For the purpose of securing Microsoft Office installs we see many of our customers moving to a macro signing strategy. Furthermore, Microsoft is trying to battle macro malware by enforcing Mark-of-the-Web (MotW) control on macro-enabled documents. In this blog we will dive into some of the quirks of Microsoft Office macro security, various commonly used configuration options and their bypasses.
- In the first part of the blog we will discuss various Microsoft Office security controls on macros and add-ins, including their subtleties, pitfalls and offensive bypasses.
- In the second part of this blog the concept of LOLdocs is further explained, detailing how vulnerabilities in signed MS Office content might be abused to bypass even strictly configured MS Office installs.
This blog is related to our BruCON talk on LOLdocs: legitimately signed Office documents where control flows can be hijacked for malicious purposes.

Attempt 1: Enforce macro signing
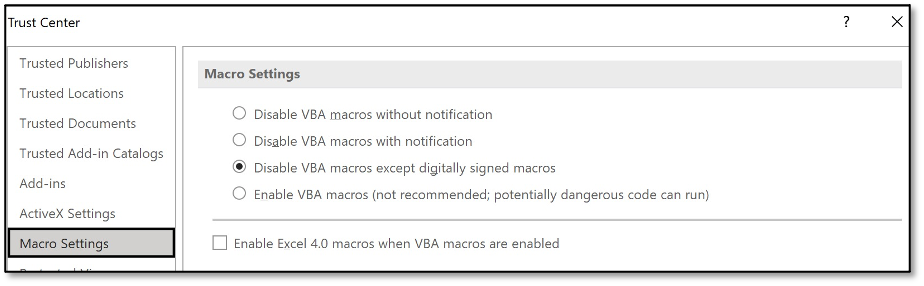
As an enterprise planning to block macros you first run an inventory of macros in use, then start designing mitigation strategies for these exceptions (e.g. sign them, configure a trusted location or design a policy for a couple of ‘special users’). After quite some work, discussions on risks etc, finally the big day is there. Time to block those pesky macros! The sysadmin changes the GUI options to disable VBA macros except digitally signed macros, as displayed below.
Bypass – Self-signed macros still render a yellow bar!
However, there is a big caveat for this configuration: any self-signed macro will just end up in the same GUI as before. So all the work done before did not really affect attackers or block those pesky macros.
Even when configuring a set of ‘trusted publishers’ any self-signed document will still render this yellow bar. Time for something more powerful.
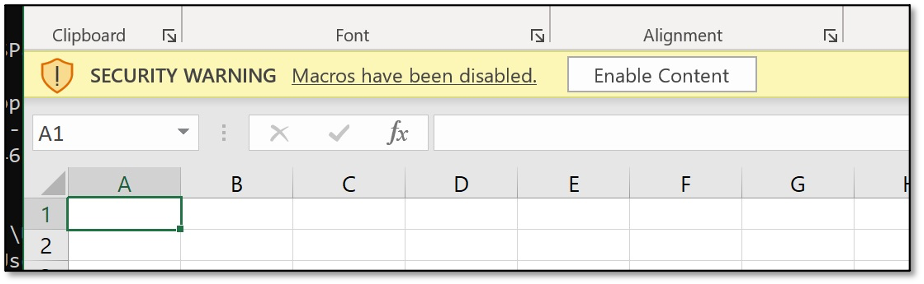
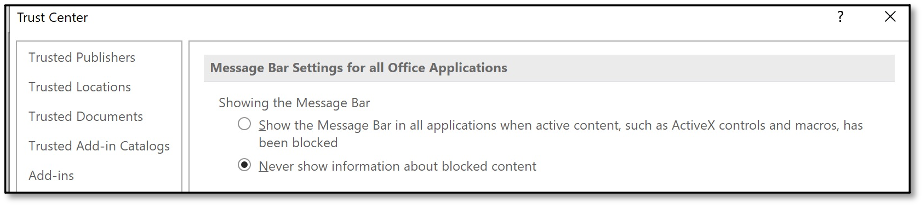
Attempt 2: Block the message bar
The issue with self-signed macros is that the message bar is shown. Luckily, we can control the message bar feature via policies and settings. So combining the macro signing enforcement and removing the message bar is our next step in blocking macro attacks.
End-users are no longer prompted for a warning when opening a signed Office file from a non-trusted publisher and we can safely sleep right?
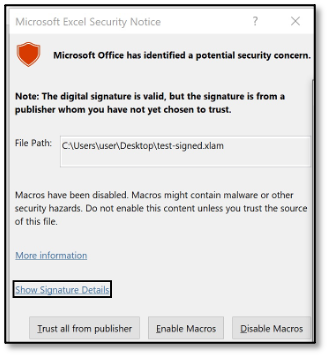
Bypass – macro-based add-ins still render a prompt!
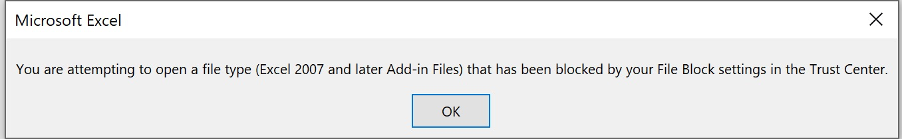
Well… there is an exception. Let’s test macro-based add-ins (XLA/XLAM file-format).
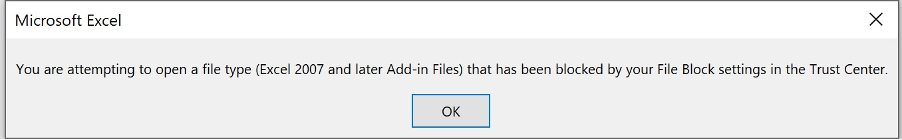
Oops, this file format still renders a prompt. The previous setting that related to the ‘message bar’ does not apply to this ‘dialogue’ (yes, for real…). Thus further configuration is needed.
Attempt 3: MS Office configuration options to block add-ins
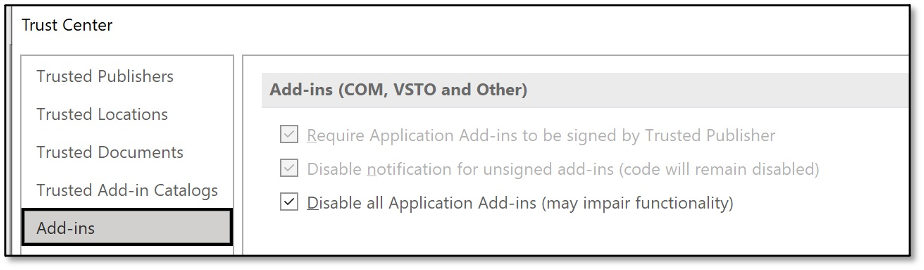
When digging deeper into the settings, an option can be found to disable add-ins (COM, VSTO and others).
But despite this setting, still the XLA/XLAM add-in warning dialogue is still shown to end-users. My guess is that this setting applies to various add-in types, but certainly not to XLAM/XLA add-ins… Leaving add-ins disabled may have its value, but appears not to relate to macros.
Attempt 4: There is a way to block XLA/XLAM
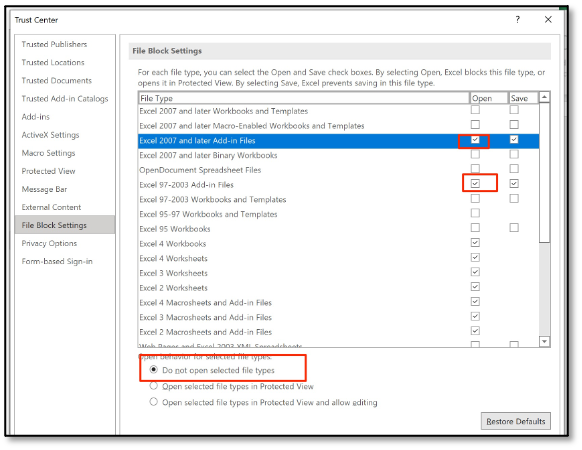
To block XLAM and XLA add-ins you can use the ‘file block settings’, combine that with the steps from attempt 1 and 2 and you are blocking quite some macro attack surface. However, this does have a drawback, even legit (signed) XLA/XLAMs no longer work.
Now all macro-related settings have been securely configured, we must be safe, right? Not completely, as we were securing settings mostly at the end of Microsoft Office’s security decision tree.
Block macro documents from the Internet decision tree
Microsoft provided a nice writeup with details on how the security flow works in modern Office versions.
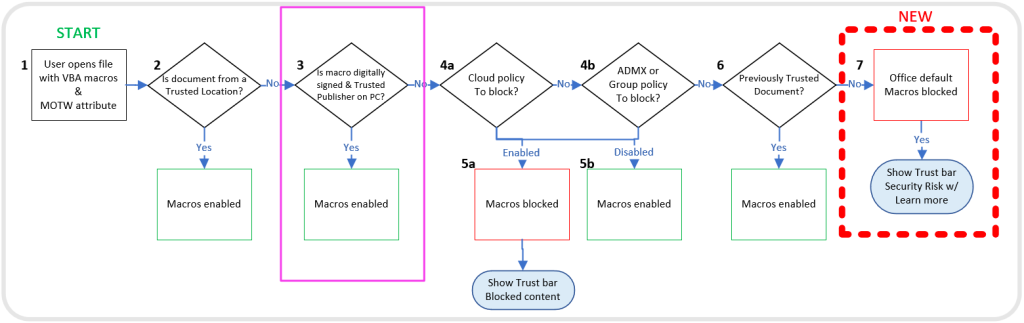
The red block is drawn by Microsoft as the blog relates to the the new feature ‘Macros from the internet will be blocked by default in Office’. The diagram tells us that trusted locations or files signed by a trusted publisher could pose a risk. Based on our experience, misconfigurations in trusted locations still occur quite often in enterprises (e.g. home drive or downloads folder of a user configured as a trusted location).
After configuring the Trusted Locations, Trusted Publishers and all above mentioned macro and filetype settings correctly, we must be safe, right?
Digitally Signed macro from Trusted Publisher
In the remainder of this blog we will dive into the purple block of the decision tree and dive into abusing signed files.
Based on the flow, any ‘signed file from a trusted publisher’ will automatically be executed, no need to worry on Mark-of-the-Web and as it is trusted and it bypasses AMSI by default. In our previous blogs we demonstrated that there are some legitimately Microsoft signed macros that can be abused to run arbitrary code. If Microsoft was marked as a trusted publisher in Office, then this could be the perfect phishing vector.
Generalizing our previous attacks
After reporting vulnerabilities towards Microsoft (write-ups here and here), we reflected on what we are actually doing. We summarized it as:
“Taking signed files ‘out of context’, manipulate the environment of the file to influence the execution flow”.
If we can find other files that are signed by a trusted publisher of our target we immediately bypass 3 layers of security controls:
- Controls blocking macros in downloaded files and MOTW, as these are ignored for trusted publishers.
- Macro security control settings (even when setting VBA macros to “blocked without notification”!), as these are ignored for trusted publishers.
- AMSI, as trusted files are exempt from inspection.
When generalizing this attack type, we are looking for: Execution flows that relate to ‘external file loads’.
Via various means we composed a dataset of signed files and code snippets and structured our research.
We identified 4 classes of coding patterns that can be abused.
Abuse pattern 1: Execution flow depending on cell contents
As explained in a previous blog post, CVE-2021-28449 is rooted in the fact that the VBA execution flow depended on cell contents. The cell content is not part of the signed data. By editing the cell content, malicious code could be loaded by legitimately signed files.
Abuse pattern 2: Declares & DLL references
Another bad coding pattern was identified by Microsoft themselves after they investigated our bug report. When studying the patch for CVE-2021-28449, we noticed changes to Solver.xlam. The original Microsoft signed Solver could be abused because of an insecure DLL reference.
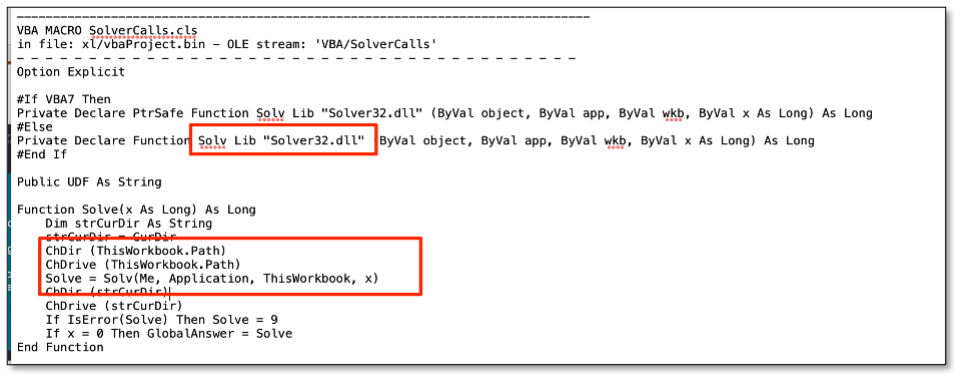
When looking at this specific code sample, the issue becomes apparent. When using a declare in VBA, a reference is made to an external module. In regular VBA, upon the first call of the referenced function, the referenced DLL is loaded with a standard LoadLibrary call.
In the Solver.xlam, the function Solv is referenced from Solver32.dll, and prior to calling the Solv function, the VBA code performs a ChDir and Chdrive to the path of the current workbook. This allows for a very simple attack: In case an attacker would send Solver.xlam and a rogue Solver32.dll together (e.g. in a zip, in an ISO container or on a WebDAV share), then the Microsoft signed XLAM would load the rogue code.
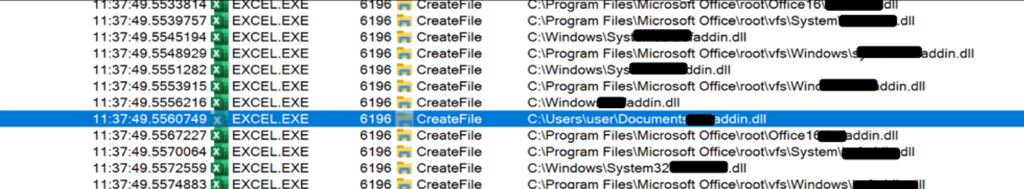
Identifying the abuse patterns in this code sample was relatively simple, so we tried to abuse other signed code that relied on external declares, and that did not have any chdir function calls in the code. We noticed that LoadLibrary would always attempt to load the external content from the Documents folder instead of the folder where the Office document was located.
Upon further analyzing this, this loading behaviour is related to Office configurations. The ‘Default File location’ is used as current directory of the Office path when loading VBA references.
Default file location configuration in MS Office
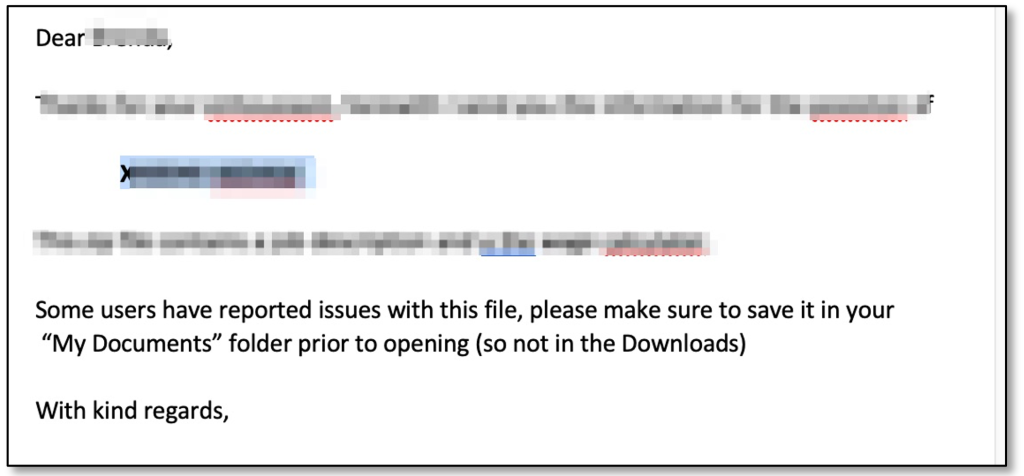
A simple attack plan from an offensive/red team viewpoint:
- Locate a signed file that is most likely a trusted publisher for your victim that relies on any external declare.
- Inform the user that the document only works from his ‘My Documents’ folder.
- Watch your malware beacons coming in!
Abuse pattern 3: Loading other documents
In case VBA code is used to open another Office document, we can abuse the fact that the macros in the document being opened are auto-executed. Some Excel macros import other Excel add-ins or even Word macros. So locating a signed Excel macro that opens a Word file (e.g. a mail-merge macro) could be your way in!
Abuse pattern 4: Beyond VBA – XLL ghosting hijack
Lastly, there is an attack class that goed beyond VBA. XLL files (which adhere to macro security settings!) can contain references to other DLL files, including DLL files that are custom and not available on a default Windows installation. As an attacker you can distribute the signed XLL file together with the ‘missing DLL’ and the signed XLL subsequently loads the DLL. We found various signed XLL files in the wild that suffer from this vulnerability.
Mitigations
The most important mitigation: be really restrictive on configuring trusted publishers. One should understand that a vulnerability in content within a signed MS Office file from a trusted publisher can be abused to circumvent most MS Office security settings, including macro security and MOTW controls.
For those involved in signing files or developing VBA and XLLs, consider the idea that your code may be abused to run other MS Office content or DLLs. It would be good to include a source-code security review in the development lifecycle prior to signing a new release.
Conclusion
This blog showed how to harden your Office environment against macro based threats and some common pitfalls for popular settings.
However, even a strongly hardened Office environment could be vulnerable for various attacks:
- Blocking a user prompt for XLA/XLAMs is hard, and can only be achieved by completely disabling the filetype. Additional monitoring on these filetypes is recommended.
- There are some fundamental weaknesses and risks when working with signed office files. Mitigation is complex, but organisations can consider:
- Code review prior to signing MS Office files.
- Evaluate previously signed files for security weaknesses.
- Compensating controls for revocation, such as processes for replacing the signing certificate in case a vulnerable file has been signed in the past.
- Only allow a minimal required set of trusted publishers.
- Be particularly careful when you develop software for Microsoft Office, especially when end-users should trust your code signing certificate.
Just “blindly signing” all internal legacy macros without proper analysis is a bad strategy. There is still a VBA/macro risk looming over your shoulder and in fact this may have made an attacker’s life easier, since signed content bypasses many MS Office security controls…
Signing can be a powerful tool to secure Office documents and to prevent maldoc phishing. However, creating secure signed macros is way more complex than we anticipated: legacy features, Operating System dependencies, and limited documentation are making it hard to identify weaknesses.
For further questions and discussions on this, reach out to us via twitter @DaWouw and @ptrpieter
如有侵权请联系:admin#unsafe.sh