2024-1-4 18:7:24 Author: blogs.sap.com(查看原文) 阅读量:5 收藏
(Jana Subramanian serves as Head of Cybersecurity, APJ Strategic Customer Engagements and is a Fellow of Information Privacy (FIP), awarded by the International Association of Privacy Professionals (IAPP). In this role, Jana supports strategic customer engagements on cybersecurity, data privacy, multi-cloud security integration architecture, contractual assurance, audit, and compliance.)
Introduction
In today’s cloud-driven world, reliable cloud computing is everything. But ensuring its safety is contingent upon two essential pillars: cybersecurity and data privacy. While crucial and often inter-linked, these pillars play distinct roles in safeguarding our digital assets in cloud and foundation of everything we do in the digital realm. Through my own journey within this intricate domain, I have come to appreciate the nuanced differences between these areas. Each pillar holds unique characteristics that are crucial for ensuring the security and privacy of our cloud environment.
This blog delves into the distinctions and unique synergy between cybersecurity and data privacy. Also, with the escalating demand for specialized knowledge in Data Privacy field, I will attempt to shed some light on highly valued data privacy certifications offered by IAPP and ISACA. These certifications lay out a clear path for learning and specializing in data privacy domain and an established pathways for cybersecurity professionals who want to transition to the data privacy domain.
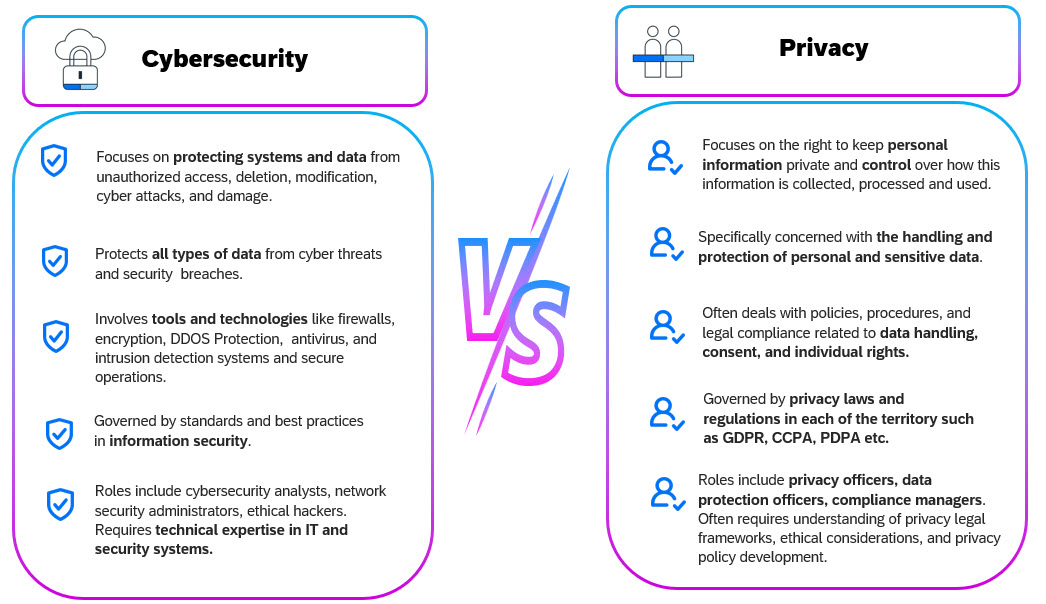
Distinguishing Cybersecurity and Data Privacy
The following table illustrates the key differences between cybersecurity and privacy.
| S.No | Feature | Cybersecurity | Privacy |
| 1 | FOCUS |
|
|
| 2 | GOAL |
|
|
| 3 | METHODS |
|
|
| 4 | TYPE OF THREATS |
|
|
| 5 | IMAPCT |
|
|

Figure 1: Cybersecurity Vs Privacy
Protecting Personal Data – Technical and Organization Measures
Most privacy regulations around the globe including GDPR and PIPL emphasize two critical types of measures to safeguard personal data: technical and organizational measures. These are mandatory elements for compliance and play a critical role in protecting individuals’ privacy rights.
What are Technical and Organizational Measures:
Technical measures refer to the tools and technologies used to protect personal data from unauthorized access, disclosure, alteration, and destruction. The essence of technical measures remains in their ability to create a robust defence against cyber threats and data breaches, leveraging technology to secure data across various processing stages. Some of the technical measures may be embedded within the cloud applications.
Organizational measures, on the other hand, encompass the internal policies, procedures, and practices that govern how an organization handles personal data. These are less about technology and more about the management, culture, and governance of data processing. Organizational measures are crucial for embedding data protection into the fabric of an organization, ensuring that every member understands and contributes to the safeguarding of personal data.
You may refer to Technical and Organizational Measures for SAP cloud services that are part of contractual assurance in SAP role as a “data processor” for SAP Cloud Services.
The following table broadly provides illustrative example for technical and organizational measures.
| Examples of Technical Measures | Examples of Organizational Measures |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Global Privacy Certifications for aspiring Privacy professionals
The International Association of Privacy Professionals (IAPP) and ISACA offer different certifications in the field of privacy, each with its own focus and benefits.
The International Association of Privacy Professionals (IAPP): This is the largest and most extensive worldwide community focused on information privacy. The IAPP offers privacy certifications that assist professionals in enhancing their skills and career growth. These certifications provide essential knowledge and tools for effectively handling privacy risks and safeguarding data in organizations. As technology and regulatory landscape constantly evolve and change, these certifications are updated providing a structured learning and testing of skills. The table below provide high level details and links for anyone interested in pursuing privacy skills and certifications.
| S.No | Certification | Description |
| 1 | Certified Information Privacy Professional (CIPP) |
|
| 2 | Certified Information Privacy Manager (CIPM) |
|
| 3 | Certified Information Privacy Technologist (CIPT) |
|
| 4 | Artificial Intelligence Governance Professional (AIGP) |
|
To earn credentials from the International Association of Privacy Professionals (IAPP), you need to become a professional member of the IAPP and register for each exam individually. Preparing for these exams requires a comprehensive understanding of privacy regulations and case studies. Many of the exam questions are scenario-based and require an in-depth understanding of privacy and analyze specific case study, as well as the ability to interpret regulations in the context of these scenarios. This process involves not only knowing facts but also understanding how privacy principles apply in real-world situations. The reference materials and books are available in the IAPP once you become a member. Earning CIPP credentials may take between 3-6 months depending on your effort, prior knowledge, practical experience among others.
ISACA (Information Systems Audit and Control Association): ISACA’s Certified Data Privacy Solutions Engineer (CDPSE) certification tackles the critical technical skills gap in data privacy. It empowers aspirants to assess, build, and implement comprehensive privacy measures, minimizing risk, enhancing efficiency and in navigating the complex landscape of modern data protection. The main focus on the certification is on privacy governance, privacy architecture and data life cycle and is more tuned towards technical skills.
While decision between taking the IAPP’s Certified Information Privacy Professional (CIPP) certification and ISACA’s Certified Data Privacy Solutions Engineer (CDPSE) certification depends on your professional focus and career aspirations, I would think that CIPP would be more suitable for Privacy Lawyers, Privacy Policy Professional, Data Protection Officers, Privacy Managers and Consultants. ISACA’s CDPSE may be suitable for technical professionals, privacy implementors, Risk Assessment and Management. It is possible to obtain Fellow of Information Privacy from IAPP if one passes CIPP as well as CIPM or CIPT and possesses demonstrated experience in data privacy domain.
Conclusion
The evolution of privacy regulations around the globe and cutting-edge privacy-enhancing technologies calls for continuous learning. This is especially true with the rise of AI and Machine Learning in data privacy, presenting exciting opportunities, threats, and challenges. Recognizing the intertwined nature of cybersecurity and data privacy, professionals in both fields can benefit from expanding their horizons. Cybersecurity experts can leverage their technical expertise to excel in privacy engineering, while privacy professionals can gain strategic insights from security best practices. Even legal professionals, navigating the legal landscape of this dynamic domain, will find foundational knowledge of cybersecurity and privacy-enhancing technologies increasingly valuable.
If you are aspiring to be a data privacy professional, wish you happy learning in 2024 with these certifications.
如有侵权请联系:admin#unsafe.sh