2023-12-13 05:38:56 Author: blog.sucuri.net(查看原文) 阅读量:26 收藏
In this post, we will look at how to use WPScan as a WordPress vulnerability scanner. This security tool provides you with a better understanding of your WordPress website and any vulnerabilities that may be present in your environment. It also happens to be pre-installed in Kali Linux. If you haven’t set it up yet, be sure to check out our post on installing WPScan to get started with the software.
Contents:
- How to scan and analyze your WordPress site
- How to start using WPScan
- How to run a basic scan
- How to scan WordPress for vulnerable themes and plugins
- How to check user enumeration
- How to test a password attack
- Enumeration options
Big threats come from unexpected places
Imagine for a second that you’re a survivor in a zombie apocalypse.
You’ve holed up in a grocery store, barricading windows and checking door locks. Things seem pretty quiet and secure. But just as you sit down to enjoy an oversized can of chocolate pudding, a thought crosses your mind. A bunch of thoughts, really.

You remember all the times you’ve seen this exact scenario in zombie movies. You start thinking about all the unknown possibilities that could still expose you to the horde:
- Faulty window fittings that’ll give with too much pressure
- A nasty gang that raid supplies from this spot every couple weeks
- A fire alarm that erratically triggers and draws zombies from miles around
- A very-real dumpster fire that’s growing outside and could set the whole place ablaze
- A backroom freezer where previous inhabitants locked a dozen very-hungry zombies
Wouldn’t it be nice if you could scan the entire grocery store in a way that would reveal if those potential problems were real problems?
Well, a double-sized helping of good news:
- You’re not living in a zombie apocalypse.
- WPScan does exactly this for your WordPress website.
How to scan and analyze your WordPress site with WPScan
WPScan examines your site in the same way most attackers do: It enumerates details and checks them against its database of vulnerabilities and exploits.
Having this information in your own hands, you can more precisely address issues that might not be readily apparent.
How to start using WPScan
A command line will, of course, be your base of operations.
If you’ve installed WPScan, always begin with an update. After all, if everyone knows about a potential issue but you, you’re ripe for an attack.
Use this command:
gem update wpscan
If you installed on Mac with the Homebrew approach, use this instead:
brew upgrade wpscan
How to run a basic scan with WPScan
When using WPScan, your command will always start with wpscan, and then it’ll point the tool to your URL.
wpscan --url yourwebsite.com
Running the command above will perform a basic scan of your site. After a few minutes, you’ll have a whole bunch of “Interesting Findings” that WPScan discovered from your site’s code. That could include information like:
- Headers to discover server information
- Accessibility of xmlrpc.php
- Accessibility of wp-cron.php
- WordPress version
- Active theme and its basic information
- Active plugins and their basic information
- Discoverable Config backups
Different site and server configurations might reveal different information.
Troubleshooting firewall restrictions
If your site runs behind a firewall and you’re encountering issues, you can try the following commands to reduce noise and bypass restrictions. These may not work on some firewalls, however.
Random user agent
Test different user agents by adding the –random-user-agent option to the end:
wpscan --url yourwebsite.com --random-user-agent
Throttle (Milliseconds)
Define the number of milliseconds that should pass before making another request, which can help with navigating rate-limiting checks:
wpscan --url yourwebsite.com --throttle 2500
Stealthy mode
Try the stealthy mode alias that combines the following scan options to most effectively avoid nose and bypass restrictions: –random-user-agent –detection-mode passive –plugins-version-detection passive
wpscan --url yourwebsite.com --stealthy
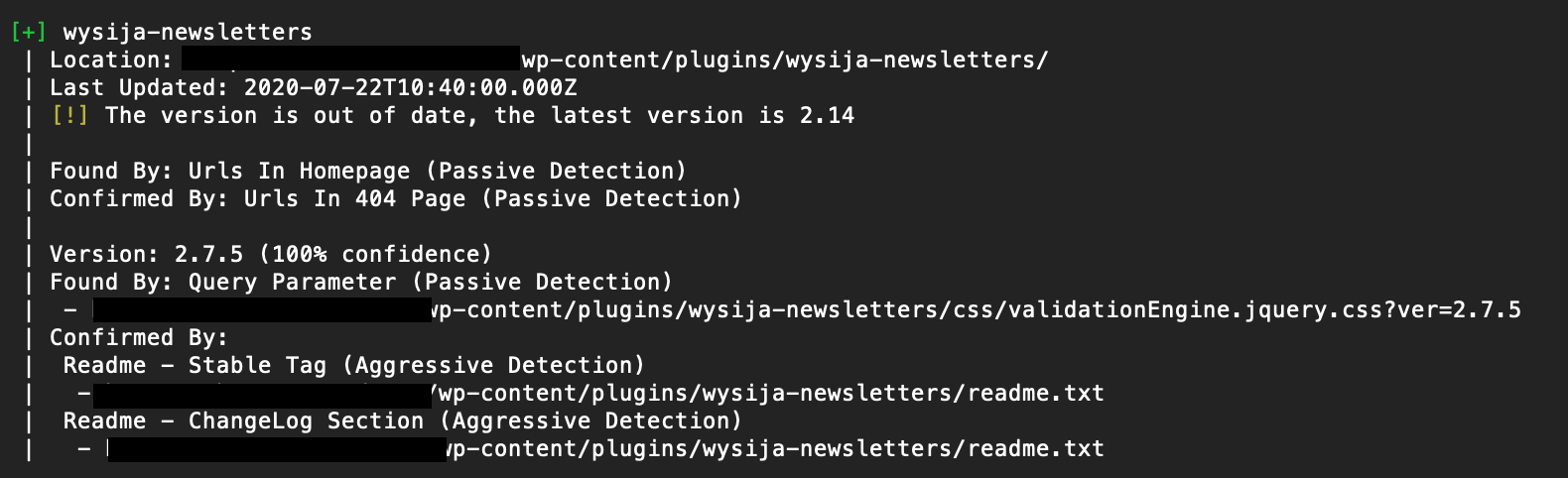
How to scan WordPress for vulnerable themes and plugins
While a basic scan will show you if a theme or plugin version is out of date, it won’t tell you if there are specific vulnerabilities with that version. To get that info, you’ll need to utilize the WPScan Vulnerability Database API.
In our WPScan installation guide, we had you register to use the API. You’ll now insert your unique API token into a scan in order to access this specialized information.
You’ll also add some additional flags based on the specific information you want to get. The most important one in this case is -e (which stands for “enumerate”) and the choice of vp (which, you guessed it, stands for “vulnerable plugins”).
Here’s the most-common command to search for vulnerable plugins:
wpscan --url yourwebsite.com -e vp --api-token YOUR_TOKEN
Keep in mind that this will take a lot longer than the basic scan. In some cases a five-minute basic scan may become a 25-minute vulnerability scan.
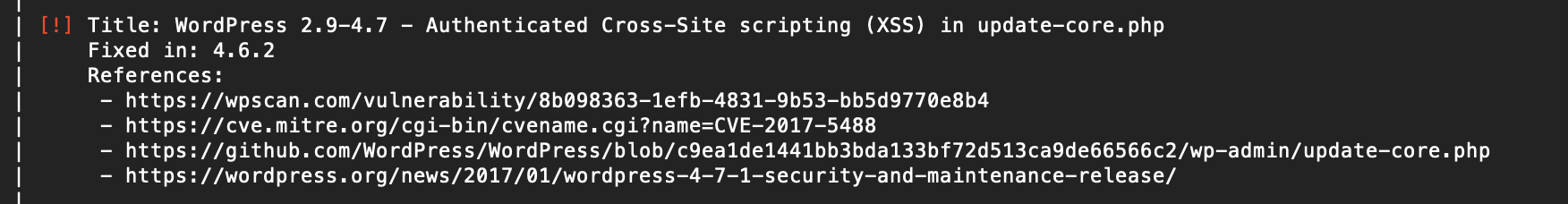
Here’s the same detected plugin from the scan above, but using the vulnerability database:
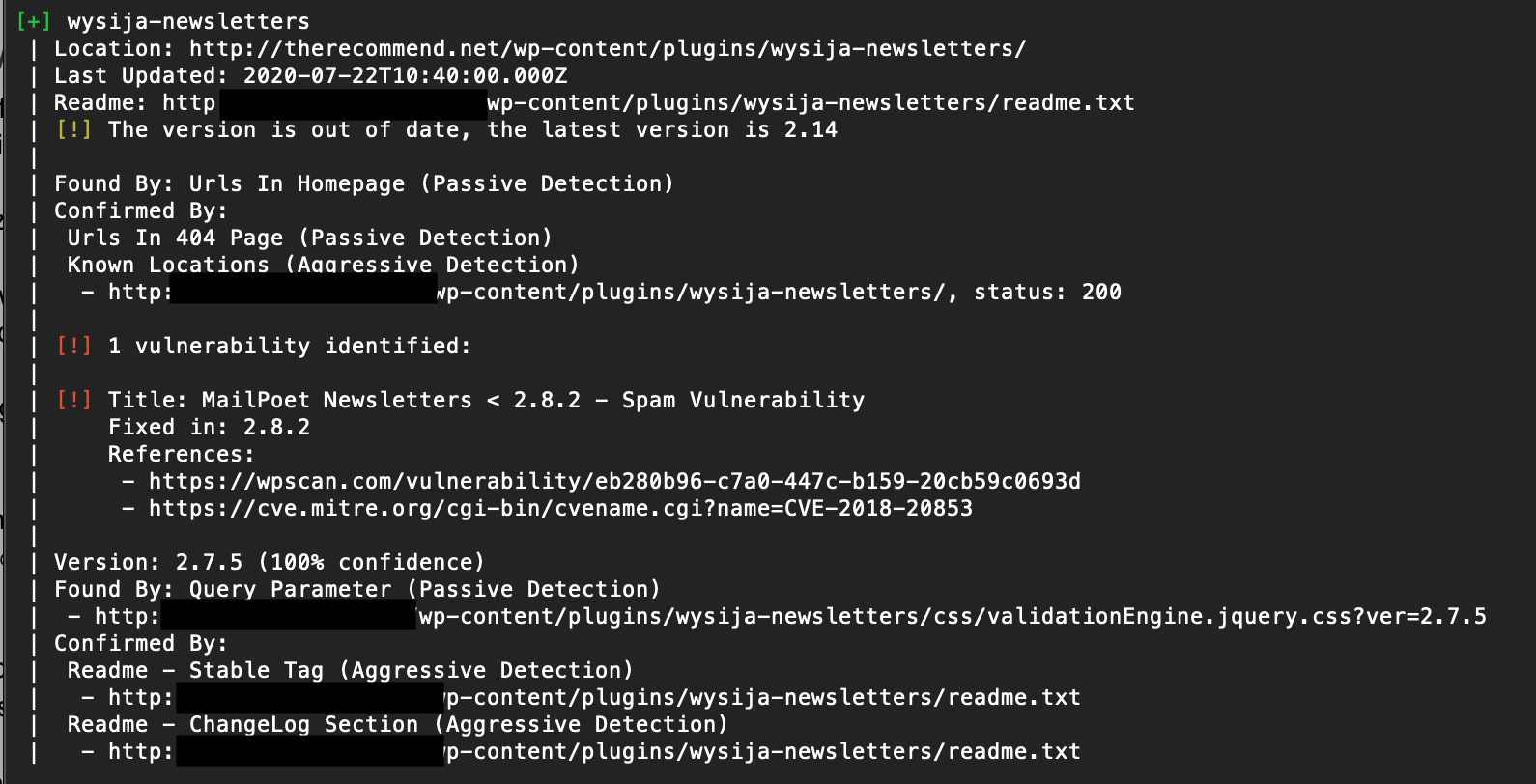
To check your site for a vulnerable theme, replace the vp with vt (“vulnerable themes”). Everything else can stay the same.
wpscan --url yourwebsite.com -e vt --api-token YOUR_TOKEN
On top of the theme or plugin vulnerabilities, WPScan will also report any vulnerabilities with the version of WordPress your site is running.
How to check user enumeration with WPScan
Don’t stop at vulnerable plugins and themes, though. Password attacks pose another big threat to your site’s security. And WordPress can provide attackers with the critical access and information they look for.
With WPScan, you can determine what usernames are discoverable from the outside.
To run this enumeration scan, we’ll use this command:
wpscan --url yourwebsite.com -e u
You can probably guess what the “u” stands for.
WPScan will use a few different techniques to do its own guessing: determining usernames based on the information available publicly on your site (i.e. author names). WordPress will tip its hands in some subtle ways as WPScan probes those guesses. (The blacked out content below are discovered user IDs.)
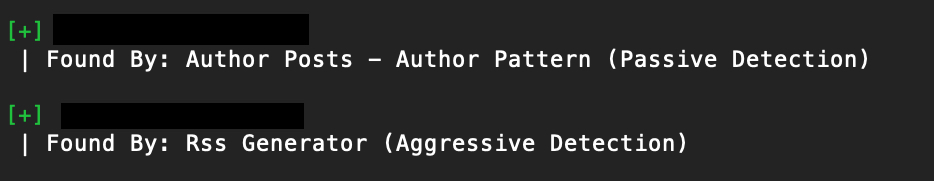
Ideally, you don’t want any usernames to be discoverable with these techniques. The easiest way to prevent that is by using different publicly visible nicknames than your user IDs.
Why does user enumeration work on WordPress?
By default, WordPress is prone to user enumeration. This is because of permalinks, a feature that provides permanent URLs to individual WordPress posts and pages.
Notably, WordPress lets you list all posts by a specific author’s username or ID, which could be exploited by attackers to identify valid usernames. This is where WPScan’s enumeration tool comes in handy, as it quickly checks if your WordPress site is susceptible to user enumeration.
Attackers strive to collect information about the targeted website, like usernames, plugin names, their versions, themes, and other factors. Knowing usernames alone might not enable an attacker to breach your site, but this information can aid them in crafting their attack strategy.
How to test a password attack with WPScan
How does an attacker follow up discovering a username? By attempting to access its account, of course.
WPScan actually allows you to simulate this. And this will be especially helpful if the site you’re managing has a lot of contributors: corporate sites, collaborative blogs, and the like.
First, you’ll need to get or create a list of passwords. With a quick Google search, you can find a number of lists of the most commonly used passwords, including the often-used rockyou wordlist. Keep in mind these lists are long, and this step does amount to a brute-force attack on the scanned site. So, plan appropriately before running this scan: e.g. Prepare your server/admin, shorten the list, clone the site in a staging environment, run during visitor downtime, etc.
To initiate the scan, the command will be:
wpscan --url yourwebsite.com -passwords file/path/passwords.txt
If you put your wordlist into the current directory, you’ll just need the name of the file. But if you place it anywhere else, you’ll need to provide the full path.
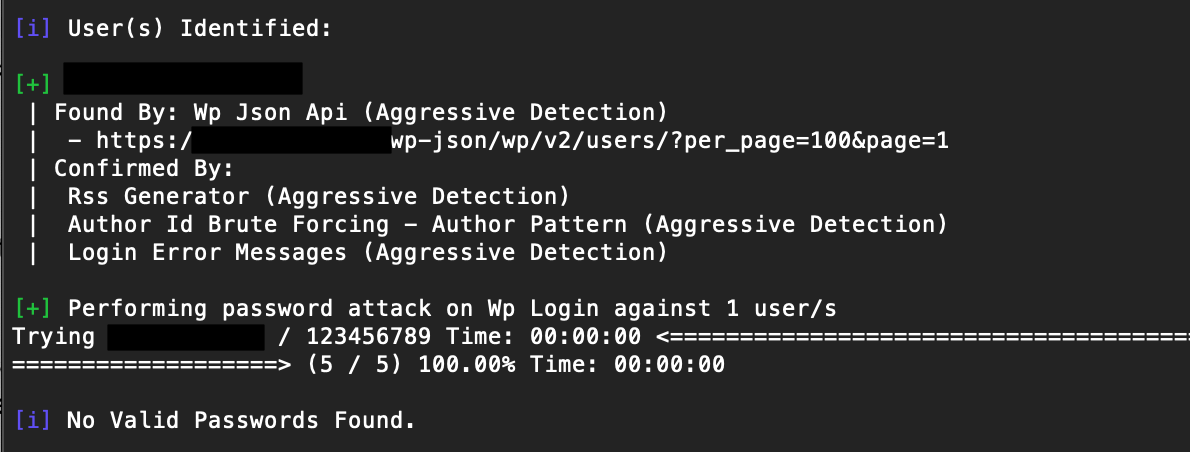
In the scan above, we ran a short list of the 5 most common passwords against a site with one enumerated user. Because that user wasn’t using any of these passwords, WPScan reports “No Valid Passwords Found.”
WPScan enumeration options
To make things a bit easier to reference, we’ve consolidated the full list of WPScan enumeration options into a handy table. Remember to start with the -e command to leverage these options.
| Option | Description |
| ap | Enumerate all plugins |
| vp | Enumerate only vulnerable plugins |
| p | Enumerate popular plugins |
| at | Enumerate all themes |
| vt | Enumerate only vulnerable themes |
| t | Enumerate popular themes |
| tt | Enumerate timthumbs |
| cb | Enumerate publicly exposed wp-config files |
| u | Enumerate user ID ranges (example: u1-9) |
| m | Enumerate media ID ranges (example: m1-9) |
Looking for more arguments? You can run the following help command to view all available scan and enumeration options from the command line interface.
wpscan --help
Proactive protection with WordPress vulnerability scanning
In the end, the preventative measures you take to ensure the security of your WordPress sites upfront reduce the likelihood – and potential impact – of problems down the line.
The more thoroughly you incorporate tools like WPScan (or even our own website firewall) into your site building process, the easier it will be to find and fix new vulnerabilities as they arise.
It’s also worth noting that WPScan is not able to detect website malware – so, if you’ve identified any vulnerabilities on your site, you may want to check for signs of a hacked website after you’ve patched up any security holes in your environment. And be sure to use a solid website monitoring solution, too.
Even if your site’s been around for a long time, there’s no better time to start than now in assessing risks and securing it. The last thing you want is to be 64-ounces deep in a can of pudding and have a zombie grab the spoon out of your hand.
如有侵权请联系:admin#unsafe.sh
