2023-11-28 16:17:29 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Security misconfiguration is a critical vulnerability that can lead to unauthorized access, data breaches, service disruptions, and reputation damage. In today’s digital landscape, where cyber threats are constantly evolving, it is essential to address security misconfiguration proactively. One emerging approach is the use of machine learning techniques to identify and mitigate security misconfiguration issues. In this article, we will explore the concept of security misconfiguration, its common types, the impact it can have, and how machine learning can help in researching and addressing this issue.
What is Security Misconfiguration?
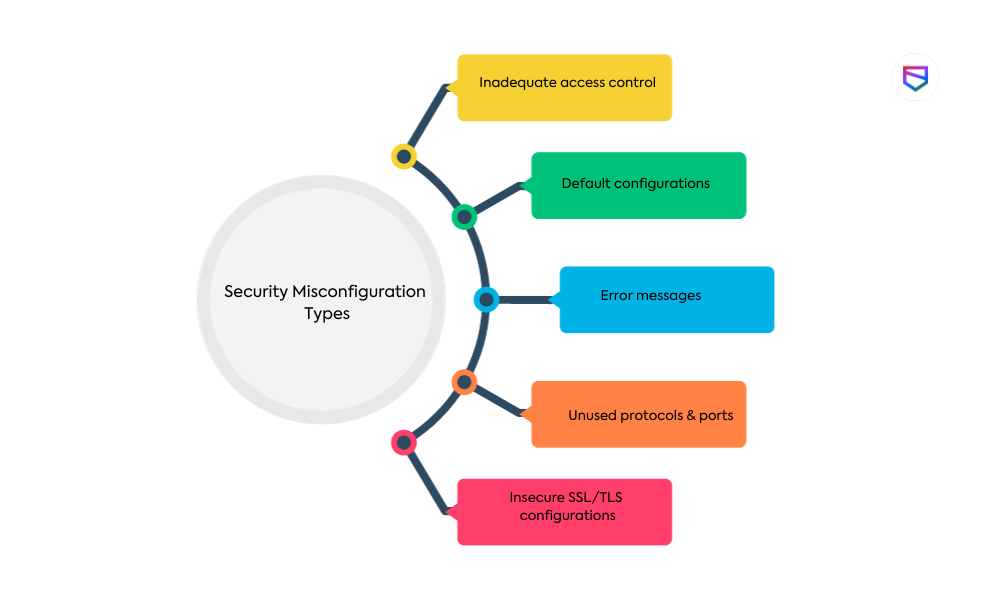
Security misconfiguration refers to the misconfiguration of a system or application that can leave it vulnerable to potential attacks. It can happen due to various factors, such as inadequate access controls, default configurations, error messages revealing sensitive information, unused protocols and ports, and insecure SSL/TLS configurations.
The Importance of Security Misconfiguration
Security misconfiguration is a significant concern in the realm of cybersecurity. It can provide an easy entry point for attackers, enabling them to exploit the vulnerabilities and gain unauthorized access to sensitive information. Therefore, it is crucial for organizations to understand the types of security misconfiguration and take appropriate measures to prevent them.
Common Types of Security Misconfiguration
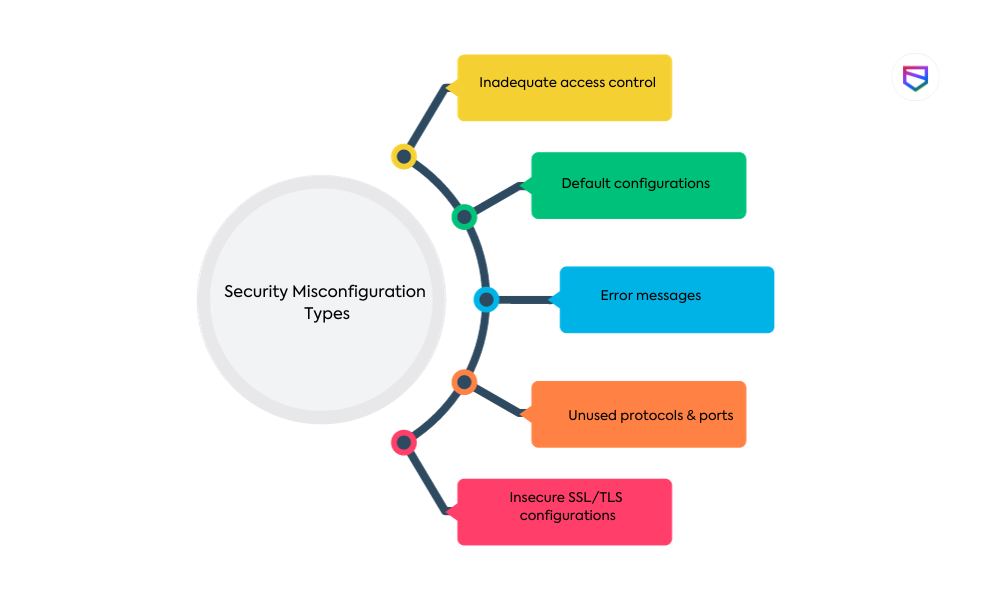
- Inadequate access control: Improperly configured access controls can allow unauthorized users to gain access to sensitive data or functionalities.
- Default configurations: Failure to change default configurations poses a significant risk as attackers are familiar with default settings and can exploit them to compromise systems.
- Error messages: Detailed error messages that reveal sensitive information can aid attackers in finding vulnerabilities and gaining further access.
- Unused protocols and ports: Unused and open protocols and ports increase the attack surface and provide potential entry points for attackers.
- Insecure SSL/TLS configurations: Improper SSL/TLS configurations can make encrypted communications vulnerable to attacks such as man-in-the-middle.
The Impact of Security Misconfiguration
- Unauthorized access: Security misconfiguration can lead to unauthorized access, allowing attackers to steal sensitive information, manipulate data, or disrupt services.
- Data breaches: Misconfigured systems can result in data breaches, leading to the exposure of customer information, trade secrets, and other sensitive data.
- Service disruptions: Misconfigurations may cause system failures, leading to service disruptions, downtime, and financial losses.
- Brand reputation damage: Security misconfiguration incidents can harm an organization’s reputation, erode customer trust, and result in legal and financial consequences.
How does machine learning help in identifying security misconfiguration?
Machine learning techniques play a crucial role in identifying security misconfiguration by analyzing large datasets and automating vulnerability detection. This allows organizations to identify potential issues more efficiently, enhance incident response, and create proactive security measures.
- Analyzing large data sets: Machine learning algorithms can process vast amounts of data to identify patterns and anomalies in system configurations, aiding in the detection of potential security misconfigurations.
- Automating vulnerability detection: By leveraging machine learning, organizations can automate the detection of security misconfigurations, reducing the reliance on manual inspections and increasing efficiency.
- Creating proactive security measures: Machine learning algorithms can learn from historical data and security incidents, enabling organizations to proactively implement security measures to prevent future misconfiguration issues.
- Enhancing incident response: Machine learning can play a crucial role in incident response by analyzing real-time data, identifying potential misconfigurations, and prioritizing response actions.
Examples of machine learning algorithms used in security misconfiguration research:
- Support Vector Machines (SVM): SVM is a popular algorithm used in security misconfiguration research due to its ability to classify and identify patterns in complex datasets.
- Random Forest: Random Forest is another widely used algorithm that combines multiple decision trees to identify patterns and anomalies in system configurations.
- Deep Learning: Deep Learning techniques such as Convolutional Neural Networks (CNNs) and Recurrent Neural Networks (RNNs) can be used to analyze large datasets and detect security misconfigurations with high accuracy.
Best Practices to Prevent Security Misconfiguration
Implementing best practices is essential to mitigate security misconfiguration risks and ensure the security of systems and applications. Here are some key practices:
- Regular vulnerability assessments: Conduct regular vulnerability assessments to identify potential misconfigurations and vulnerabilities in your systems and applications.
- Applying the least privilege principle: Implement the principle of least privilege to ensure that users have the minimum privileges necessary to perform their tasks, reducing the risk of unauthorized access.
- Keeping software up to date: Regularly update software and applications to ensure you benefit from the latest security patches and bug fixes.
- Reducing attack surface: Minimize the attack surface by disabling unused functionalities, removing unnecessary software, and closing unnecessary ports.
- Implementing secure configurations: Follow secure configuration guidelines provided by vendors and security experts to achieve a strong security posture.
Patching Security Misconfigurations
- Identifying vulnerabilities: Use vulnerability scanners or automated tools to identify security misconfigurations and vulnerabilities in your systems.
- Prioritizing and planning patching: Prioritize vulnerabilities based on their severity and potential impact, and plan the patching process accordingly.
- Applying patches and updates: Apply patches and updates promptly, following best practices recommended by vendors and security experts.
Conclusion
Security misconfiguration is a critical concern that can have severe consequences for organizations. Leveraging machine learning techniques can greatly assist in identifying and mitigating security misconfigurations by analyzing large datasets, automating vulnerability detection, creating proactive security measures, and enhancing incident response. Implementing best practices, such as regular vulnerability assessments, secure configurations, and prompt patching, is vital to prevent security misconfiguration risks. By staying vigilant and continually learning from security incidents, organizations can effectively protect their systems and data.
Recommended Reading
Penetration Testing for Server-Side Request Forgery (SSRF) in E-commerce Platforms
Vulnerability Prioritization: An Effective Security Approach
Securing the Democratic Narrative: Cybersecurity in Election Promotion
The post Safeguarding Against Security Misconfigurations with the Power of Machine Learning appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Naimisha. Read the original post at: https://wesecureapp.com/blog/safeguarding-against-security-misconfigurations-with-the-power-of-machine-learning/
如有侵权请联系:admin#unsafe.sh
