A few hours ago Certego's Incident Response Team detected a malware campaign serving a new Ransomware variant through Nuclear Pack Exploit Kit.
Compromised web sites redirect the user to the Exploit Kit's first step, located at IP address 85.143.218 .208. The domain name used for this first step varies over time, and some of the variants we saw are:
mexicoss.everythingcannabis .biz shift.boutiqueeuphoria .com
The resource name, instead, does not seem to change:
/customerss/detect.js
The second step is located at IP address 62.76.180 .20 and some of the domain names we saw are:
actually.murdererswelcome .com utah.murwel .com
In this case, the resources seem to mimic the behaviour of a search engine:
/search?q=...
The Exploit Kit serves a Flash SWF file with a 0/56 detection rate on VirusTotal.
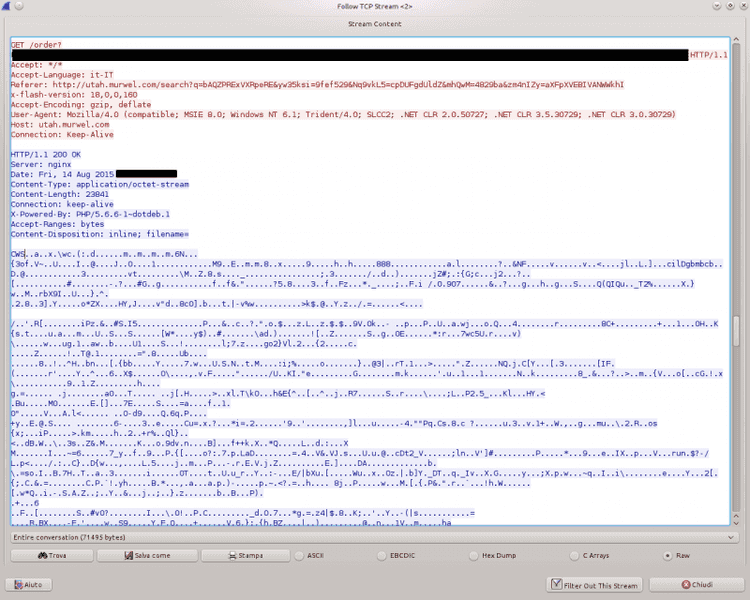
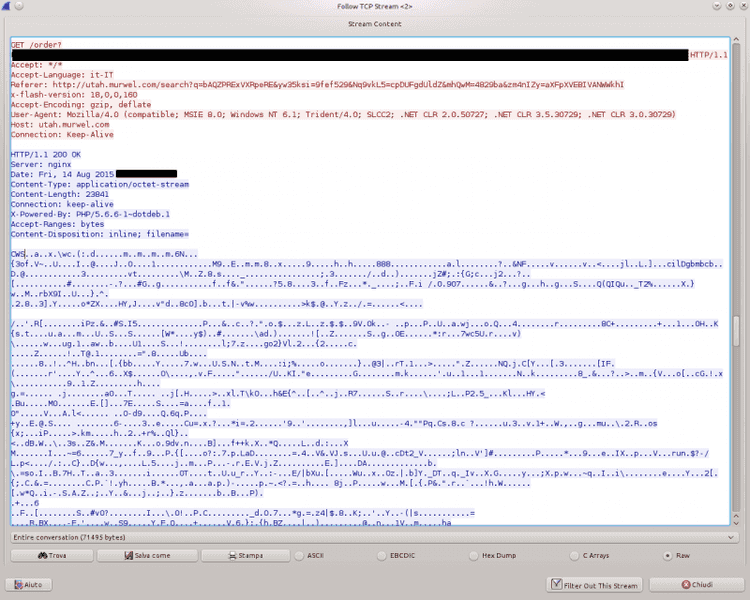
The execution of this exploit causes the download of a payload that is obfuscated by running a byte-wise XOR with a 7 bytes long key, as shown in the picture below.
Deobfuscation is pretty simple and leads to a PE file (Windows executable) that has a pretty low detection rate on VirusTotal (2/56), with only AhnLab-v3 and SUPERAntiSpyware detecting it as malicious.
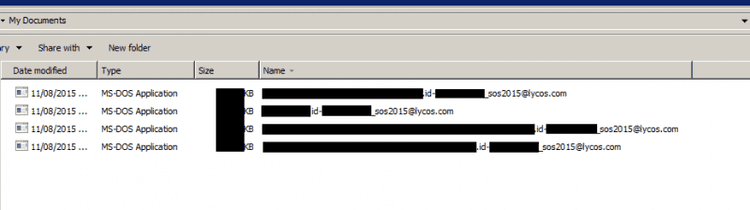
But what does this malware do? Execution on Certego's sandbox shows it will encrypt all of the files on the affected PC, renaming them in the form:
<original_name>.id-
with <original_name> being the original file name,
The most peculiar characteristic of this ransowmare is the fact that it does not give you clear instructions for the payment: it simply renames all your files, and you'll have to be smart enough to understand that all you have to do is to contact the email address you see appended in your file names. The fact that almost no antivirus solution is still able to correctly detect this ransomware shows that it's probably a brand new piece of malware. We still haven't analyzed it, so we still cannot say anything, but right after being executed, the malware makes a single POST request to the following site:
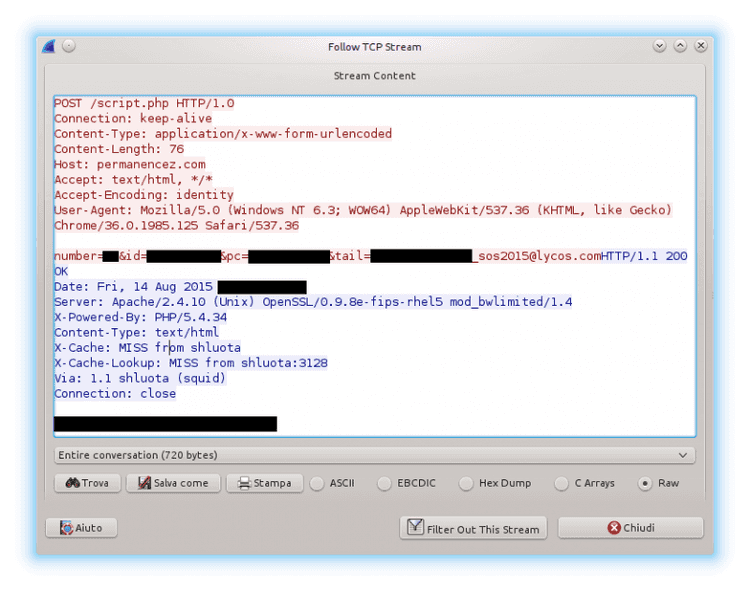
http://permanencez .com/script.php
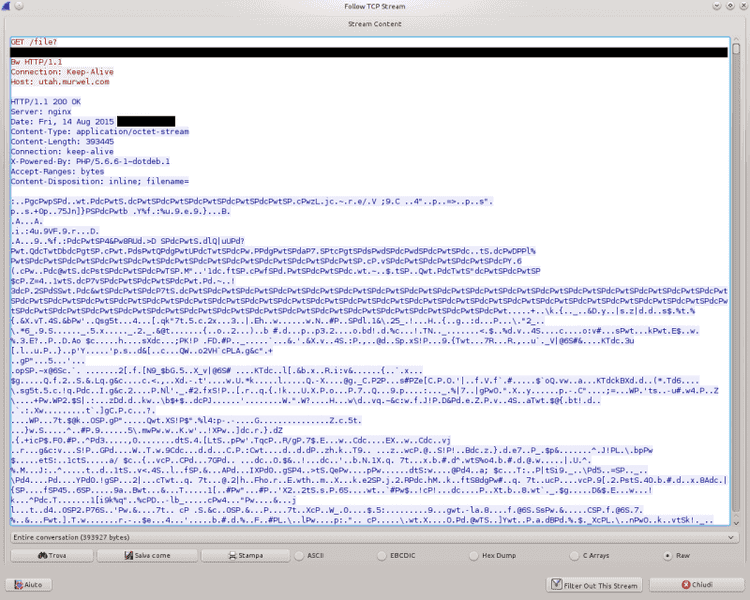
The content of the POST request and the subsequent server response are shown below.
Basically, the malware sends its C&C server a unique ID, the hostname of the infected machine, the whole string appended to the file names (using the format shown above) and a number that appears to be randomly generated. The server answers with a binary string that may contain the encryption key - but we still have to verify this point. They also seem to be using one or more Squid instances as reverse proxies to hide the real C&C's address.
The exploit kit can be detected by using the following two Emerging Threats Snort/Suricata signatures:
ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2
However, the download of the XOR-ed payload and the malware's request to the above mentioned C&C Server do not seem to trigger any alert on Snort at the moment.