This is an interesting challenge that contains an attack on a WordPress site using multiple IP addresses and techniques to breach the site. Our goal is to identify the attacker and their methods by analyzing the Apache access.log file. There are 6 question in the challenge and we will use Linux CLI to solve this.
If an attacker is attacking a web application, he/she might try to login to the admin panel. If they don’t have the required credentials, they may try to brute force the account. This approach is noisy and reports a lot of login failure events in the access.log file. So first lets count the authentication failures for each IP.
cat access.log | grep "403" | cut -d " " -f 1 | sort | uniq -c | sort -nr

So the IPs to investigate are 110.29.54.120, 168.22.54.119, 197.23.128.35 and 119.241.22.121
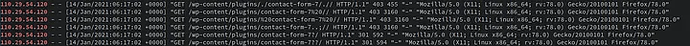
When we investigate the first IP in the list: 110.29.54.120 we see a large number of login failures.
cat access.log | grep "110.29.54.120"
Anyhow the above picture contains the answer to the first question in the challenge.
Interestingly before all those failures, this IP successfully made a couple of logins to the admin panel. However after all those login failures, this IP tried to enumerate the contact form 7 plugin, but had no luck.
Now if we investigate the second IP: 168.22.54.119 and match the wp-login attempts using the following command, we see something that looks like an SQL injection payload.
cat access.log | grep "168.22.54.119" | grep "/wp-login.php?itsec-hb-token=adminlogin"
The payload is url encoded and if we decode it, it translates as follows:
2151+AND+1=1+UNION+ALL+SELECT+1,NULL,'<script>alert("XSS")</script>',table_name+FROM+information_schema.tables+WHERE+2>1--/**/;+EXEC+xp_cmdshell('cat+../../../etc/passwd')#
Please note there are few more SQLi payloads other than the one shown here. So we can suspect this attacker might have used something like sqlmap. To verify this we can isolate the user agent and analyze.
cat access.log | grep "168.22.54.119" | cut -d " " -f12-
And as we suspected, we can see sqlmap user agent in the logs:
If you examine the SQL injection payload, it tries to get a command shell using xp_cmdshell. However, the command xp_cmdshell is a MS SQL Server command so the attacker might be assuming that the wordpress site is using MS SQL Server for linux. Please check the links below.
Additionally this IP had access to the admin page for a brief period of time. However it seems after trying some other SQL injection payloads, the IP got logged out of the account.
Another interesting thing with this IP is, it tried to enumerate two plugins, Contact Form 7 and Simple File List.
cat access.log | grep "168.22.54.119" | egrep "contact|simple"
These two plugins are vulnerable to Arbitrary File Upload. This means an attacker can upload any file to the server, for example a webshell. If you simply search Contact Form 7 arbitrary file upload on duckduckgo, you will find the corresponding CVE (Link below) and that answers the 3rd question.
The other plugin that is vulnerable is Simple File List. If you search again for a Simple File List exploit, you can find the following link that explains the exploit and the affected version, which answers the 4th question.
https://wpscan.com/vulnerability/365da9c5-a8d0-45f6-863c-1b1926ffd574/
Now lets go ahead and analyze the next IP on the list, 197.23.128.35.
It seems this IP also had some success with admin login before getting a lockout.
After the lockout, it seems this IP tried various attacks, but without a success.
So now, to the final IP address: 119.241.22.121. Now, a lot of things has happened with this IP as well.
First of all, just like the IP 168.22.54.119, this IP also tried to exploit the two plugins: Contact Form 7 and Simple File List.
Then it goes on and try a bunch of enumerations to find login portals and control panels:
Then it gains some access to the admin account before getting logged out of it.
Since this is an interesting IP address, lets check the user agents used by this IP. We issue the command like before but with this IP address.
Here we see something interesting, the attacker used WPScan to enumerate or exploit the WordPress site. So now we know the two tools used by the attacker: sqlmap and wpscan. This answers the 2nd question.
Finally, the attacker has figured out that it is better to use a webshell to access the server. Hence he/she exploited the Simple File List plugin and uploaded the fr34k.png file.
Now we have a lead. The attacker found a way to exploit the application. So lets see if there are any other files with the same name “fr34k”
cat access.log | grep "fr34k"
Yeah so we have a bunch. What stands out is fr34k.php and this is probably a webshell which the answer to the 5th question. Interestingly the webshell upload was done by using a different IP address: 103.69.55.212 which had only one 403 Forbidden case.
Finally if we match the IP: 103.69.55.212 and the word “fr34k.php” we get all the logs corresponding to the webshell.
cat access.log | grep "103.69.55.212" | grep "fr34k.php"
Here, at the end we see when the attacker tried to access the webshell he/she got a 404 error and this answers the 6th question.
This is a very interesting challenge that teaches you how to use Linux CLI to analyze the web server logs. To prevent such an attacks, one can use Web Application Firewalls (WAFs). There is a plenty of WordPress WAFs available and you can also use application agnostic WAFs like CloudFlare or CrowdStrike to mitigate such attacks.
Originally published on Medium: Blue Teams Lab: Log Analysis — Compromised WordPress | by Higgsborn | Dec, 2023 | Medium