
2024-1-10 01:0:0 Author: securityboulevard.com(查看原文) 阅读量:12 收藏
In 2023, the industry experienced a significant uptick in attacks against network devices such as VPNs, firewalls, load balancers, switches, and routers. This prompted us to document the history of attacks against network devices. The infographic below (click here to open it in a new tab for easier viewing) is not exhaustive, but provides a visual depiction of how these attacks have grown in sophistication and scale.
In the timeline, note the rapid increase of attacks against network infrastructure by ransomware gangs which took off in 2020. Network devices have become a favorite initial access vector for ransomware operators because they exist in highly privileged parts of an organization and lack security tooling like EDR, while providing ample opportunity for lateral movement within the internal network and the ability to covertly route command and control traffic.
Insecure network infrastructure is causing lots of trouble
Fundamentally, the security of network infrastructure is subpar. Insecure software and inadequate vendor responses have left IT organizations scrambling to patch a seemingly endless stream of vulnerabilities. Because the patch process can affect production traffic, remediation often lags weeks or months behind the normal patching cadence seen with desktop and server operating systems. For example, in June 2023, a 9.8 CVSS remote code execution bug was patched in Fortinet devices; three weeks later, 330K devices were still vulnerable.
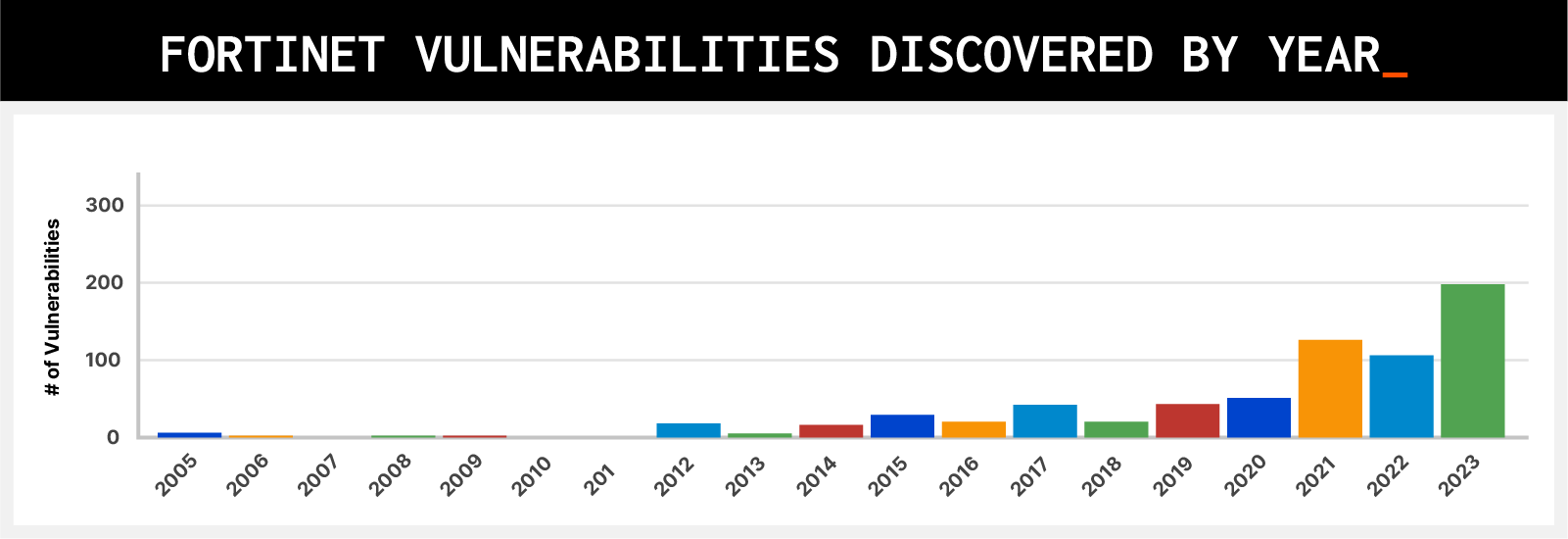
Fortinet serves as a case in point. Querying the NIST NVD database, we can see the number of vulnerabilities in Fortinet devices alone has gone up significantly in the past few years. As of this writing, there were a record 185 vulnerabilities discovered in 2023 (compared with 106 in 2022, 126 in 2021, and 51 in 2020, see chart below). Other network device vendors have seen similar increases in discovered vulnerabilities.
To lessen their exposure to these product vulnerabilities, organizations need to start incorporating product security evaluations into their vendor risk assessment processes. Similar to how the National Highway Traffic Safety Administration provides crash test ratings for passenger vehicles, Eclypsium provides third-party insight into the safety of IT products such as network devices. In addition, Eclypsium adds layered defenses to these devices in production, helping with vulnerability management and detection of compromise.
Additional resources
Product tour: Eclypsium Guide to Supply Chain Security
White paper: Network Infrastructure on the Front Line
Webinar: Network Infrastructure in Ransomware’s Crosshairs
Blog: A New Approach to Defending Network Infrastructure


2005

Independent security researcher Mike Lynn demonstrates the first-ever Cisco IOS rootkit at the Black Hat conference. [1][2]
2008
The FBI concludes Operation Cisco Raider, a two-year initiative to disrupt a Cisco distribution network that had sold counterfeit Cisco gear to the U.S. military and other organizations. [3]
2015
SYNful Knock malware targets Cisco IOS devices, installing an implant that provides persistent access that is difficult to detect. [4] Nation-state
Cisco warns customers about attacks that swap ROMMON remote management firmware with maliciously altered images. [5]

Juniper discloses a supply chain attack where two backdoors were implanted in its NetScreen VPN products. Researchers attribute the backdoors to the NSA. [6] Nation-state
2017

Wikileaks’ Vault 7 leak exposes tools used by the CIA and leads to the discovery of CVE-2017-3881 affecting 300+ Cisco routers and switches. [7] Nation-state
2018

The VPNFilter campaign infects 500K+ devices worldwide from Linksys, MikroTik, Netgear, and TP-Link. The malware has data collection and destructive capabilities, and is attributed to the Russian Sandworm threat group. [8] Nation-state
Five backdoors discovered in Cisco products raise worries about a supply chain attack. One of the backdoors is an undocumented user account with privilege level 15 that has a default username and password in Cisco IOS. [9]
2019
CVE-2018-13379 is discovered in the FortiOS SSL VPN web portal. This vulnerability is subsequently listed among CISA’s Top 12 Routinely Exploited Vulnerabilities in 2020, 2021, and 2022, underscoring the difficulty in patching network appliances. [10]
Echobot, a variant of the Mirai botnet malware, targets SCADA systems and enterprise networking gear, including Barracuda and Citrix appliances. [11]
2020

Security researchers detail a campaign targeting Citrix ADCs as entry points to disable Windows Defender and install Ragnarok ransomware on Windows machines in the network. [12] Ransomware

Criminals launch a wide-scale campaign targeting Pulse Secure VPN appliances to steal Active Directory credentials, disable endpoint security, and install REvil ransomware. [13] Ransomware
Security researchers detail the techniques of the Iranian-backed Fox Kitten campaign, whose primary method of initial access is VPN devices from Citrix, Fortinet, Palo Alto Networks, and Pulse Secure. [14] Nation-state

COVID-19 restrictions in March put a focus on the security and availability of VPN infrastructure as employees connect remotely. [15]

Sophos alerts customers to a zero-day exploit against its XG firewalls that deploys the Asnarök data-stealing trojan and then attempts to install Ragnarok ransomware. The attacks are foiled by a hotfix from the vendor. [16] Ransomware
F5 discloses its first-ever vulnerability with a CVSS of 10.0. Public exploits are available within a week and the vulnerability is widely exploited. [17]

The FBI releases IOCs for widespread Netwalker ransomware attacks that target vulnerable Pulse Secure VPN devices for initial access. [18] Ransomware
CISA issues a cybersecurity advisory to help U.S. government agencies defend against Chinese state-sponsored attack activity, which includes exploiting recent vulnerabilities in F5 BIG-IP, Citrix VPN, and Pulse Secure VPN appliances. [19] Nation-state
2021

Kaspersky details techniques used by attackers to install Cring ransomware in enterprise victims. Initial access focused on vulnerable FortiGate VPN appliances. [20] Ransomware
Multiple campaigns target vulnerabilities in Pulse Secure VPN appliances, including a zero-day (CVE-2021-22893). Mandiant tracks 12 separate malware families targeting Pulse Secure devices and also says Chinese state-sponsored groups exploit these vulnerabilities for espionage. [21][22] Nation-state

F5 publishes a security advisory containing 21 CVEs, including four critical vulnerabilities. CVE-2021-22986 is later observed as an initial access vector for Lockbit 3.0. [23] Ransomware

Dozens of critical vulnerabilities involving SQL injection, buffer overflow, out-of-bound read, etc. are discovered in SonicWall devices. Mandiant notes the ransomware group UNC2447 uses some of these exploits for initial access and persistence. [24][25] Ransomware

Hackers publish a list of credentials stolen from 87K Fortinet devices on a ransomware forum. The credentials were harvested using a vulnerability from 2018. [26] Ransomware
2022
Cyclops Blink malware targets Watchguard firewalls and ASUS routers, and is attributed to the Russian Sandworm threat group. In a court-authorized operation, the FBI disabled the botnet by removing the malware and closing external management ports on infected devices used for C2. [27] Nation-state

CVE-2022-1388 affects F5 BIG-IP devices and is listed among CISA Top 12 Routinely Exploited Vulnerabilities for 2022. [28]
The NSA releases threat hunting guidance for Citrix ADC devices targeted by APT5 as part of its espionage activities. Recommendations include checking hashes of important binaries, monitoring logs, and running YARA rules to look for specific malware used. [29] Nation-state
A critical zero-day vulnerability (CVE-2022-42475) is discovered in FortiGate firewalls during an incident investigation by the vendor. [30]
2023
March
Another Fortinet zero-day is discovered (CVE-2022-41328) being exploited by Chinese hackers (UNC3886), who use the appliances as a pivot to ESXi infrastructure and then to VM guests. [31] Nation-state
April

The U.K. National Cyber Security Centre releases a report warning of Jaguar Tooth malware targeting Cisco IOS. Nation-state
May
Security researchers observe widespread exploitation of CVE-2023-28771 in Zyxel devices to build a Mirai-based botnet. [32] Nation-state

22 Danish energy firms are compromised in a campaign that exploited CVE-2023-28771 as well as two new zero-day vulnerabilities in Zyxel devices (CVE-2023-33009 and CVE-2023-33010). The attacks were attributed to the Russian Sandworm group. [33] Nation-state

Microsoft publishes details of its investigation into the Chinese Volt Typhoon group targeting U.S. critical infrastructure. The attackers use an unknown Fortinet exploit and use routers from ASUS, Cisco, D-Link, NETGEAR, and Zyxel as proxies for C2 traffic. [34] Nation-state
In response to an ongoing campaign utilizing a zero-day vulnerability (CVE-2023-2868) against Barracuda appliances, the vendor recommends that customers return their appliances for new ones. [35] Nation-state
June

CISA directs federal agencies to either implement zero-trust for network management interfaces or remove them from the internet. [36]
July

CVE-2023-3519 is discovered as a zero-day in Citrix Netscalers and mass exploitation commences within weeks, compromising 30K+ devices. The campaign is attributed to the ransomware actor FIN8. [37] Ransomware
August

Rapid7 responds to a number of incidents involving Cisco ASA SSL VPNs, some involving ransomware gangs Akira and Lockbit. Less than two weeks later, Cisco discloses CVE-2023-20269 which is related. Ransomware
September
The NSA and the Japanese government issue a warning about the Chinese group BlackTech targeting “various brands and versions” of routers to install implants for espionage. [38] Nation-state
October
Cisco discovers a campaign exploiting two zero-day vulnerabilities (CVE-2023-20198 and CVE-2023-20273) to create admin accounts and install implants on Cisco IOS XE devices. Before a patch is available, at least 10K devices are infected. [39]

A zero-day vulnerability (CVE-2023-4966) dubbed Citrix Bleed is discovered. Mandiant reports threat activity since August, allowing attackers to hijack authenticated sessions. [40] Lockbit and ALPHV/BlackCat use Citrix Bleed to compromise numerous organizations, including Boeing, ICBC, Toyota Financial Services, DP World, and Fidelity National Financial. Ransomware

- The Holy Grail: Cisco IOS Shellcode And Exploitation Techniques, Michael Lynn, July 2008
- An Insider’s View of ‘Cisco-gate’, WIRED, August 2005
- FBI probe discovers counterfeit kit in US military networks, The Register, May 2008
- SYNful Knock
- Attackers are hijacking critical networking gear from Cisco, company warns, Ars Technica, August 2015
- Researchers Solve Juniper Backdoor Mystery; Signs Point to NSA, WIRED, December 2015
- The Wikileaks Vault 7 Leak – What We Know So Far, Cisco Blogs, March 2017
- VPNFilter
- Backdoors Keep Appearing In Cisco’s Routers, Tom’s Hardware, July 2018
- 2022 Top Routinely Exploited Vulnerabilities, CISA, August 2023
- Echobot Malware Now up to 71 Exploits, Targeting SCADA, F5 Labs, December 2019
- Ragnarok Ransomware Targets Citrix ADC, Disables Windows Defender, Bleeping Computer, January 2020
- VPN warning: REvil ransomware targets unpatched Pulse Secure VPN servers, ZDNet, January 2020
- Fox Kitten Campaign Widespread Iranian Espionage-Offensive Campaign, Clearsky Cybersecurity, February 2020
- Cybersecurity Advisory: Enterprise VPN Security, CISA, April 2020
- Hackers tried to use Sophos Firewall zero-day to deploy Ransomware, Bleeping Computer, May 2020
- Threat Actor Exploitation of F5 BIG-IP CVE-2020-5902, CISA, July 2020
- FBI Flash: Indicators Associated with Netwalker Ransomware, FBI, July 2020
- Chinese Ministry of State Security-Affiliated Cyber Threat Actor Activity, CISA, December 2020
- Vulnerability in FortiGate VPN servers is exploited in Cring ransomware attacks, Kaspersky, April 2021
- Check Your Pulse: Suspected APT Actors Leverage Authentication Bypass Techniques and Pulse Secure Zero-Day, Mandiant, April 2021
- Re-Checking Your Pulse: Updates on Chinese APT Actors Compromising Pulse Secure VPN Devices, Mandiant, May 2021
- LockBit: Access, Encryption, Exfiltration, & Mitigation, November 2023
- UNC2447 SOMBRAT and FIVEHANDS Ransomware: A Sophisticated Financial Threat, Mandiant, April 2021
- SonicWall Zero-Day Exploited by Ransomware Group Before It Was Patched, SecurityWeek, April 2021
- Fortinet warns customers after hackers leak passwords for 87,000 VPNs, The Record, September 2021
- Justice Department Announces Court-Authorized Disruption of Botnet Controlled by the Russian Federation’s Main Intelligence Directorate (GRU), U.S. Department of Justice, April 2022.
- 2022 Top Routinely Exploited Vulnerabilities, CISA, August 2023
- APT5: Citrix ADC Threat Hunting Guidance, NSA, December 2022
- We’re Out of Titles for VPN Vulns—It’s Not Funny Anymore, WatchTowr, January 2023
- Fortinet Zero-Day and Custom Malware Used by Suspected Chinese Actor in Espionage Operation, Mandiant, March 2023
- Hackers exploit critical Zyxel firewall flaw in ongoing attacks, BleepingComputer, May 2023
- Russian Hackers Linked to ‘Largest Ever Cyber Attack’ on Danish Critical Infrastructure, The Hacker News, November 2023
- Volt Typhoon targets US critical infrastructure with living-off-the-land techniques, Microsoft, May 2023
- Barracuda ESG Zero-Day Vulnerability (CVE-2023-2868) Exploited Globally by Aggressive and Skilled Actor, Suspected Links to China, Mandiant, June 2023
- BOD 23-02: Mitigating the Risk from Internet-Exposed Management Interfaces, CISA, June 2023
- Attacks on Citrix NetScaler systems linked to ransomware actor, BleepingComputer, July 2023
- People’s Republic of China-Linked Cyber Actors Hide in Router Firmware, NSA, September 2023
- “Cisco buried the lede.” >10,000 network devices backdoored through unpatched 0-day, ArsTechnica, October 2023
- Remediation for Citrix NetScaler ADC and Gateway Vulnerability (CVE-2023-4966), Mandiant, October 2023
The post Infographic: A History of Network Device Threats and What Lies Ahead appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
*** This is a Security Bloggers Network syndicated blog from Eclypsium | Supply Chain Security for the Modern Enterprise authored by Chris Garland. Read the original post at: https://eclypsium.com/blog/infographic-a-history-of-network-device-threats-and-what-lies-ahead/
如有侵权请联系:admin#unsafe.sh