Our honeypots saw a number of scans for "/j_acegi_security_check" the last two days. This URL has not been hit much lately, but was hit pretty hard last March. The URL is associated with Jenkins, and can be used to brute force passwords.
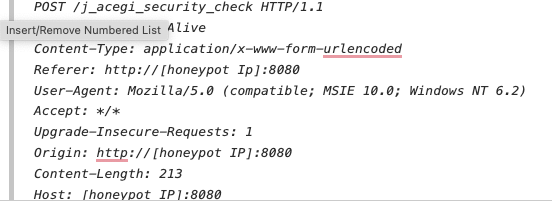
A typical request seen by our honeypots:
POST /j_acegi_security_check HTTP/1.1
Connection: Keep-Alive
Content-Type: application/x-www-form-urlencoded
Referer: http://[honeypot Ip]:8080
User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2)
Accept: */*
Upgrade-Insecure-Requests: 1
Origin: http://[honeypot IP]:8080
Content-Length: 213
Host: [honeypot IP]:8080j_username=112233&j_password=&from=%2F%2Fscript&json=%7B%22j_username%22%3A+%22112233%22%2C+%22j_password%22%3A+%22%22%2C+%22remember_me%22%3A+false%2C+%22from%22%3A+%22%2F%2Fscript%22%7D&Submit=%E7%99%BB%E5%BD%95
The body of the request URL decodes to
j_username=112233&j_password=&from=//script&json={"j_username": "112233", "j_password": "", "remember_me": false, "from": "//script"}&Submit=[Chinese Characters]
The Chinese characters at the end translate to "Log in," indicating that this request may have been originally based on a Chinese language version of Jenkins. I have observed usernames like admin, 1, 123, adminadmin, root. The intent of this particular query may be to test if the server is running Jenkins and not an actual brute-force attempt. But it is always difficult to guess a particular attack's intent. The honeypot is not attempting to emulate Jenkins at this point (something we may need to add to our agile honeypots soon).
One IP is particularly active in exploring this URL: 118.239.30.233. This IP showed up in our data first two days ago and is so far exclusively checking this one URL and "/," indicating more of a recon focus. As far as I can tell, the IP is located in China but has no specific history.
As said before, Do not offer Jenkins to the public.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
如有侵权请联系:admin#unsafe.sh