Too Long; Didn't Read
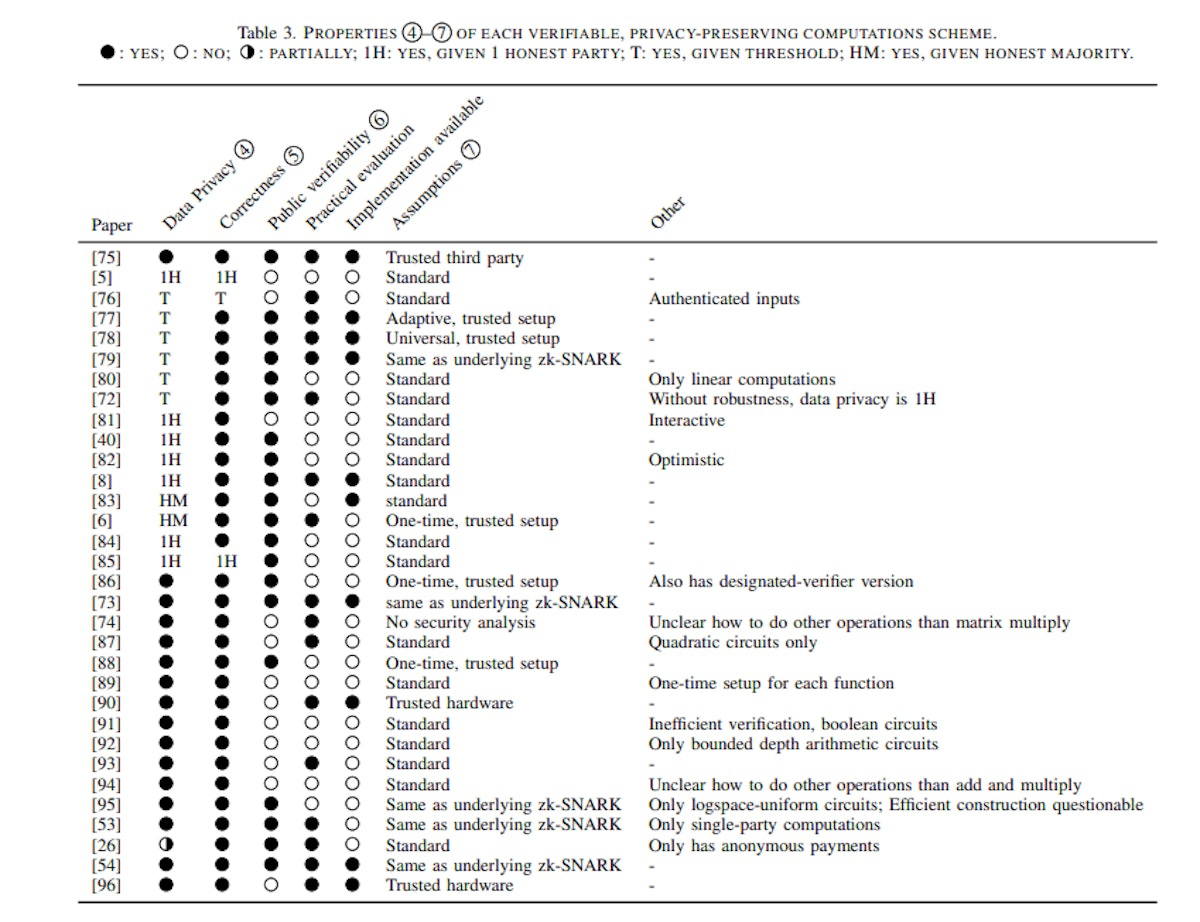
This section meticulously examines the fusion of Privacy Enhancing Technologies (PETs) with verifiable computing. By categorizing and comparing works in Zero-Knowledge Proofs (ZKPs), Message Authentication Codes (MACs), Trusted Execution Environments (TEEs), and more, it navigates the landscape of secure computations. The analysis covers efficiency trade-offs, security assumptions, and the complex interplay between data privacy and verifiability, offering valuable insights into the realm of privacy-preserving computing.

@encapsulation
Bundling data and functions into a single unit
At Encapsulation.Tech we organize and structure code, enhancing security and promote a software design.
Receive Stories from @encapsulation

RELATED STORIES





L O A D I N G
. . . comments & more!