2024-1-11 22:0:28 Author: securityboulevard.com(查看原文) 阅读量:18 收藏
SentinelLabs today published a report identifying a Python-based tool that cybercriminals are using to compromise cloud computing and software-as-a-service (SaaS) platforms.
Alex Delamotte, senior threat researcher at SentinelLabs, said FBot is used to take over Amazon Web Services (AWS) accounts in addition to targeting PayPal and other various SaaS applications, such as Office365, she added.
A secondary goal appears to be the harvesting of credentials that can be used for spamming attacks, noted Delamotte.
Specifically, FBot contains multiple utilities, including an IP address generator and port scanner. There is also an email validator function, which uses an Indonesian technology service provider to validate email addresses. The tool itself appears to be of Indonesian origin, said Dellamotte. The letter F in the tool stands for a vulgar term that appears to have been adopted to help market the tool to cybercriminals.
FBot has three functions dedicated to AWS account attacks. The first is an AWS API Key Generator, handled by function aws_generator, which generates a random AWS access key ID by appending 16 randomly selected alphabetic characters to the standard AKIA prefix. It then generates a secret key from 40 randomly selected alphabetic characters.
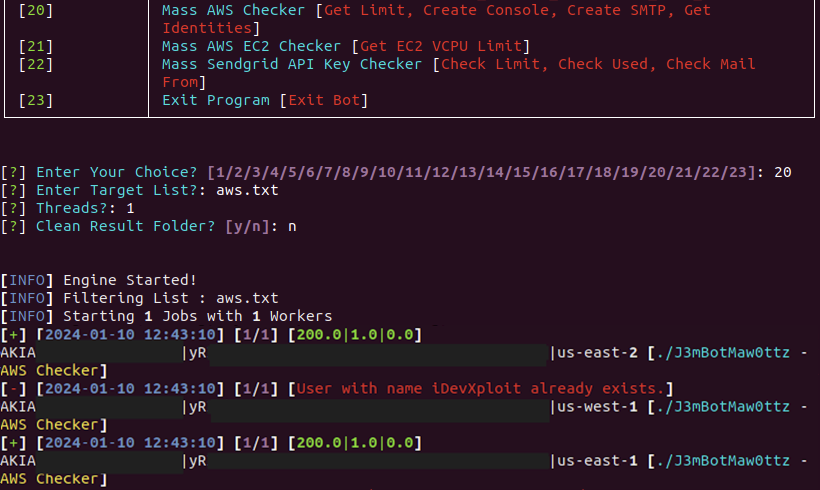
The second AWS feature is a Mass AWS Checker, handled by function aws_checker. This function checks for AWS Simple Email Service (SES) email configuration details, including the maximum send quota and rate, as well as how many messages have been sent in the past 24 hours, likely to maximize spamming efforts against the targeted account. It also creates a new user account with the username iDevXploit and the password MCDonald2021D#1337 and attaches the AdminsitratorAccess policy to elevate privileges for the new account. Unlike other cloud attack tools such as AlienFox, FBot does not delete the compromised account the attacker used to gain access.
The third and final AWS feature is an AWS EC2 Checker, with the description Get EC2 VCPU Limit, which is handled by function ec_checker. This function reads a list of AWS identities from a text file in the format of AccessKey|SecretKey|Region. The script uses these values to check the targeted account’s EC2 service quotas. The FBot menu highlights that this can be used to check vCPU details. The query results describe the account’s EC2 configurations and capabilities and then iterates through a list of specified AWS regions, runs the query again for each region and logs the result to a text file.
In terms of functionality and design, FBot is similar to an existing Legion infostealer tool, but is based on a different codebase that was clearly created by professional developers, said Delamotte. As such, it is likely that whoever built FBot adapted some of the code used to create Legion, she added.
There is no mechanism for identifying whether FBot has been used to compromise a cloud service, but its discovery should serve as a reminder to limit the scope of the cloud services that any single credential should be allowed to access, said Delamotte.
Hopefully, there might be a repository created one day that keeps track of the tools being used by cybercriminals in the hope of making it simpler to identify tactics and techniques. In the meantime, there is no substitute for basic cloud security hygiene in an era where the tools being created by cybercriminals are only going to become increasingly sophisticated.
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
