
2023-12-23 13:38:37 Author: securityboulevard.com(查看原文) 阅读量:27 收藏
Recent attacks have demonstrated a significant growth in Zero Days and Remote Code Execution. Kratikal has observed that threat actors have placed a special focus on Web Apps, IoT, and Open-Source tools. In this blog, we will discuss a recently found Remote Code Execution attack in Apache Struts2. Apache Struts helps developers to create web applications in Java. It also helps developers maintain and secure their web applications.
For developers and security professionals, december didn’t start with something merry, but rather with a threatful bang. On December 7th, the Apache Software Foundation disclosed a critical vulnerability in Apache Struts2, named CVE-2023-50164. This flaw, embedded in the core of a popular open-source web framework, carries an alarming high Common Vulnerability Scoring System (CVSS) score of 9.8, placing it firmly in the “critical” category. So, what exactly makes CVE-2023-50164 so perilous, and how can we patch this vulnerable hole in our web applications.
Why Does It Matter? Understanding The Vulnerability
At its core, CVE-2023-50164 exploits a flaw in Struts2’s file upload logic. Imagine this: an attacker crafts a carefully created file upload request, manipulating specific parameters. This request, instead of uploading a harmless document, allows the attacker to traverse the server’s file system, potentially reaching sensitive data or even planting a malicious file. But the true nightmare unfolds when you realize this malicious file can be executed. Yes, you read that right – Remote Code Execution (RCE) is on the table.
Parameter Pollution & Path Traversal Bug
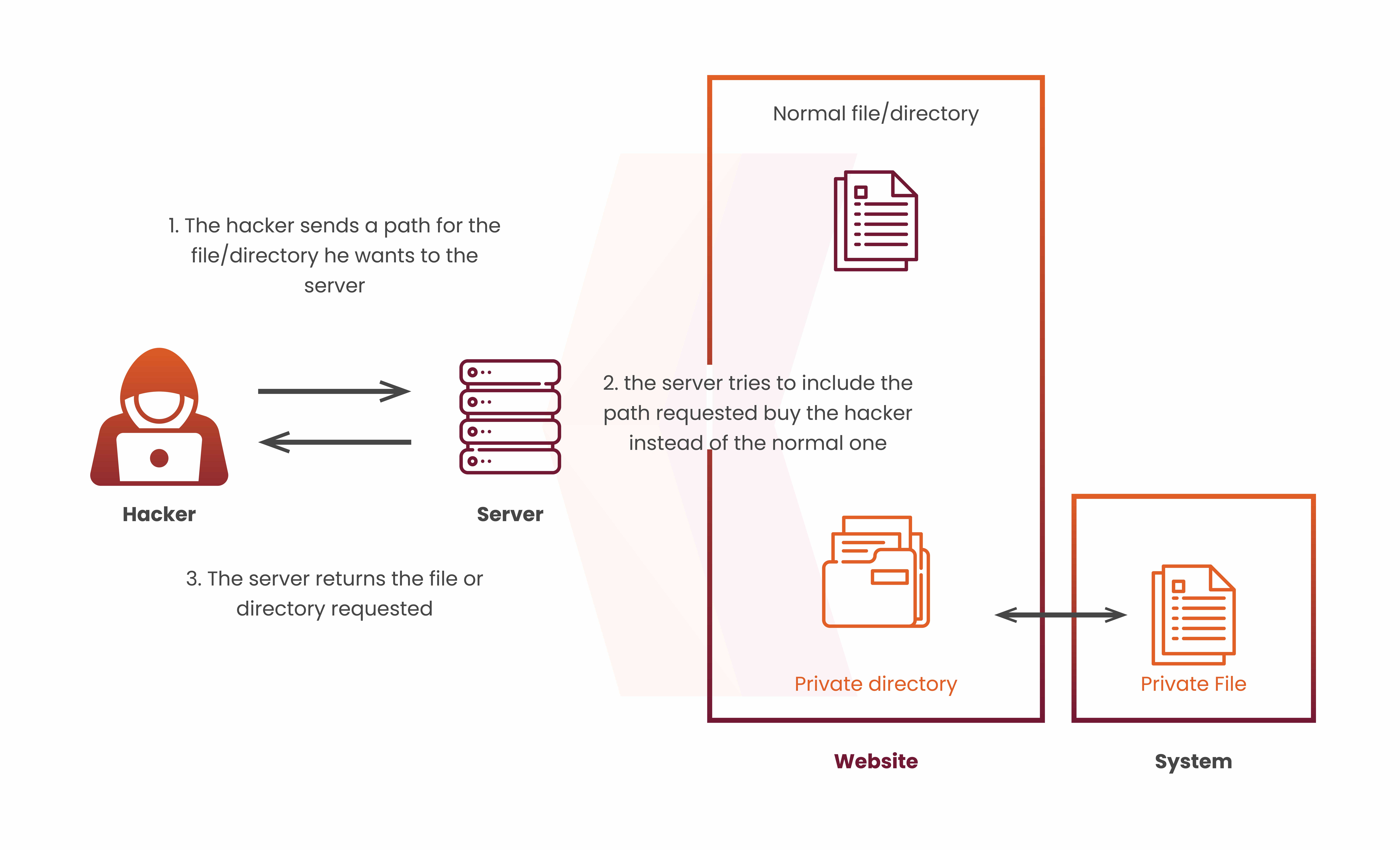
This bug is leading to path traversal leading to access files outside the root directory. The vulnerability also leads to parameter pollution when an attack changes the initial parameter and adds additional parameters in lowercase. This overrides the internal file name variable and that is what causes the system to exploit and the attacker to gain Remote Code Execution.
RCE is a big concern when it comes to secure systems. If exploited, this weak spot can let a hacker take over a server. Things like user passwords, fiscal details, or disrupting activities could then be on the line. The effects could be huge, harming folks, businesses, and crucial resources alike.
The Scope of Threat: Who’s Vulnerable?
What’s the worst part? This vulnerability affects many applications developed with Struts2. All versions 2.5.0 to 2.5.32 and 6.0.0 to 6.3.0 are vulnerable. Struts2 boasts a wide user base, powering enterprise applications, government websites, and private businesses. This means that the potential for attacks is high, making CVE-2023-50164 a critical threat to organizations around the world.
Combating Remote Code Execution: Immediate Response is Required
So, what organizations are supposed to do to patch immediately? Apache has released patched versions for all affected Struts2 versions. Upgrading to Struts 2.5.33 or Struts 6.3.0.2 or later is the ultimate and most effective solution. Don’t delay, delaying can lead to severe outcomes.
But only patching is not going to help you, to stop such critical vulnerability here are some additional tips:
Scan your Environment: Conduct a thorough scan of your systems to identify any applications using vulnerable versions of Struts2. Prioritize patching these applications first.
Monitor for Suspicious Activity: Implement security monitoring tools and SIEM solutions to detect any suspicious activity that might indicate an attempted exploit.
Raise Awareness: Train your employees and developers about the vulnerability and the importance of patching. Encourage a culture of security awareness to prevent future exploits.
What After Patching: Building a Defense in Depth
While patching is crucial, it’s essential to remember that it’s just one piece of the puzzle. A layered security approach is key to truly mitigating the risks posed by vulnerabilities like CVE-2023-50164. Here are some additional layers you can add to your defense:
Implement Input Validation: Validate all user input to prevent malicious code from being uploaded or executed.
Restrict File Extensions: Limit the types of files that can be uploaded to only those necessary for your application.
Book a Free Consultation with our Cyber Security Experts

Taking Control of User Access: Make sure you are implementing strict user access control to only allow privileged users to access sensitive data.
Remember to Keep Your Software Up to Date: This is the basis that everyone must follow whether you are in the field of cybersecurity or not.
Conclusion
CVE-2023-50164 is a critical vulnerability with potentially destructive consequences. But by taking swift action, raising awareness, and implementing a layered security approach, we can mitigate the risks and keep our systems from becoming victims of this fundamental flaw.
There is a critical need to address the serious vulnerability CVE-2023-50164 in Apache Struts2. While patching is important, an all-encompassing defense plan is significantly vital. Upgrade to Struts 2.5.33 or Struts 6.3.0.2, do system scans, keep an eye out for unusual activity, and spread awareness by organizations.
Kratikal, a CERT-In empanelled auditor is an essential component in the battle against cyber threats, providing cybersecurity solutions through Governance, Risk, and Compliance to identify, stop, and minimize vulnerabilities. Kratikal helps businesses defend against ever-evolving threats by providing them with proactive defense, security training, and sophisticated scanning tools. Remember, security is an ongoing journey, not a one-time fix. Patching, cyber vigilance, and proactive defense are our weapons against the ever-evolving cyber threats. Let’s use it wisely and make our digital world safer.
The post Impact of Apache Struts2 Code Execution Vulnerability appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Riddika Grover. Read the original post at: https://kratikal.com/blog/impact-of-apache-struts2-code-execution-vulnerability/
如有侵权请联系:admin#unsafe.sh