As CMMC Final Rule approaches, one of the most common concerns defense contractors have is the cost of achieving compliance. CMMC will step up enforcement of the 110 NIST 800-171 controls, making compliance a prerequisite for continued work with the Department of Defense (DoD). In order to achieve certification, defense contractors will need to budget for the implementation of new technologies, training, protocols, and assessments. These costs can add up fast.

Fortunately, there is a way to significantly reduce the cost of achieving compliance: a CMMC enclave. Creating a CMMC enclave allows companies to deploy the tech and resources required to protect CUI for only the part of the organization that must handle sensitive data. This saves time and money, making it an ideal solution for budget-conscious small- to medium-sized contractors.
CMMC Enclave – Definition
The CyberAB’s CMMC Assessment Process (CAP) defines an enclave as “a set of system resources that operate with the same security domain and that share the protection of a single, common, and continuous security perimeter. A segmentation of an organization’s network or data that is intended to ‘wall off’ that network or database from all other networks or systems.”
In simpler terms, you can think of an enclave as a closed room within a house. The house represents the entirety of your organization, but the closed room is the only part of the house where you keep CUI. Thus the closed room is the only part of the house that must meet all of the CMMC compliance requirements.
An enclave refers not only to the physical location of CUI within your network, but also to the individuals who have access to the CUI. Going back to the closed room image, the more people who have a key to that room, the more people you need to train on protocols for handling CUI.
Contractors are responsible for establishing which assets, including endpoints and employees, are included within their CMMC enclave. If your entire organization can access CUI, then your entire organization will be part of your CMMC assessment. That is the most expensive way to do things. Instead, make your enclave as small as possible in order to save time and money.
The more your organization can limit the enclosed perimeter where CUI lives, the more it can limit who has access to CUI, the more you’ll save.
How CMMC enclaves expedite compliance
As mentioned above, creating a CMMC enclave can save you a lot of money. An enclave means a smaller compliance footprint, leaving you with fewer endpoints to protect and assess. This reduces your technology costs, as well as the time required for implementation.
Creating an enclave also means only those employees who need to handle CUI will have access to CUI. This means you’ll only need to train and manage those employees in the applicable protocols for compliance. This, too, will save you time and money.
By reducing the scope of assessment, enclaves make achieving compliance a faster, cheaper, easier process.
How to create a CMMC enclave
Creating an enclave doesn’t need to be complicated. Here’s a step-by-step guide to help you get started.
- Define your scope.
- Create a compliance boundary.
- Implement technologies
- Create policies and procedures
- Conduct a self-assessment against NIST 800-171
The first step in creating a CMMC enclave is to find out where CUI currently lives in your system and who has access to it. If your answer is that it’s everywhere and everyone on your team can access it, you need to seriously consider who must handle CUI as an essential component of their job.
Everyone on your team should not need to touch CUI, with only very few exceptions of very small organizations. Similarly, CUI shouldn’t need to be stored everywhere in your system and accessible from all endpoints.
Your compliance boundary will clearly define the enclave where CUI lives in your system.
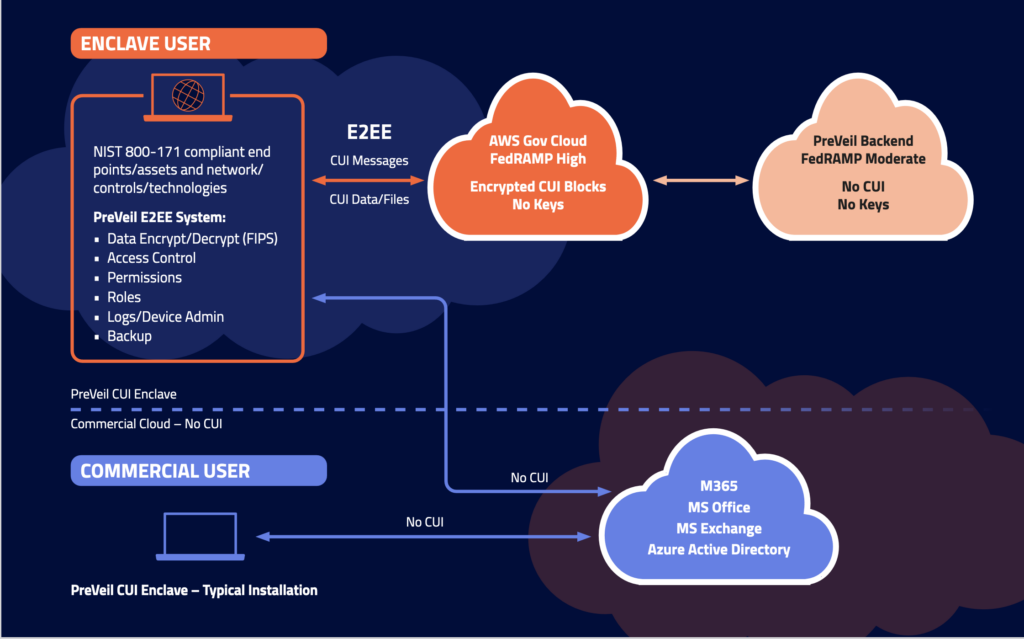
Most CUI is shared through email and file sharing. If you’re currently using a commercial platform like Microsoft O365, your platform does not support CMMC compliance. You will need to implement technologies that can do so.
Ensure the technologies you choose, including email and file sharing platforms, support meet DFARS 7012 c-g requirements and FIPS 140-2 requirements. DFARS 7012 c-g instructs defense contractors how to report cybercrimes such as identity fraud, theft of corporate data or ransomware attacks. FIPS 140-2 sets a cryptographic-based security standard for systems protecting CUI.
Achieving CMMC compliance will require a combination of policies, procedures, and technologies. Your policies and procedures should define who manages CUI, who handles, and how they can do so in a compliant way. The human part of the equation is just as important as implementing secure technologies.
The CMMC controls will perfectly mirror the 110 controls of NIST 800-171. Conduct a self-assessment against NIST 800-171 to determine how close (or far) you are from meeting your compliance requirements today.
Your self-assessment will help you figure out how far you need to go to achieve CMMC compliance. From there, you can map out what you need to do to meet CMMC.
A CMMC Enclave Case Study
PreVeil recently enabled a small-to-medium defense contractor to achieve a perfect score of 110/110 on a Joint Surveillance Voluntary Assessment (JSVA). The game-changer for this organization was the use of an enclave for CUI.
Originally, the organization used Microsoft O365 for its email and file-sharing needs. Microsoft 0365 does not support CMMC compliance. Rather than overhauling their entire system, the organization created an enclave for the fewer than 50 employees that handle CUI. From there, they added PreVeil for email and file-sharing.
Creating a secure enclave allowed the company to reduce scope, avoid rip and replacement, and significantly reduce compliance costs. They were able to achieve a perfect score on their JSVA and the C3PAO conducting the assessment intends to issue a CMMC Level 2 Certification once rulemaking establishes CMMC.
To learn more about how this organization achieved CMMC-readiness, see the full case study here.
Final Thoughts
Small- to medium-sized businesses are used to having to work smarter than the big guys. Enclaves are a key way of doing exactly that. The use of enclaves can help small-medium contractors mitigate compliance costs and secure a competitive advantage.
Learn more:
Video: How to Protect CUI with Compliant Enclaves
The post <span style="color:#f05f2a;">CMMC Enclaves:</span> What they are.<br/> How they help compliance. appeared first on PreVeil.
*** This is a Security Bloggers Network syndicated blog from Blog Archive - PreVeil authored by Orlee Berlove, reviewed by Noël Vestal, PMP, CMMC RP. Read the original post at: https://www.preveil.com/blog/cmmc-enclave/
