2023-12-15 04:33:0 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Author:
Kaustubh Jagtap, Product Marketing Director, SafeBreach
On December 13th, The U.S. Federal Bureau of Investigation (FBI), U.S. Cybersecurity & Infrastructure Security Agency (CISA), U.S. National Security Agency (NSA), Polish Military Counterintelligence Service (SKW), CERT Polska (CERT.PL), and the UK’s National Cyber Security Centre (NCSC) have issued an urgent advisory about the ongoing exploit of CVE-2023-42793 by Russian Foreign Intelligence Service (SVR) threat actors. Detailed information about this exploit and the associated indicators of compromise (IOCs) and the various tactics, techniques, and procedures (TTPs) is listed in US-CERT Alert AA23-347A – Russian Foreign Intelligence Service (SVR) Exploiting JetBrains TeamCity CVE Globally.
The advanced persistent threat (APT) actors involved in this exploit are a high-profile threat group commonly known as APT29, the Dukes, CozyBear, and NOBELIUM/Midnight Blizzard. These threat actors have targeted servers hosting the JetBrains TeamCity software since September 2023. TeamCity is commonly used by software developers to automate the compilation, building, testing, and release of software. By exploiting the vulnerability, threat actors can gain access to source code, and signing certificates, thereby gaining the ability to undermine the software compilation and development process. This level of compromise could potentially allow these threat actors to leverage this compromised software in future supply chain attacks. Based on initial observations, post-compromise, the SVR threat actors have used this access to escalate their privileges, move laterally, deploy additional backdoors, and take additional steps to ensure persistent and long-term access to victim networks.
Technical Details
The vulnerability CVE-2023-42793 was first discovered by the SonarSource team in September 2023. This vulnerability permits an unauthenticated attacker with access to a TeamCity server the ability to launch a remote code execution (RCE) attack, ultimately gaining complete administrative control over the server. Based on the information available from the advisory and other sources, here are some of the technical details of the attack:
- Gaining Initial Access – The SVR-affiliated APT group first began targeting the internet-connected TeamCity servers in September 2023 by exploiting CVE-2023-42793, allowing them to bypass authorization, gain higher-level access, and execute arbitrary code on the servers.
- Performing Discovery – The threat actors leveraged several basic Windows commands to gain an understanding of the target network and all the underlying components including various groups, domains, etc.
- Disabling Protection – Given the reputation of the attackers, it wasn’t any surprise that they used a technique known as “Bring Your Own Vulnerable Driver” to disable deployed EDR and AV tools. This was done using an open-source project called “EDRSandBlast” which removes protected process light (PPL) protection and injects code into the AV/EDR processes. Additional tools like Mimikatz were also observed being used.
- Maintaining Secrecy – The threat actors attempted to hide their backdoors in one of the following ways:
- Abusing a DLL hijacking vulnerability in Zabbix software and placing a GraphicalProton backdoor
- Backdooring an open-source application developed by Microsoft named vcperf and placing a GraphicalProton backdoor
- Abusing a DLL hijacking vulnerability in Webroot antivirus software and placing a GraphicalProton backdoor
Additionally, a covert C2 channel was also created to transfer stolen, obfuscated files and place them into cloud-sharing services like OneDrive and Dropbox.
- Escalating Privileges – Threat actors used multiple techniques including WinPEAS, NoLMHash registry key modification, and the Mimikatz tool to escalate their privileges and perform further malicious actions.
- Maintaining Persistence in Victim Networks – WindowsScheduled tasks were leveraged to ensure a consistent execution of deployed backdoors and maintain access. To secure long-term access, Rubeus toolkit was used to create Ticket Granting Tickets (TGTs).
- Exfiltration of Sensitive Data – To exfiltrate Windows Registry, threat actors saved Windows Registry hives into files, packed and obfuscated them, and exfiltrated them using backdoors. The SharpChromium tool was also leveraged to obtain sensitive browser data such as session cookies, browsing history, or saved logins.
- Performing Further Reconnaissance – Once a persistent presence was established on victim networks, further reconnaissance was performed using tools like port scanner and PowerSploit.
- Lateral Movement – The WMI command-line (WMIC) utility and golden ticket attacks were used to move laterally within the infected networks.
Important Note for SafeBreach Customers – Coverage for AA23-347A (APT29 – JetBrains TeamCity)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers were already protected against a lot of the behavioral and IOC-based attacks commonly used by APT29 and identified in the advisory. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
NEW Behavioral Attacks Related to CERT Alert
- #9413 – Enable LMHash policy
NEW IOC-Based Attacks Related to CERT Alert
- CVE-2023-42793
- #9412 – Remote exploitation of JetBrains TeamCity vulnerability CVE-2023-42793 (WAF)
- EDRSandblast
- #9414 – Write EDRSandblast (14e7a0) hacktool to disk
- #9415 – Pre-execution phase of EDRSandblast (14e7a0) hacktool (Windows)
- #9416 – Transfer of EDRSandblast (14e7a0) hacktool over HTTP/S
- #9417 – Transfer of EDRSandblast (14e7a0) hacktool over HTTP/S
- #9418 – Email EDRSandblast (14e7a0) hacktool as a compressed attachment
- #9419 – Email EDRSandblast (14e7a0) hacktool as a compressed attachment
- GraphicalProton
- #9395 – Write GraphicalProton (e44dcf) backdoor to disk
- #9396 – Pre-execution phase of GraphicalProton (e44dcf) backdoor (Windows)
- #9397 – Transfer of GraphicalProton (e44dcf) backdoor over HTTP/S
- #9398 – Transfer of GraphicalProton (e44dcf) backdoor over HTTP/S
- #9399 – Email GraphicalProton (e44dcf) backdoor as a compressed attachment
- #9400 – Email GraphicalProton (e44dcf) backdoor as a compressed attachment
- Backdoored vcperf
- #9401 – Write Backdoored vcperf (600443) backdoor to disk
- #9402 – Pre-execution phase of Backdoored vcperf (600443) backdoor (Windows)
- #9403 – Transfer of Backdoored vcperf (600443) backdoor over HTTP/S
- #9404 – Transfer of Backdoored vcperf (600443) backdoor over HTTP/S
- #9405 – Email Backdoored vcperf (600443) backdoor as a compressed attachment
- #9406 – Email Backdoored vcperf (600443) backdoor as a compressed attachment
- GraphicalProton HTTPS
- #9407 – Write GraphicalProton HTTPS (bb0b93) backdoor to disk
- #9408 – Transfer of GraphicalProton HTTPS (bb0b93) backdoor over HTTP/S
- #9409 – Transfer of GraphicalProton HTTPS (bb0b93) backdoor over HTTP/S
- #9410 – Email GraphicalProton HTTPS (bb0b93) backdoor as a compressed attachment
- #9411 – Email GraphicalProton HTTPS (bb0b93) backdoor as a compressed attachment
Existing Behavioral Attacks Mapped to the CERT Alert
- #102 – Covert data exfiltration via Dropbox
- #794 – Extract Login Information using MimiKatz
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #1269 – Creating Windows schedule task (schtasks.exe)
- #1693 – Collect Windows system data using CMD
- #2124 – Hide a file – Windows
- #2164 – Scheduled Task
- #2188 – Extract Process List using Windows Commands
- #2189 – Account Manipulation
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #2389 – Modify Firewall Rules using netsh.exe
- #3829 – Run obfuscated Mimikatz on host
- #4136 – Execute EXE file using process hollowing (PowerShell)
- #5107 – Stop a service using net stop command
- #5672 – Agentless lateral movement via WMI
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #6809 – Execute DLL by signed executable (igfxtray.exe)
- #6824 – Create hidden user (Windows)
- #7144 – Unregister anti-malware scanning interface providers
- #7169 – Dump the SAM database from the registry (Windows)
- #7172 – Spawn a hidden PowerShell process
- #7173 – Spawn a hidden process (Windows)
- #7220 – Process Injection – Thread Execution Hijacking
- #7834 – Add Exclusions to Windows Defender
- #7945 – Add Mimikatz as exclusion to Windows Defender and execute Mimikatz
- #8018 – Web application port scanning
- #8019 – Port scanning target simulator
- #8020 – Port scanning of the local subnet network
- #8055 – Load and execute vulnerable driver
- #8359 – Process Injection – Asynchronous Procedure Calls
- #8377 – Golden Ticket
Existing IOC-based Attacks Mapped to the CERT Alert
- All existing Mimikatz attacks from the SafeBreach playbook
- #6817 – Pre-execution phase of winPEAS malware
- #6818 – Write winPEAS malware to disk
- #6819 – Transfer of winPEAS malware over HTTP/S
- #6820 – Transfer of winPEAS malware over HTTP/S
- #6821 – Email winPEAS malware as a compressed attachment
- #6822 – Email winPEAS malware as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
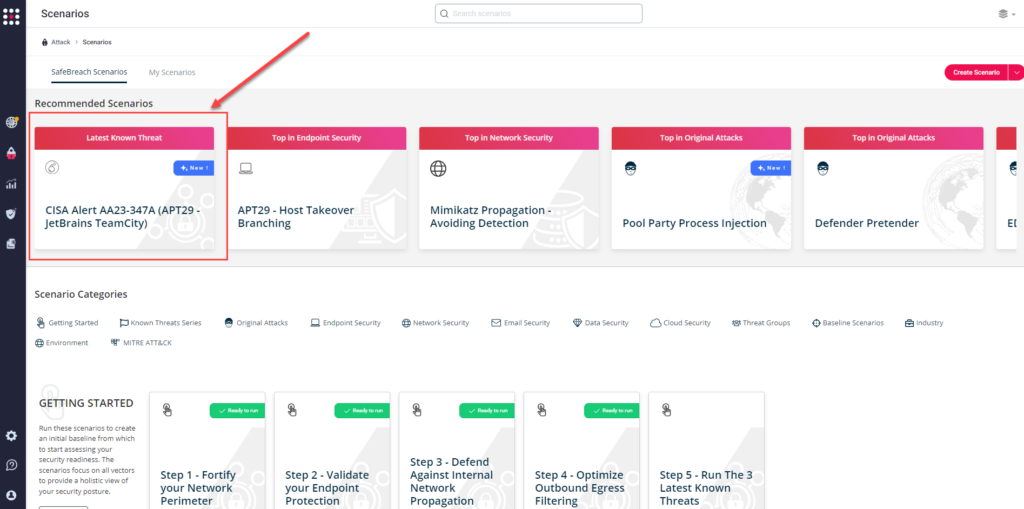
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA23-347A (APT29 – JetBrains TeamCity) scenario from the list of available scenarios.
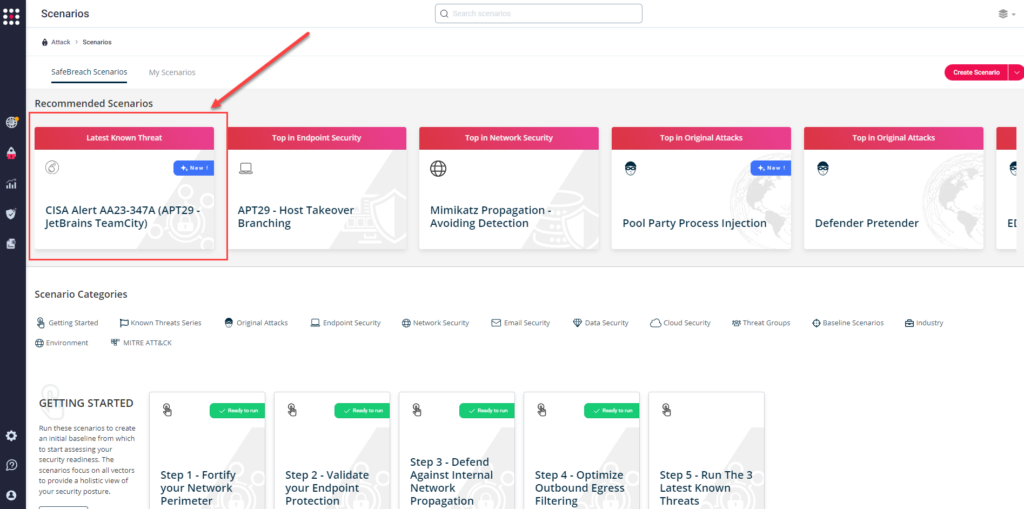
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-347A . Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
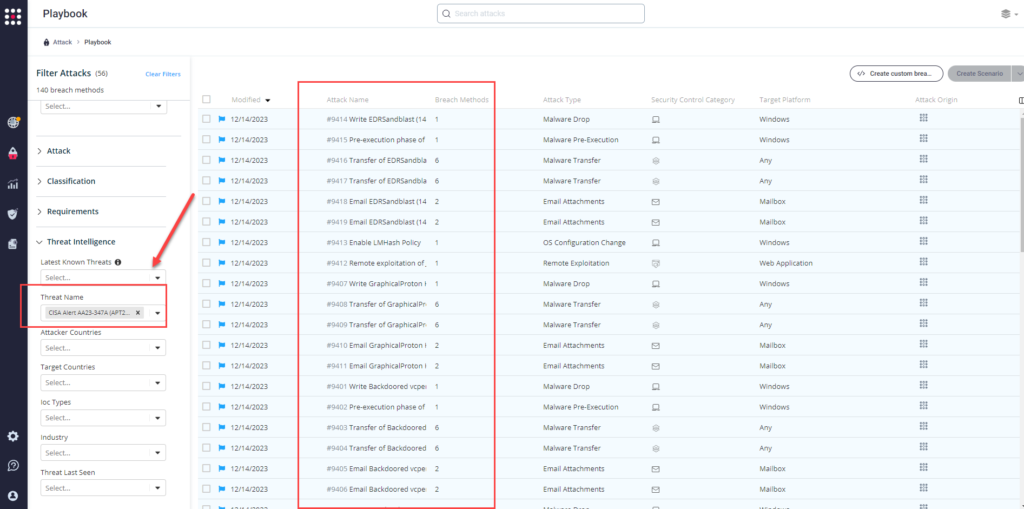
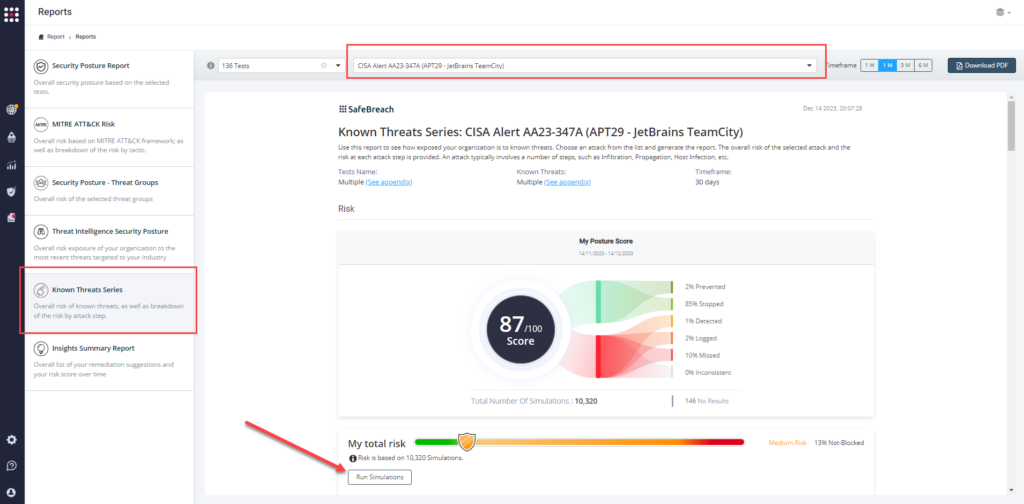
Method 3 – From the Known Attack Series report, select the AA23-347A (APT29 – JetBrains TeamCity) report and select Run Simulations which will run all attack methods.
NOTE – FBI, CISA, NSA, SKW, CERT Polska, and NCSC recommend continually validating your security program, at scale, in a production environment to ensure optimal security against the growing menace of advanced cyber threats. Additional recommendations include:
- Apply available patches for CVE-2023-42793 issued by JetBrains TeamCity in mid-September 2023.
- Monitor the network for evidence of encoded commands and execution of network scanning tools.
- Enable multifactor authentication (MFA) for all services to the extent possible, particularly for webmail, VPN, and accounts that access critical systems.
- Keep all operating systems, software, and firmware up to date.
- Deploy software to identify suspicious behavior on systems.
- For detailed information about mitigations and incident response, please refer to the full advisory
You Might Also Be Interested In
Get the latest
research and news
The post JetBrains TeamCity Vulnerability Exploit: SafeBreach Coverage for US-CERT Alert (AA23-347A) appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/blog/jetbrains-teamcity-safebreach-coverage-for-us-cert-alert-aa23-347a/
如有侵权请联系:admin#unsafe.sh