2023-11-29 16:39:45 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Encoding the content of sensitive emails prevents the compromise of information. So, even if a threat actor gets their hands on critical details, email encryption won’t allow them to decode, understand, and misuse them for attempting malicious activities.
Also, encrypted emails no longer require special encryption software as cloud-based interfaces are more readily available and offer better efficiency.
The increased number of phishing attacks, data breaches, BEC scams, and other types of cybercrimes have fueled the need for enterprises, government bodies, and individuals to exchange encrypted emails. Considering the rapidly growing cyber menace, regulatory bodies across the globe have laid down stringent mandates, including email encryption. Both of these factors are pushing companies and individuals to adopt security measures to shield emails’ content, owing to which the global email encryption market size is anticipated to soar to $16.3 billion.
However, small and mid-sized businesses are still lagging behind and not hopping on the cybersecurity trends, making themselves easy and favorite targets for professional scammers. We at PowerDMARC are on a journey to educate organizations and individuals about the gravity and urgency of placing cybersecurity protocols and technologies. Let’s discuss 5 practical reasons why every company should pay attention to email encryption, irrespective of its size and operational style.
What is Email Encryption?
Email encryption is an email security process involved in barring hackers and other unauthorized people from reading the content of email messages you send by disarranging the message into a format that is incomprehensible. The encrypted emails can then be decoded only at the desired recipients’ ends.
Emails are the basis of corporate communication, meaning that a lot of sensitive and secretive company information along with personally identifiable data are exchanged on a daily basis through emails. Data leaks are a common threat that plaque email communications – leading to devasting breaches of corporate data, files, financial information, and even employee details. This makes email encryption a viable method of protecting email data.
Email encryption is supported by most major mailbox providers. For example, Gmail sends and receives emails with encryption only when the other email provider supports TLS encryption.
How are Emails Encrypted?
Email encryption can take place with the help of several encryption methods and protocols. The process can either be automated wherein all outgoing email traffic is encrypted or manual wherein only specific email messages that contain sensitive information or personally identifiable information (PII) are encrypted.
Email encryption can be facilitated by installing encryption software on your device, however much more recently there are cloud-based hosted solutions and platforms that facilitate email encryption without you having to install any applications on your operating system or device.
Read more about email encryption architecture.
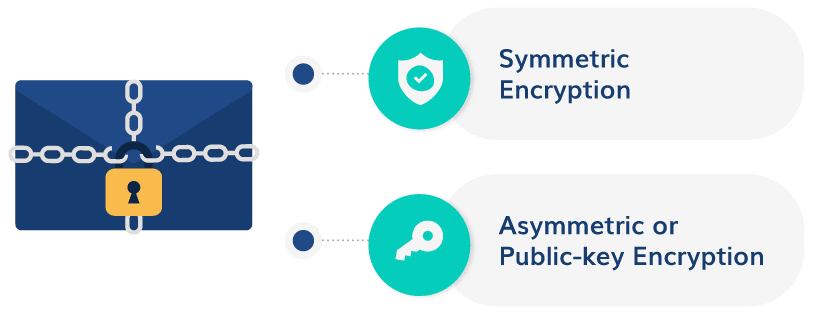
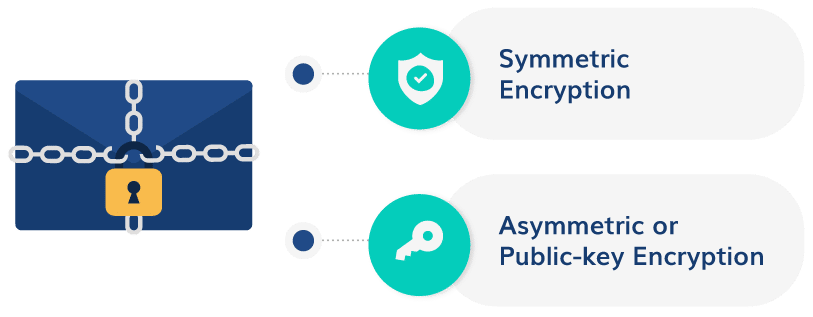
Two Primary Email Encryption Methods
There are two primary email encryption methods used by encryption protocols :
1. Symmetric Encryption
In this case, both the encryption key and the decryption key are the same. While this is a pretty straightforward method, it’s often challenging to share the key securely between the email sender and the email receiver without compromising the information’s privacy.
2. Asymmetric or Public-key Encryption
This is a more secure alternative to the symmetric encryption method as it requires different keys for encryption and decryption. The key pair contains a public and a private key wherein the public key is accessible to everyone but the private key can only be used by the key-owner to decrypt the message.
Common Email Encryption Types
The three major types of email encryption are as follows:
1. Pretty Good Privacy (PGP)
Pretty Good Privacy or PGP is an email encryption type that uses a combination of two encryption frameworks – symmetric-key encryption and public-key encryption, that allows you to encrypt your email information during communications. PGP is often used to encrypt sensitive files and emails with an extensive range of security features that ensure message privacy.
2. Secure Multi-purpose Internet Mail Extension (S/MIME)
S/MIME is another email encryption type that can be used to encrypt email content and digitally sign them for authentication. S/MIME was created by RSA data security and it requires the issuance of digital certificates from a reliable CA (Certificate Authority).
3. Transport Layer Security (TLS)
Transport Layer Security or TLS is an email encryption protocol that allows users to cryptographically encrypt email content during transmission so that the message travels over a secure connection between two communicating servers. Email authentication protocols like MTA-STS help enforce TLS encryption to ensure your email traffic is protected against cyber eavesdropping.
5 Ways Email Encryption Can Protect Your Business
In the simplest words, safeguarding the attachments, links, and text of any email coming in and going out on behalf of your company should be your priority. But if you are still not convinced, then continue reading to have your mind changed.
1. Data Breaches are Hazardous to Your Business Reputation
Unencrypted emails allow bad actors to extract sensitive information related to your business, like customer database, employee details, marketing and PR strategies, finance and accounting tangles, etc. Now, do you think your brand will not be affected at all if any such information comes out in the market?
We don’t need to remind you that competitive brands are always on their ‘riffle shooting positions’ to hunt you down by taking advantage of any bad move you make!
Imagine how badly your business reputation will be tarnished if all newspapers and news channels flash how critical details of your customers got compromised, and they got tricked into making financial transactions to the accounts of cybercriminals.
Just when we were drafting this article, we came across just the right news that fits the scenario well, and we think it’s going to convince you to take the possibilities of data breach instances seriously. Taj Hotel, one of the largest chains of luxury hotels, has been the target of a data breach where customers’ addresses, membership IDs, mobile numbers, and other personally identifiable information (PII) from 2014 to 2020 were compromised.
As of 25th November 2023, the threat actor going by the name ‘Dnacookies’ has demanded a ransom of $5000. Not just this, but you should also know that the Digital Personal Data Protection or DPDP Act suggests imposing fines of up to Rs 250 crore (approx $30 million) on businesses (recognized as data fiduciaries) for each data breach occurrence. Additionally, the maximum penalty for multiple breaches is set at Rs 500 crore (approx $60 million).
These numbers and instances reflect how ugly the situation can get if cybersecurity isn’t taken seriously!
2. Regulatory Compliances Afloat Your Boat
Depending upon the industry and country/ city of operations, your business could be liable to different encryption compliances regulated by the government. Failing to comply with them leaves your brand vulnerable to lawsuits and heavy penalties from consumers whose data is exploited because of your lack of securing their confidential details. Some notable regulatory compliances are:
-
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA mandates end-to-end encryption for emails containing PHI or Protected Health Information in transit as well as in rest. Small healthcare providers lacking in-house IT staff to guarantee HIPAA compliance for their email systems are advised to opt for third-party HIPAA-compliant email service providers.
Non-compliance to HIPAA regulations leads to civil monetary penalties, making a small to very large hole in your pockets with fines ranging from $100 to $50,000 per violation based on the degree of culpability. Intentional violations may incur criminal penalties, leading to fines and possible imprisonment.
-
General Data Protection Regulation (GDPS)
GDPR doesn’t explicitly mandate the exchange of encrypted emails; however, it strongly recommends it. It believes that the 122 work-related emails sent per day by email users should be protected from getting exploited in all possible ways.
-
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS requires companies to protect customers’ details during transit and while in storage. You are also liable to detail the measures taken to ensure that cardholder data is protected during transit. Recently DMARC PCI-DSS implementation has also been made mandatory for organizations as a future-dated requirement before enforcement begins in 2025.
PCI DSS imposes fines varying from $5000 to $100,000 per month on non-compliant companies.
-
California Consumer Privacy Act (CCPA)
Businesses obligated to CCPA are required to encrypt emails containing the personal information of consumers. Strong litigations are imposed on companies responsible for disclosing or losing sensitive customer data. It is crucial to research potential service providers to confirm their adherence to CCPA standards and ensure that their services align with your specific requirements.
3. Message Modification is Villainous
Unsecured and unencrypted messages can be tracked down in transit to modify the content and its narrative without tipping off senders and recipients at all. This can be detrimental to the brand’s and the sender’s reputation. Changing an email’s tone, content, and intent may result in disputes and legalities as well.
Encryption services encompass expiration times and timestamps, ransom session keys, and one-time use passwords, which are immediately discarded to reduce the risk of message reply.
4. Impersonation Can Disrupt Relationships and Cause Personal Distress
Hackers can masquerade as you and alter outgoing messages, straining relationships with contacts who may be confused or upset by the content of the emails. On a personal level, being the victim of impersonation can cause emotional distress due to the violation of personal or professional boundaries, requiring significant efforts to rectify the situation and mitigate associated risks.
5. Saves Money on Different Levels
Implementing email encryption can significantly contribute to cost-cutting for a company in various ways. Firstly, by safeguarding sensitive information and communications, encryption helps prevent data breaches and cyberattacks. The financial repercussions of a security breach, including legal fees, regulatory fines, and potential loss of business, can be substantial. Email encryption minimizes these risks, saving the company from potential financial burdens.
Additionally, encrypted communications enhance trust among clients and business partners, reducing the likelihood of reputational damage that might otherwise lead to revenue loss. Moreover, compliance with data protection regulations is crucial in avoiding penalties, and email encryption aids in meeting these compliance requirements, preventing costly consequences. By investing in email encryption solutions, companies not only secure their sensitive data but also make a strategic investment in cost-effective risk mitigation and regulatory compliance.
To Conclude
This article aimed to share the cruciality of using email encryption software or cloud-based services to allow only authorized entities to read emails containing important details. The rising number of cyberattacks on small and mid-scale businesses are loud alarms that fuel the need to adopt measures to shield your organization from newer and more sophisticated means of tampering with messages.

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Ahona Rudra. Read the original post at: https://powerdmarc.com/what-is-email-encryption-types-and-methods/
如有侵权请联系:admin#unsafe.sh
