The threat actor referred to as Cloud Atlas has been linked to a set of spear-phishing attacks on Russian enterprises.
Targets included a Russian agro-industrial enterprise and a state-owned research company, according to a report from F.A.C.C.T., a standalone cybersecurity company formed after Group-IB's formal exit from Russia earlier this year.
Cloud Atlas, active since at least 2014, is a cyber espionage group of unknown origin. Also called Clean Ursa, Inception, Oxygen, and Red October, the threat actor is known for its persistent campaigns targeting Russia, Belarus, Azerbaijan, Turkey, and Slovenia.
In December 2022, Check Point and Positive Technologies detailed multi-stage attack sequences that led to the deployment of a PowerShell-based backdoor referred to as PowerShower as well as DLL payloads capable of communicating with an actor-controlled server.
From USER to ADMIN: Learn How Hackers Gain Full Control
Discover the secret tactics hackers use to become admins, how to detect and block it before it's too late. Register for our webinar today.
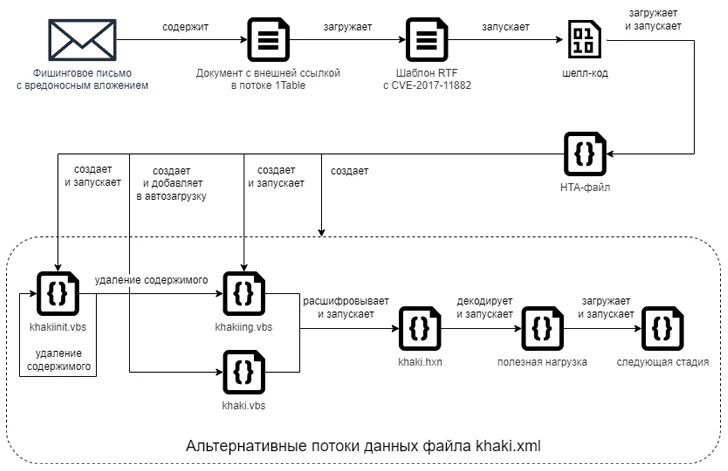
Join NowThe starting point is a phishing message bearing a lure document that exploits CVE-2017-11882, a six-year-old memory corruption flaw in Microsoft Office's Equation Editor, to kick-start the execution of malicious payloads, a technique Cloud Atlas has employed as early as October 2018.
"The actor's massive spear-phishing campaigns continue to use its simple but effective methods in order to compromise its targets," Kaspersky noted in August 2019. "Unlike many other intrusion sets, Cloud Atlas hasn't chosen to use open source implants during its recent campaigns, in order to be less discriminating."
F.A.C.C.T. described the latest kill chain as similar to the one described by Positive Technologies, with successful exploitation of CVE-2017-11882 via RTF template injection paving the way for shellcode that's responsible for downloading and running an obfuscated HTA file. The mails originate from popular Russian email services Yandex Mail and VK's Mail.ru.
The malicious HTML application subsequently launches Visual Basic Script (VBS) files that are ultimately responsible for retrieving and executing an unknown VBS code from a remote server.
"The Cloud Atlas group has been active for many years, carefully thinking through every aspect of their attacks," Positive Technologies said of the group last year.
"The group's toolkit has not changed for years—they try to hide their malware from researchers by using one-time payload requests and validating them. The group avoids network and file attack detection tools by using legitimate cloud storage and well-documented software features, in particular in Microsoft Office."
The development comes as the company said that at least 20 organizations located in Russia have been compromised using Decoy Dog, a modified version of Pupy RAT, attributing it to an advanced persistent threat actor it calls Hellhounds.
The actively maintained malware, besides allowing the adversary to remotely control the infected host, comes with a scriptlet designed to transmit telemetry data to an "automated" account on Mastodon with the name "Lamir Hasabat" (@lahat) on the Mindly.Social instance.
"After materials on the first version of Decoy Dog were published, the malware authors went to a lot of effort to hamper its detection and analysis both in traffic and in the file system," security researchers Stanislav Pyzhov and Aleksandr Grigorian said.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.