2024-1-4 20:53:50 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Resecurity, a provider of cybersecurity services, this week identified a GXC Team cybercriminal syndicate that has developed a tool that makes use of artificial intelligence to generate invoices that are then embedded within a business email compromise (BEC) attack.
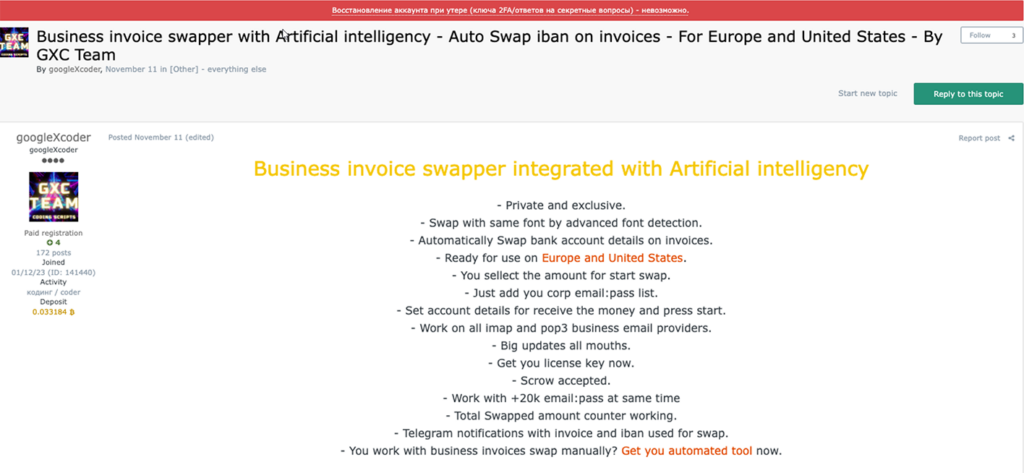
The Business Invoice Swapper tool being made available by GXC Team uses proprietary algorithms to scan compromised emails through POP3/IMAP4 protocols, identifying messages that either mention invoices or include attachments with payment details. Upon detection, the tool alters the banking information of the intended recipient with information automatically generated by the perpetrator. The altered invoice is then either replaced in the original message or sent to a predetermined list of contacts.
The interface for Business Invoice Swapper also includes options to configure simple mail transfer protocol (SMTP) settings for sending out emails with the fabricated invoices it generates. The tool also includes a feature that sends reports to a designated Telegram channel to provide command-and-control (C2C) communication. This functionality also extends to providing details about the generated invoices.
For the tool to function, the operator must input a list of compromised email accounts to be scanned. This process involves specifying the credentials, as well as the IBAN and BIC codes that will be used for the ‘swapping’ or spoofing process in the documents. Thus far, the tool is designed to specifically target more than 300 entities, with attacks thus far primarily located in the United Kingdom, Spain, France, Poland, Italy, Germany and Switzerland.
Cybercriminals can either subscribe to use the tool starting at $2,000 per week or, alternatively, pay a one-time fee of $15,000 for unlimited access.
Resecurity CEO Gene Yoo said the level of sophistication enabled by Business Invoice Swapper would require organizations to apply significantly higher levels of vigilance when processing invoices. Today, there is often a tendency within organizations to pay automatically and issue payments without always checking invoice details, he noted.
Many fake invoices will be accompanied by messages conveying a sense of urgency, so organizations should make sure they review any payments being made outside of any normal workflow, added Yoo. One of the issues that organizations need to come to terms with is that it has become much simpler to wire funds using various online services, any one of which might be used by cybercriminals to facilitate a payment, said Yoo.
Hopefully, AI tools will enable organizations to identify fake invoices, but as tactics and techniques evolve, an AI-based system is going to need to be continuously updated with fresh data to identify attacks, so there will always be a need for humans to review payments, he added.
It’s not clear to what degree AI in the hands of cybercriminals might require organizations to completely revamp invoice processing workflows, but it’s all but certain the amount of fraud being perpetrated is about to exponentially increase. The challenge now is making sure there are enough humans aided by machines in place to thwart attacks that could easily lead to organizations collectively losing billions of dollars that will never be recovered.
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
