2024-1-16 18:49:32 Author: securityboulevard.com(查看原文) 阅读量:18 收藏
Pursuing a cybersecurity initiative takes more than a simple decision made by an organization’s chief information security officer (CISO). It requires resources, time, and, most crucially, buy-in from an organization’s key stakeholders, such as C-suite executives and board members.
But trying to persuade the budget approvers while speaking in the technical language of cybersecurity can be off-putting.
Instead, these leaders want to know what cyber risk means in clear business terms. They want to understand the value that cybersecurity programs bring to the organization and how they align with the overall mission. Essentially, when reporting to business stakeholders, it’s critical to speak in a language they are familiar with, allowing them to easily comprehend what’s at stake. That’s why it’s important to talk about how cyber attacks can lead to financial loss.
When key stakeholders understand that cyber attacks can result in significant monetary losses due to regulatory fines, data recovery expenses, and extortion payments, among other potential costs, they’re more likely to be motivated to invest in stronger defenses. By clearly communicating the cyber risk scenarios that are likely to occur and the potential expenses, CISOs can much more easily acquire the funding they need to keep the organization resilient.
Categorizing the Costs
To facilitate these necessary higher-level discussions and explain how various cyber risk scenarios can impact the company, CISOs can start by grouping financial losses from cyber attacks according to three primary areas. By breaking down these costs into distinct categories, CISOs can better justify why they may choose to prioritize specific initiatives over others.
Technology Costs
A cyber event can cost an organization if malicious actors are able to infiltrate the technology or software and even more so if they decide to encrypt its respective data somehow or tamper with code. Resources will then have to be allocated to repair, replace, or upgrade the affected technology. Businesses may also need to pay for data restoration and forensics services or add new cybersecurity protections, like implementing threat detection software.
Hard Business Costs
In addition to direct technology costs, cyber attacks often require organizations to spend capital on supplemental business expenses, minimizing potential profits. For example, stakeholders may need to hire external PR teams or additional legal counsel to manage the attack response and ensure regulatory compliance. Similarly, because IT staff will put in extra hours to ensure minimized downtime, they’ll need to be compensated accordingly.
Soft Business Costs
Following the hard business expenses, there are often soft business costs that aren’t always as easy to quantify but cause significant resource depletion. For instance, even after a PR team does damage control, the organization could suffer additional reputational harm, and stock prices could drop. In that case, more resources may need to be invested in marketing to make up for the lost customers.
The Importance of Understanding the Expenses
To avoid getting hit with these expenses unexpectedly, organizations of all sizes should aim to understand how their cyber risk translates into financial terms and break them down according to the type of cost. With this level of detail, budget-makers can more effectively plan by investing in technology and human resources or ensuring they set enough capital aside specifically for cyber-related losses.
The Top Cyber Risk Scenarios for Business
Coupled with the types of losses that can be incurred due to a cyber event, businesses should also be aware of the scenarios most likely to cause this financial damage. Because each scenario results in unique implications, if assessed beforehand, stakeholders can be more prepared financially.
The more detailed an organization’s understanding of the various expenses it may face, the more likely it is to remain resilient. With that in mind, the top nine cyber risk scenarios that can lead to financial loss are:
1. Data Breaches
If your organization experiences a data breach, the situation can quickly get expensive. While data breaches are often thought of as malicious, they can also occur because an employee accidentally leaked or exposed sensitive data. Ultimately, a data breach constitutes any event during which private company information is obtained, viewed, or extracted.
From remediating the attack to notifying affected parties to facing compliance penalties or fines, there can be many different types of costs associated with a data breach. On average, data breaches in 2023 cost $4.45 million, up 15% since 2020, and, based on the trend, there’s no reason to believe the costs will ebb anytime soon.
The expense categories can vary widely depending on factors such as the type of data an organization holds and the scope of the attack. Although there are financial impacts, like remediation, that are common to all data breaches, it would be more valuable to conduct financial cyber risk quantification (CRQ), offering you insights into the specific consequences for your organization.
Indeed, the financial impact of a data breach can also depend on how your business responds to it in the immediate aftermath. For example, Yahoo!, at the time known as Altaba, had to pay a $35 million penalty to the US Securities and Exchange Commission (SEC) due to “charges that the company misled investors by failing to disclose one of the world’s largest data breaches in which hackers stole personal data relating to hundreds of millions of users.”
2. Ransomware
Another costly cyber event, malicious by definition, is ransomware. This type of incident is when an attacker encrypts an organization’s files or systems, rendering it impossible to operate business as usual. After the data has been encrypted, the hacker demands a ransom payment, hence “ransomware,” in exchange for restoring access or providing a decryption key.
“Ransomware incidents can severely impact business processes and leave organizations without the data they need to operate and deliver mission-critical services. The monetary value of ransom demands has increased, with some demands exceeding $1 million,” notes the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
There is also the potential for this extorted data to be exfiltrated, an additional action technically referred to as “double” ransomware. Just as with a data breach, a data leak due to double ransomware can be costly to clean up. Not only does the company have to deal with the initial cost of removing the ransomware, but it also might face expenses, like having to notify customers and suffering reputational damages.
Although agencies like the FBI don’t support the use of ransomware payments, the reality is that many businesses do make these expensive extortion payments to unencrypt files, believing it to be the most economical option. (Disclaimer: Kovrr does not endorse making ransomware payments.)
However, even if business leaders decide not to pay the ransom, other remediation processes, like restoring data from a backup, take time, especially if it hasn’t been updated lately. Instead of investing resources into sales and revenue growth, organizations are forced to make unexpected expenditures towards fixing the issue, hurting bottom lines.
3. Business Interruption
While ransomware can cause operational delays, downtime is not the primary objective. Business interruptions due to cyber attacks, on the other hand, are specifically geared toward halting essential functions for a prolonged period and can stem from a variety of sources.
For example, distributed denial-of-service (DDoS) attacks, which often involve cybercriminals sending a flood of traffic through the server, can make websites completely nonfunctional. While this hiccup can be a mere frustration for some organizations, for others, like e-commerce businesses, this downtime can directly lead to lost revenue.
Even if a business interruption due to a cyber attack doesn’t result in a loss of revenue, there are still other costs to consider, like mitigation expenses and incident responses, such as purchasing more bandwidth in the case of a DDoS incident. Employees may also be unable to access critical systems during this time, leading to a loss of productivity.
4. Financial Theft
Organizations should watch out for cyber attacks that directly lead to financial theft. This occurs when unauthorized actors or entities gain access to financial information with the primary intent of stealing money. For instance, an attacker may deploy a phishing scheme to get an employee to accidentally reveal bank login details or wire transfer money to a third party.
Initially, malicious actors targeted banks for this type of attack, going directly to the source. However, “banks have [since] invested so heavily in security that it’s becoming very costly for fraudsters to attack them directly. Instead, fraudsters change tactics and increase their efforts by way of deceiving business owners,” notes M&T Bank.
A common strategy scammers employ is pretending to be from a tax agency, for example, and scare businesses into paying for something they don’t really owe. Managers and employees with access to the organization’s financial data need to remain acutely aware of this possibility and remain suspicious of any external party requesting these details.
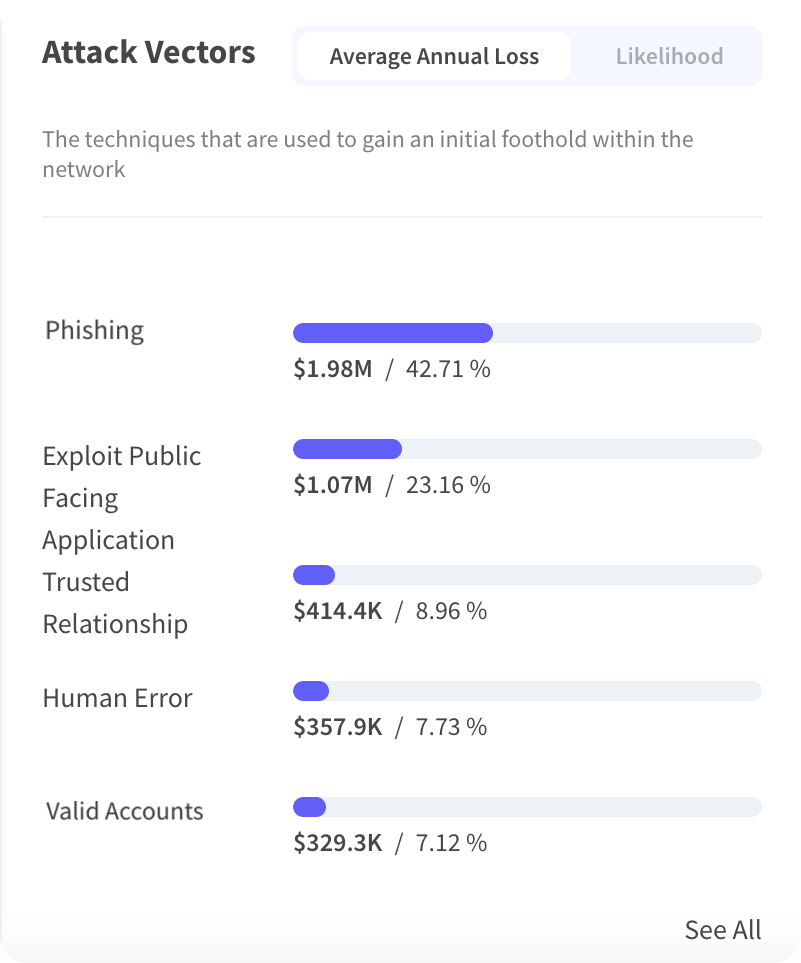
5. Phishing Incidents
As generative AI models are fed more and more data, the more adept they are at mimicking the way we write and speak, making it much easier for hackers to convince unsuspecting employees to give them sensitive information or click on malicious links. This deception, known as phishing, is a type of social engineering commonly used to gain access to an organization’s systems.
In 2023, the notorious hacker group BlackCat successfully impersonated an MGM Resorts employee using information found on the professional networking platform LinkedIn. From there, a member of the group got in touch with the IT department, got password reset approval, and was able to eventually take control of the system, resulting in a $52 million loss.
Phishing schemes aren’t solely executed with the aim of system infiltration. Some have the intention of procuring data for other reasons. Regardless, phishing has the potential to wreak havoc on an organization and cause irreparable financial loss and reputational damage. CISOS must be aware of the likelihood of a phishing event and the level of monetary loss it could lead to avoid such losses.

Leveraging Kovrr’s cyber risk quantification solution, enterprises can gain a more accurate understanding of the loss they face due to a phishing event. With the attack vector forecasts, CISOs can invest a commensurate amount into awareness programs and advanced threat detection solutions. As time goes on, AI will only become more sophisticated, making it essential for employees at all levels to stay vigilant.
6. Third-Party Service Provider Outage and Risks
Just as organizations, or “first parties,” suffer from various cybersecurity events, so, too, do the third-party service providers they rely on. A third-party provider is any external business or entity that supplies the first party with goods or services that are vital to the operations, including cloud service providers, payment processors, and suppliers.
If any of these third parties experience a disruption or operational downtime, it can hinder an organization’s ability to carry out the essential functions. On the less severe end of possibilities, a service provider may suffer from an outage due to an environmental factor, such as a particularly strong thunderstorm. This outage may lead to the first party being unable to access their systems for a few hours.
While this inability results in a loss of productivity and revenue, an organization can still take comfort in knowing that all of the data and logistics will be back in place when the third-party systems return to normal. Still, depending on how long the outage is and the level of integration, CISOs would do well to conduct a third-party risk assessment to evaluate the financial impact this type of event may have.
After gaining a deeper understanding of the likelihood of a third-party provider outage and the potential monetary consequences, businesses can plan accordingly. Having alternative solutions or backup plans in place to quickly switch to is one strategy while negotiating uptime guarantees and commensurate penalties is another. By understanding this particular cyber risk scenario for their organizations, CISOs can plan data-driven initiatives that offset the risk.
7. Third-Party Service Provider Data Breach
Although data outages for third-party service providers can be costly for the first party, data breaches can be more so. When a data breach hits the provider, it potentially results in confidential information about millions of customers of the first party being leaked. Because these service providers generally cater to hundreds, if not thousands, of organizations, the consequences can be extremely wide-reaching.
Recently, Okta, Inc., an identity and access management company that connects organizations’ apps and devices into a single digital environment, fell victim to a data breach. They provided these services to global companies such as FedEx, T-Mobile, and Paramount. About a month after the incident, Okta announced that hackers had stolen data on all users in the system, of which there were about 50 billion.
In the aftermath, Okta’s stock fell by 2.5%, and its reputation was tarnished. While the full effects of this data breach are still unfolding as of January 2023, it still stands as a reminder that which third-party service provider an organization partners with carries significant consequences. When choosing who to work with, organizational leaders need to consult with CISOs to understand the level of risk they’re incurring with the new partnership.
8. Employee Credential Theft
Recent research conducted by Kovrr’s data team found that compromised employee credentials are prevalent across all market industries, particularly in businesses with a market cap of between $1 and $10 million. Password reuse is extremely common for users across their various apps and platforms, including those used for work, making it much easier for attackers to gain access to an organization’s system.
In light of these findings, CISOs should pay close attention to an organization’s password policies and invest in employee credential theft prevention. Introducing measures such as mandatory resets, minimum characters and complexities, and two-factor authentication can make the difference between a successful penetration attempt and an unsuccessful one.
Cybersecurity leaders also need to understand who should have access to specific data and manage access permissions. This way, if a malicious actor does obtain a low-level employee’s login credentials, they will nevertheless not be able to exfiltrate the more sensitive information that only executives use for everyday business functions.
Precisely how much resources an organization invests in password protection directly depends on the levels of financial damage this particular entrance vector has the potential to cause. However, given that harvesting credentials is a relatively simple process for malicious actors, CISOs need to ensure that employees are well aware of the importance of password best practices.
9. Business Email Compromise (BEC) Scams
A business email compromise (BEC) scam is a specific type of phishing scenario that’s highly profitable. In 2020 alone, BEC scammers raked in more than $1.8 billion. Typically, these malicious actors will often pretend to be board members, C-suite executives, or high-level business partners, convincing unsuspecting employees to wire money to them or to reveal confidential financial details about the organization.
For example, in 2019, an attacker posed as an executive partner of a Toyota subsidiary and sent an email to the financial and accounting personnel explaining that payment of $37 million was due. One of the employees believed it to be true and subsequently sent the money to the attacker’s bank account. As of 2023, there is no information suggesting that Toyota ever discovered the perpetrator or received their money back.
CISOs need to make their organizations aware of BEC scams and urge that everyone take caution when financial details or payments are requested, even requiring that such appeals be verified by reaching out directly to the party. Revealing financial details can prove detrimental to an organization, and employees, no matter their level, should be extremely cautious about any email asking for that information.
Financially Quantify Your Cyber Risk With a CRQ Solution
As these cyber risk scenarios show, cyber events can cost your organization money in several ways. While it’s not always possible to block all threats, companies can at least prepare as best they can for these scenarios, accounting for their potential financial impact and investing in cybersecurity programs accordingly.
If your organization is struggling to determine the dollar value at-risk around each of these cyber risk scenarios, talk to one of our cyber risk quantification experts today. We can help you understand your financial exposure according to the specific scenarios your business faces.
如有侵权请联系:admin#unsafe.sh