Too Long; Didn't Read
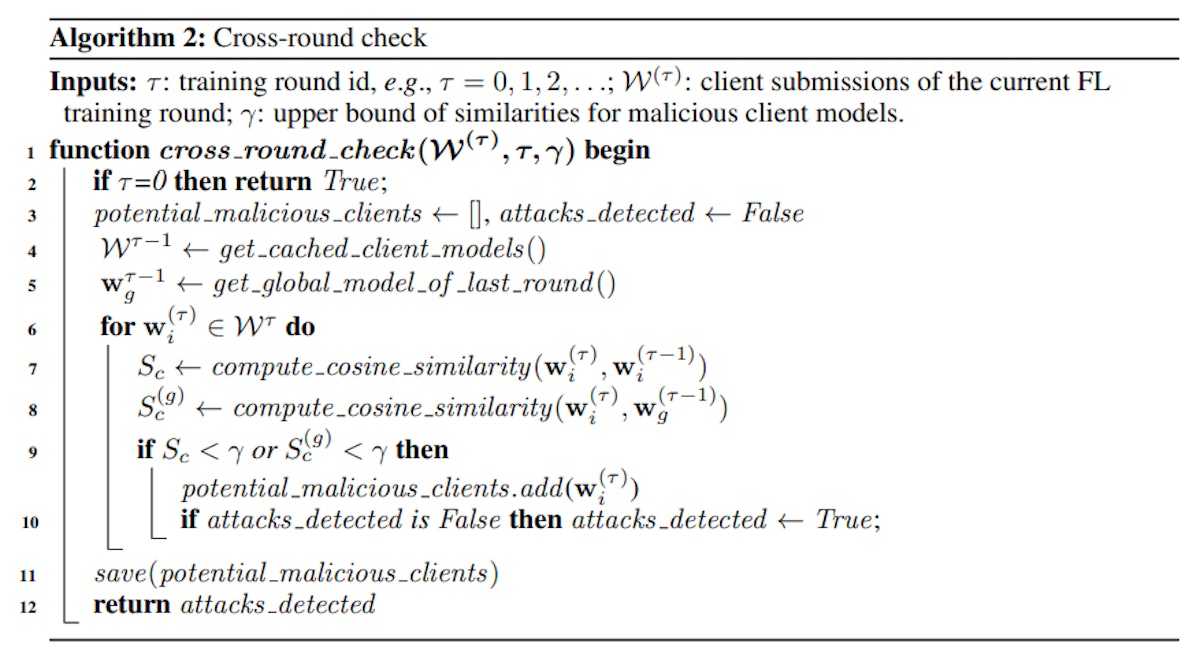
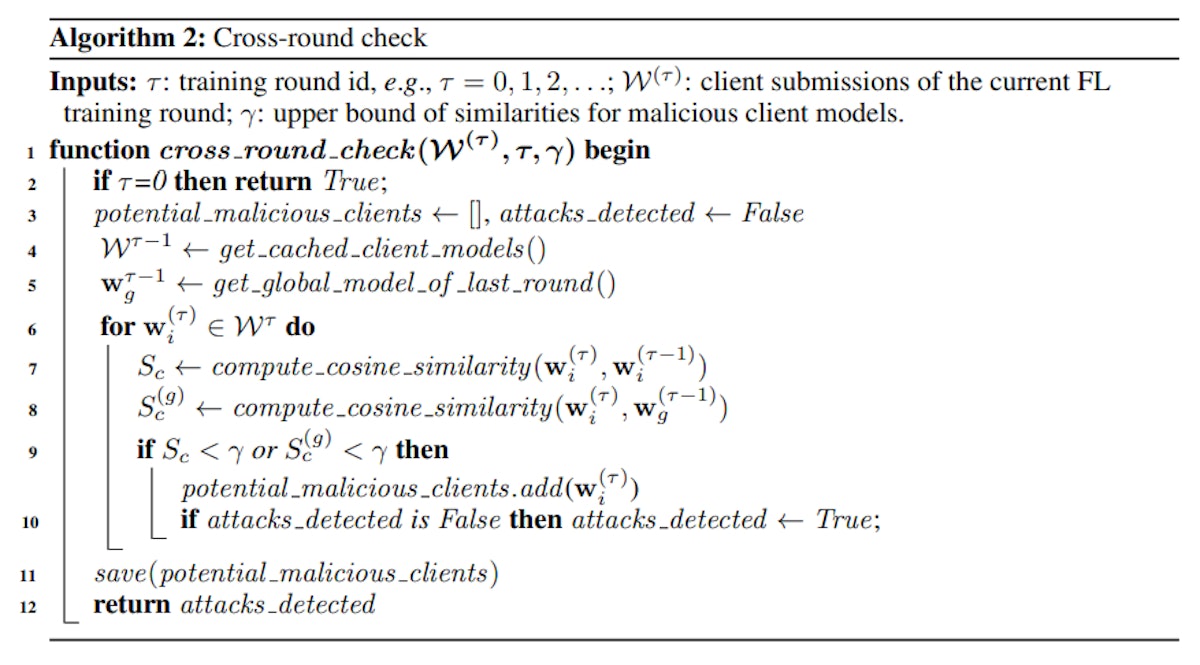
Cross-Round Check: The algorithm initializes with reference models, detecting potential attacks in Federated Learning rounds. It skips the check if no reference models exist. Cross-Client Anomaly Detection: Utilizing the three sigma rule, this stage assesses potentially malicious clients. L2 scores guide model removal, and an approximate average model is computed for subsequent rounds, ensuring robust security in Federated Learning.

@quantification
Quantification Theory Research Publication
The publication about the quantity of something. The theory about why that quantity is what is. And research!
Receive Stories from @quantification

RELATED STORIES





L O A D I N G
. . . comments & more!