2023-12-19 07:1:15 Author: blog.qualys.com(查看原文) 阅读量:21 收藏
Misconfiguring Amazon S3 Buckets Can Pose Major Risks
Amazon Web Services (AWS) is the world’s largest cloud security provider, and it provides the ability to store massive amounts of cloud-resident data with the Amazon Simple Storage Service (S3) bucket. Amazon S3 is an object storage solution known for its exceptional scalability, data availability, security features, and performance capabilities. S3 buckets are often used by AWS users to store sensitive or critical business data. When these resources are not adequately secured, they become susceptible to unauthorized access, potentially leading to data breaches due to misconfigurations, as evidenced in recent incidents.
Understanding malicious actors’ tactics, techniques, and procedures provides valuable insights into preventing or promptly addressing such incidents. Attackers use tools like “S3Scanner” and “BucketStream” during the reconnaissance phase to identify exposed ports or resources that can serve as entry points into an environment. Many of these exposed resources, such as S3 buckets, result from misconfigurations and inadequate security practices.
If an attacker has obtained credentials, they can infiltrate the environment and identify exploitable assets. Once inside, attackers can escalate their privileges to gain access to sensitive information, manipulate or delete critical infrastructure components, and carry out other malicious actions. These considerations are described below; they underscore the importance of robust security measures to safeguard valuable data and infrastructure.
Surveying Recent Exploits of S3 Bucket Misconfigurations
In the first quarter of 2023, the International Spy Museum experienced a breach where credit card authorization forms were unintentionally accessed due to a misconfigured cloud storage bucket. The misconfiguration exposed sensitive data, including 100 credit card authorization forms used for student reservations. In another case, a UK-based agency for freelance doctors disclosed the personal details of approximately 3,200 individuals due to unsecured S3 buckets. Cybernews researchers discovered these exposed buckets, potentially containing 98,000 files with personal information.
In June 2023, a well-known sports confederation also faced a comparable situation, where the researchers discovered a misconfigured S3 bucket. The bucket contained copies of 4,600 passports. An attacker may have used his personal information in various detrimental ways.
Similarly, MPD FM, a facility management and security company serving UK government departments, left an open Amazon S3 bucket that exposed sensitive employee data, including passports, national IDs, and more. While the data has been secured since this incident, it highlights the risks of disclosing such information, with potential consequences for employees and the company.
Reindeer, a now-defunct digital marketing firm in New York, inadvertently exposed its Amazon S3 bucket to the public, which resulted in a significant breach, leaking 50,000 files (32 GB) and affecting 306,000 individuals. The exposed data included full names, addresses, emails, phone numbers, and hashed passwords.
MITRE Tactics and Techniques Mapped to S3 Misconfigurations
According to research conducted in 2023 by Qualys TotalCloud Security Insights, cloud resource misconfiguration is the foremost concern for ensuring the security of cloud environments. Inadvertent public exposure of data is a common misconfiguration by users of all major cloud providers. Improper configuration of internet-facing assets can have a cascading impact on the effectiveness of other cloud services. Unfortunately, the convenience of — say, working on cloud assets from anywhere without a VPN — suddenly transforms into a potential breach just waiting to happen. As shown in the research findings below, 31% of S3 buckets are currently open to the public, which puts them at risk of various security vulnerabilities and the potential for subsequent attacks. Public S3 buckets can expose sensitive data and potentially put multiple services at risk.
For example, EC2 instances and RDS databases may be compromised if their access keys, credentials, or backup files are stored in an insecure S3 bucket.
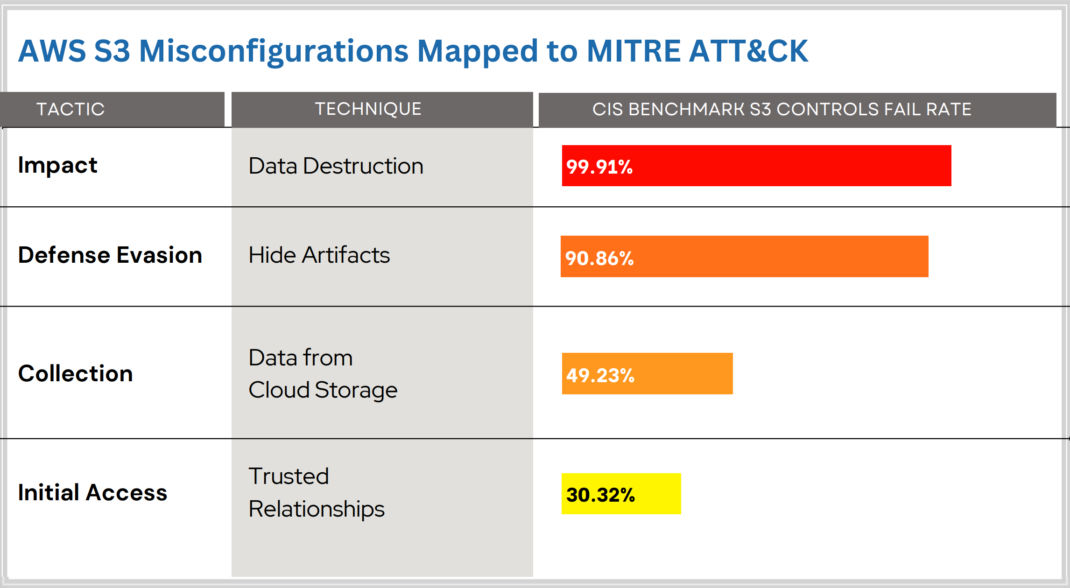
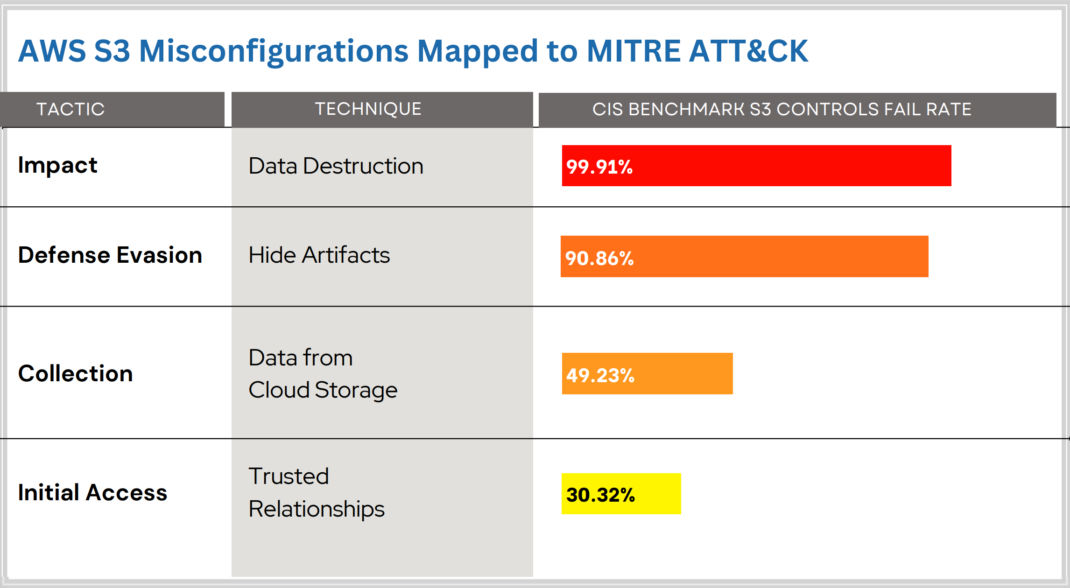
The MITRE ATT&CK framework outlines a variety of tactics that adversaries may use to compromise systems. In the context of the statistics for AWS S3 misconfigurations derived by Qualys research, the details of these tactics are as follows:
1. Impact (Data Destruction): This tactic involves an adversary’s attempt to destroy data, which can significantly disrupt an organization’s operations and lead to the loss of critical information. The high fail rate of 99.91% indicates that most organizations do not implement effective controls to prevent or recover from such attacks.
2. Defense Evasion (Hide Artifacts): Defense evasion consists of techniques that adversaries use to avoid detection throughout their intrusion. With a fail rate of 90.86%, it suggests that adversaries are often successful in concealing their activities, making it challenging for organizations to detect breaches and take timely action.
3. Collection (Data from Cloud Storage): The collection tactic refers to techniques used to gather valuable data from the target. A fail rate of 49.23% in this category implies that almost half of the organizations are vulnerable to unauthorized data extraction from their cloud storage resources.
4. Initial Access (Trusted Relationships): This tactic involves exploiting trust relationships to gain initial entry into an organization’s network. A 30.32% fail rate here indicates that many organizations need to adequately secure their cloud environments against unauthorized access, potentially through compromised credentials or by exploiting trusted connections.
Qualys TotalCloud’s controls described in the next section are designed to counteract these tactics by providing rigorous checks and preventive measures. For example, to mitigate the risk of data destruction, MFA Delete (CID 255) is recommended to add a layer of security before data can be permanently removed. To prevent adversaries from hiding their tracks, enabling object-level logging for read and write events (CID 177 and 178) is crucial. This provides a detailed audit trail that can be analyzed for suspicious activities.
For the collection tactic, encryption in transit and at rest (CID 57 and 67) is key to protecting data from unauthorized access and exfiltration. Lastly, to defend against initial access exploitation, Controls CID-63 through CID-66 focus on securing bucket policies and access controls to ensure only authorized entities can access AWS S3 resources. When properly implemented, these controls help organizations align with the best practices for cloud security and reduce their exposure to the tactics identified by the MITRE ATT&CK framework.
The previous assessment highlights several frequently neglected configuration points that are exploitable by attackers. Figure 2 illustrates the attack path, aligning it with MITRE ATT&CK Tactics and Techniques, and provides recommendations for mitigating misconfigurations using Qualys TotalCloud.
Qualys TotalCloud is a cloud-native application protection platform (CNAPP) that snaps into public cloud environments like AWS. It automatically scans your cloud environment to discover and remediate S3 configuration issues described in this blog. Many of the remediation ideas described below are enabled with Qualys TotalCloud.

The AWS cloud-based environment in Figure 2 shows the flow of data exchange among various resources. Within this environment, a misconfigured S3 Bucket remains publicly accessible, granting direct access to multiple resources, thereby paving the way for diverse types of attacks. Callout numbers in Figure 2 show the locations of potential attacks. Their descriptions enumerated below also suggest best practices for the remediation of these issues.
1. Initial Access and Collection
A publicly exposed S3 bucket is an open door for potential attackers, allowing them to infiltrate your AWS environment. This initial access, often categorized as TA0001 in the MITRE ATT&CK framework, can set the stage for dangerous events.
Initial Presence of Attackers: Once attackers gain access to your S3 bucket, they initiate unauthorized activities. Attackers can infiltrate your systems, lay the groundwork for further attacks, and compromise your digital fortress.
Sensitive Data Exposure (TA0009): The consequences of this breach can be severe. Attackers’ subsequent objectives usually include collecting sensitive data stored within the S3 bucket. This includes but is not limited to credentials, logs, Personally Identifiable Information (PII), and other confidential information.
Compromised Security: The impact of this breach goes beyond just data exposure. It can significantly compromise your overall security posture, potentially resulting in data breaches, financial losses, damage to reputation, operational damage, and even legal consequences.
Organizations should prioritize the following best practices to reduce the potential impact of an S3 bucket compromise for initial access and data collection.
Use Bucket Policies and Access Control Lists (ACLs): Create fine-grained access controls using bucket policies and ACLs. Define who can access the bucket and what they can do. Be explicit about permissions.
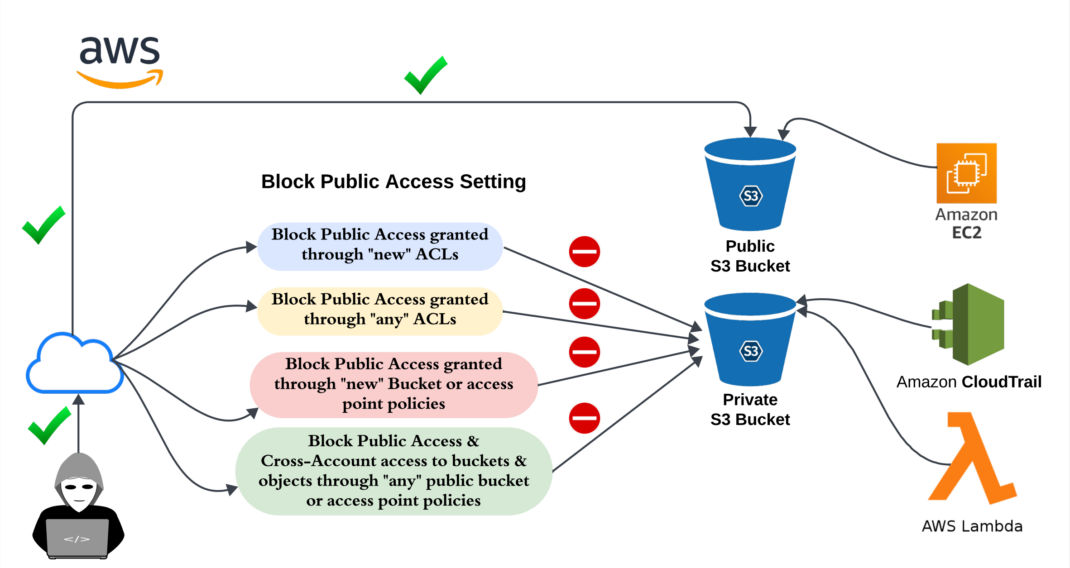
To achieve this, you can follow the security best practices that Qualys TotalCloud provides for S3 buckets. CID numbers refer to Qualys Control IDs used by TotalCloud.
- Block Public Access granted through “new” ACLs (CID 59)
- Block Public Access granted through “any” ACLs (CID 60)
- Block Public Access granted through “new” bucket or access point policies (CID 61)
- Block Public Access and Cross-Account access to buckets and objects through “any” public bucket or access point policies (CID 62)
2. Credential Access and Exfiltration
In the AWS environment, adversaries may employ credential scanning techniques, as highlighted by the MITRE ATT&CK framework under TA0006, to search for AWS access keys or database credentials in public S3 buckets.
The impact of this problem is the potential risk of data exfiltration. Once attackers locate the credentials, they can exploit data exfiltration techniques to transfer sensitive data from the compromised S3 bucket to external endpoints. This could result in severe data breaches and reputational damage for organizations that do not counter these tactics. It is vital to follow the security best practices outlined below:
Data Protection through Encryption: To address these challenges, it is crucial to implement encryption for data at rest (CID 67). This approach aligns with internationally recognized information security norms and significantly amplifies data protection, reducing the risk of unauthorized access to sensitive data.
Strengthen S3 Bucket Security with Encryption: Encryption, especially for customer-managed keys, is highly recommended to enhance data security within S3 buckets (CID 363). This adds an extra layer of defense, making it more challenging for unauthorized parties to access sensitive information.
Securing Data in Transit: Recognizing data vulnerability during transit, organizations should adopt secure data transfer protocols, such as HTTPS. By configuring S3 bucket policies to reject unencrypted HTTP requests (CID 57), they can ensure that all data transfers occur securely, mitigating the risk of interception by malicious actors.
Comprehensive Security Enhancement: Implementing these security measures, including encryption at rest and secure data transfer, comprehensively enhances data security within the AWS ecosystem. It acts as a robust defense mechanism against credential scanning and data exfiltration threats, safeguarding sensitive information and maintaining the integrity of AWS environments.
3. Discovery, Lateral Movement, and Execution
Attackers may attempt to discover S3 buckets as part of their reconnaissance efforts. They can use DNS enumeration, public data source searches, or scanning for publicly exposed S3 buckets.
Discovery (TA0007) in this context helps them identify potential targets for further exploitation. Once an attacker gains initial access to an AWS environment, they may use compromised credentials or vulnerabilities to move laterally within the environment. This lateral movement (TA0008) can involve accessing and exfiltrating data from S3 buckets, mainly if they have obtained sufficient permissions to navigate the AWS infrastructure.
Managing and maintaining permissions in a cloud environment can be daunting, especially within medium to large organizations. This challenge often leads administrators to inadvertently deviate from the least privilege principle, granting unnecessary permissions to users or roles. In the context of S3, such misconfigurations may involve opening ACLs to everyone or All Authenticated users or using wildcard entries like “*” that potentially expose vulnerabilities related to Privilege Escalation (TA0004).
The concept of least privilege signifies granting only the permissions necessary to accomplish a specific objective. For instance, if a web application expects to get some information from the S3 bucket, it should be provided with READ access only for the folders and objects it peruses. S3 bucket least privilege determination is possible in diverse ways. Identity and access management (IAM) role/user access levels can be determined and kept in check using policies that allow actions to be defined explicitly. Another way is through Access Control Lists. The ACLs can permit or deny access to a group of users at once. When configuring Bucket Policy for S3 buckets, it is essential to avoid using wildcard characters (like “*”). Instead, opt for fine-grained permission definitions achievable through policies. Policies allow you to precisely define permissions for various S3 bucket operations, such as “getBucket” and “getObject,” using resource blocks.
As S3 can be accessed through multiple ways, even if requested internally, we suggest following these best practices:
- Ensure the S3 Bucket Access Control List does not Grant Access to Everyone or Authenticated Users (CID 45) to prevent unintended access.
- Avoid using wildcards and maintain a granular (CID 46) in-bucket policy for a well-defined access control strategy.
Attackers might leverage S3 buckets for the execution (TA0002) of malicious payloads or scripts. By placing malicious files within an S3 bucket, they can execute code or commands from these files, potentially compromising the consumer’s environment’s security.
4. Impact
Attackers with compromised credentials or phishing techniques can infiltrate S3 buckets, leading to data exfiltration, theft, or even malicious alterations. The impact could be profound, encompassing data breaches, loss of sensitive information, regulatory non-compliance, financial repercussions, and damage to an organization’s reputation.
Although S3 offers various access methods for ease of use, it is essential to remember that these access options can sometimes be excessively permissive, potentially leading to data destruction (TA0040).
The impact of a compromised S3 bucket extends beyond the initial breach, with a cascade of consequences that can severely affect an organization:
Data Breaches: Unauthorized access to an S3 bucket can lead to data breaches, exposing sensitive customer records, financial data, and proprietary business information. The ramifications of such breaches can be far-reaching, potentially leading to identity theft, fraud, and privacy violations.
Loss of Sensitive Information: Attackers who gain access to S3 buckets can steal, manipulate, or destroy critical and confidential data. This loss compromises an organization’s proprietary assets and can have legal ramifications, including liability for data mishandling and disclosure.
Regulatory Non-Compliance: Breaches of sensitive data stored in S3 buckets can result in regulatory violations, as many industries have stringent data protection and privacy requirements. Non-compliance can lead to significant fines, legal actions, and damage to an organization’s standing with regulatory bodies.
Financial Repercussions: The financial repercussions of an S3 bucket compromise can be substantial. Remediation efforts, including forensic investigations, data recovery, and security enhancements, can incur significant costs. Legal expenses may arise from handling lawsuits and addressing compliance issues. Furthermore, the breach’s aftermath can lead to decreased revenue, as customers may lose trust in an organization’s ability to protect their data.
Reputation Damage: A compromised S3 bucket can tarnish an organization’s reputation and erode trust among customers and partners. Data breach news can spread quickly, causing public relations nightmares and customer churn. Rebuilding trust and restoring a damaged reputation can be lengthy and arduous, often requiring significant marketing and customer outreach investments.
Best Practices for Securing Amazon S3 Buckets
Organizations must proactively implement robust security measures to mitigate these risks and adhere to best practices to safeguard their S3 buckets and sensitive data. Here are some best practices to consider:
- Secure Access Controls: Implement strong access controls and adhere to the principle of least privilege. Only grant necessary permissions to users, roles, and applications.
- Enable Encryption: Encrypt data at rest and in transit using AWS Key Management Service (KMS), specifying Customer Managed Keys (CMK) for robust security.
- Regular Audits: Periodically review and audit your S3 bucket permissions to ensure they remain up-to-date and aligned with security policies.
- Versioning: Enable versioning for S3 buckets to track changes and protect against accidental data deletion or overwrites (CID-48).
- Access Logging: Enable S3 access logging to monitor and track access requests for auditing and security analysis (CID-47).
- Public Access Blocks: Use this S3 feature to prevent unintended public access to your buckets.
- Multi-Factor Authentication (MFA): Enable MFA Delete for critical buckets to add an extra layer of security against destructive actions (CID 255).
- Lifecycle Policies: Configure lifecycle policies to automatically transition or delete objects based on your data retention and archiving needs.
- Content Security Policies: For web applications, implement Content Security Policies (CSP) to define where your content can be loaded and executed, reducing the risk of cross-site scripting attacks.
- Incident Response Plan: Develop and test an incident response plan to swiftly address security incidents and mitigate damage.
- Employee Training: Educate your team on S3 bucket security best practices to reduce the risk of human error.
By adhering to these best practices, you can significantly enhance the security of your S3 buckets and minimize the potential impact of a compromise.
Conclusion
In conclusion, even a minor misconfiguration in an S3 bucket can have far-reaching consequences, potentially resulting in significant exploitation. However, by understanding these risks, you can proactively take measures to bolster the security of your buckets. By carefully examining various security practices, you can ensure that data stored within these buckets remain safe, all while meeting necessary compliance requirements.
Contributors
- Rahul Pareek, Signature QA Engineer, Cloud Security Compliance, Qualys
- Harshal Khachane, Signature Engineer, Cloud Security Compliance, Qualys
如有侵权请联系:admin#unsafe.sh