2024-1-10 04:37:13 Author: www.malwarebytes.com(查看原文) 阅读量:19 收藏
Ransomware groups are liars, yes, but even when these dangerous cybercriminals would ransack organizations and destroy entire companies, a few select groups espoused a sort of “honor among thieves.” According to those few groups, their cybercriminal actions would never include organizations actively involved in healthcare, such as hospitals.
But, as can be expected from ransomware groups, these were nothing but lies. The million-dollar criminal operations, awash with cash, are still vulnerable to greed.
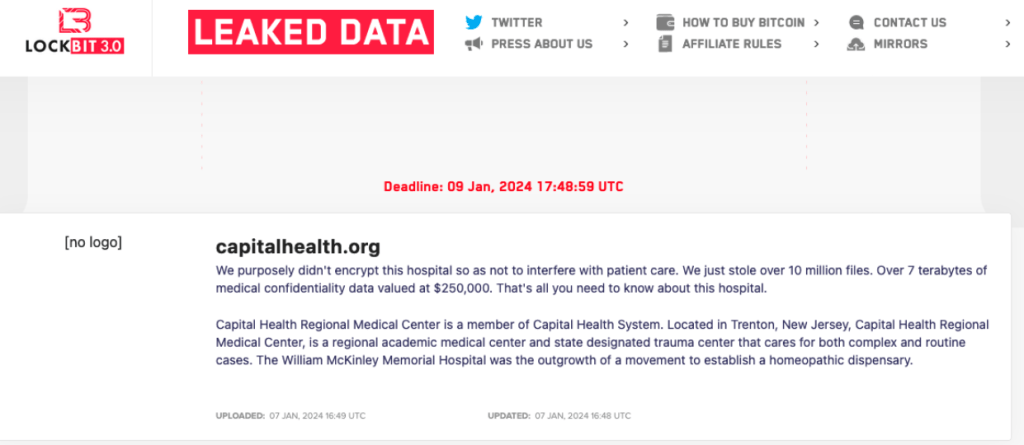
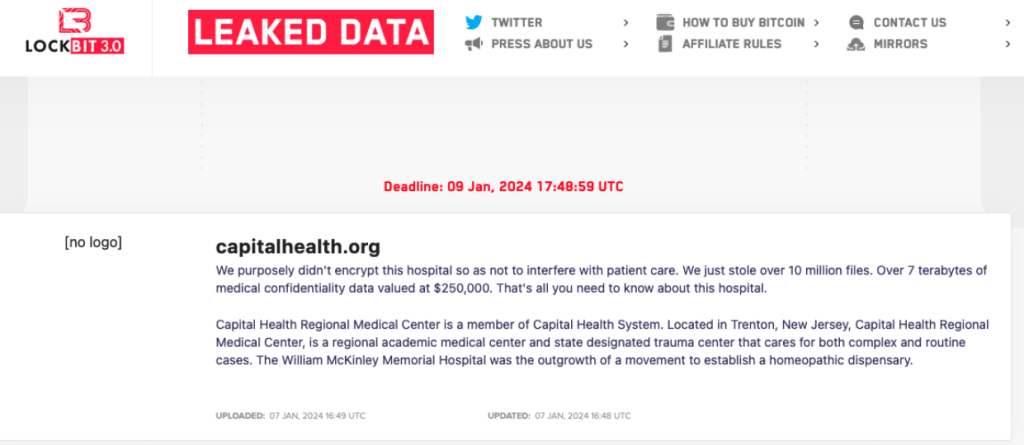
LockBit has claimed the recent attack on Capital Health. And even though LockBit claims they did not encrypt the hospitals files, the hospitals and physicians’ offices experienced IT outages that forced them to resort to emergency protocols designed for system outages. Several surgeries were moved to later dates and outpatient radiology appointments were canceled.


Unfortunately, we have seen these type of disruptions in healthcare before. And despite promises, we expect to see them again.
But in an even more brutal turn of events, a ransomware group is crossing another line, and resorted to threatening physical violence against patients. As fewer organizations are willing to pay the ransom, it seems the ransomware operators have lost all human decency (admittedly, it’s hard to believe they ever had any).
Again, we have seen ransomware groups turn on people who had their data stolen before. It’s an extra type of leverage to get the target organization to pay the ransom. Integris Health for example, an organization which operates a network of 15 hospitals and 43 clinics, reported that some of their patients received emails threatening to sell their information on the dark web.
But in the case of Seattle’s Fred Hutchinson Cancer Center, the criminals have taken it even a few steps further and threatened to “swat” hospital patients.
Swatting is where someone makes a hoax emergency call to law enforcement in order to get armed police (in reference to US “Special Weapons And Tactics” teams) to target a particular address. Over time, swatting has evolved from a dangerous type of prank to a cybercrime that can be ordered as a service.
Swatting is dangerous because of the potential consequences. Not only does it take emergency services away from their actual tasks, but there have been swatting incidents that had fatal consequences.
Once the Fred Hutchinson Cancer Center became aware of the cybercriminals’ swatting threats, they immediately notified the FBI and Seattle police. Let’s hope this reduces the potential dangers involved in swatting.
Data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened, and follow any specific advice they offer.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the vendor website to see if they are contacting victims, and verify any contacts using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Set up identity monitoring. Identity monitoring alerts you if your personal information is found being traded illegally online, and helps you recover after.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
如有侵权请联系:admin#unsafe.sh