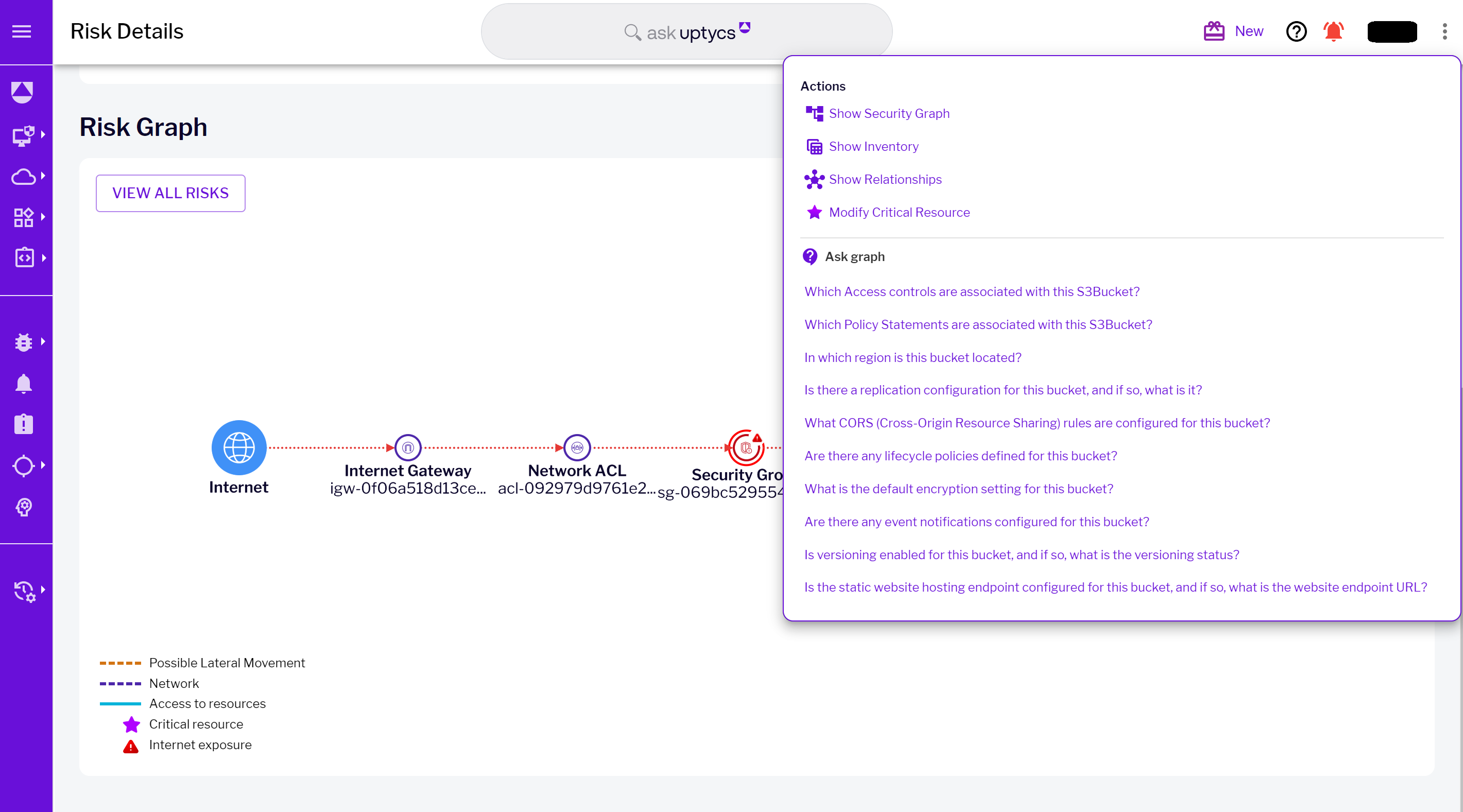 Figure 9 - Critical resource ‘Ask Graph’ capability
Figure 9 - Critical resource ‘Ask Graph’ capabilityDynamic risk evaluation
This aspect measures the probability of a breach, taking into account current defenses and attack methods. For instance, in our scenario, a system with numerous known vulnerabilities has an elevated breach likelihood due to potential security weaknesses.
Uptycs also assesses the potential impact of a breach, not only in the immediate sense but also in terms of broader business consequences. A breach in critical systems, as exemplified by our scenario involving a sensitive S3 bucket, is considered critical due to potential data loss, regulatory compliance issues, and reputational damage.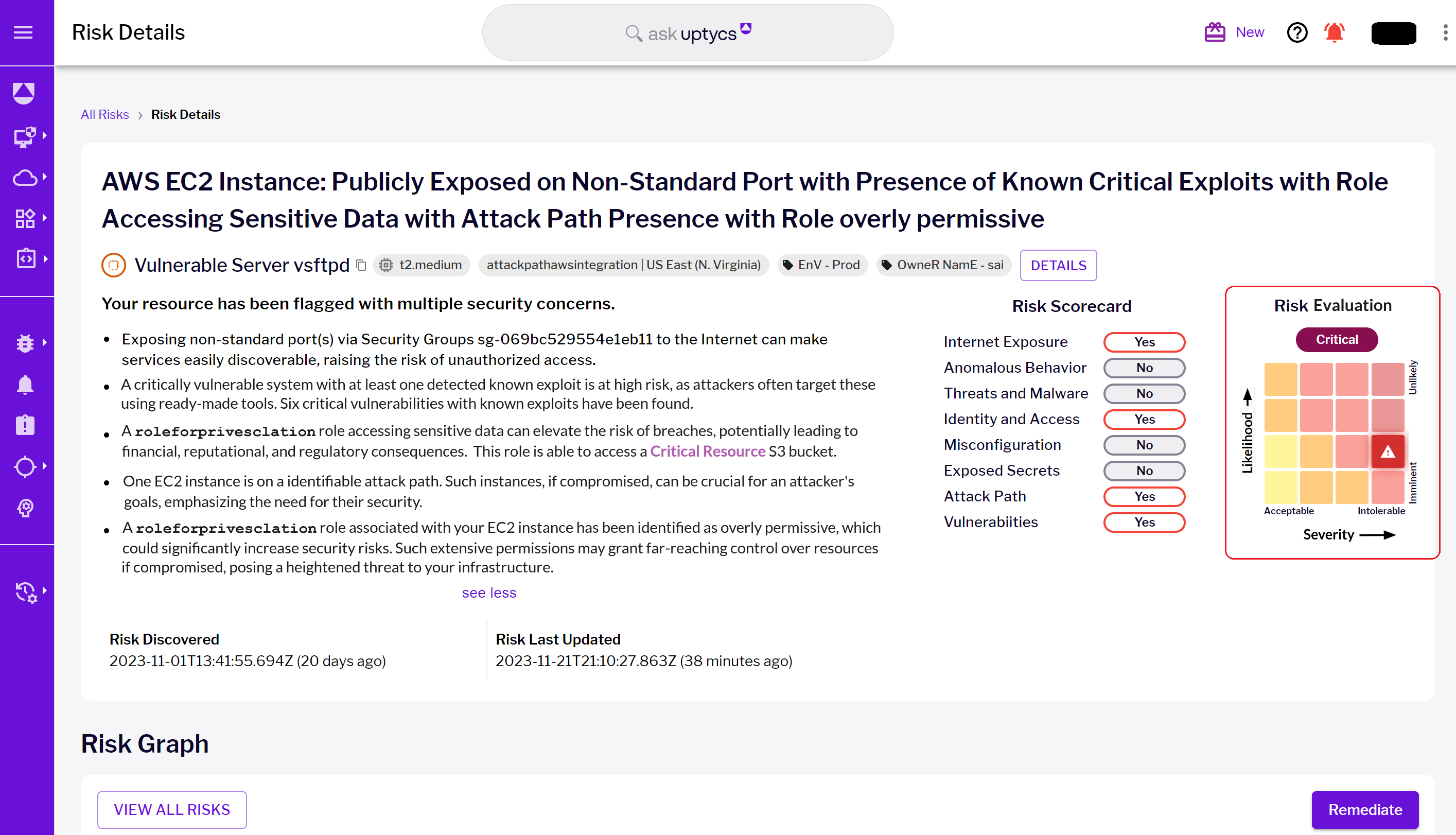 Figure 10 - Risk details landing page with highlighted Risk Evaluation matrix
Figure 10 - Risk details landing page with highlighted Risk Evaluation matrixMastering cloud security with Uptycs
More from the series

Manage Cloud Computing & AWS Security: Uptycs Risk Prioritization
2023-11-28 05:53:48 Author: www.uptycs.com(查看原文) 阅读量:17 收藏
2023-11-28 05:53:48 Author: www.uptycs.com(查看原文) 阅读量:17 收藏
文章来源: https://www.uptycs.com/blog/cloud-security-risk-prioritization-threat-management
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh