
The safety team at Twitter (I refuse to call the site X because that’s the completely daft kind of name a nine-year-old would choose) has responded to the high profile hack of the SEC Twitter account, which made headlines around the world.
And what do they have to say?
Well, in a nutshell – “it’s not our fault.”
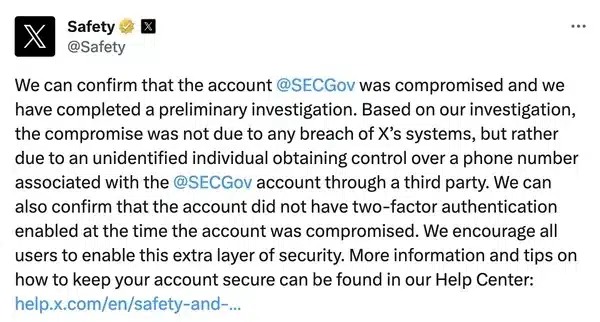
Based on our investigation, the compromise was not due to any breach of X’s systems, but rather due to an unidentified individual obtaining control over a phone number associated with the @SECGov account through a third party. We can also confirm that the account did not have two-factor authentication enabled at the time the account was compromised.
What @Safety is saying is that someone hijacked control of the mobile phone number associated with the official SEC account. This was, one assumes, through a SIM swap attack.
A SIM swap attack is where a scammer manages to trick the customer service staff of a cellphone provider into giving them control of someone else’s phone number. Sometimes this is done by a fraudster reciting personal information about their target to the telecoms company, tricking them into believing they are someone they’re not.
When a service – such as Twitter – later sends a password reset link or authentication token to the user’s phone number via SMS it ends up in the hands of the criminal.
Victims of SIM swap attacks in the past have included former Twitter boss Jack Dorsey, who had his Twitter account hijacked in 2019.
And, I’m afraid, Twitter does make it possible to reset an account password just by knowing and having access to a mobile phone number.
The other interesting revelation is that the official SEC Twitter account did not have two-factor authentication (2FA) enabled. This is a feature that I would recommend all users turn on, as it provides an additional layer of security – and can make it harder (albeit not entirely impossible) for criminals to break into an account.
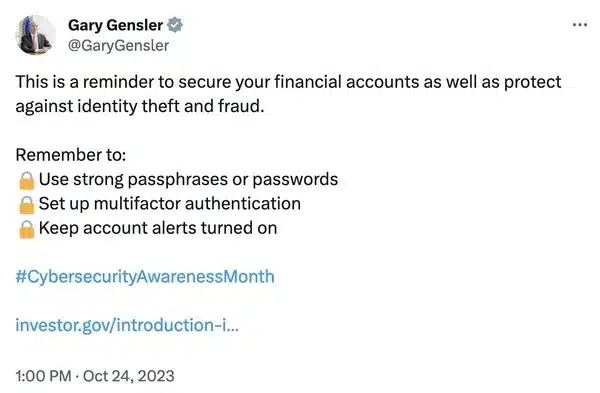
To hear that the US Securities & Exchange Commission did not have multo-factor authentication enabled is frankly bonkers.
Is this the same SEC that is chaired by Gary Gensler, who during cybersecurity awareness month in October, reminded everyone of the importance of setting up multi-factor authentication to secure their accounts?
Hey, here’s an idea for Twitter/X/Elon’s multi-billion dollar vanity project (delete as applicable).
Why don’t you make two-factor authentication (preferably not SMS-based, as there are better forms of 2FA) mandatory for verified and corporate accounts on Twitter?
