Fast food chains’ growth has increased by an average of 5.75% in the second quarter of 2023. Covid, the Ukraine-Russia war, and supermarket greediness has tremendously increased the food prices, whereas the fast food prices increase in a much slower pace. This makes it a viable nurturing option for many people, thus increasing the fast food companies’ profits. And I can only assume that some of this profit increase will be invested in the means of production and ways to further increase profits in the long and short term.
When it comes to cybersecurity, one of the biggest fast-food companies, Yum! Brands, was hit with ransomware in 2023. It was even reported that employee data were stolen during this attack.
So you can see that, inspite of the profit gain, cybersecurity is still a threat for damage. Of course, such large companies are hard to manage, security-wise. But did they learn from past mistakes?
PepsiCo Access to Staging/Dev API Environment leaks Employees’ Emails, Email Servers, and possible patrial AWS Credentials Leak.
@messede showed me the responsibledisclosure.com project by Synack. Multiple companies, including PepsiCo, use responsibledisclosure.com to create a VDP platform, so users can report vulnerabilities on their systems. Messede had found a pretty critical issue on KFC (more on that below), so I thought of giving it a try with PepsiCo, as it would be suitable to also research a fast-food-like company.
Discovery
As you may already know, Shodan surfing can take you places. My standard approach is the classic ssl:domain.tld filter, then depending on the number of the hosts, I go through them manually or using a flyover tool to screenshot them and go over them locally. Although there were more than 300 results, I decided to first manually browse the Shodan results.
When going over Shodan results, it’s important to note the hostnames. IPs or HTTP titles may not give a lot away, but hostnames are the number one source for developers to identify hosts. One of the hosts that cought my eye was one with the name “testapp”. Always intruiging.
Enumeration and useless IDOR
The application was looking indeed like a test application. Four simple buttons: Login, Create Account, Forgot Password, and Social Login. Nothing more.
The Create Account button redirected me to another app that looked a lot more stable. After creating an account, I started looking around the API and the application itself, looking for information, only to find some email addresses of the PepsiCo contractor that built the application. Requesting their email addresses to the API and…
Although that is an IDOR indeed, the application is built only for testing purposes. We got some PII of the contractor itself, but there isn’t a user base to leak any information.
Directory listing
After examining the API requests and the web application I started to look closer into the API structure. Directory fuzzing revealed that it was possible to list the directories that the API was utilizing. So, that way I recursively downloaded everything I could. Visiting the directories I acquired
showed that this API was hosting multiple consumers/testing applications. In those directories, were found partial AWS keys (only one key of the pair needed to access n AWS environment), email server hostnames, and their encryption keys
and the emails of the developers
Although a minor finding, this certainly provides some more insight on the way PepsiCo operates, as well as some email addresses of developers and people associated with it.
KFC Authentication Bypass and API Exposure leaks Millions of Receipts with PII
TLDR:
- Found a “ordering system” web app while look for food-chain related infra on shodan.
- WebApp employed client side checks for authentication, could be easily bypassed by settings a localStorage variable
- Led to discovery of a api endpoint which discloses customer phone number, delivery addresses, and order details.
This is one of those bugs that you can find without ever leaving the browser, it also highlights the importance of enumerating the UI frameworks (React in this case).
We started with a random search for “KFC” on Shodan, while filtering results through countries, we came across an interesting result on AWS Mumbai, a site seemed to be some sort of order management/administration system.
First order of business when dealing with a webapp is to pop open devtools and see what we are dealing with, so thats what we did.
Luckily we had js source maps, so we didn’t have to read through uglified js code. The imports make it clear that we are dealing with React, the route map gave us a few interesting endpoints to explore.
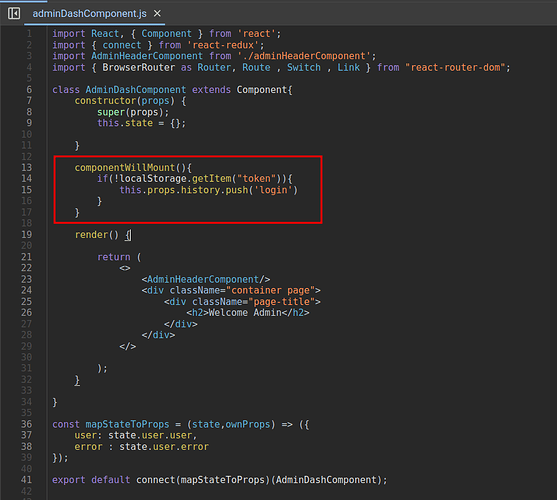
So we tried visiting /admin directly and were immediately thrown back to the login page. It was time to take a look at that AdminDashComponent the routemap was referring to.
All the adminComponent did in the name of authorization was check if a localStorage item “token” exists, we happily set the token manually to a random value.
We now tried visiting /admin and voila!
The API was too unstable to get all of the results. With some simple trial and error, we found out that the first entries were from October 30, 2021. We observed that there was an average of 5000 orders per day (more on the weekends, but let’s keep it like this.) From the first day, i.e. 30th of October, until the time of writing (November 8th, 2023) 739 days have passed. This leads to appr. 3.695.000 receipts. Of course, not all of them contain PII. PII could be observed only in delivery receipts, where home addresses, phone numbers, and names were printed out.
Also, when examining the receipts, we came across some interesting delivery addresses and orders, such as a military station.
Disclosure
Both vulnerabilities were reported around the same time through responsibledisclosure.com. We have waited for 90 days to pass, in the hope for both vulnerabilities to be patched.
UPDATE: As of December 2023, both vulnerabilities seem fixed!