You might be logging into SAP by entering User name and password. I was doing so from the last 20+ years. However, some of the client systems have Single Sign-on enabled which will login without entering a password and access SAP systems with a concept called tokenization.
For over two decades, I’ve been logging into SAP using the conventional method of entering a username and password. However, certain client systems have the Single Sign-On (SSO) feature enabled that eliminates the need of a password.
Single Sign-On (SSO) simplifies user authentication by allowing individuals to access SAP applications without the need to repeatedly enter their credentials.
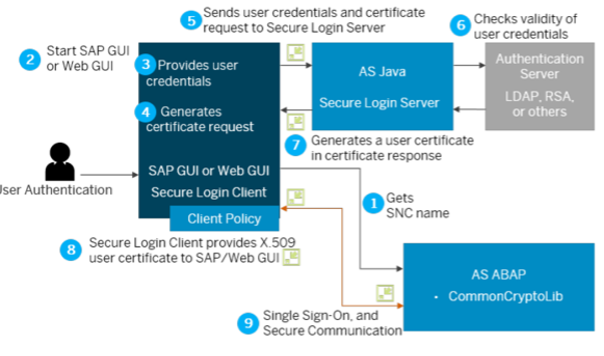
User logs in to the Windows system by utilizing Active Directory (AD) credentials and subsequently launches the SAP GUI or Web GUI application. SAP/Web GUI application gets the SNC name and initiates the generation of a certificate request, transmitting both the user credentials and the certificate request to the Secure Login Server (SLS). The SLS undertakes a validation check on the user’s legitimacy across various systems such as AD, LDAP, RSA, and others, culminating in the generation of a user certificate as part of the certificate response.
The Secure Login Client then furnishes the SAP or Web GUI with the X.509 user certificate, facilitating the establishment of a secure connection with the SAP system. Have a look at the below image that details the process:

Source – Tom Cenens blog
You may get more detailed information about SAP Single Sign On 3.0 product, steps to configure SSO in SAP S/4 HANA and other detailed are outlined in Tom Cenens blog – Click here to read.
That sounds fantastic! Are you satisfied with this, or would you be open to elevating this to the next level?
Exploring the concept of passwordless authentication adds an intriguing dimension to our security discussions, don’t you think? Passwordless authentication is not only convenient to users, but also brings high security. Have a look at the below image that highlights the various options:

Source – Microsoft Learning
In this blog post, we’ll focus on the available options for SAP. While I won’t detail into the nitty-gritty details of implementation and configuration in this discussion, I’ll provide an overview of the various options and share relevant resources.
I’ve outlined seven potential passwordless options below. You may select the one that aligns best with your business and IT requirements, and proceed with its implementation.

1. Biometric Authentication:
Have you heard about FIDO2 biometric authentication? FIDO2 is the Fast IDentity Online 2 open standard for user authentication that aims to strengthen the way people sign in to online services to increase overall trust.
By configuring FIDO2 biometric authentication, users can log on to applications with their biometric information such as fingerprint, face scan, or Windows Hello, without the need to provide username and password.
For more details on setting up FIDO2, visit the SAP Help documentation.
If you are using Fiori or SAP BTP, you may look at the other relevant blogs, and links too:
2. One-Time Passwords (OTPs):
To implement OTPs, you can use SAP Multi-Factor Authentication (MFA) solutions or integrate with third-party MFA providers. SAP supports various MFA methods, including OTPs. Configure the MFA settings in SAP NetWeaver or SAP Fiori to enable OTPs.
You may utilize solutions such as SAP SSO. Many of these solutions supports Web GUI and Fiori based logins, but for the SAP GUI, solutions such as ToggleNow’s UserSentry can be utilized to quickly enable 2FA or MFA.
3. Security Tokens:
Integrating security tokens involves configuring SAP to recognize and validate tokens such as RSA, You may need to set up SAP Single Sign-On (SSO) with support for security tokens. There are typically four types of tokens that are wisely used:
- Static password token
- Synchronous dynamic password token
- Asynchronous password token
- Challenge–response token
These tokens can be integrated with SAP using various methods/protocols such as Restful APIs, oAUTH tokens and many more. Tokens can be used at login level or at specific data level.
4. Mobile Device Authentication:
Another effective strategy is the adoption of mobile device authentication tools like SAP Authenticator, Google Authenticator, Microsoft Authenticator, or Cisco Duo (can be other too). These implementations often require the setup of SAML and SSO configurations, adding an extra layer of security to the authentication process. Mobile device authentication can be seamlessly integrated at either the primary or secondary level. In a recent project, I’ve successfully incorporated Cisco Duo for app-based secondary authentication on mobile devices. This integration covered various interfaces, including Web GUI, Fiori Launchpad, and several cloud applications such as Success Factors and Ariba.
5. Push Notifications:
Set up SAP to send push notifications to users’ mobile devices as part of the authentication process. This often involves seamless integration with Latlongs for enhanced security and management capabilities. When SAP detects a login attempt from a new geographical location, device, or IP address, a mobile device notification is triggered to the mobile number stored in the user’s SU01 personal information. The user is required to acknowledge or authenticate the login request.
This type of authentication is gaining prevalence across various applications due to its heightened security features. While this method can be utilized for primary authentication, I recommend implementing it at the secondary level for optimal security measures.
I’ve successfully implemented this significant enhancement for several clients, providing an additional layer of protection against potential identity theft or system takeovers and see a greater benefit. I’ve utilized Google Geo location APIs to determine the user’s latitude and longitude and added an extra layer of accuracy for the business critical systems.
6. QR Code Authentication:
Although there is still an option to enable QR code-based authentication through the TOTP Two-Factor Authentication service, it is not widely adopted. Generating multiple QR codes is a tedious task (even with API integration) and is used in areas where the generation is less. For example: In warehousing modules for bin and stack identification but face limited use in authentication due to several constraints.
7. Magic Links:
Magic links typically involve sending authentication links via email. You may configure them to generate and send magic links to users’ registered email addresses. The link will be valid for a short duration and grant access upon clicking.
Benefits:
Here are some of the benefits of using password less authentication:
- As detailed initially, Passwordless authentication is more difficult to hack than passwords, which can be stolen or phished for. A quick search bought an article that is published in 2010 which says the most popular password is 123456. Check the article – the most popular password is…
Additionally, check haveibeenpwned.com with your email ID and you will get to know how many data breaches have your email ID. If you are using the same password for your email ID and SAP, then it’s time to change 😊

Remember, the only secure password is the one you can’t remember. Else, adopt to the “passwordless” methods.
- Password less authentication is more convenient for users because they do not have to remember or reset passwords.
- Organizations can save money on password resets and other security-related costs.
Setting up passwordless registration and login processes in applications like SAP Customer Data Cloud (CDC) is relatively straightforward. I strongly suggest looking at Suresh Musham’s blog series provides an interesting and detailed guide on implementing these capabilities with SAP CTD. You can explore the series at this link.
It’s important to note that many of the SAP solutions are not fully available to be integrated, especially NetWeaver-based applications at this time. As technology evolves, it’s possible that these features could become more widely adopted and integrated into various SAP applications, providing enhanced security and user experience across the SAP ecosystem. Stay informed about updates and advancements in SAP’s authentication and security features for potential future implementations in NetWeaver applications.
By understanding and integrating these password less authentication options, organizations can fortify their cyber defences, ensure compliance with ever-stringent regulations, and enhance the end-user experience.
Password less authentication is a promising technology that has the potential to make online authentication more secure and convenient. If you are looking for a way to improve the security of your organization’s online accounts, password less authentication is a good option.
如有侵权请联系:admin#unsafe.sh