2023-12-12 22:3:7 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Reco today launched a platform that makes use of machine learning algorithms and graph technology to secure software-as-a-service (SaaS) applications.
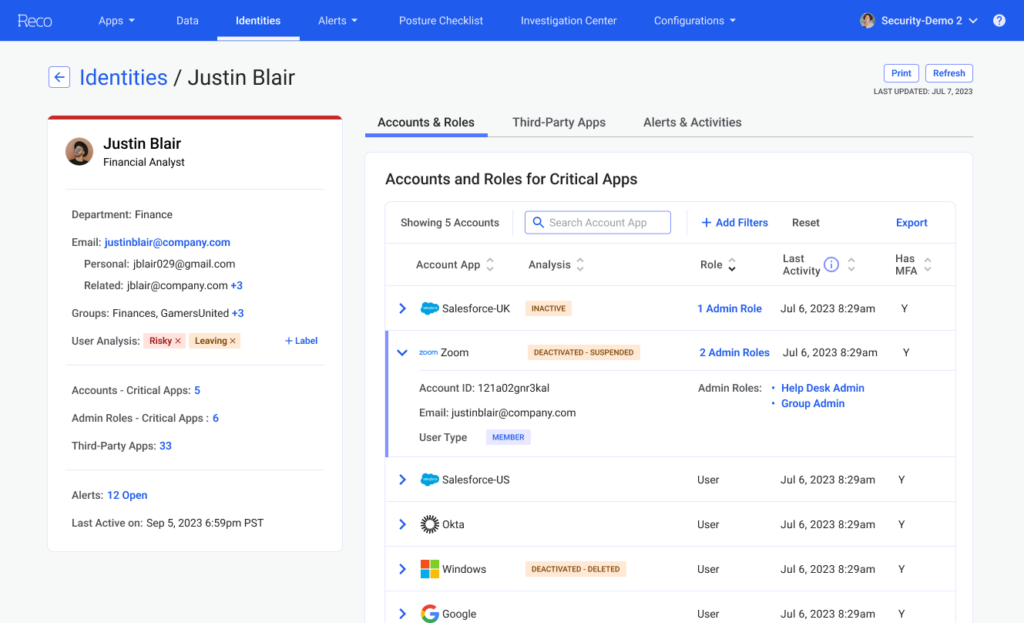
The Reco Identities Interaction graph technology connects to SaaS applications via its application programming interface (API) to establish and track the relationship between applications, data, accounts, permissions and end users.
Reco CEO Ofer Klein said that approach to SaaS security posture management (SSPM) will enable cybersecurity teams to take advantage of graph technology enabled by artificial intelligence (AI) to continuously secure the fastest-growing attack surface in the enterprise.
Cybersecurity teams can employ the Reco platform to also discover and protect any SaaS applications that employees have begun to use with or without authorization, he added. Cybersecurity teams can then control access and prioritize actions to reduce risks.
In addition, the platform can be used to discover historical interactions with applications as the underlying graph technology discovers the SaaS application environment, noted Klein.
By employing graph technology, Reco is promising to significantly reduce the time and effort that would otherwise be required to secure SaaS applications. The pace at which these applications are being adopted continues to outpace the ability of cybersecurity teams to protect attack surfaces, Graph technology enabled by AI provides cybersecurity teams with an approach that continuously discovers interactions with SaaS applications.
The issue that cybersecurity teams are contending with is that while they are held responsible for data security, they often lack the authority to prevent end users from subscribing to a SaaS application. The Reco approach provides a method for applying security controls to any SaaS application that exposes an API. The graph technology employed by Reco was originally developed by the Israeli military to discover relationships between online activities of terrorists, noted Klein.
It’s not clear how quickly cybersecurity teams are embracing AI to secure IT environments, but as the overall attack surface continues to expand, the ability of chronically short-staffed cybersecurity teams to protect platforms is limited. AI technologies provide a mechanism that helps level a playing field that, today, is decidedly tipped in favor of cybercriminals.
The challenge, as always, is finding the budget for additional cybersecurity platforms at a time when many organizations are looking to either contain or outright slash IT spending. The fact of the matter is, however, that as the attack surface continues to expand, the amount of budget dollars allocated to protecting those platforms will need to increase.
In the meantime, it’s safe to assume that cybercriminals are either already or soon will be leveraging AI to find and exploit weaknesses. The only difference is the amount of budget they can allocate to experimenting with new technologies is considerably higher than the average IT organization.
One way or another, however, as data protection regulations become more stringent, organizations will need to address SaaS application security in a way that goes well beyond the controls that any single provider of those applications may make available.
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
