2023-12-22 10:42:23 Author: blogs.sap.com(查看原文) 阅读量:7 收藏
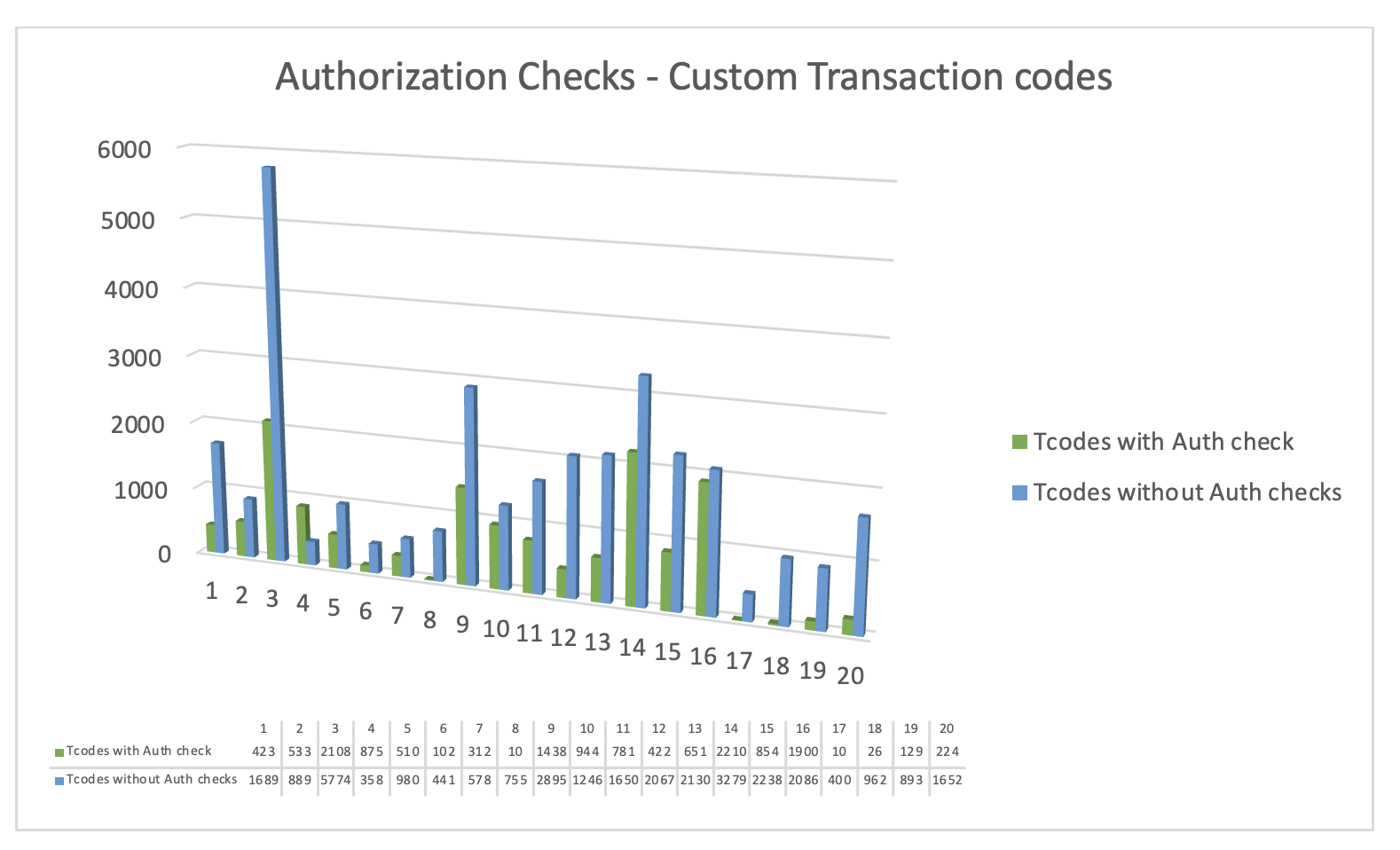
In a recent study, our team delved into the practices of over 50 customers (with 20 responses depicted in the chart) and uncovered a startling reality: a significant number of organizations overlook the importance of securing custom transaction codes with proper authorization checks. The statistics we’ve gathered shed light on this concerning trend, revealing an alarming disregard for crucial security measures.
Did you know? According to IBMs Cost of Data Breach Report, the global average cost of a data breach in 2023 was USD 4.45 million, a 15% increase over 3 years.
Check – Cost of Data breach report.

The report reveal that organizations are intending to allocate above 51% of their budget towards enhancing cyber awareness, improving incident detection and response tools, and other related areas. It’s crucial to emphasize that securing custom transaction codes is the fundamental step that every organization must prioritize from a SAP Security stand point.
SAP stands tall when it comes to customizations and helps organizations to streamline their business processes. Among its many capabilities, custom transaction codes play a pivotal role where organizations can create various custom reports, maintenance views, table maintenance and query views and provide access to them through custom transaction codes.
Understanding the top Risks with custom transaction codes:
Security Vulnerabilities: In many of the cases, custom transaction codes are created without proper authority checks. They are deployed in the production systems without rigorous testing and validation processes. This increases the likelihood of security vulnerabilities, potentially opening doors for unauthorized access, data breaches, or system manipulation.
In a recent project, we noticed that the customer has 2144 custom transaction codes. Here is a synopsis of our analysis:
- 267 transaction codes have authority checks (as most of them call other transaction codes).
- 491 transaction codes allow users to maintain tables where the user profiles have * (star) value maintained for S_TABU_DIS and S_TABU_NAM objects. These transaction codes gives access to critical PA*, Vendor Master, and Customer Master tables as well which are categorized as critical in nature.
- 87 transaction codes are obsolete (the calling transaction codes are no more valid)
- 124 transaction codes call BADIs/BAPIs directly and no check is maintained.
- 51 transaction codes are simple reporting programs.
- 1124 transaction codes doesn’t have any authority checks.
Imagine a scenario where a custom transaction code, “ZFIN_REPORT” is developed without proper authorization checks and is deployed in a company’s SAP production system to generate detailed financial reports. Now, any user within the system can access sensitive financial data using this transaction code. Malicious intent aside, an employee inadvertently executes the ZFIN_REPORT transaction and gains access to critical financial information beyond his role. Consequently, confidential financial reports are leaked outside the intended audience, causing a breach of client confidentiality and regulatory compliance. This breach not only damages the company’s reputation for safeguarding sensitive information but also incurs financial losses due to potential lawsuits, penalties for non-compliance, and loss of client trust.
The aftermath includes extensive damage control efforts, legal fees, potential fines, and a substantial hit to the company’s credibility, ultimately resulting in a loss of market confidence and future business opportunities.
Compliance and Governance Challenges: Many of the organizations create custom transaction codes to help business teams in performing their job duties quickly. They become the organization assets over a period of time. However, many organizations don’t identify the risks associated with these transaction codes. Deploying custom transaction codes without validating them against risks will lead to non-compliance with industry regulations or internal governance standards and may cause significant damage. Custom transactions might inadvertently bypass controls, leading to audit failures and compliance breaches.
Consider a scenario where a company implemented custom transaction codes within their SAP system without conducting a thorough risk assessment. These transaction codes lack the necessary checks, potentially sidestepping crucial controls. This oversight triggers a chain reaction of compliance breaches and audit failures, exposing the company to penalties, legal consequences, and a loss of trust from stakeholders and regulatory bodies alike. The absence of a proactive risk identification strategy turns these once-helpful custom codes into liabilities, causing substantial harm to the organization’s reputation and financial stability.
Dependency and Maintenance Concerns: Custom transaction codes might create dependencies on specific personnel or developers for maintenance and regular updates. In case of staff turnover or lack of documentation, this reliance can become a substantial operational risk.
Custom transaction codes in SAP bring some challenges when they’re not taken care of properly. While we can see a few of these problems, there are many more that might show up if we’re not careful.
Strategies for Risk Mitigation:
1. Ensure to have proper authority checks: It’s recommended to implement AUTHORITY CHECKS for the custom transaction codes. This ensures that authorization restrictions are appropriately implemented, preventing unauthorized individuals from accessing, or manipulating critical business data.
2. Always update SU24 check proposals: Manually adding Authorization objects in roles and maintaining them or relying on enabler (bolt-on) roles isn’t recommended. The best practice involves establishing a direct correlation between transaction codes and the relevant authorization objects. It’s critical to maintain these relationships in SU24 check proposals for effective and secure maintenance.
3. Implement a robust Change Management process: Ensure that no transaction codes are deployed to production without AUTHORITY CHECKS defined. If custom transaction codes involve Table Maintenance, verify that the associated tables have appropriate Authorization Groups assigned (Check table TDDAT). Tables in the “&NC&” Authorization Group grant broader access, typically ABAPers use it for ease of maintenance. However, it’s crucial to assign custom tables to a different authorization groups for stricter control. Additionally, ensure that authorization objects S_TABU_DIS and S_TABU_NAM are maintained properly.
Lastly, before deploying the custom transaction code to production, ensure the SU24 check proposals are updated correctly.
4. Regular Audits and Monitoring: Keep an eye on the custom transaction codes. Here are some of the questions that should go into your check list:
- Which custom transaction codes are deployed into the production system?
- What kind of authorization restrictions have been implemented?
- What is the status of SU24 check proposals?
- Which critical tables/data users can access using the custom transaction codes?
- Who has access to it?
- Are they giving access to any critical business data through backdoor?
- If it is calling an existing transaction code, why do business need a customization? How relevant it is to the business?
- Which roles gives access to these custom transaction codes?
- What is the risk involved in these custom transaction codes?
In addition, it is recommended to do a periodic review of the custom transaction code usage and remove those which are no more relevant to the business.
5. Thorough Risk Assessment: Conduct comprehensive risk assessments for custom transactions before deploying them in the production environment. This includes evaluating security loopholes (backdoors), performing code reviews, and ensuring compliance with industry standards.
6. Documentation: Maintain detailed documentation for custom codes. This includes functional specifications, technical designs, and operational manuals. Facilitate knowledge transfer among team members to reduce dependencies.
7. Governance and Compliance Adherence: Align custom transactions with governance frameworks and compliance standards. This involves enforcing proper access controls (critical transaction codes should be given only through Firefighter IDs), implementing a proper segregation of duties by updating the rulesets, and regular compliance checks.
I must speak about some of the specialized tools such as ToggleNow’s xPedite that have emerged that evaluates the risks associated with the custom transaction codes, provide valuable insights and even updates the Risk IDs and maintain SU24 check proposals with a click. It deep dives into the transactions, propose the relevant risk IDs that needs to be updated with the custom transaction codes and with a click update the risk IDs as well as the SU24 check proposals.

Custom Transaction code Analyzer
Conclusion:
Custom transaction codes in SAP present organizations with both opportunities and risks. While they offer customization capabilities to streamline processes, they also pose potential security, compliance, and operational challenges. Mitigating these risks demands a proactive approach involving thorough assessment, continuous monitoring, adherence to best practices, and a robust governance framework. By carefully managing and mitigating risks associated with custom transactions, organizations can harness the power of SAP while ensuring a secure and efficient operational environment.
如有侵权请联系:admin#unsafe.sh