Too Long; Didn't Read
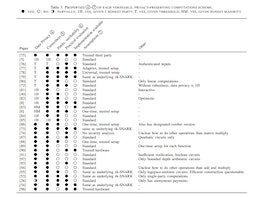
This article had provided a thorough exploration of verifiable privacy-preserving computations, focusing on decentralized data scenarios and Privacy Enhancing Technologies (PETs) like MPC and HE. It delves into the significance of public verifiability, analyzes solutions, and highlights challenges, pointing toward future research directions, including the need for post-quantum security and efficient publicly verifiable Homomorphic Encryption (HE) schemes.


@encapsulation
Bundling data and functions into a single unit
At Encapsulation.Tech we organize and structure code, enhancing security and promote a software design.
Receive Stories from @encapsulation

RELATED STORIES





L O A D I N G
. . . comments & more!