2023-12-6 21:35:32 Author: www.forcepoint.com(查看原文) 阅读量:7 收藏
In our previous blog post, we delved into the world of risk management, uncovering its significance in shaping a secure digital future.
The NIS2 Information security awareness requirements include:
Today we will focus on Information security awareness and hygiene best-practices which play a crucial role for achieving NIS2 Compliance.
- General cybersecurity awareness
This includes topics such as identifying and reporting security incidents, safe use of IT and best practices for protecting sensitive information. - Role-specific cybersecurity awareness
For example, employees who have access to sensitive information should be trained on how to protect the data from unauthorized access. - Regular training
Cybersecurity awareness to all company employees to keep them up-to-date.
Preparing for NIS2 requires the cooperation of all employees, from those with little cyber security knowledge to the most skilled CISO.
Traditionally humans have been considered the weakest point in regard to cybersecurity. That’s why information security awareness is so important. An educated employee will be less likely to be impacted by a cyberattack, even if the organization has spent millions of Euros on the best security solution in the market.
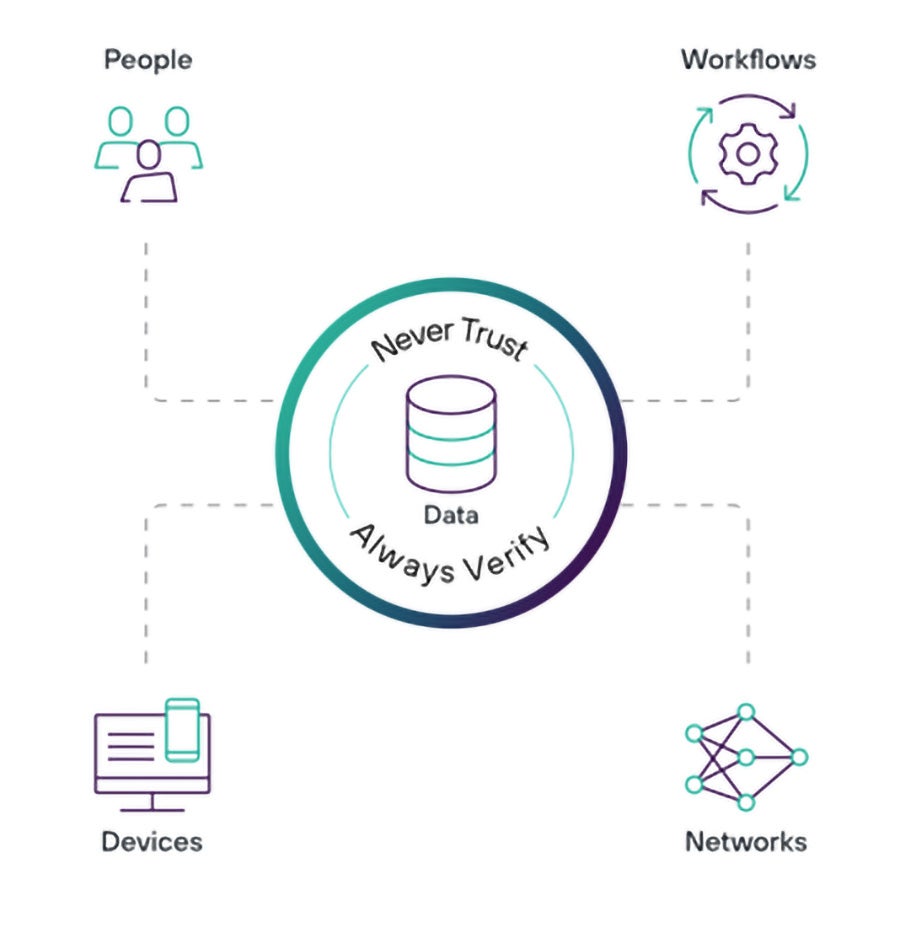
Therefore, we must foster a culture of security consciousness to minimize human-related risks. Zero Trust is a basic principle in each of Forcepoint solutions. Never trust, always verify, assess the risk, and provide access only to what’s required.
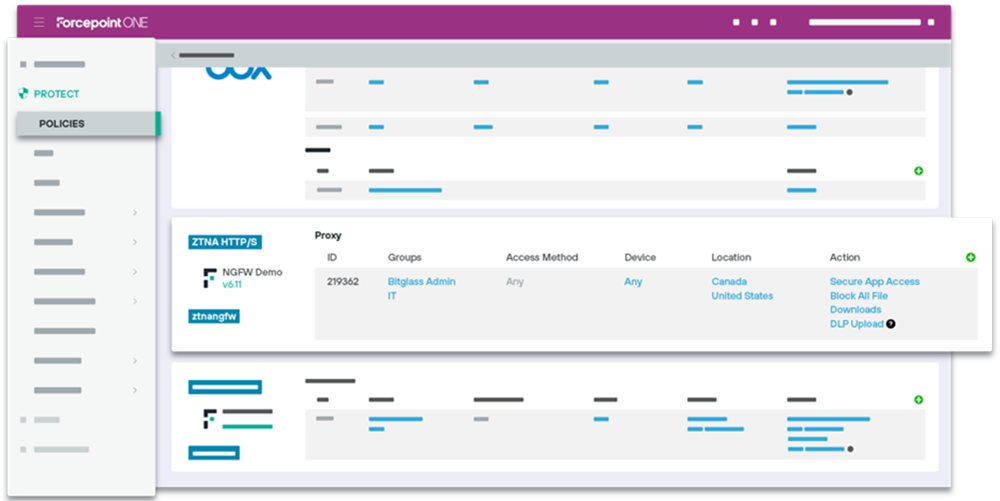
 With Forcepoint ZTNA. we are able to provide access to internal sensitive services only after carefully inspecting the user, as opposed to traditional VPN solutions we will provide access only to the required internal resource avoiding lateral movement in the network.
With Forcepoint ZTNA. we are able to provide access to internal sensitive services only after carefully inspecting the user, as opposed to traditional VPN solutions we will provide access only to the required internal resource avoiding lateral movement in the network.
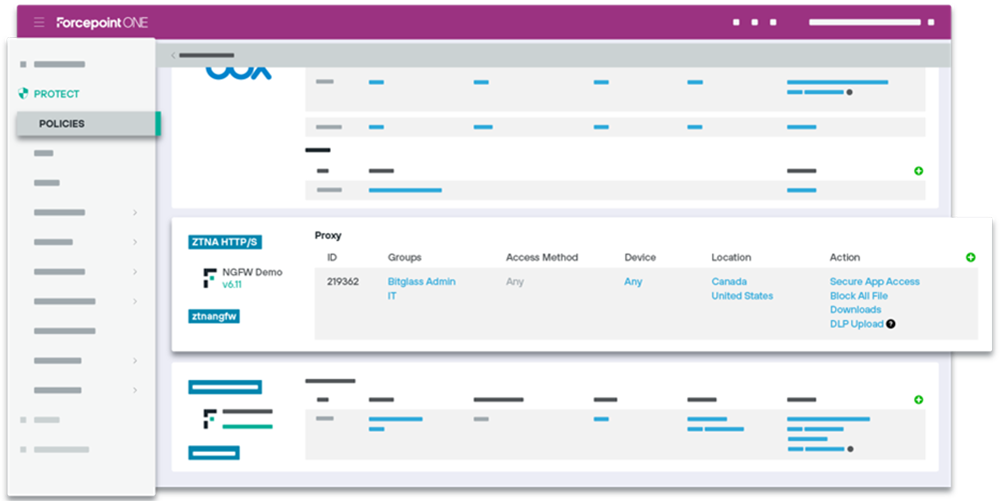
While the traffic would still be fully inspected with DLP capabilities, and many additional security engines such as Zero Trust CDR.
ZT CDR will transform the file into a safe file removing all known and unknown malicious content, while making sure nothing hidden is travelling along with the file.
This is a proprietary patented technology giving 100% protection from threats in files and is able to provide full protection as well from steganography attacks.

Our RBI solution is able to provide isolated web environment so any attack which originated from the web would not be able harm the organization , as it would be fully run in a remote container which will be wiped once the end user has finished browsing the site, and any file which need to be downloaded would be scanned first and transformed using our ZT CDR.
With RBI we are also able to provide read only access to suspicious based on continuous risk scoring and assessment of the site.
Coaching capabilities is also a key factor, as technology would never be sufficient to mitigate all possible risks,
This helps us to educate the end user, warn them of risky activities so the next time the end user would be less likely to behave in a risky manner.
We can coach the end user when trying to use web services which are not approved by the cyber security team, redirecting them to an approved solution.
Our DLP solution can show a popup message before blocking an action which involves sensitive information, allowing the end user to provide justification in case this is a false-positive related to standard work procedures.
Forcepoint has a range of cybersecurity solutions that can help organizations with their NIS2 transformation journeys.
Forcepoint's Data-first SASE solution and each of its building blocks discussed in the series will greatly enhance your compliance toward NIS2.
We are committed to working with our customers to find the right tools and processes to prepare their businesses for NIS2 and beyond.
In case you missed other parts of our NIS2 series, you can read them here:
如有侵权请联系:admin#unsafe.sh