This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Hackers associated with the Turkish government are conducting new cyber-espionage operations across Europe and the Middle East, according to recent reports from PwC, StrikeReady, and Hunt & Hackett.
Tracked as Sea Turtle (Teal Kurma, Silicon, UNC1326, Cosmic Wolf), the group rose to fame between 2018 and 2020 when it conducted a series of DNS hijacking campaigns that intercepted traffic for Cypriot, Greek, and Iraqi government systems.
Ever since its public ousting in late 2020, the group wound down its DNS hijacking infrastructure, and very little activity has been linked to its operations.
In recent reports, the three security firms claim the group has now re-tooled and changed its modus operandi, although some connections to its old infrastructure remained.
Sea Turtle has now been linked to the SnappyTCP backdoor, a simplistic reverse shell designed for Linux and Unix systems, which the group has been using in recent operations.
These new attacks targeted governments, telecommunication, and IT service providers. All three reports conclude the attacks were classic cyber-espionage operations—aimed at collecting information that can further Turkey's economic or political interests.
On top of that, Sea Turtle has also been seen running websites mimicking the sites of Turkish news outlets and bloggers, Kurdish news sites, and NGOs and TV channels in the Arab world.
Aside from victims in the Netherlands, none of the three reports mention the exact location of the group's recent operations.
According to Hunt & Hackett, initial access occurred via compromised cPanel accounts, from where the group pivoted to the victim's other infrastructure via SSH.
The group then planted the SnappyTCP backdoor for future access, which they leveraged to collect data from victim environments, such as email archives.
The StrikeReady report also mentions a cluster of Windows malware artifacts with a "software update" theme.
The three reports highlight a noticeable shift in the group's operations, moving away from DNS hijacking to a classic compromise-and-collect approach. Hunt & Hackett specifically warns telcos, ISPs, and managed service providers to secure their infrastructure, as the group has been seen going after similar organizations in attempts to pivot to accounts operated by their primary targets.
Russia hacked UA webcams: Russian hackers have hijacked at least two security cameras and used their live video feeds to adjust missile strikes targeting the city of Kyiv at the start of the year. Ukraine's Security Service SBU says it detected the hacks and took down the cameras in order to prevent further abuse. The agency says that since the start of Russia's invasion, it has taken down more than 10,000 security cameras across Ukraine.
Kyivstar cyberattack: Russian hackers breached and stayed hidden inside the network of Ukrainian telco Kyivstar network for at least seven months. The hackers breached the telco in May before being discovered and ousted in early December of 2023. According to Illia Vitiuk, the head of Ukraine's SBU intelligence agency, the hack was carried out by Sandworm, a hacking unit inside Russia's military intelligence agency GRU. The group allegedly wiped thousands of the telco's internal systems. Vitiuk says the hack had a significant impact on the civilian population but no impact on military operations. [Additional coverage in Reuters]
Gallery Systems cyberattack: Several US museums are unable to display their art collections online after hackers hit Gallery Systems, a shared provider of IT infrastructure. [Additional coverage in ARTNews]
Xerox hack: Xerox has confirmed that hackers breached its US subsidiary as part of a ransomware attack.
Orange Spain incident: Mobile operator Orange Spain has had its entire internet traffic sent into a black hole after an unidentified individual logged into the company's RIPE account and changed BGP routes randomly. Fun, fun, fun!
23andMe drama: 23andMe is trying to blame its users for its recent data breach by claiming they are at fault for using weak passwords. The new drama comes after the company was sued more than 30 times for a recent security breach and after the company sneakily modified its terms of service to force people into arbitration. [Additional coverage in TechCrunch]
Beirut airport hack: A hacktivist group defaced the public screens at the Beirut international airport in Lebanon with anti-Iran and anti-Hezbollah messages. A group calling itself "Lord and the People" took credit for the incident. [Additional coverage in ArabNews]
CoinsPaid hacked again: Estonian cryptocurrency platform CoinsPaid fell victim to a cyberattack and lost an estimated $7.5 million worth of crypto assets. This is the company's second hack after it lost $37.3 million in July 2023. CoinsPaid blamed last year's incident on North Korean hackers. [Additional coverage in CryptoNews]
Gamma crypto-heist: The Gamma cryptocurrency platform says it lost $6.1 million worth of assets after a threat actor abused the infrastructure of one of its providers and manipulated exchange prices.
Radiant Capital cyber-heist: A threat actor has stolen almost $4.5 million worth of crypto-assets from crypto-platform Radiant Capital. The incident is suspected to have been a flash loan attack. [Additional coverage in Coinpedia]
Mandiant Twitter scam: A threat actor hijacked the Twitter account of Google's Mandiant division and promoted a cryptocurrency scam. It was one of many incidents that hit high-profile Twitter gold badge accounts over the past week. The hacks appear to be linked to a new underground market where hacked Twitter business accounts are being offered for sale. [Additional coverage in ArsTechnica]
Merck settles NotPetya lawsuit: American pharmaceutical company Merck has settled a lawsuit with three insurers in relation to the NotPetya cyberattacks. The parties settled the lawsuit a day before oral arguments were meant to be heard in front of the New Jersey Supreme Court. The company sought $1.4 billion in damages from its insurers following the 2017 NotPetya cyberattack. A New Jersey appeals court ruled the company was entitled to $700 million in claims before the insurers moved the case to the state's Supreme Court. The terms of the settlement have not been disclosed. [Additional coverage in Insurance Journal and Bloomberg]
Facebook creepy tracking: Meta has enabled a new feature named Link History for all Facebook users that will keep track of their visited links and use the data to show ads. The feature was forcibly enabled by default for all users, and you can only disable it through an option hidden deep in the app's settings. [Additional coverage in SearchEngineLand]
LastPass master password changes: Password management service LastPass is forcing customers to choose stronger and longer 12-character-long master passwords. The company is enforcing the new rule more than a year after it suffered a security breach in November 2022. In September 2023, security experts found that hackers cracked some of the weaker master passwords and stole more than $35 million worth of cryptocurrency from LastPass customers.
AWS security best practices: The AWS team has published a guide covering best practices for configuring AWS security services. This is a guide for how to configure AWS security tools, not how to secure AWS infrastructure.
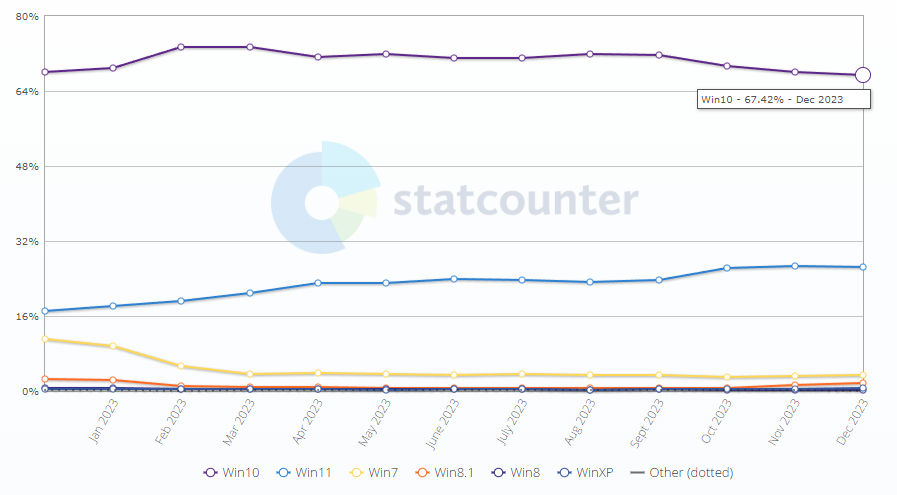
Windows market share: Windows 10 has remained around the 67% figure last year, while Windows 11 has grown from 16% to 26%, according to StatCounter.
More FBI cyber agents abroad: The FBI has increased the number of cyber assistant legal attachés deployed at embassies across the globe. New legal attachés positions have been established in New Delhi, Rome, and Brasilia. The FBI began deploying cyber legal attachés in 2011 and is currently employing 63 cyber legal attachés in Australia, the Netherlands, Estonia, Romania, Ukraine, and Canada. The agents' main role is to work with local law enforcement to investigate and disrupt cybercrime operations. [Additional coverage in CyberScoop]
New CNMF chief: Marine Corps Maj. Gen. Lorna Mahlock has assumed the leadership of the Cyber National Mission Force, a cyber investigations unit inside US Cyber Command. Maj. Gen. Mahlock replaces Army Maj. Gen. William Hartman, who was named Cyber Command's new deputy chief. [Additional coverage in The Record]
Greece to set up cybersecurity agency: The Greek government has published a draft law that will establish a National Cybersecurity Authority, a new agency aimed at bolstering the country's cyber defenses. [Additional coverage in BalkanInsight]
In this Risky Business News sponsor interview Tom Uren talks to Chris St Myers, Stairwell’s head of threat research, about managing the risk from software you absolutely must use.
Pompompurin breaks parole: The FBI has re-arrested a hacker known as Pompompurin after the 21-year-old broke his parole conditions. Officials say Conor Brian Fitzpatrick connected to the internet via a VPN from a computer without monitoring software installed. The 21-year-old was initially arrested in March 2023 for running BreachForums, a cybercrime forum where hacked data was leaked and traded. Fitzpatrick pleaded guilty to hacking and child pornography charges and was released on parole in July last year. His sentencing is scheduled for January 19, later this month. [Additional coverage in The Record]
xDedic fallout: The US Justice Department says that five years after shutting down the xDedic cybercrime marketplace, it has now identified and charged 19 individuals active on the site. Officials say they have now identified and handed down sentences to the site's main operators, two individuals from Moldova and Ukraine. Sentences have also been handed down to xDedic sellers and buyers, individuals who sold and bought hacked servers off the site. Many of these individuals were also charged with other crimes related to the exploitation of xDedic's inventory, with some sentences reaching 78 months in prison.
BEC scammer detained: US officials have indicted a Nigerian national on charges of allegedly stealing more than $7.5 million through BEC scams. Olusegun Samson Adejorin was arrested in Ghana on December 29 and is awaiting his extradition to the US. Two of Adejorin's victims are charitable organizations.
Follow-on extortion campaigns: Security firm ArcticWolf reports that multiple victims that got hit by the Akira and Royal ransomware groups last year have been contacted by other criminal groups with new extortion threats. These second groups attempted to extort victims with threats to publish their older stolen data or they offered to hack into the first ransomware gang's servers and delete the stolen data for a fee. These groups used names like the Ethical Side Group (ESG) or xanonymoux.
OpJapan: South Korean security firm S2W Talon has published a report looking at a hacktivism campaign tracked as #OpJapan, where various hacktivist groups targeted Japanese organizations after the country released treated water from the Fukushima nuclear plant back into the ocean.
New npm malware: Twenty-four malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
PyPI malware: Fortinet researchers have spotted three malicious Python libraries on the official PyPI portal that were designed to deploy cryptocurrency miners on Linux systems.
Terrapin exposure: More than 11 million internet-connected devices are vulnerable to a new SSH attack known as Terrapin (CVE-2023-48795). According to a scan performed by the Shadowserver Foundation, nearly half of all systems with an exposed SSH port over IPv4 are vulnerable.
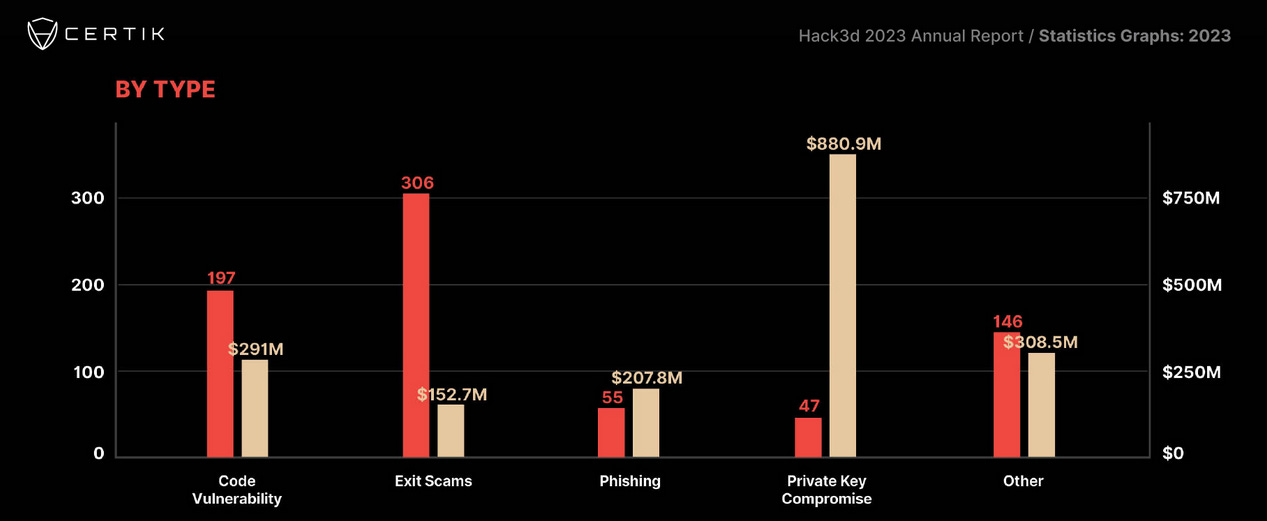
2023 crypto-hacks: Hackers have stolen more than $1.8 billion worth of crypto assets across 751 security incidents in 2023. The number is 51% down from the $3.7 billion lost a year before, in 2022. According to blockchain security firm CertiK, the top 10 most costly incidents accounted for more than $1.1 billion lost last year. The most costly incidents were linked to leaks or compromises of private keys, with more than $880 million stolen this way last year. Fairyproof has the 2023 crypto-heist stats at $1.23 billion across 489 incidents. According to TRM Labs, North Korean hackers were linked to $600 million stolen assets.
Mirai.TBOT: QiAnXin researchers have discovered a new Mirai-based botnet. Named Mirai.TBOT, the botnet has been active since August, infected more than 30,000 systems, and is mainly used for DDoS attacks. This is the same botnet that Akamai tracks as InfectedSlurs.
SilverRAT: CyFirma has published a report on SilverRAT, a new remote access trojan that launched in November of last year. According to researchers, the malware was created by a Syrian national going by the name of "Anonymous Arabic," who previously also created the S500 RAT. SilverRAT has a new feature meant to destroy system restore points, a feature that's unique among RATs sold online.
AsyncRAT: AlienLabs looks at some recent AsyncRAT samples the company has spotted in the wild over the past 11 months.
LockBit: Chinese security firm Xitan has published a report on the LockBit ransomware.
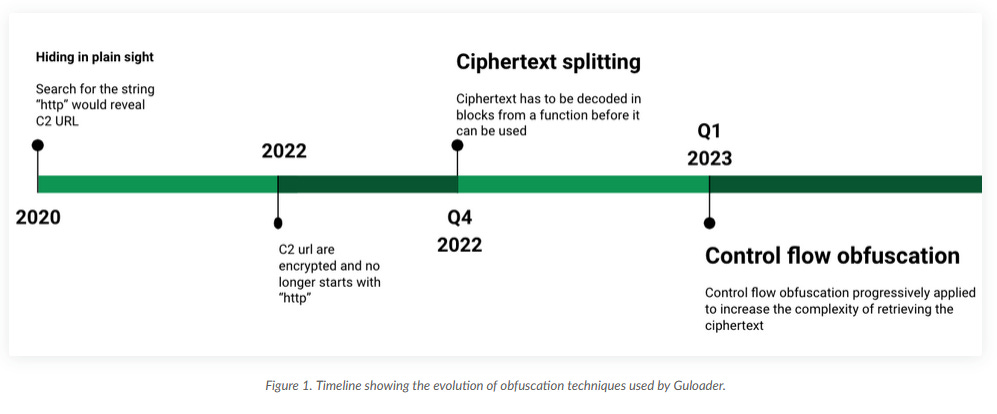
Anti-analysis techniques: Palo Alto Networks looks at the recent anti-analysis techniques used by malware strains such as GuLoader and RedLine Stealer.
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
Hafnium's persistence method: Researchers at Purple Team have looked at how Hafnium is modifying scheduled tasks on infected hosts to maintain persistence.
Bluenoroff's SpectralBlur: macOS malware researcher Patrick Wardle has published an analysis of SpectralBlur, a macOS backdoor linked to DPRK's Bluenoroff's cyber-espionage group.
UAC-0050: Uptycs looks at recent UAC-0050 spear-phishing campaigns pushing the RemcosRAT, also seen by Ukraine's CERT team.
SideWinder: Bridewell has published a report with details on new SideWinder infrastructure. SideWinder APT, also known as Rattlesnake, is one of the oldest nation-state threat actors that is believed to originate from India.
Patchwork: Chinese security firm looks at recent Patchwork APT operations targeting China's energy sector.
No-Justice wiper: ClearSky has published a technical breakdown of No-Justice, the data wiper used by Iranian hacking group Homeland Justice in a recent attack targeting the Albanian Parliament and other local companies. The attack took place on December 24 last year. Homeland Justice is the same group that hacked and crippled the Albanian government in the summer of 2022.
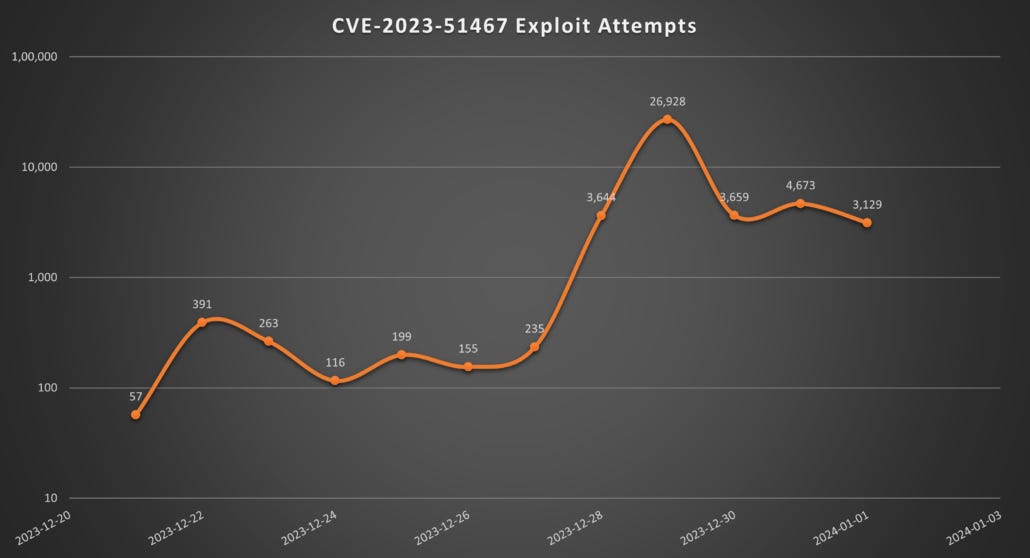
OFBiz exploitation: Threat actors are exploiting a recently disclosed vulnerability in OFBiz, an ERP solution from the Apache Foundation. The attacks began a week after SonicWall security researchers disclosed the bug in a blog post and after Apache patched the issue. Tracked as CVE-2023-51467, the vulnerability is an authentication bypass that can lead to SSRF and RCE attacks. Some parts of the OFBiz project are used in Atlassian products, but the company said its software is not affected.
Bitwarden vulnerability: Password management application Bitwarden has fixed a major vulnerability that could have allowed threat actors to remotely steal a user's password vault without knowing the password or requiring biometric authentication.
Ivanti EPM security update: Ivanti (formerly MobileIron) has published a security update for its Endpoint Manager (EPM) server. Tracked as CVE-2023-39336, this is an SQL injection vulnerability rated as critical (9.6/10).
QNAP security updates: Taiwanese company QNAP has released security updates to fix 12 vulnerabilities across several products.
OpenOffice security updates: The Apache Foundation has released a security update for the OpenOffice software suite that fixes four vulnerabilities.
PHP library vulnerability: CERT-PL has found a vulnerability (CVE-2023-6551) in a popular PHP library used to handle image uploads.
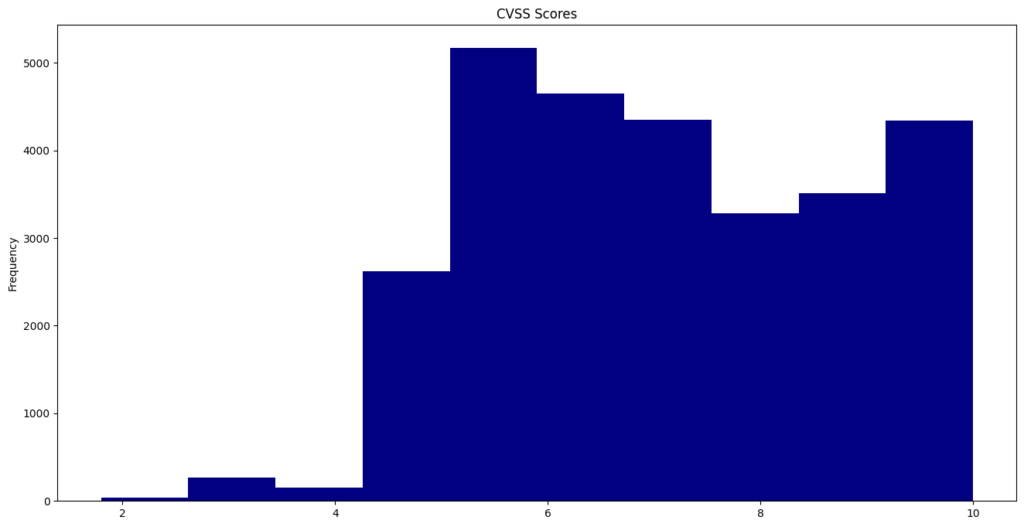
2023 vulnerabilities: Cisco's Jerry Gamblin has published a statistical overview of 2023's CVEs. In total, there were 28,902 published CVEs, up 15% from 2022. Thirty-six CVEs scored a "perfect" 10.0. Less than 1% were routinely exploited in the wild, according to the Qualys 2023 Threat Landscape report.
Acquisition news #1: Airbus is in talks to buy Atos, a prominent EU cybersecurity startup.
Acquisition news #2: SentinelOne announced its intention to acquire cloud-native application protection platform PingSafe.
Acquisition news #3: SonicWall has acquired Banyan Security, a provider of security solutions for edge networking devices.
Acquisition news #4: Mimecast has acquired Elevate Security, an email security company specializing in human behaviors and risk.
New tool—SSH-Snake: Security researcher Joshua Rogers has open-sourced SSH-Snake, a tool designed to perform automatic network traversal using SSH private keys discovered on systems. Rogers says the tool's main objective is to create a comprehensive map of a network and its dependencies to identify the extent to which a network can be compromised using SSH and SSH private keys starting from a particular system.
New tool—Galah: Niantic Labs security engineer Adel Ka has released Galah, a web honeypot tool powered by OpenAI.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about recent hints that the Ukrainian government has figured out how to make use of the IT Army.