点击上方[蓝字],关注我们
本文仅用于技术讨论与学习,利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,文章作者及本公众号团队不为此承担任何责任。
今天,我将教大家如何破解Windows机器上受保护的.ZIP文件的密码。为了更好地理解,我创建了一个名为“secret.zip”的受密码保护的ZIP文件,如下所示。我们将在本文中一步一步地破解它的密码。
由于ZIP文件对密码的错误尝试没有限制,我们将使用一个名为“John the Ripper”的工具对其进行暴力破解,而不是猜测它。按照下面的步骤在Windows计算机上成功安装它。
John the Ripper是一个开源的密码安全审计和密码恢复工具,适用于许多操作系统。
1. 导航到https://www.openwall.com/john/。由于我在64位Windows机器上,我将安装“jumbo-1 64位Windows二进制文件”。
下载后,解压缩ZIP文件。
导航到下载文件中的“run”文件夹并找到“zip2john.exe”。
在当前文件夹(/run)中打开CMD并输入以下命令:
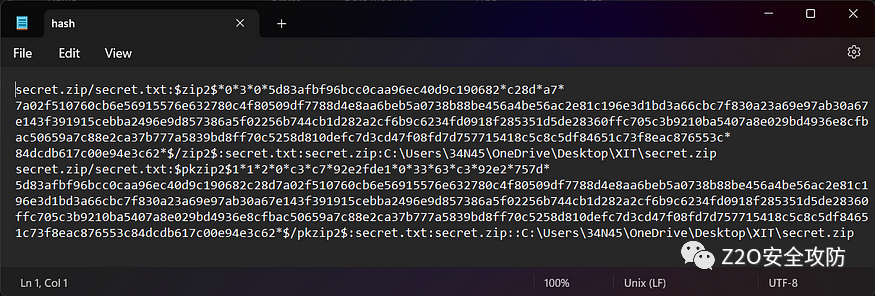
zip2john.exe target.zip我们可以看到文件哈希,我们将使用它来破解目标文件的密码。
要将此哈希文件保存到当前文件夹,请运行以下命令:
zip2john.exe target.zip > hash现在,在记事本中打开哈希文件。
运行以下命令:
john hash我们已经成功破解了密码。
制作自己的自定义单词列表或使用自定义单词列表很简单-只需考虑目标可能用作密码的内容,例如他们名字或最喜欢的爱好。也可以在GitHub或SecLists等网站上找到免费的单词列表来获得一些想法。然后,你使用这些单词使用相同的过程来猜测密码。
使用SecLists获取自定义PassWordlist
SecLists是用于道德黑客和网络安全的单词列表的强大资源。Dorks是在搜索引擎上查找特定信息的搜索查询。转到SecLists GitHub存储库:https://github.com/danielmiessler/SecLists。
点击“Code”,然后“下载ZIP”,以获得整个集合。
然后我们就拥有了一个基于自定义搜索条件的自定义单词列表。此列表可用于进一步的密码破解。
你可以在下载的文件中的“doc”文件夹中找到破解其他文件的使用指南。
Cracking ZIP files with JtR Jumbo
=================================1. Run zip2john on password protected .zip file(s).
E.g. $ ../run/zip2john target.zip > hash
2. Run john on the output of zip2john.
E.g. $ ../run/john hash
3. Wait for the password to get cracked.
Cracking PDF files with JtR
---------------------------
1. Run pdf2john.pl on the .pdf file(s).
E.g. $ ../run/pdf2john.pl test.pdf > hashes
2. Run john on the output of pdf2john.pl program.
E.g. $ ../run/john hashes
Cracking Tezos keys with JtR Jumbo
==================================
1. Run tezos2john.py and provide it with the required data. Run tezos2john.py
without any options to see the usage instructions.
E.g. $ ../run/tezos2john.py 'put guide flat machine express cave hello connect stay local spike ski romance express brass' '[email protected]' 'tz1eTjPtwYjdcBMStwVdEcwY2YE3th1bXyMR' > hashes
E.g. $ ../run/tezos2john.py 'monster crack glance favorite humble group bone grid clock bottom employ gold jelly fatigue tragic' '[email protected]' 'tz1Zgd3LHuryw6rBzsQKnBMVqu99KzWankj8' >> hashes
The passwords for these sample hashes are "4FGU8MpuCo" and "VPhvU2LgyJ" respectively.
2. Run john on the output of tezos2john.py script.
E.g. $ ../run/john hashes
3. Wait for the password(s) to get cracked.
Cracking password protected ssh private keys
============================================
1. Build JtR-jumbo
2. Run ssh2john.py on SSH private key file(s)
3. Run john on the output of step 2.
Cracking bitcoin-qt (bitcoin) wallet files with john
====================================================
1. Run bitcoin2john.py on bitcoin wallet file(s).
E.g. $ ../run/bitcoin2john.py wallet.dat >> hashes
2. Run john on the output of bitcoin2john.py script.
E.g. $ ../run/john hashes
3. Wait for the password(s) to get cracked.
This document is about cracking password protected BitLocker encrypted
volumes with JtR.
Step 1: Extract the hash
------------------------
In order to use the BitLocker-OpenCL format, you must produce a well-formatted
hash from your BitLocker encrypted image. Use the bitlocker2john tool to
extract hashes from password protected BitLocker encrypted volumes. It returns
four output hashes with different prefixes:
* If the device was encrypted using the User Password authentication method,
bitlocker2john prints these two hashes:
* $bitlocker$0$... : it starts the User Password fast attack mode
* $bitlocker$1$... : it starts the User Password attack mode with MAC verification (slower execution, no false positives)
* In any case, bitlocker2john prints these two hashes:
* $bitlocker$2$... : it starts the Recovery Password fast attack mode
* $bitlocker$3$... : it starts the Recovery Password attack mode with MAC verification (slower execution, no false positives)
Hash extraction example,
$ ../run/bitlocker2john minimalistic.raw # operate on a disk image
Signature found at 0x00010003
Version: 8
Invalid version, looking for a signature with valid version...
Signature found at 0x02110000
Version: 2 (Windows 7 or later)
VMK entry found at 0x021100b6
Key protector with user password found
minimalistic.raw:$bitlocker$0$16$e221443f32c419b74504ed51b0d66dbf$1048576$12$704e12c6c...
Instead of running bitlocker2john directly on BitLocker encrypted devices
(e.g. /dev/sdb1), you may use the dd command to create a disk image of a
device encrypted with BitLocker
$ sudo dd if=/dev/disk2 of=disk_image conv=noerror,sync
+4030464+0 records in
+4030464+0 records out
+2063597568 bytes transferred in 292.749849 secs (7049013 bytes/sec)
For further details about User Password and Recovery Password attacks, please
refer to the Wiki page: http://openwall.info/wiki/john/OpenCL-BitLocker.
Step 2: Attack!
---------------
Use the BitLocker-OpenCL format specifying the hash file:
$ ./john --format=bitlocker-opencl --wordlist=wordlist target_hash
Currently, this format is able to evaluate passwords having length between 8
(minimum password length) and 55 characters.
The mask you can use to generate Recovery Passwords is:
-mask=?d?d?d?d?d?d[-]?d?d?d?d?d?d[-]?d?d?d?d?d?d[-]?d?d?d?d?d?d[-]?d?d?d?d?d?d[-]?d?d?d?d?d?d[-]?d?d?d?d?d?d[-]?d?d?d?d?d?d
Links
-----
Samples BitLocker images for testing are available at,
* https://github.com/kholia/libbde/tree/bitlocker2john/samples
* https://github.com/e-ago/bitcracker/tree/master/Images
Samples of User Password/Recovery Passwords dictionaries are available at
https://github.com/e-ago/bitcracker/tree/master/Dictionary
More information on BitLocker cracking can be found at,
* http://openwall.info/wiki/john/OpenCL-BitLocker
* https://github.com/e-ago/bitcracker
Cracking Mozilla Firefox, Thunderbird and SeaMonkey master passwords
====================================================================
1. Run mozilla2john.py on key3.db file.
./mozilla2john /some/path/key3.db > mozilla.in
2. Run john on output of mozilla2john.
./john mozilla.in
3. Wait for master password to get cracked.
学习圈子
一个引导大家一起成长,系统化学习的圈子。
如果看到这里的师傅是基础不够扎实/技术不够全面/入行安全不久/有充足时间的初学者...其中之一,那么欢迎加入我们的圈子,圈子提供以下内容:
目前已经规划了几个月的内容:
欢迎加入我们,一起学习:
交流群
关注公众号回复“加群”,添加Z2OBot好友,自动拉你加入Z2O安全攻防交流群(微信群)分享更多好东西。(QQ群可直接扫码添加)
关注我们
关注福利:
回复“app" 获取 app渗透和app抓包教程
回复“渗透字典" 获取 针对一些字典重新划分处理,收集了几个密码管理字典生成器用来扩展更多字典的仓库。
回复“书籍" 获取 网络安全相关经典书籍电子版pdf
回复“资料" 获取 网络安全、渗透测试相关资料文档
点个【 在看 】,你最好看
如有侵权请联系:admin#unsafe.sh