2023-12-6 21:36:37 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a two-step security testing methodology. The first step is Vulnerability Assessment, in which our team identifies all vulnerabilities in an application or network. However, this method cannot differentiate between exploitable and non-exploitable vulnerabilities. The second step, Penetration Testing (PT), comes in here. PT takes the vulnerabilities identified in the first step, identifies exploitable vulnerabilities, and attempts to exploit them. Combining these two methods in VAPT helps organizations better understand their current security vulnerabilities, how exploitable they are, and the potential impact they could have.
How does it work?
Let’s say that you hired a robber to try and break into your business (in this universe, let’s pretend ethical robbers exist). Any skilled robber would do some investigation before the actual break-in. They would identify any obvious vulnerabilities, like in VA, initially like…
- Unlocked doors
- Security codes posted in a visible place
… and figure out how to exploit them, like in PT. Next comes the main event, the actual robbery! The robber would identify exploitable vulnerabilities and continue onward to exploit them.
In their first attempt, they try to get in through an unlocked door. Congrats! You have a security system enabled so the bad guy gets caught before they can get access to your data. This is a good example of having an effective security protocol in place to protect your data and network.
In their second attempt, they spotted a sheet of paper taped behind the register with your door security code written on it. They gain entrance to your storefront and enter the security code. Sadly, the robber broke into your business and got access to your payment information, credit card data, customer data, and inventory data. This is an example of having a poor security protocol in place because while you may have a security system, the credentials to disable them might as well have been plastered on a billboard.
The ethical robber would report their findings to you and provide insight on how to solve the issues they identified and ultimately improve how secure your business would be against an attack in the future.
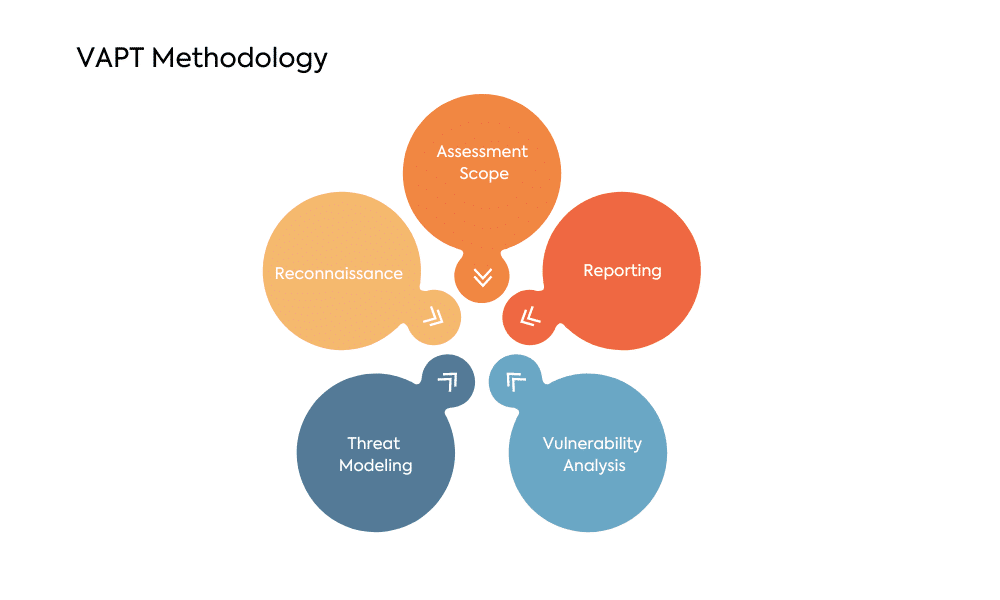
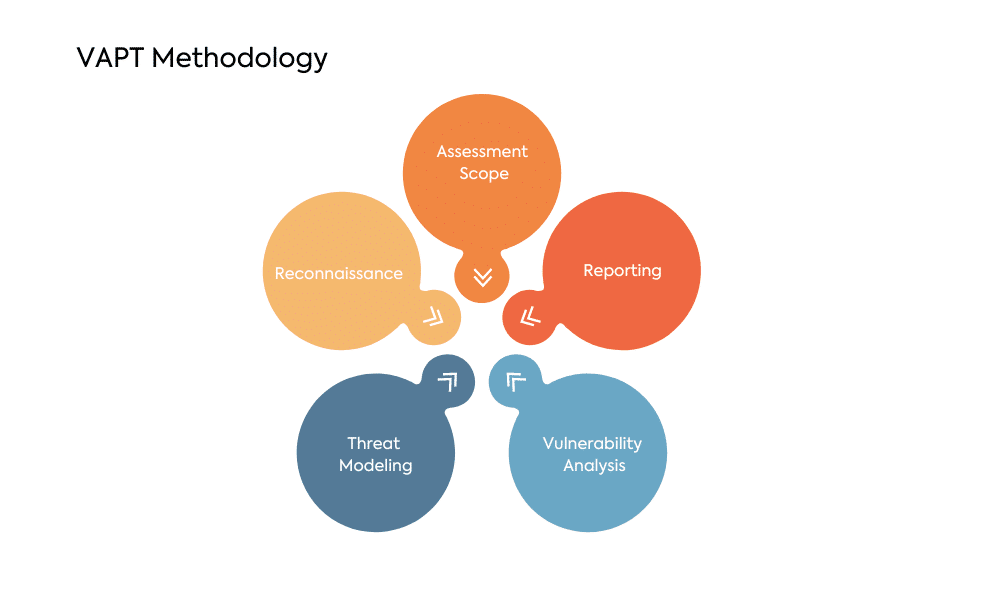
VAPT Methodology
Vulnerability Assessment
Vulnerability Assessment is the first line of defense in VAPT. It involves a systematic review of systems, applications, and networks to identify potential vulnerabilities. This process employs specialized tools to scan and analyze the infrastructure, providing a comprehensive view of potential weaknesses.
Penetration Testing
Penetration Testing takes the assessment a step further by simulating real cyberattacks. Ethical hackers, often internal or external security experts, attempt to exploit identified vulnerabilities to evaluate the system’s security response. This hands-on approach helps organizations understand their security gaps in a controlled environment.
Why is VAPT Important?
- It helps to protect your organization from cyberattacks. Cyberattacks are a growing threat, and they can cause serious damage to your organization. VAPT can identify and fix vulnerabilities before attackers can exploit them.
- It can help you to comply with regulations. Many regulations require organizations to perform VAPT regularly. VAPT can help you to ensure that you are meeting your compliance obligations.
- It can help you improve your overall security posture. VAPT can help you identify and address security weaknesses that you may not be aware of. This can help you to improve your overall security posture and make it more difficult for attackers to compromise your systems.
- It can help you save money. Cyberattacks can be very expensive. VAPT can help you prevent cyberattacks from happening, which can save you money in the long run.
By becoming aware of what vulnerabilities exist in live products, weaknesses in different steps in the SDLC become apparent. Things like under-trained staff, current lack of security protocol, and overall lack of awareness can detract from your organization’s security posture as a whole. However, even without the mentioned weak points, vulnerabilities occur.
No development staff is perfect, and so there will always be overlooked vulnerabilities. Luckily, at WeSecureApp – a Top VAPT company, actively pair automated tools and our team of highly skilled ethical hackers to provide you with a thorough VAPT report. With regular VAPT audits and testing, you can rest assured that your data and your reputation are safe.
Recommended Reading
Top 7 Penetration Testing Companies in the USA
The post Understanding VAPT: A Simple Guide to Vulnerability Assessment and Penetration Testing appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by WeSecureApp. Read the original post at: https://wesecureapp.com/blog/understanding-vapt-simple-guide-to-vulnerability-assessment-and-penetration-testing/
如有侵权请联系:admin#unsafe.sh