2023-12-11 22:0:36 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
SentinelLabs, Microsoft and PwC jointly issued an alert that threat actors thought to be associated with cybercriminals based in China have adopted an advanced persistent threat (APT) known as Sandman to insert malware in IT environments.
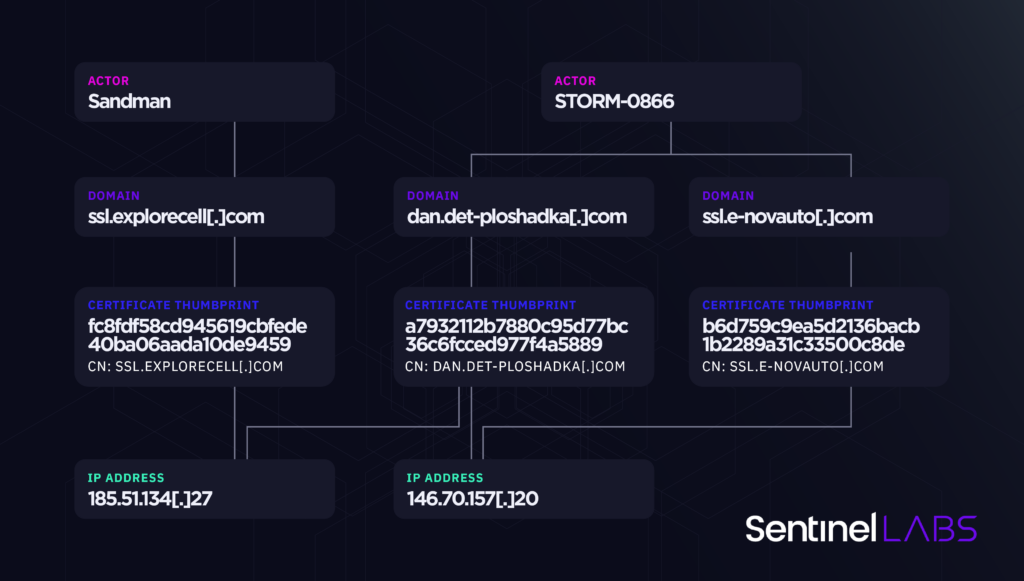
Aleksandar Milenkoski, senior threat researcher at SentinelOne, said the Sandman APT has now been linked to STORM-0866/Red Dev 40, a threat actor that is aligned with advancing the national interests of China.
Sandman was first discovered being used by Western intelligence agencies but is now being employed more widely, noted Milenkoski. The Sandman APT leverages KEYPLUG backdoor malware to insert another type of malware, dubbed LuaDream, that makes us of evasion and obfuscation techniques that make it more difficult to detect, noted Milenkoski.
It’s now been discovered that Sandman is communicating via infrastructure control and management practices, including hosting provider selections and domain naming conventions, typically associated with aSTORM-0866/Red Dev 40.
The malware created by Sandman is also finding its way into other cyberespionage tactics and techniques used by intelligence agencies around the world to compromise IT environments, noted Milenkoski.
It’s not clear to what degree cybercriminals working on behalf of various intelligence agencies are sharing tactics and techniques versus merely copying them, but it’s clear that once any type of variant of malware is shown to be effective, it’s not long before it becomes more widely employed. As such, cybersecurity teams should pay more attention to malware being developed by any intelligence agency on the assumption that variants of it will not only be adopted by other governments but also by cybercriminal syndicates looking to exploit weaknesses for financial gain.
Governments around the world are going to continue to invest in developing malware to advance their national interests. Still, it’s only a matter of time before that malware is discovered and then used by others. It’s not uncommon for a variant of malware developed by one government to one day be used to attack organizations within the borders of the government that originally created it. As such, claims that one country is attacking organizations more than others often tend to ring hollow with cybersecurity teams that are, in effect, being attacked from all sides.
Making matters more challenging still, threat actors of all types are investing in artificial intelligence (AI) capabilities that promise to make it easier to both create and distribute malware.
Cybersecurity teams, as always, are largely dependent on security vendors to identify and ultimately thwart new types of malware. The challenge is that as the pace at which more advanced malware is developed continues to increase, there will need to be a corresponding increase in the research required to identify it. In essence, the pace at which the cat-and-mouse game in which cybersecurity researchers are engaged is only going to increase.
Cybersecurity teams, as a result, will need to revisit the workflows they currently rely on to combat emerging threats. After all, the primary victims of the malware being developed are most often organizations that are ultimately little more than collateral damage in a contest playing out at a global scale few of them have any ability to actually affect.
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
