2023-12-15 02:0:0 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
What is Unified Endpoint Management?
The digital landscape is evolving at an unprecedented pace, and with it, the significance of Unified Endpoint Management (UEM) has never been more paramount. What is Unified Endpoint Management? UEM offers a holistic approach to managing and securing all endpoints within an organization, ensuring seamless operations and robust security. As businesses grapple with the complexities of a diverse device ecosystem, the evolution of endpoint management has been evident.
What began as Mobile Device Management (MDM) has now transitioned through Mobile Application Management (MAM) and Enterprise Mobility Management (EMM) to culminate in UEM. This progression underscores the industry’s response to the ever-growing challenges of modern IT environments and the critical role of UEM in addressing them.
Unified Endpoint Management (UEM) is revolutionizing how businesses manage and secure their diverse range of devices. It seamlessly integrates different endpoints like smartphones, laptops, and tablets under one management umbrella, enhancing security and operational efficiency. Unlike traditional methods, UEM provides a more holistic approach, combining aspects of Mobile Device Management (MDM) and Enterprise Mobility Management (EMM) with advanced security measures. This post delves into UEM’s role in network security, comparing it with legacy systems and outlining best practices for implementation. Whether you’re transitioning from older systems or starting anew, UEM offers a streamlined, secure solution for managing today’s complex IT environments. Share your experiences and questions in the comments to contribute to our collective understanding of UEM’s potential.
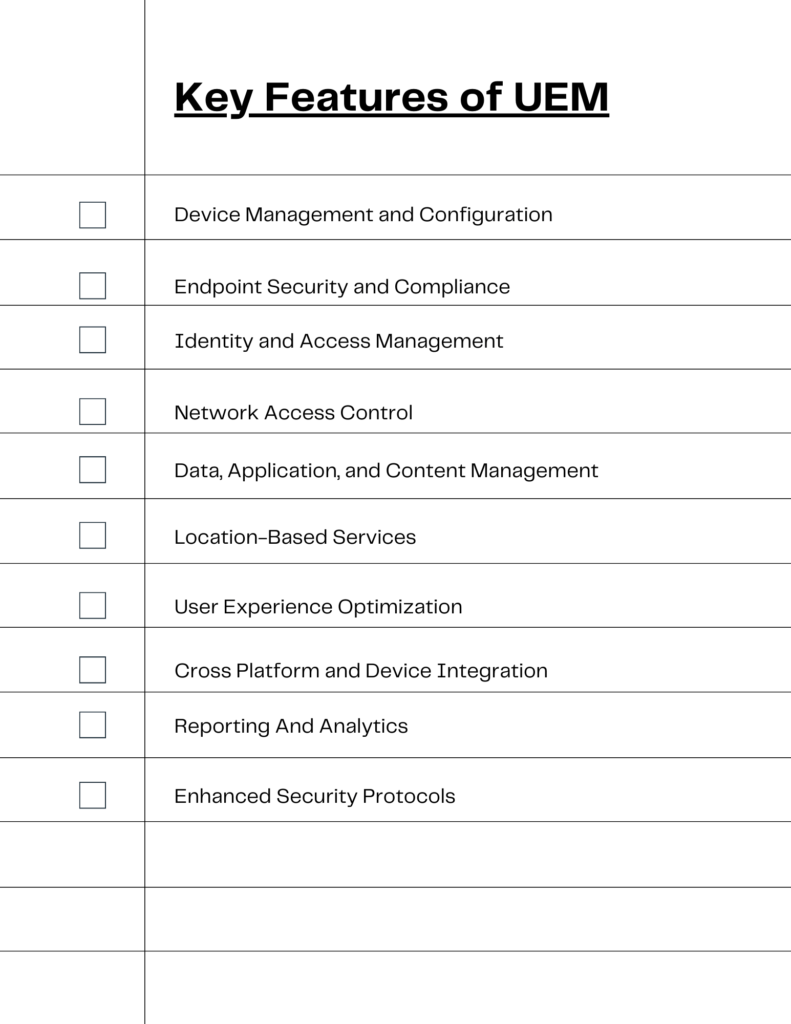
Diving Deep: Key Features of Unified Endpoint Management

Device Management and Configuration
Unified Endpoint Management (UEM) provides a comprehensive platform for the streamlined management and configuration of all devices within an organization. This foundation is pivotal for maintaining a secure digital environment.
Centralized Device Management
With the proliferation of devices in today’s corporate landscape, having a centralized console to manage all endpoints ensures uniformity in policies and configurations. This centralization is essential for maintaining consistent security standards across diverse devices, from laptops to smartphones.
Over-the-Air (OTA) Updates
In an ever-evolving digital world, devices must run the latest software and firmware versions. OTA updates allow for real-time patching of vulnerabilities, ensuring devices are safeguarded against potential exploits by cybercriminals.
Remote Configuration and Troubleshooting
The ability for IT teams to remotely configure device settings and troubleshoot issues is invaluable. This feature ensures that devices remain secure and operational without the need for physical intervention, reducing downtime and potential security risks.
Device Inventory and Asset Management
A clear and organized view of all devices helps IT teams track device status, software versions, and security configurations. This oversight ensures that all devices adhere to the organization’s security protocols and are updated promptly.
Endpoint Security and Compliance
Security remains at the core of UEM, ensuring that devices not only comply with corporate policies but are also fortified against external threats.
Enhanced Security Measures
Advanced security protocols, including encryption, remote lock/wipe, and biometric authentication, are integral to a UEM solution. These measures ensure that devices and the data they contain are shielded from unauthorized access and potential breaches.
Compliance Monitoring
Continuous monitoring of devices for adherence to corporate policies is crucial. This feature ensures that devices maintain consistent security standards, and any deviations are addressed promptly, reducing potential vulnerabilities.
Identity and Access Management
In a world where data breaches are increasingly common, ensuring that only authorized users can access corporate data is paramount. Integrating with identity providers and implementing multi-factor authentication adds an extra layer of security, minimizing potential breaches.
Network Access Control
Controlling which devices can access the corporate network based on their compliance status ensures that only secure devices connect. This reduces potential entry points for threats and ensures a fortified network perimeter.
Containerization
By creating secure containers on devices where corporate data is stored, UEM ensures that corporate data remains isolated from personal data. This separation adds an extra layer of protection, especially in BYOD scenarios.
Data, Application, and Content Management
Effective management of data, applications, and content is pivotal in ensuring only authorized access, maintaining data integrity, and facilitating seamless operations.
Content and Data Management
Delivering and managing corporate content securely on devices is essential. Features like secure containers and data encryption ensure that data remains uncompromised, even if a device is lost or stolen.
Mobile Content Management
As mobile devices become primary work tools, facilitating the secure access and storage of content on these devices is crucial. This feature ensures data security on-the-go, catering to the needs of a mobile workforce.
Application Management
Controlling the deployment, updating, and access of applications on endpoints ensures that only approved and secure apps are in use. This reduces the risk of malware infections and data breaches stemming from rogue applications.
Kiosk Mode
By locking devices to specific apps, UEM solutions can transform them into dedicated-purpose devices. This ensures users can’t access or install potentially harmful apps, especially in public-facing scenarios like information kiosks.
Location-Based Services
UEM ensures that while devices are secure, users can work efficiently without hindrances.
Geofencing
By restricting device functionalities based on geographical locations, UEM solutions can ensure that certain data or apps are inaccessible outside predefined areas. This adds a layer of data protection, especially for sensitive information that shouldn’t be accessed globally.
Policy Enforcement based on location
Devices can be programmed to adhere to specific policies when in certain locations. This context-aware security measure ensures that devices operate within the desired security parameters based on their geographical position.
User Experience Optimization
A good UEM solution doesn’t just secure devices; it also enhances the overall user experience. By ensuring that security measures are intuitive and non-intrusive, UEM solutions make it easier for users to adhere to security protocols without compromising their workflow.
Cross Platform and Device Integration
With a diverse range of device operating systems in use, from Windows to iOS, UEM solutions ensure consistent security and management protocols across platforms. This provides a uniform user experience, reducing potential friction points.
Cross-Platform Support
Ensures consistent security and management protocols across various device operating systems, providing a uniform user experience.
Integration with IoT Devices
The increasing number of Internet of Things (IoT) devices in corporate networks necessitates their secure integration. UEM extends its capabilities to these devices, ensuring they’re securely connected and managed, fortifying the entire digital ecosystem.
BYOD (Bring Your Own Device) Support
The rise of BYOD trends means personal devices are often used for work purposes. UEM securely integrates these devices into the corporate network, ensuring a clear separation between personal and corporate data, and providing the necessary security layers.
Reporting and Analytics
Insights into device usage, security incidents, and compliance are invaluable for IT teams. UEM solutions offer detailed reports and analytics, helping teams make informed decisions, spot potential vulnerabilities, and address them proactively.
Enhanced Security Protocols
As the device landscape becomes more diverse, from smartphones to IoT devices, UEM ensures all devices, regardless of type, adhere to advanced security protocols. This comprehensive approach ensures a fortified digital environment, reducing potential weak points.
Benefits of Embracing UEM for Small Businesses
In today’s fast-paced digital landscape, small businesses face unique challenges, especially when it comes to managing and securing their IT infrastructure. Unified Endpoint Management (UEM) emerges as a game-changer, offering a plethora of benefits tailored to the needs of small businesses. Let’s delve into the core advantages of adopting UEM and understand its transformative impact.
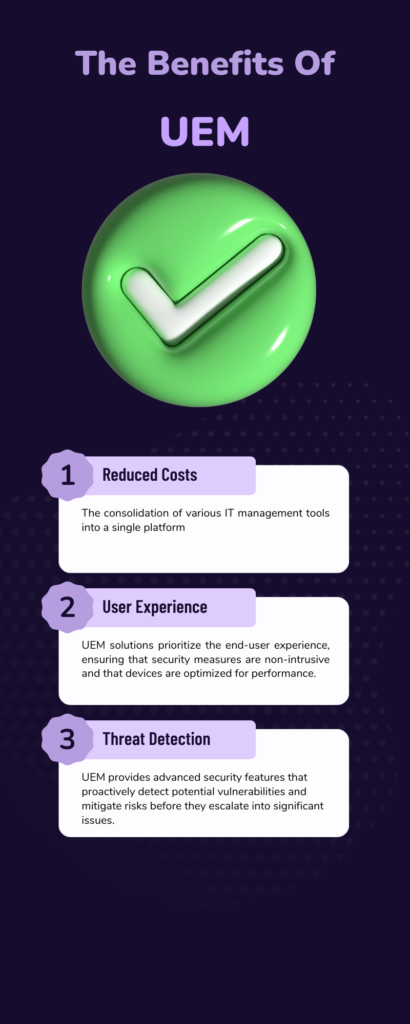
Streamlined IT Operations and Reduced Costs
One of the primary benefits of UEM is the consolidation of various IT management tools into a single platform. This centralization not only simplifies the management process but also leads to significant cost savings.
For example, consider a small business that previously relied on separate tools for mobile device management (MDM), mobile application management (MAM), and PC lifecycle management. By transitioning to a UEM solution, they can manage all these endpoints from a single console. This reduces the need for multiple software licenses, specialized training for different tools, and dedicated personnel for each system. Over time, these savings can be substantial, allowing the business to allocate resources to other critical areas.
Improved End-User Experience and Productivity
UEM solutions prioritize the end-user experience, ensuring that security measures are non-intrusive and that devices are optimized for performance. This leads to increased productivity as employees can work seamlessly without technical hindrances.
For example, a sales executive in a small business often switches between her tablet, smartphone, and laptop throughout the day. With UEM, her applications, data, and settings are synchronized across devices. She doesn’t waste time searching for files or reconfiguring settings, leading to a smoother workflow and more time spent on core sales activities.
Proactive Threat Detection and Mitigation
In an era where cyber threats are evolving rapidly, UEM provides advanced security features that proactively detect potential vulnerabilities and mitigate risks before they escalate into significant issues.
For example, a small e-commerce business noticed an unusual spike in data traffic from one of its devices. The UEM solution, with its integrated threat detection, identified this anomaly and isolated the device, preventing potential data theft. It was later discovered that the device had been targeted in a phishing attack. Thanks to UEM’s proactive measures, the business averted a potential data breach, saving them from financial losses and reputational damage.
Incorporating UEM into the IT strategy of small businesses offers a competitive edge, ensuring they remain agile, secure, and efficient in a dynamic digital environment. As illustrated by the use cases, the benefits of UEM are tangible and can lead to significant improvements in operational efficiency, user satisfaction, and overall security.
UEM vs. Traditional Endpoint Management Tools
The evolution of endpoint management has been marked by a series of innovations, each addressing the growing complexities of a digital-first world. From Mobile Device Management (MDM) to Mobile Application Management (MAM) and Enterprise Mobility Management (EMM), each tool has played a pivotal role in shaping the way businesses manage their devices. However, as the digital landscape continues to expand, Unified Endpoint Management (UEM) emerges as the holistic solution, encompassing the best of its predecessors and adding more. Let’s delve into a comparative analysis.
MDM (Mobile Device Management)
Mobile Device Management primarily focuses on the management of mobile devices, ensuring they adhere to company policies and are secure.
MDM allows for device tracking, remote wiping, and enforcing security policies like passcodes. However, its scope is limited to device-level management, often neglecting the applications or content on the device.
UEM not only incorporates these device management features but extends its capabilities to manage applications, content, and even IoT devices, offering a more comprehensive solution.
MAM (Mobile Application Management)
Mobile Application Management is centered around the management and security of applications on mobile devices, without delving deep into the device’s own settings or data.
MAM allows businesses to control which applications are installed, updated, or removed. It can also isolate business apps from personal ones, ensuring data security.
While MAM focuses solely on applications, UEM provides a unified platform that manages both the device and its applications, ensuring seamless integration and enhanced security.
EMM (Enterprise Mobility Management)
Enterprise Mobility Management is a broader solution that combines elements of MDM and MAM, offering management capabilities for devices, applications, and content.
EMM provides tools for application distribution, data security, and device management. It’s a more integrated approach compared to MDM and MAM but still lacks in managing non-mobile endpoints and advanced security features.
On the other hand, UEM takes the integrated approach of EMM a step further. It manages a wider range of devices, from PCs to IoT devices, and offers advanced security protocols, making it a truly all-encompassing solution.
Why UEM is the Future of Endpoint Management
- Holistic Management: UEM provides a single platform to manage all endpoints, be it mobile devices, desktops, or IoT devices. This centralization reduces complexities and streamlines IT operations.
- Advanced Security Protocols: With the rise of cyber threats, UEM offers enhanced security measures, from biometric authentication to geofencing, ensuring devices and data are always protected.
- User-Centric Approach: UEM solutions prioritize the end-user experience, ensuring devices are optimized for performance and security measures are non-intrusive.
- Future-Proofing: As businesses continue to adopt a diverse range of devices and technologies, UEM’s ability to integrate and manage these endpoints ensures it remains relevant and essential in the future.
In conclusion, while MDM, MAM, and EMM have played significant roles in the evolution of endpoint management, UEM stands out as the comprehensive solution for today’s diverse and dynamic digital environment. Its holistic approach, advanced security features, and user-centric design make it the undeniable future of endpoint management.
UEM Deployment Options
UEM deployment options offer organizations the flexibility to choose between on-premises or cloud-based platforms. These options are designed to cater to the specific needs and requirements of each organization. With unified endpoint management (UEM), organizations can centrally manage and secure all their endpoint devices from a single platform. This eliminates the need for separate management tools, such as mobile device management (MDM), and streamlines the management process.
Cloud-Based UEM Options
Cloud-based UEM platforms provide organizations with the convenience of accessing their management tools and security features from anywhere, at any time. This allows for easy scalability and reduces the burden on IT infrastructure. On the other hand, on-premises UEM platforms provide organizations with complete control over their data and security. This option is preferred by organizations that have strict regulatory requirements. Or those organizations who prefer to keep their data within their own premises.
Whether organizations choose an on-premises or cloud-based UEM platform, they can benefit from centralized management and mobile security solutions. These solutions enable organizations to efficiently manage their endpoint devices and mitigate the risks associated with device usage. With UEM, organizations can ensure the proper configuration and security of devices, implement access controls, and protect their networks from potential threats. By leveraging the power of unified endpoint management, organizations can enhance their overall network security and streamline their endpoint management processes.
UEM Deployment Flexibility
UEM provides flexibility in deployment options. Organizations can choose between on-premises or cloud-based UEM platforms, depending on their specific needs and requirements. Both options offer centralized management and mobile security solutions. Thus, allowing organizations to choose the deployment method that best suits their IT infrastructure.
UEM provides organizations with the flexibility to choose between on-premises or cloud-based platforms for unified endpoint management (UEM). This allows them to tailor their deployment method based on their specific needs and requirements. With both options, organizations can benefit from centralized management and robust mobile security solutions. This ensures the optimal management and protection of their endpoint devices.
The choice between on-premises or cloud-based UEM platforms depends on factors such as IT infrastructure, resource availability, and security preferences. On-premises UEM offers organizations greater control over their data and systems. This also provides the ability to integrate UEM with existing identity and access management (IAM) solutions. Cloud-based UEM, on the other hand, provides the advantages of scalability, flexibility, and reduced maintenance efforts, as the UEM tool is hosted and managed by the UEM provider. Regardless of the chosen deployment method, organizations can effectively manage and secure their mobile devices and other endpoint devices with the comprehensive management features offered by UEM software.
Solutions in the UEM Market
UEM solutions have gained significant traction in the market due to their comprehensive features and the importance of endpoint management and security in today’s digital landscape. Organizations are increasingly recognizing the need for a unified approach to managing and securing their endpoint devices, including mobile devices. This has led to the rise in UEM tools and solutions.
With UEM, organizations can efficiently manage and secure their endpoints, regardless of the operating system or type of device. UEM solutions offer a centralized management platform that allows IT teams to remotely manage and configure devices, deploy necessary software and updates, and enforce security policies. This not only enhances productivity but also ensures network security by minimizing vulnerabilities and protecting against potential threats. In addition, UEM provides robust endpoint security features such as secure device configurations and network access control, further strengthening network security measures.
There are several UEM vendors in the market, offering UEM products and solutions. Some popular UEM vendors include Ivanti UEM, Citrix Endpoint Management, and BlackBerry UEM. These solutions provide comprehensive endpoint management and security, enabling organizations to effectively manage and secure their endpoint devices.
UEM and Enterprise Mobility Management (EMM)
Unified Endpoint Management, or UEM, is the next evolution of Enterprise Mobility Management (EMM) and traditional mobile device management (MDM). UEM enables organizations to manage and secure all endpoint devices, including mobile devices, laptops, desktops, and IoT devices, from a single management console. With UEM software, organizations can streamline their patch management, app management, and identity management processes, leading to enhanced productivity and reduced security risks.
The Evolution of EMM to UEM
One of the key advantages of UEM over traditional endpoint management systems is its unified approach to management and mobile security. Unlike EMM, which focuses solely on mobile devices, UEM extends its capabilities to include all endpoint devices. This means that organizations can leverage the same set of unified endpoint management features, such as lifecycle management and endpoint detection and response, across all devices, regardless of the operating system. This holistic approach not only simplifies the management process but also ensures consistent security measures are applied throughout the organization, regardless of the device being used.
Comparing UEM with Traditional EMM Approaches
However, it’s important to note that UEM and EMM are not mutually exclusive. In fact, they are closely related, with UEM building upon the foundations of EMM. While EMM is specifically designed for mobile device management, UEM encompasses traditional endpoint management tools as well. As organizations continue to adopt new technologies and operating systems, such as Windows 10 and IoT devices, UEM provides a comprehensive solution that addresses the challenges of managing and securing a diverse array of devices. This makes UEM a critical investment in today’s fast-paced and interconnected business landscape.
UEM is closely related to Enterprise Mobility Management (EMM). While EMM focuses on managing and securing mobile devices, UEM extends its capabilities to include all endpoint devices. UEM merges mobile device management and mobile application management with traditional endpoint management tools, providing a holistic approach to endpoint management and security.
Key Features Differentiating UEM from EMM
UEM, or Unified Endpoint Management, is closely related to Enterprise Mobility Management (EMM). While EMM focuses primarily on managing and securing mobile devices, UEM extends its capabilities to include all endpoint devices, including desktop operating systems. By merging mobile device management and mobile application management with traditional endpoint management tools, UEM provides a comprehensive enterprise mobility management solution that caters to the diverse needs of modern organizations.
With UEM, organizations can benefit from a single platform that offers centralized management and security solutions for all their endpoint devices. This integrated approach eliminates the need for separate management systems for different device types, streamlining the overall management process. UEM solutions allow organizations to efficiently handle tasks such as device provisioning, configuration, application deployment, and security enforcement from a single, centralized platform. This not only enhances operational efficiency but also ensures consistent security measures across all endpoint devices. UEM solutions enable organizations to implement network security measures, such as secure device configurations and network access control, to protect their networks from external threats. The evolution of endpoint management to include mobile device management and mobile application management has empowered organizations with a holistic approach to endpoint management and security.
UEM and Network Security
UEM and network security go hand in hand, with UEM providing the necessary capabilities to manage and secure different endpoint devices. Multiple endpoint management tools, such as Ivanti UEM and Citrix Endpoint Management, enable organizations to effectively handle the management and security of various endpoint devices, including mobile devices, PCs, and more. These UEM solutions offer comprehensive visibility across all endpoint devices, allowing IT teams to remotely manage and secure them in a centralized manner.
Challenges in Traditional Network Security
In addition to managing and securing endpoints, UEM tools provide organizations with the ability to implement network security measures. By unifying endpoint management and security, UEM ensures that network access control and secure device configurations are in place to protect against potential threats. This holistic approach to endpoint management and security alleviates the burden of connecting different systems and simplifies the overall network security infrastructure. With the use of UEM tools, organizations can create a seamless and secure environment where unified endpoint management works alongside network security to safeguard valuable data and assets.
UEM plays a crucial role in network security. By ensuring the security of endpoint devices, UEM helps prevent unauthorized access and potential breaches. UEM solutions enable organizations to implement network security measures, such as secure device configurations and network access control, to protect their networks from external threats.
UEM plays a crucial role in network security by ensuring the security of endpoint devices. By effectively managing and securing these devices, UEM helps prevent unauthorized access and potential breaches. The importance of endpoint security cannot be overstated, as compromised endpoints can serve as entry points for attackers to infiltrate an organization’s network. UEM solutions combine tools to manage and secure various endpoint devices, including laptops, smartphones, and tablets, providing a comprehensive approach to threat management.
UEM’s Role in Strengthening Cybersecurity
One of the key features of UEM is its ability to implement network security measures. UEM solutions allow organizations to configure endpoints with secure settings and apply network access control policies, ensuring that only authorized devices can connect to the network. By enhancing network security, UEM helps protect valuable endpoint data and sensitive information from falling into the wrong hands. The centralized management offered by UEM solutions enables IT teams to efficiently monitor and enforce security policies, ensuring that all endpoints adhere to the organization’s security standards. In addition, UEM merges mobile device management and mobile application management with traditional endpoint management tools, providing a complete endpoint management solution that caters to modern enterprise management needs.
Getting Started with UEM: Best Practices and Recommendations
Implementing Unified Endpoint Management (UEM) is a strategic move that can significantly enhance the operational efficiency and security of an organization. To successfully integrate UEM, it’s essential to follow a structured approach. This includes assessing your current IT landscape, setting clear objectives, choosing the right solution, planning phased deployment, training your team, monitoring system performance, and measuring return on investment. The following steps provide a comprehensive guide on how to effectively implement UEM in your organization, ensuring a smooth transition and maximizing the benefits.
A stepwise approach
- Assess Your Current Infrastructure: Start by thoroughly evaluating your existing IT setup. Identify all devices, systems, and software that will integrate with the UEM solution. This step is crucial for understanding the scope of UEM deployment and ensuring compatibility across your organization’s technology landscape.
- Define UEM Objectives: Clearly outline what you aim to achieve with UEM. This could include enhancing security, improving the user experience, or streamlining IT operations. Setting specific, measurable goals helps guide the selection and implementation process, ensuring the UEM solution aligns with your business objectives.
- Choose the Right UEM Solution: Research various UEM platforms, focusing on features that meet your specific needs. Consider factors like scalability, ease of use, and compatibility with your existing infrastructure. Select a solution that not only fits your current requirements but also has the flexibility to adapt to future changes.
- Plan Deployment Phases: Implement UEM in manageable phases. Start with the most critical assets or user groups to minimize disruptions. Gradual deployment allows for addressing unforeseen challenges and making necessary adjustments before full-scale implementation.
- Train Your Team: Provide comprehensive training for your IT staff and end-users. Effective training ensures that everyone understands how to use the UEM platform efficiently and can help in identifying and resolving issues quickly.
- Monitor and Adjust: After deployment, continuously monitor the performance of the UEM system. Use feedback and data analytics to refine and optimize the setup. Regular monitoring helps in identifying areas for improvement and adapting the system to evolving business and IT needs.
- Measure ROI: Periodically assess the impact of UEM on your organization. Look at key metrics like productivity, security incident rates, and IT operational costs. Evaluating ROI helps in understanding the value delivered by the UEM system and guides future investment decisions.
Maximizing Business Potential with UEM: A Closing Perspective
Unified Endpoint Management (UEM) is more than a technological upgrade; it’s a transformative strategy for modern businesses. By carefully implementing UEM, organizations can significantly enhance efficiency and security. Remember, the journey to effective UEM integration is continuous and evolving. We encourage you to share your insights, experiences, and questions in the comments. Your contributions can help build a knowledgeable community, making UEM adoption smoother and more effective for everyone involved. Let’s collaborate and grow in our UEM journey.
What is UEM and why is it important for network security?
UEM stands for Unified Endpoint Management. It is important for network security as it ensures the security of endpoint devices, preventing unauthorized access and potential breaches.
What deployment options are available for UEM?
UEM provides flexibility in deployment options. Organizations can choose between on-premises or cloud-based UEM platforms, depending on their specific needs and requirements.
What are some popular UEM vendors in the market?
Some popular UEM vendors include Ivanti UEM, Citrix Endpoint Management, and BlackBerry UEM. These solutions provide comprehensive endpoint management and security.
How is UEM related to Enterprise Mobility Management (EMM)?
UEM is closely related to EMM. While EMM focuses on managing and securing mobile devices, UEM extends its capabilities to include all endpoint devices. It provides a holistic approach to endpoint management and security.
How does UEM contribute to network security?
UEM plays a crucial role in network security. It helps prevent unauthorized access and potential breaches by ensuring the security of endpoint devices. UEM solutions enable organizations to implement network security measures, such as secure device configurations and network access control.
The post Unified Endpoint Management (UEM): What is it and What’s New? appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/unified-endpoint-management/?utm_source=rss&utm_medium=rss&utm_campaign=unified-endpoint-management
如有侵权请联系:admin#unsafe.sh