2023-11-30 01:29:37 Author: www.thezdi.com(查看原文) 阅读量:16 收藏
In a previous blog, we took a look at the ChargePoint Home Flex EV charger – one of the targets in the upcoming Pwn2Own Automotive contest. In this post, dive in with even greater detail on all of the EV Chargers targeted in the upcoming Pwn2Own Automotive competition. This isn’t meant to be a detailed exploitation guide. However, we hope these high-resolution images will inspire some of the research we hope to see on display in Tokyo.
This post provides detailed imagery of the target EV chargers we are including in the upcoming Pwn2Own Automotive contest. Our intention is to help contestants understand the component hardware included in the EV chargers for the competition. But first, a safety reminder:
EV Chargers contain high voltages. Use extreme caution when working with them. Never touch interior components when powered on. If you are unable to determine the safe vs unsafe regions within the device, seek qualified assistance before proceeding. An open enclosure can be a deadly enclosure. Modifications to charging devices should not be made if there is an intent to ever plug the device into a vehicle or use the charging cable power or signal conductors as part of the experimentation. If there is such an intent, the EV charger should not be modified, and the appropriate connections should be made per the manufacturer's instructions.
With that out of the way, let’s move on to the images.
Autel Maxi EV Charger
The following list summarizes the components Trend Micro Research has identified as notable components and/or potential attack surfaces in the Autel Maxi EV Charger.
· ST Micro STM32F407ZGT6
· Renergy RN830(B)
· Barrot BR8051A01 bluetooth radio
· Quectel EC25-AFX
· GigaDevices GD32F407
· Espressif ESP32-WROOM-32D
· Winbond 128Mbit Flash device
· ISSI IS62WV10248EALL/BLL
The Autel Maxi comprises multiple boards. One board is dedicated to the display, one board is a metrology board for power measurement and distribution, one is a mobile communication module board, and, finally, there’s a CPU board.
Figure 1 - The Autel Maxi metrology board hosts the ST Micro STM32F407ZGT6 and Renergy RN830(B).
Figure 2 - The Autel Maxi mobile communication PCB hosts the Quectel EC25-AFX.
Figure 3 - The Autel Maxi CPU PCB hosts the GigaDevices GD32F407, an Espressif ESP32-WROOM, a Winbond flash storage chip, and a Barrot BR8051A01 Bluetooth radio.
Figure 4 -The reverse side of the Autel Maxi CPU board contains the Barrot BR8051A01 Bluetooth radio.
Figure 5 - A detailed look at the Barrot BR8051A01 Bluetooth radio.
ChargePoint Home Flex
The following list summarizes the components Trend Micro Research has identified as notable components and/or potential attack surfaces in the ChargePoint Home Flex EV charger.
· Atmel AT91SAM9N12
· Micron MT47H64M16NF-25E IT:M - 1GB DRAM
· Micron MT29F4G08ABBDAH4-IT:D - 4GB NAND flash
· Inventek ISM43340 Wi-Fi Bluetooth SIP Module
The ChargePoint Home Flex comprises two circuit boards within the device housing. Those boards are the metrology board and the CPU board. The CPU board hosts an Atmel ARM CPU, a Wi-Fi radio, and a Bluetooth LE radio. The CPU board is labeled CPH-50 CPU on the PCB silkscreen markings. Also, the unpopulated debug header labeled CN1 exposes the JTAG debugging interface of the Atmel AT91SAM9N12.
Figure 6 – ChargePoint Home Flex CPU board side 1, with Atmel ARM CPU, WiFi radio, and Bluetooth LE radio. P3 serial port labels have been added to the image.
Figure 7 – ChargePoint Home Flex CPU board, side 2.
The metrology board hosts an MSP430 microcontroller. It terminates the power connection from the power supply. It also terminates the charging cable that end users connect to the electric vehicle. The metrology board also provides power to the CPU board via a stacked PCB connector on the upper right of the metrology board. The metrology board is labeled with the identifier Panda AC 50 on the PCB silk screen markings.
Figure 8 – ChargePoint Home Flex metrology board side 1, with MSP430 microcontroller.
Figure 9 - ChargePoint Home Flex metrology board side 2.
Emporia Smart Home EV Charger
The following list summarizes the components Trend Micro Research has identified as notable components and/or potential attack surfaces in the Emporia Smart Home EV charger.
· Espressif ESP32-WROVER-IB
· TI MSP430F6736A
The device is built around the Espressif ESP32-WROVER-IB Wi-Fi and Bluetooth module. It is marked on the board as U1. The serial interface of the ESP32 is connected to the vias located directly next to the module labeled H3-H10. Identifying the pinout is an exercise for the reader.

Figure 10 - Emporia Smart Home EV Charger employs a single board design. The ESP32 module is to the left, and the MSP430 is in the center.
The Emporia Smart Home EV charger uses a TI MSP430F6736A microcontroller for the metrology function.

Figure 11 - Emporia Smart Home EV Charger detail image of the TI MSP430F6736A used for metrology.
Enel X Way Juicebox 40 EV Charger
The following list summarizes the components Trend Micro Research has identified as notable components and/or potential attack surfaces in the Enel X Way Juicebox EV charger.
· Silicon Labs WGM160PX22KGA3
· Silicon Labs MGM13S SiP Module
· Atmel ATmega328P
· Atmel M90E36A Metering IC
The following image shows an overview of most of the main PCB. The Silicon Labs WGM160PX22KGA3 is toward the top-left of the following image and is marked U3. The Silicon Labs MGM13S SiP Module is toward the lower left of the following image and is labeled U11. The Atmel ATmega328P is located left-of-center in the following image and is labeled U14.
Figure 12 - Enel X Way Juicebox 40 EV Charger main PCB hosts both application and metrology. The Silicon Labs WGM160PX22KGA3 is shown in the lower right of this figure, and the Atmel ATmega328P is shown in the middle.
The following image shows the right-hand side of the board. This is where the Atmel M90E36A Metering IC is located. It is located on the right-hand side of the board and is marked U25.
Figure 13 - Enel X Way Juicebox 40 EV Charger main PCB is shown with the Atmel M90E36A metrology processor shown to the right.
Figure 14 - Enel X Way Juicebox 40 EV Charger detail view of Silicon Labs WGM160PX22KGA3.
Phoenix Contact CHARX SEC 3100
The following list summarizes the components Trend Micro Research has identified as notable components and/or potential attack surfaces in the Phoenix Contact CHARX SEC 3100 EV charge controller.
· NXP MCIMX6G2CVM05AB - i.MX 6UltraLite Processor
· Infineon OPTIGATM TPM SLB 9670 TPM2.0
· Micron MT41K256M16TW-107 IT:P - 4gb DDR3 memory module
· Micron MTFC8GAKAJCN-4M IT - 64 Gbit MMC NAND flash
· Sierra Wireless RC7620-1
· STM32F303 Arm microcontroller
The Phoenix Contact CHARX SEC 3100 is an EV charging controller. The device is typically mounted on a DIN rail. The enclosure contains two PCBs interconnected via a bus at the rear of the enclosure. In this document, we refer to one PCB as the CPU Board, and the other as the Metrology Board.
The CPU Board hosts the NXP MCIMX6G2CVM05AB ARM Cortex A7 CPU along with its associated DDR3 and NAND flash components. Additionally, the CPU Board comprises two Ethernet interfaces, one USB C interface, a micro SD card reader, a micro SIM card slot, and a Sierra Wireless RC7620 cellular modem.
The Phoenix Contact CHARX SEC 3100 runs Linux, and the manufacturer provides access via a preexisting user account on the system.
Figure 15 - Phoenix Contact CPU Board Side 1. This CPU board contains the NXP MCIMX6G2CVM05AB - i.MX 6UltraLite Processor, the Micron MT41K256M16TW-107 IT:P - 4gb DDR3 memory module, and the Micron MTFC8GAKAJCN-4M IT - 64 Gbit MMC NAND flash.
Figure 16 - Phoenix Contact CPU Board Side 2. This side of the CPU board has two Ethernet controller chips and the Infineon OPTIGATM TPM SLB 9670 TPM2.0
The Metrology Board hosts the STM32F303 Arm microcontroller.
Figure 17 - Phoenix Contact Metrology Board Side 1. The metrology board hosts circuitry for power metering.
Figure 18 - Phoenix Contact Metrology Board Side 2. The metrology board hosts a STM32F303 Arm microcontroller and communicates with the CPU board over the inter-board bus connector shown on the left side of the board in this figure.
Ubiquity EV Station
The following list summarizes the components Trend Micro research has identified as notable components and/or potential attack surfaces in the Ubiquity EV Station.
· Qualcomm APQ8053 SoC
· Nuvoton M482LGCAE (ARM)
· Samsung KMQX60013A-B419 DRAM / NAND
· Realtek RTL8153-BI Ethernet controller
· Qualcomm WCN3680B (Wi-Fi)
· NXP PN71501 (NFC)
· TI USB 4 Port Hub - TUSB2046BI
· Qualcomm PMI8952 (PMIC)
· Qualcomm PM8953 (PMIC)
· UART DEBUG port
· USB C port
The following is an overview image of the main CPU board of the Ubiquity EV Station. The board has several collections of highly integrated components, each isolated inside its own dedicated footprint on the board. Each of these areas of the PCB appears to be dedicated to discrete functionality, such as CPU with RAM and flash, Wi-Fi, NFC, Ethernet, USB, and display.
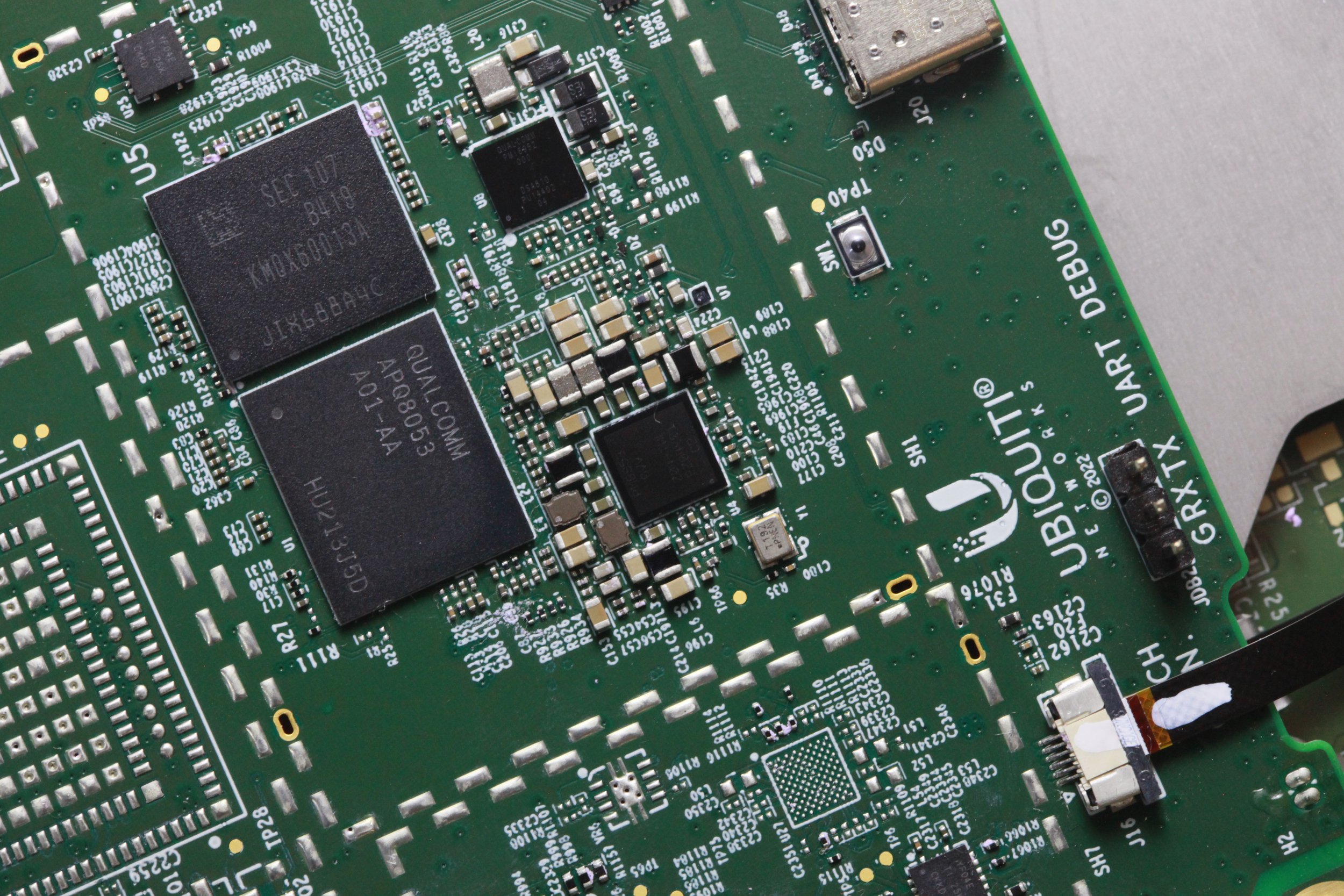
In the center of the board sits the Qualcom APQ8053 and Samsung KMQX60013A-B419 combination DRAM and NAND controller. These represent the primary application processor for the device, along with the RAM and flash storage for the device. They are marked U5 on the PCB silkscreen.
Just beneath this section of the PCB lie three connectors. A connector marked JDB2 and UART DEBUG emits boot messages from the Ubiquity EV Station upon boot. In the center is a USB C connector marked J20. To the right is a two-pin connector marked J28. The functionality of this connector is not yet understood.
In the top center of the following image is an unpopulated component marked U20. It’s possible this is an unpopulated footprint for a cellular communication module.

Figure 19 - Ubiquity EV Station CPU board. The Ubiquity EV Station is a highly integrated device based around a Qualcomm APQ8053 SoC.
The following image shows the Qualcomm CPU and associated RAM and NAND flash chip inside the Ubiquity EV Station:

Figure 20 - Ubiquity EV Station CPU board, showing details of the Qualcomm APQ8053 SoC and Samsung KMQX60013A-B419 combination flash storage and RAM device.
In the following image, the PCB shows a stencil marked “J23.” Trend Micro researchers endeavored to discover where this header is connected. They surmised it might be possible that the vias in J23 might be connected to a debug interface on the board. Upon further inspection, they determined the vias on J23 are connected to the unpopulated device marked U20.
Figure 21 - Ubiquity EV Station detail image of Realtek RTL8153-BI Ethernet controller.
Conclusion
We hope this imagery will inspire you to take a deeper look at the EV chargers to be targeted at Pwn2Own Automotive. Time is running out to register, with the deadline being January 18, 2024. As always, we recommend using basic electrical safety handling procedures whenever working with electrical devices. Potentially lethal voltages will be present within the unit, especially when powered from a 230VAC source. We hope to see both you and your exploits in Tokyo.
Until then, stay tuned to this blog for attack surface reviews and how-to guides for other devices, and if you’re curious, you can see all the devices included in the contest. Until then, follow the team on Twitter, Mastodon, LinkedIn, or Instagram for the latest in exploit techniques and security patches.
如有侵权请联系:admin#unsafe.sh